You get a 403 Forbidden error when calling an OIDC configuration client
Sure, maybe you do have full administrator privileges to your network, and maybe you are authorized to do anything you want with Hosted Login. And yet, despite all that, you might still encounter a situation like the following when trying to run one of the OpenID Connect Configuration APIs:
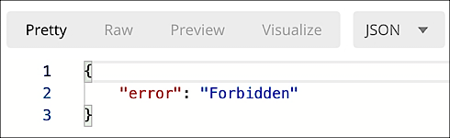
How could this happen? Doesn’t Hosted Login know who you are?!?
To be honest, no, Hosted Login doesn’t know who you are. Nor does it care. As you probably know, the OpenID Connect Configuration APIs rely on bearer token authentication: to run one of the APIs you supply an access token, and Hosted Login takes action (or, as in the preceding case, doesn’t take action) based on the properties of that token. If the token is allowed to do X then you’re allowed to do X. And if the token isn’t allowed to do X? Well ….
Like we said, Hosted Login takes action based solely on the properties of the access token. And one of those properties is this: an administrative access token can only be used for 60 minutes before it expires. More often than not, the 403 Forbidden error occurs because your access token has expired.
Before you ask, no, you can’t rely on a refresh token to automatically grab you a new token any time your current token expires; that’s because administrative access tokens don’t have refresh tokens:
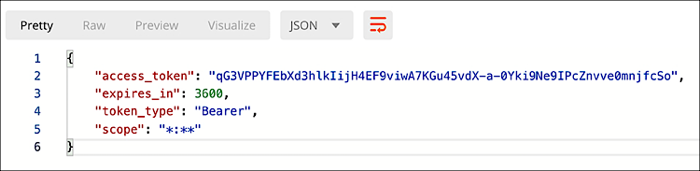
As soon as your access token expires it’s useless. Period.
So what are you supposed to do if your access token expires? Just go get a new one. Get a new access token and you’ll be able to do whatever it is you set out to do in the first place (assuming, of course, that you do it within the next 60 minutes):
Updated almost 4 years ago
