Common use cases for VLANs
Secure data and traffic
If you have sensitive data on your network, you can use a VLAN to help keep it secure. By isolating the devices in the network with privileged data, you decrease the possibility of confidential information breaches. For example, the devices in an organization can be segmented into VLANs such as management, sales, support, guests, and others. The devices in one VLAN cannot directly access devices on another VLAN.
Likewise, the traffic in the VLAN is secure. All packets sent over the network in the VLAN are private and protected from access by anyone outside of the network.
Example: web server and secure database
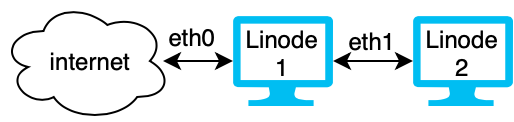
In the diagram above, Linode 1 is a web server and has access to the internet over the eth0 interface. It also has access to Linode 2 and the VLAN over the eth1 interface. Linode 2 on the VLAN is a secure database that houses sensitive data. Communication between Linodes 1 and 2 is transmitted over VLAN and is secure and private.
Example: Kubernetes cluster
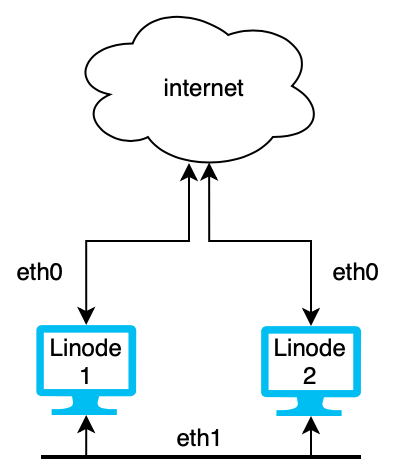
In the diagram above, Linodes 1 and 2 are both in a Kubernetes cluster. Both nodes have services exposed to the internet over the eth0 interface and communication between Pods is kept private and secure on the VLAN over the eth1 interface.
Example: add a NodeBalancer
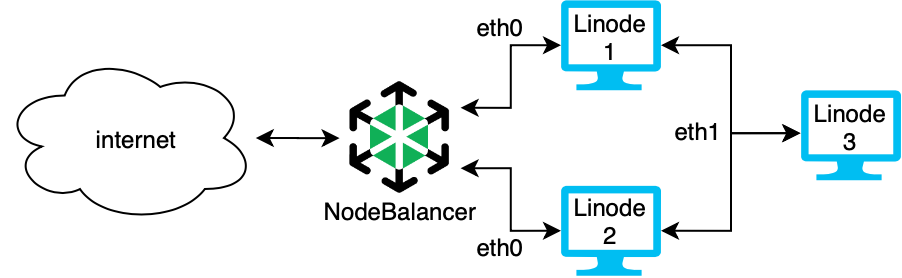
You can increase performance and stability of your application by adding a NodeBalancer while securing the communication between two dedicated servers. In the high availability system above, Linodes 1 and 2 both run the same web application. They both have a connection to the VLAN with the network interface eth1 so they can communicate securely with each other and with Linode 3 which is a database. All communications made over eth1 are private and secure. They are also connected to a NodeBalancer to manage the load over the eth0 interface. The NodeBalancer directs traffic, maintains load balancing, and performs active health checks to make sure the system only directs traffic to healthy servers.
Cost effective network management
VLANs reduce the cost of the networking by efficiently using the existing resources and bandwidth. For example, you can run a secure VLAN in the cloud that is protected from the rest of the internet without generating extra outbound network transfer costs since internal VLAN traffic is internal and private.
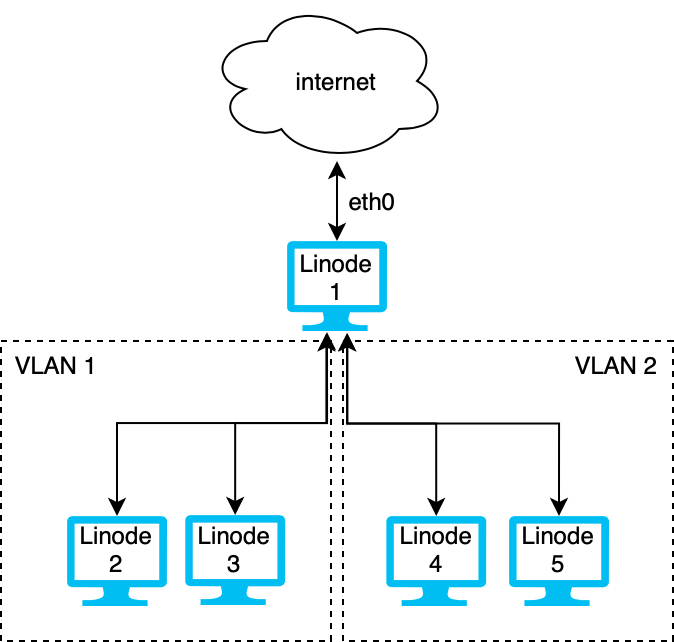
In the diagram above, Linode 1 has three virtual Ethernet NICs, one is attached to the internet and two others to separate VLANs. Linodes 1, 2, and 3 can communicate securely with each other over VLAN 1. Likewise, Linodes 1, 4, and 5 can communicate with each other over VLAN 2. However, Linodes 2 and 3 cannot directly communicate with Linodes 4 and 5.
Next steps
Visit the VLAN product documentation to learn how to create a VLAN.
Updated 8 months ago
