Prepare your edge certificates
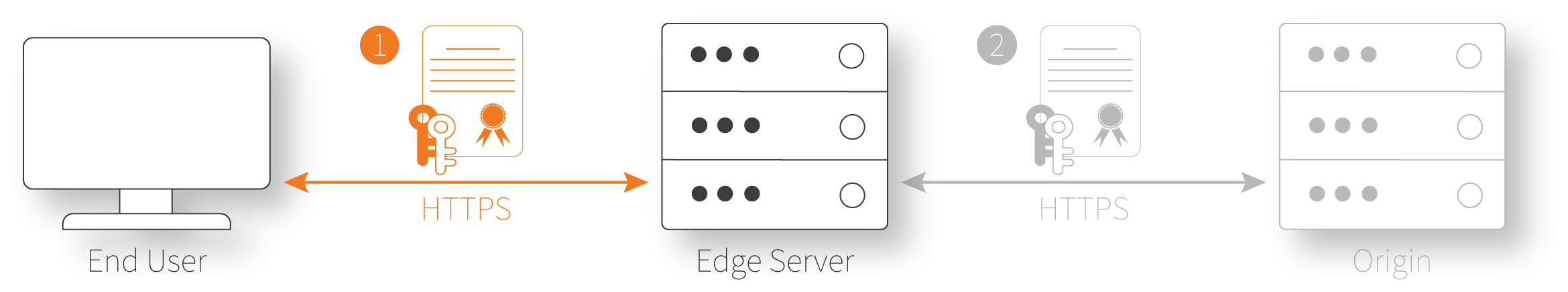
The edge certificate protects the first stage of the request flow—the request from an end user (client) that's received by Akamai edge servers.
Review the available certificate options and plan which one would work best for you. With the CPS-managed certificate, you need to create it before you create your property.
Get to know the security levels
There are various levels of security you can apply:
| Security option | Description |
|---|---|
| Enhanced TLS | This is intended for sites and content with high-assurance security requirements, such as FedRAMP and PCI compliance (HTTPS L3). It also supports custom or very old clients that don't send a TLS SNI header, which requires a VIP hosted certificate. This is what you need if the initial client request or content delivered back to the client include any personally identifiable information (PII). Behind the scenes, Enhanced TLS adds the edgekey.net suffix to your hostname, but it's not visible to the end user. |
| Standard TLS | This security enables the delivery of sites, content, and video streaming over HTTPS using customer-branded certificates. It's secure (HTTPS L1), but not as rigorous as Enhanced TLS. Standard TLS is not FedRAMP or PCI compliant, but it is Sarbanes Oxley (SOX) and International Standards Organization (ISO) compliant. If you're looking for secure delivery, but aren't transferring PII, Standard TLS could work for you. Behind the scenes, Standard TLS adds the edgesuite.net suffix to your hostname but it's not visible to the end user. |
| Akamai shared certificate | This method supports secure access and delivery over HTTPS, without the need to provision and manage a certificate. While it's quicker and easier to set up, you need to use a hostname within the Akamai-owned domains such as example.akamaized.net or example-a.akamaihd.net. It's also not recommended if you're exchanging or delivering PII. Use Enhanced TLS, instead. |
For a more detailed comparison, see Compare the security levels.
Option 1: The CPS-managed certificate
This method supports both Enhanced TLS and Standard TLS secure delivery and it's available to all Akamai customers.
CPS-managed certificates can take a while to provision, and you need one before you can fully set up your Property Manager property for secure delivery. So, you should create one first.
Create certificates with CPS
The Certificate Provisioning System (CPS) is a separate Akamai utility you can use to generate a certificate. All certificates are signed by a Certificate Authority that is known to be trusted by every major browser or operating system.
Use Akamai Control Center to create the certificate
Akamai offers a separate user interface in Control Center that you use to create certificates. See the Certificate Provisioning System user documentation for instructions on this process. During the select network setting phase, you set Deployment Network to the desired level of security, Standard TLS or Enhanced TLS. To make sure everything with your delivery is ready, test it on the staging network before pushing it to production.
Use an API to create the certificate
Akamai also offers an application programming interface (API) that you can use to create your certificate, too. Have a look at the developer documentation for CPS for details.
Wait for the certificate to provision
Regardless of the tool you used, a certificate can take from 3 - 6 hours to provision, based on the level of security you've chosen. The email address set for the Control Center account that you used to create the certificate will receive an email when it's ready.
Create certificates via a third-party vendor
Talk to your Akamai account team for information on supported third-party vendors. Work with a supported vendor to set up an Enhanced TLS or Standard TLS certificate. Then, you need to:
- Make note of the exact domain used to access it from the third-party vendor.
- Provide the certificate to your Akamai account team.
Your account team will contact you when the certificate has been fully provisioned for use.
Option 2: The Default DV certificate
The Default Domain Validation (DV) certificate supports both Standard TLS and Enhanced TLS security. This is an automated approach to creating the certificate. When you set up the connection between your website or app and the Akamai edge network—using a property hostname—you select the level of security you want to use. Akamai automatically creates and provisions the certificate for you and applies it to your Property Manager property.
At this stage, you don't need to create a certificate perform any additional prerequisites. Continue with preparing your origin server.
Option 3: The Akamai shared certificate
This lets you quickly incorporate HTTPS delivery by selecting this certificate type while applying the hostname for your site or app in a property hostname. Its level of security is comparable to Standard TLS
At this stage, you don't need to create a certificate perform any additional prerequisites. Continue with preparing your origin server.
Compare the security levels
There are various security options available for your configuration, based on the level of HTTPS security you apply in your edge certificate. Review the table here to make sure you're choosing the right level of security.
Consider these points:
Specific details may vary in corner cases and for older products that aren't listed. Check with your account team for details. Security properties listed should be taken as rough suggestions and may not apply to all scenarios.
All that's listed is also supported with plain text HTTP requests to the same hostname. No security properties are obtained unless HTTP traffic is redirected to HTTPS. Once you commit to HTTPS-only, HSTS can be used to indicate to clients that HTTP is no longer supported. But, there is no going back.
Non-secure HTTP is also available, but it's not recommended. It's included in this table for comparison.
| Support/feature | Enhanced TLS Certificate | Standard TLS Certificate | Shared Certificate | HTTP only |
|---|---|---|---|---|
Supports HTTPS to encrypt data in transit and validate the identity of the delivery server using TLS certificates. Prevents network-based attackers (such as malware on open Wi-Fi) from viewing and modifying HTTPS requests and responses. | ✅ | ✅ | ✅ | ❌ |
Engineered to meet the high-security demands of banking, e-commerce, healthcare, and similar industries for protecting data-in-transit, while also providing high-performance, scale, and a global footprint. | ✅ | ❌ | ❌ | ❌ |
Engineered to provide high-performance, and massively scalable delivery of media assets as well as many types of websites. | ❌ | ✅ | ✅ | ✅ |
Enables web browsers to indicate that a page is "secure" (such as by a lock icon in the browser address bar) when all page resources are delivered over HTTPS. | ✅ | ✅ | ✅ | ❌ |
TLS server certificate private keys are managed securely to protect against loss. | ✅ | ✅ | ✅ | ❌ |
Support for some very old or custom clients that do not send TLS SNI (Server Name Indication). | ✅ (with VIP cert) | ❌ | ✅ | ❌ |
HTTPS traffic supports Compliance Management for FedRAMP, HIPAA, ISO 27002, PCI and SOC2. Note that additional configuration constraints may apply. | ✅ | ❌ | ❌ | ❌ |
Uses a common/default Akamai certificate that supports clients which do not send SNI. | ❌ | ❌ | ✅ | ❌ |
Includes a DV SAN SNI certificate by default, with other SNI certificate types available as add-ons. | ❌ | ✅ | ❌ | ❌ |
Supports HTTP/2. | ✅ | ✅ | ✅ | ❌ |
Supports HTTP/3. | ✅ | ✅ | ✅ | ❌ |
Supports IPv4 and IPv6+IPv4 dual-stack. | ✅ | ✅ | ✅ | ✅ |
Supports protocol downgrade from HTTPS to HTTP between the Akamai edge and an origin. | Strongly discouraged and additional limitations apply. | ✅ | ✅ | ❌ |
Supports China CDN. (Additional terms apply.) | ✅ | ✅ | ❌ | ✅ |
Supports delivery within Russia. | Only with "Russia CDN Secure" opt-in. | ✅ | ✅ | ✅ |
Supports Edge IP Binding. | ✅ | ✅ | ✅ | ✅ |
Supports Client Access Control. | ✅ | ❌ | ❌ | ❌ |
Supports ESN Staging. | ✅ | ✅ | ✅ | ✅ |
Supports Instant Config hostnames ( | ❌ | ❌ | ❌ | ✅ |
Updated about 1 month ago
