Enhanced Proxy Detection with GeoGuard
Enhanced Proxy Detection (EPD) leverages the GeoGuard service provided by GeoComply to add proxy detection and location spoofing protection. It identifies requests for your content that have been redirected from an unwanted source via a proxy. You can then allow, deny, or redirect these requests.
Using this behavior enables the Show My IP feature by default. This feature allows you to identify the client machine that makes a request to the /geoguard/show-my-ip endpoint using an EPD enabled hostname. AK_CLIENT_IP we use can be a proxy or a non-proxy client.
Use Best Practices mode (recommended)
Once you've enabled this behavior, you need to set the Configuration Mode. Akamai recommends Best Practices. Select it to automatically apply the primary categories that GeoGuard identifies as essential for proxy detection.
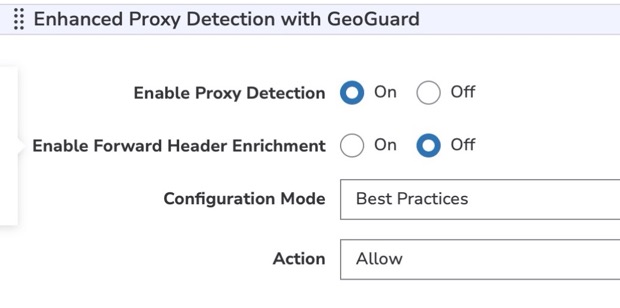
GeoComply maintains a fixed list of categories for their GeoGuard service. This includes multiple primary, must-have categories for proxy detection. The Enhanced Proxy Detection with GeoGuard behavior leverages these categories to recognize that a request is coming from a proxy.
How Best Practices mode is applied
This mode automatically incorporates all of the GeoGuard service's must-have categories. You define an action to be taken when a request is identified from any of these categories:
- Allow. This lets the request through, and the action is logged. You can later audit the logs to determine how setting this to a different action may affect your traffic.
- Deny. This blocks all matching requests.
- Redirect. This sends these requests to an alternate URL that you define.
A Redirect URL can't exceed 2,000 characters in length. Use an absolute URL and ensure that it doesn’t include the same hostname, to avoid creating a redirect loop.
Use Advanced mode
Set this as your Configuration Mode if you're looking to customize GeoGuard categories individually to meet your specific needs.
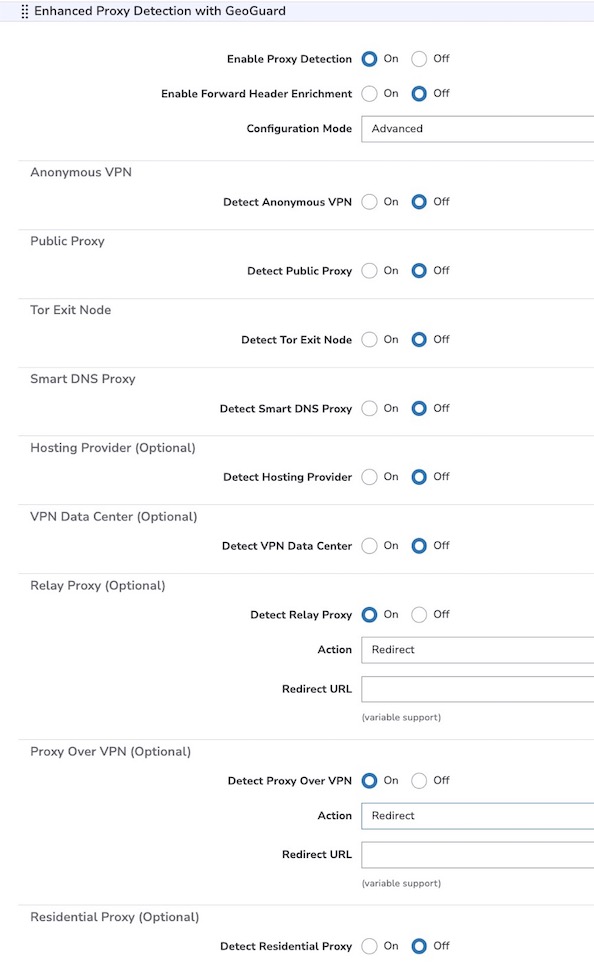
GeoComply maintains a fixed list of categories for their GeoGuard service. This includes multiple, primary ("must-have") categories for proxy detection. The Enhanced Proxy Detection with GeoGuard behavior leverages these categories to recognize that a request is coming from a proxy.
To ensure basic protection, make sure that all of GeoGuard's must-have categories are On. If you don't, Akamai can't promise proper proxy detection protection.
How Advanced mode is applied
For the proxy detection categories you enable, you can define an action to be taken when a request is identified from any of these categories:
- Allow. This lets the request through, and the action is logged. You can later audit the logs to determine how setting this to a different action may affect your traffic.
- Deny. This blocks all requests from that category.
- Redirect. This sends requests from that category to an alternate URL that you define.
A Redirect URL can't exceed 2,000 characters in length. Use an absolute URL and ensure that it doesn’t include the same hostname, to avoid creating a redirect loop.
Requests from categories that are left at Off are processed as normal: they're allowed without logging.
Use case: Different actions for each category
We recommend that you stick with the Best Practices mode for ease of use, and to offer the best overall proxy detection. However, Best Practices require that you use a single action for requests coming from all GeoComply categories. If you need to apply a different action type for the various categories, select Advanced mode and:
- Enable them all.
- Apply the appropriate action for each.
This way, all GeoComply must-have categories have proxy detection enabled, similar to what’s offered with the Best Practices mode.
Allow specific IP addresses
Do you have selected IP addresses that you want to allow, even though EPD positively identifies a proxy? This is called allow-listing. If you do, talk to your Akamai account team to escalate a false positive result with EPD. They'll work with you to either:
- Contact GeoComply. Your account team will alert them to a false positive result for a specific IP address or CIDR block.
- Push a metadata feature override. Your account team will push a metadata update to override a false positive at the platform level.
Add Forward Header Enrichment (optional)
You can also include a header that tells you if a connecting IP address in a request is associated with an anonymous proxy. This can be especially helpful if you need to check the requester before providing access to your content.
It’s implemented in one of two ways, and both methods are supported for use with the Best Practices and Advanced modes for EPD.
Method 1: Enable it directly in the behavior
Here, you add the Enhanced Proxy Detection with GeoGuard behavior to a rule in your property and set Enable Forward Header Enrichment to On. The header is sent along with all requests that meet the match criteria for that rule. For example, if you include the behavior in the Default Rule, that rule applies to all requests. So, the header will be sent along with all requests coming from proxies.
This is the approach you want to take if you have other rules in your configuration that use a behavior to block access. For example, if you're using Content Targeting - Protection with Adaptive Media Delivery, you'd apply EPD as a higher priority (lower in the rule list), to have all Enhanced Proxy Detection settings applied.
Method 2: Add a separate behavior
With this method, you add and enable the Enhanced Proxy Detection with GeoGuard - Forward Header Enrichment behavior to a separate rule. This lets you better control how the header is applied. You add this behavior to a separate rule and use a unique match criteria. Only requests that meet that match criteria will include the header.
This method also requires that you include the Enhanced Proxy Protection with GeoGuard behavior in your property. These points also apply:
- The behaviors need to exist in different rules. This behavior only applies if you want to use a different match criteria to include the header after a request. If you want the match criteria to be the same for both, just use Method 1.
- Ensure the Enable Forward Header Enrichment option is disabled.
- If you’re using other access blocking protections, such as Content Targeting - Protection, you may not want to use Method 1, instead. Otherwise, ensure that both rules you need for this method are higher in priority (lower in the rule list).
About the header
The Akamai-EPD header contains the following information:
Akamai-EPD: <letter code>
The feature leverages GeoGuard's must-have and optional categories to identify and label requests in the header as two-letter or three-letter code:
| Akamai EPD Letter Code | GeoGuard Category |
|---|---|
| is_anonymous_vpn |
| is_public_proxy |
| is_smart_dns_proxy |
| is_tor_exit_node |
| is_vpn_datacenter |
| is_hosting_provider |
| is_residential_proxy |
| is_relay_proxy |
| is_proxy_over_vpn |
So, for a Smart DNS Proxy running in a public cloud, you'd see:
Akamai-EPD: hp dp
Updated 8 months ago
