Manage firewall rules
Rule Sets and Prefix Lists
Cloud Firewalls can be configured with both Inbound and Outbound rules.
-
Inbound rules limit incoming network connections to a Akamai Cloud service based on the port(s) and sources you configure.
-
Outbound rules limit the outgoing network connections coming from a Akamai Cloud service based on the port(s) and destinations you configure.
Inbound and outbound rules are applied to Linodes and Linode interfaces (BETA). Only inbound rules are applied to NodeBalancers.
View rules
-
Log in to Cloud Manager and select Firewalls from the navigation menu.
-
From the Firewalls listing page, click on the Cloud Firewall that you would like to view or modify.
Rules are separated into Inbound and Outbound rule sections.
In the rule tables, you can click on Rule Sets and Prefix Lists to view their details. To learn more about referenced rules, see Rule Sets and Prefix Lists (Beta).

Add rules
- Log in to Cloud Manager and select Firewalls from the navigation menu.
- From the Firewalls listing page, click on the firewall that you would like to add new rules to. This takes you to the firewall's Rules page.
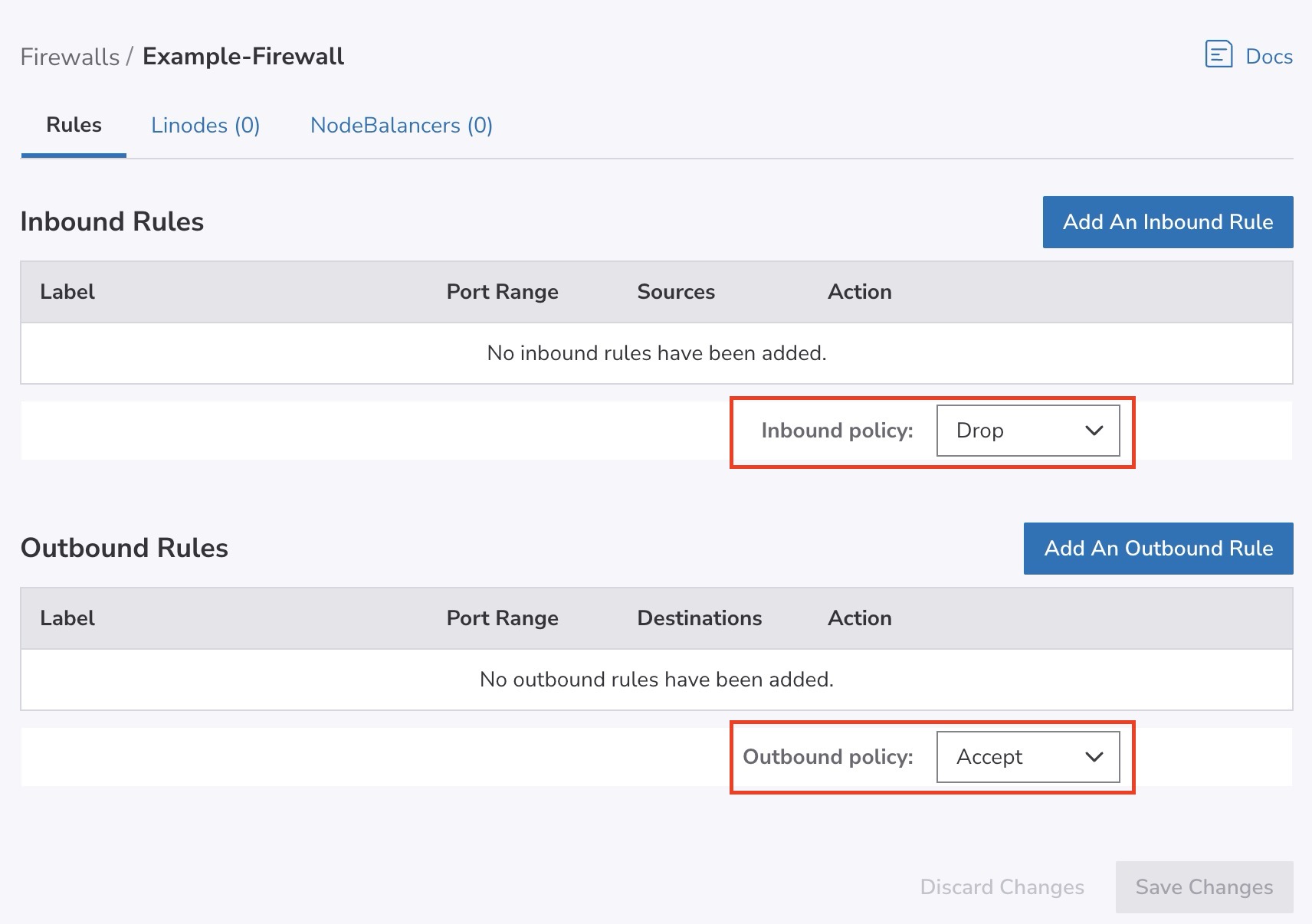
- On the Rules page, select the default behavior for both inbound and outbound traffic using the Inbound Policy and Outbound Policy dropdown menus. Accept allows all traffic except for those defined in the listed rules, and Drop denies all traffic except for those defined in the rules.
Inbound Policy
A default inbound policy of Accept is generally not recommended.
- Click on the Add an Inbound/Outbound Rule link (click on the appropriate link for the type of Rule you would like to add). The Add an Inbound/Outbound Rule drawer appears.
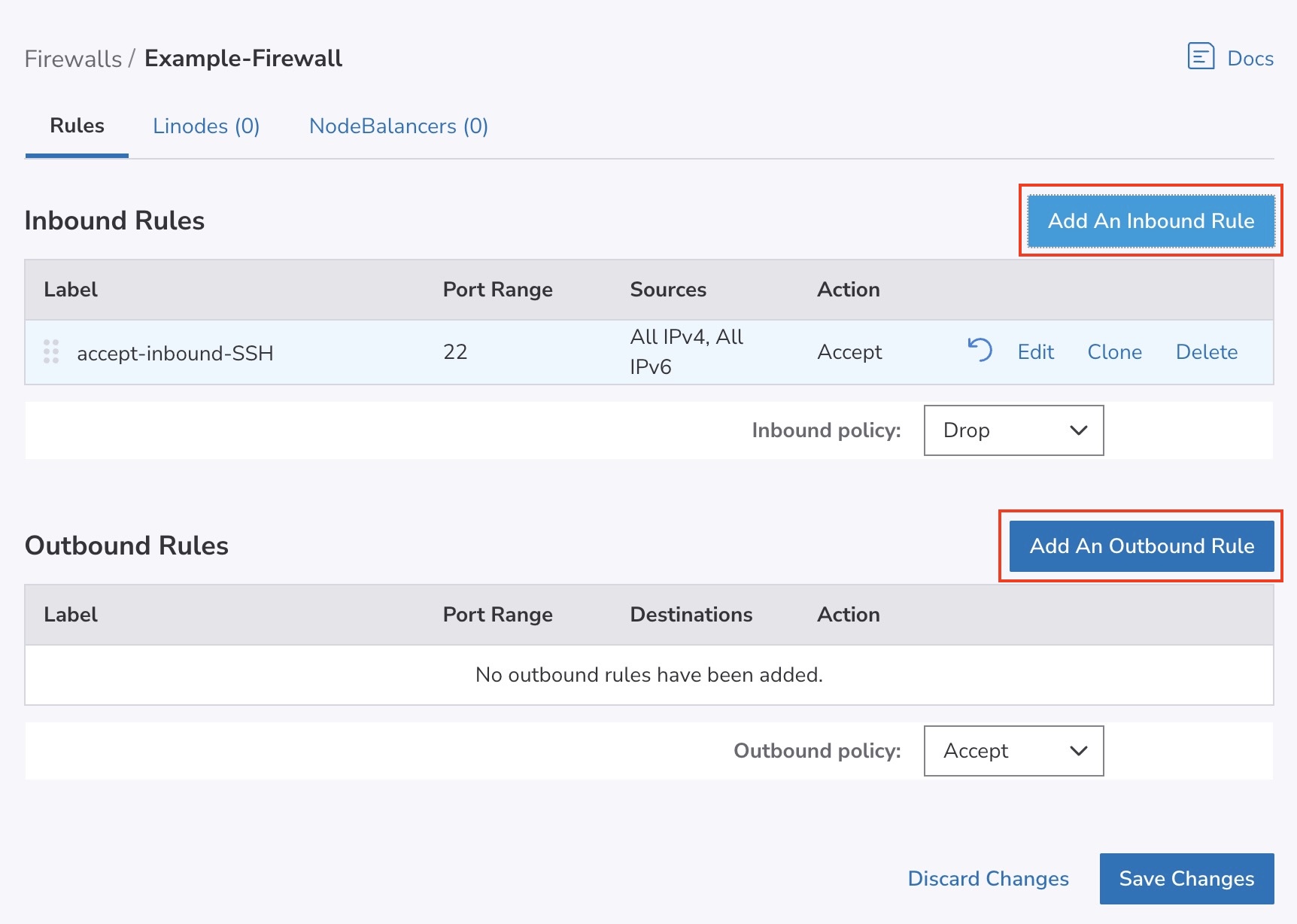
- Select the option to Create a Rule or Reference a Rule Set.
A firewall can include rules defined directly within it, as well as referenced rules. To learn more about referenced rules, see Rule Sets and Prefix Lists (Beta).- If you select the Reference Rule Set option, start entering the name of the Rule Set or pick it from the list. Proceed to the next step (step 7).
- If you select the Create a Rule option, provide the following Rule configurations:
| Configuration | Description |
|---|---|
| Preset | Select from a list of optional predefined Firewall rules. Selecting a predefined rule fills in the remaining rule configuration values, however, they can all be edited. Optional. Cloud Manager provides a list of predefined rules that you can add to your firewall. The predefined rules support common networking use cases and provide an easy foundation to get started with Cloud Firewalls. Since you can edit any rule applied to a firewall, you can modify a predefined rule to accommodate your own applications and requirements. |
| Label | A label for the rule being created. This is used only as an identifier for the account holder and does not have any impact on firewall performance. Required. |
| Description | A description of the rule being created. This is used only as an identifier for the account holder, and does not have any impact on firewall performance. Optional. |
| Protocol | Select the Transport Layer protocol to use for this Firewall rule. Required. The IPENCAP (IP Encapsulation) protocol in a Cloud Firewall rule matches packets based on the protocol field. For IPv4 packets, it looks at the protocol field in the IPv4 header, and for IPv6 packets, it checks the Next Header field in the IPv6 header. The IPENCAP rule only matches the values 4 (for IPv4) and 41 (for IPv6). In short, it matches IP packets that encapsulate an IPv4 or IPv6 packet. |
| Ports | Select from a list of common port numbers, or select Custom to open the Custom Port Range configuration option. Up to 15 ports (and port ranges) can be added to a single firewall rule. Port ranges are considered to be 2 total ports towards the total of 15 maximum ports. Port numbers must be within 1 and 65535, and they cannot contain leading zeroes. Required for TCP and UDP protocols. Not allowed for ICMP and IPENCAP protocols. |
| Custom Port Range | Provide a port number or a range of ports on which to take action. Multiple ports or ranges can be added by separating each port or range with a comma (,). To configure a Port Range, enter the starting port and ending port numbers separated by a dash (-). The port range string can contain up to 15 pieces, where a single port is treated as one piece, and a port range is treated as two pieces. For example, here is an example value that applies the rule to ports 21, 993, 995, and 2000-3000, considered a total of 5 pieces: 21,993,995,2000-3000. |
| Sources | Required for Inbound rules only. Choose from a list of Sources that limit incoming connections to the chosen internet protocol, netmask, or specific IP address(es) and ranges. Select IP/Netmask / Prefix List to specify specific IP addresses or a Prefix List. Add an IP. When defining IP/Netmask sources, a /32 mask is assumed for individual IPv4 addresses and a /128 mask is assumed for IPv6 addresses if unspecified. Each rule can include 255 total IPv4 and IPv6 addresses/ranges. Add A Prefix List. Select a Prefix List and click view details to see information and the IP ranges included. For prefix Lists that contain both IPv4 and IPv6 ranges, you can choose to use both ranges or only one type of range. |
| Destinations | Required for Outbound rules only. Select from a list of Destinations that limit the outgoing connections to the chosen internet protocol, netmask, or specific IP address(es) and ranges. Select IP/Netmask / Prefix List to specify specific IP addresses or a Prefix List. Add an IP. When defining IP/Netmask sources, a /32 mask is assumed for individual IPv4 addresses and a /128 mask is assumed for IPv6 addresses if unspecified. Each rule can include 255 total IPv4 and IPv6 addresses/ranges. Add A Prefix List. Select a Prefix List and click view details to see information and the IP ranges included. For prefix Lists that contain both IPv4 and IPv6 ranges, you can choose to use both ranges or only one type of range. |
| Action | Choose whether this rule allows or drops traffic. The action defined in specific rules takes precedence over the default inbound and outbound traffic policy. Required. |
When applying individual IP addresses or IP ranges to either the
sourceordestinationfield, the addresses must always be valid and formatted correctly using CIDR notation. IP address ranges are formatted differently than port number ranges. Instead of using a hyphenated range of numbers, CIDR notation is used to designate the network prefix and the number of bits in the prefix. The following are examples of valid IPv4 and IPv6 ranges:
192.0.2.0/24198.51.0.0/162001:db8:1234::/48In the first example above, using a range of
192.0.2.0/24applies the rule to all IP addresses from192.0.2.1through192.0.2.254.If you need to specify a single IP address, use /32 when specifying your IP range. For example,
192.0.2.1/32denotes a single IP address.
- Click on Add Rule to add the new rule to this Firewall. If you would like to add any additional rules or reference Rule Sets, repeat the process outlined in this section.
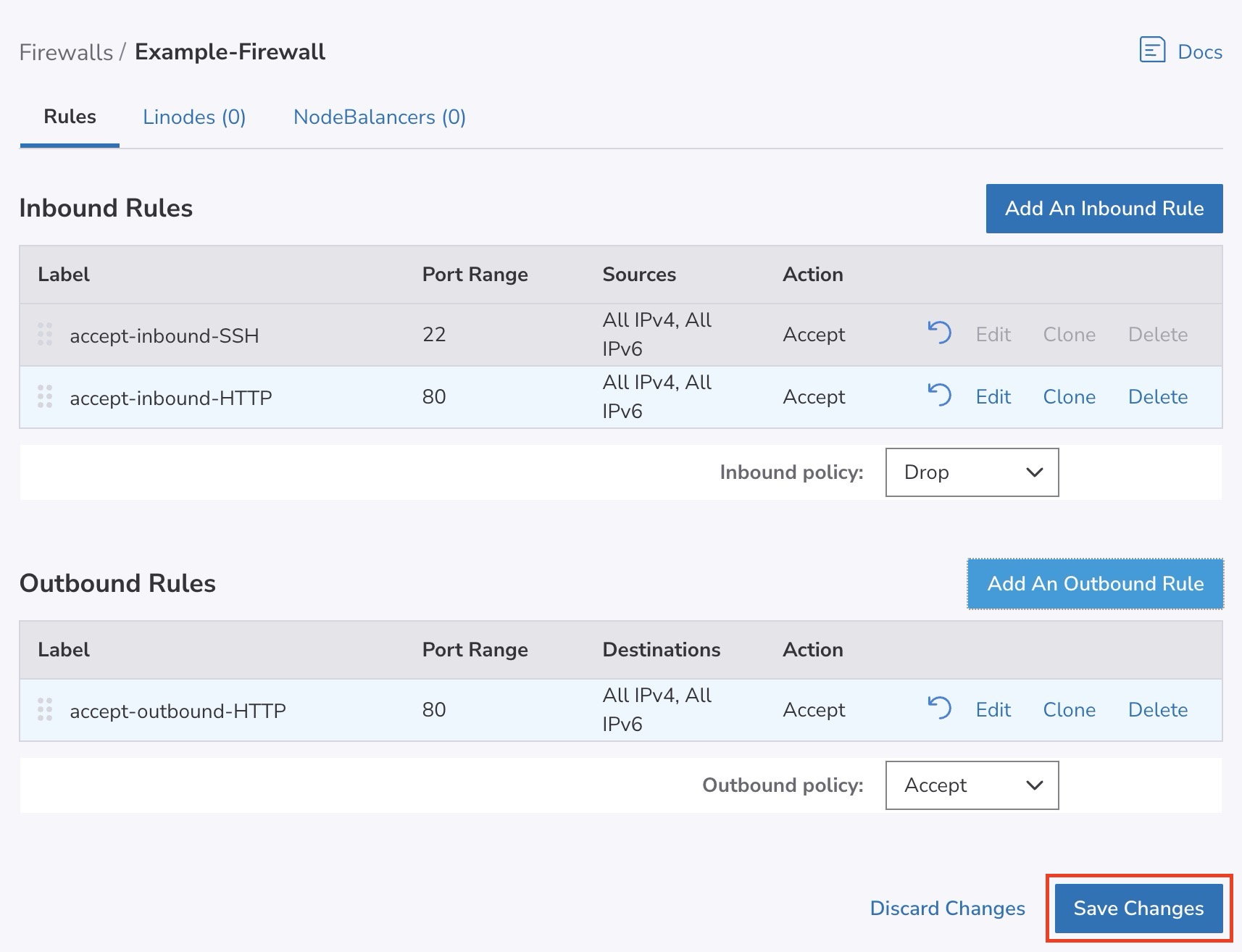
- When you are done adding new Firewall rules, review them on the Rules page you are redirected to by default. Firewall rules are applied in order from top to bottom as they appear on this page. If you would like to re-order these rules, drag and drop any row into their desired position.
- When you are done reviewing the new Firewall rules, click on the Save Changes button on the Rules page.
Any newly added rules do not take effect until you Save Changes to the Firewall.
Edit a rule
Follow the steps in this section to edit predefined and custom Firewall Rules.
-
Log into Cloud Manager and select Firewalls from the navigation menu.
-
From the Firewalls listing page, click on the Firewall whose rules you'd like to edit. This takes you to the Firewall's Rules page.
-
Click on the Edit button corresponding to the rule you'd like to edit.
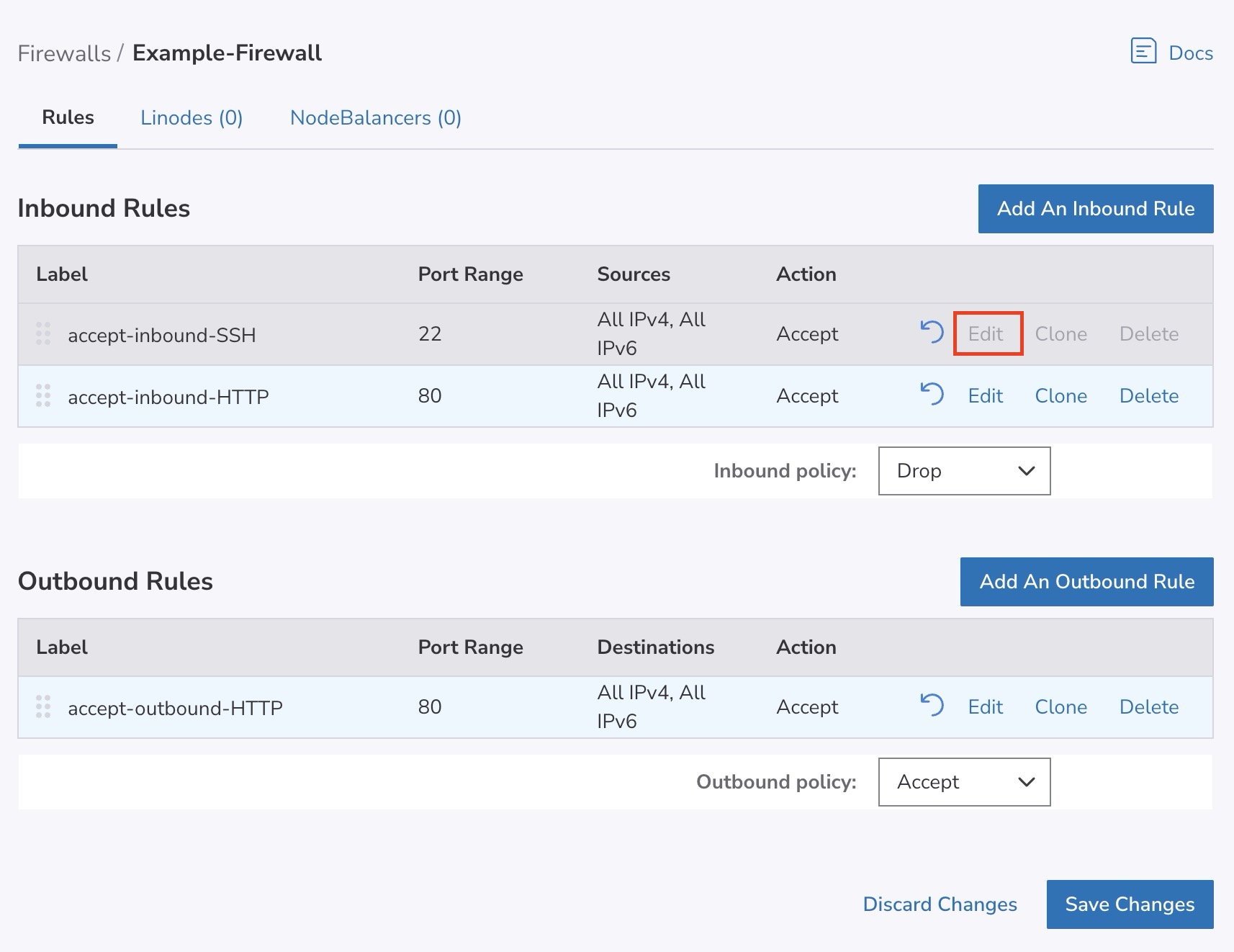
-
From the Edit Rule drawer, update the rule's configurations as needed.
-
Click on the Add Changes button to save your changes and apply them to the rule. If you would like to edit any additional rules, repeat the process outlined in this section.
-
When you are done editing your Firewall rules, click on the Save Changes button on the Rules page for those changes to take effect.
Delete a rule
-
Log into your Cloud Manager and select Firewalls from the navigation menu.
-
From the Firewalls listing page, click on the Firewall whose rule(s) you'd like to delete. This takes you to the Firewall's Rules page.
-
Click on the Delete corresponding to the rule that you would like to delete. If you would like to delete any additional rules, repeat the process outlined in this section.
-
When you are done, click on the Save Changes button on the Rules page for the delete to take effect.he
Deleting Rule Sets
If the Rule Set is still in use, it is marked for deletion and will be deleted once all references are removed.
If the Rule Set was created by a managed service it can't be deleted using a non-service account.
Updated 18 days ago
