The third-party origin
You can follow each of the sections in this workflow to add your own third-party origin server to your Property Manager property.
Before you begin: Understand the request flow
This is optional, but it's recommended. Take a minute to familiarize yourself with the flow of a request involving the Akamai network.
1. Prepare your edge certificate
The first phase of a request flow involves the end user contacting Akamai edge servers. To secure this connection with HTTPS, you'll need to prepare your edge certificate.
If you need to use the custom certificate method, you'll need to wait until it completes provisioning before you can set up your Property Manager property. You'll receive an email once it's ready.
2. Meet some prerequisites
Before you can add a third-party origin to your property, you need to work with a supported cloud provider to set up storage space to serve as your origin. You also need to collect some authentication details. See Third-party origin prerequisites for complete details.
We recommend that you use Cloud Access Manager. It lets you easily protect and manage your third-party cloud provider access information as a key. You can find more details on it in the link above.
3. Set up your Property Manager property
If you haven't yet, perform these operations to initially set up your property in Property Manager:
- Create a brand new property
- Define a secure property hostname (for delivery via HTTPS)
- Define property variables (optional)
4. Set up the Origin Server behavior
Now, let's apply some settings in the Property Configuration Settings to set up your third-party origin.
-
In the Origin Server behavior, set Origin Type to Your Origin.
-
Input the Origin Server Hostname you added to your DNS record when you set up your origin server.
Variable support
This field supports variable expression syntax. Typing "{{" in the option field triggers a list of objects to select. Additional details on this support are available by mousing over this option in the UI. Also see Variables overview.
-
Set the following options, as desired:
-
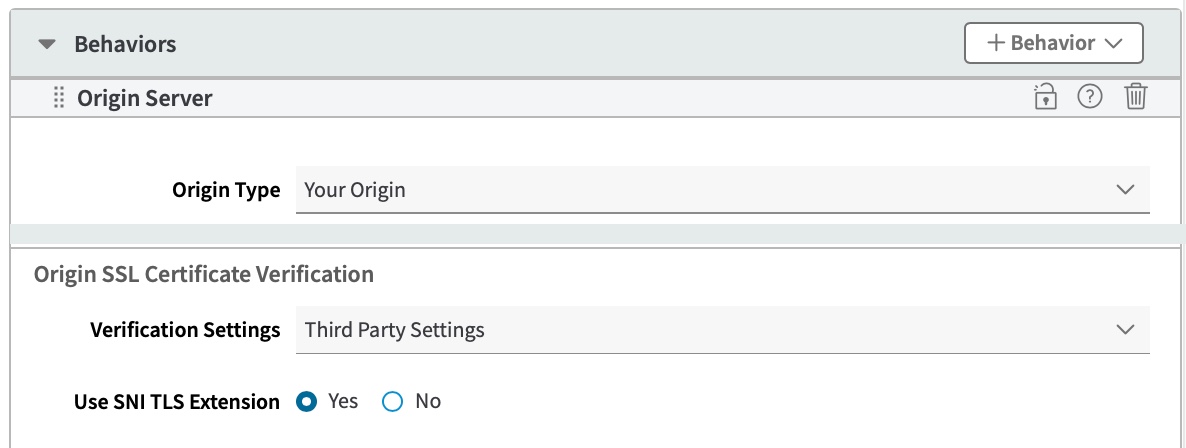
Set the Origin SSL Certificate Verification options as follows:
-
Verification Settings. Select Third Party Settings. Akamai creates a separate certificate authority set for a third-party origin, and manages the certificate for you. You don't have to do anything to upgrade your verification settings.
-
SNI TLS Extension. This only applies if your third-party origin server has been configured to host multiple Standard/Enhanced TLS certificates to support multiple sites. If this is the case, set this to Yes. The Server Name Indication (SNI) header will be sent in the SSL request to the origin. The SNI header value needs to be the same value you have set for the Forward Host Header. Talk to your cloud provider to see if you need to include the SNI header in requests to your origin. Otherwise, set this to No.
-
- Leave the Ports options at their defaults, unless told otherwise by your cloud provider. The standard port for HTTPS traffic is 443.
5. Add the Origin Characteristics behavior
This is where you provide the third-party cloud provider authentication credentials and a few other settings to help optimize delivery. Add this behavior to the Default Rule so that it'll comply with the Origin Server behavior and apply to all requests.
-
Ensure the Default Rule is selected.
-
Click Add Behavior.
-
In the Search available behaviors field, type origin, select Origin Characteristics from the list, and click Insert Behavior.
-
If your cloud provider told you that there's a specific geographic region that contains your third-party origin, set Origin Location to the closest region. Otherwise, leave this set to Unknown. Akamai will still work to optimize delivery based on end-user location.
-
Set Authentication Method options based on the type of authentication you're using, traditional or Cloud Access Manager:
| Authentication type | Amazon Web Services | Interoperability Google Cloud Storage |
|---|---|---|
Use traditional authentication |
|
|
Use Cloud Access Manager |
|
|
Are you using Ion?
An Ion property contains specific rules that you can configure to optimize end-user access and use of your origin server:
Set up Origin Connectivity. Within the Accelerate delivery rule, this sub-rule lets you optimize the connection between edge and origin.
Configure the Origin Offload rule. Here, you'll use several sub-rules to control caching content at the edge and in an end user's browser.
Updated about 2 years ago
