Define access and permissions using ACLs (Access Control Lists)
The preferred way to define access to Object Storage resources is to use a Bucket Policy. Access Control Lists (ACLs) are an older, less powerful method of defining access to Object Storage resources. You can apply ACLs to buckets and (in some cases) objects, giving users access and controlling their permission level. There are two generalized modes of access: setting buckets and/or objects to be private or public. A few other more granular settings are also available; Cloud Manager and s3cmd sections provide information on these respective settings.
ACL differences across endpoint types
Bucket ACLs work in all endpoint types, but object ACLs are only supported for endpoint types E0 and E1.
ACLs in Cloud Manager
Granular permissions for Cloud Manager
| Level | Permission | Description |
|---|---|---|
| Bucket | Private | Only you can list, create, overwrite, and delete Objects in this Bucket. Default |
| Bucket | Authenticated Read | All authenticated Object Storage users can list Objects in this Bucket, but only you can create, overwrite, and delete them. |
| Bucket | Public Read | Everyone can list Objects in this Bucket, but only you can create, overwrite, and delete them. |
| Bucket | Public Read/Write | Everyone can list, create, overwrite, and delete Objects in this Bucket. This is not recommended. |
| Object | Private | Only you can download this Object. Default |
| Object | Authenticated Read | All authenticated Object Storage users can download this Object. |
| Object | Public Read | Everyone can download this Object. |
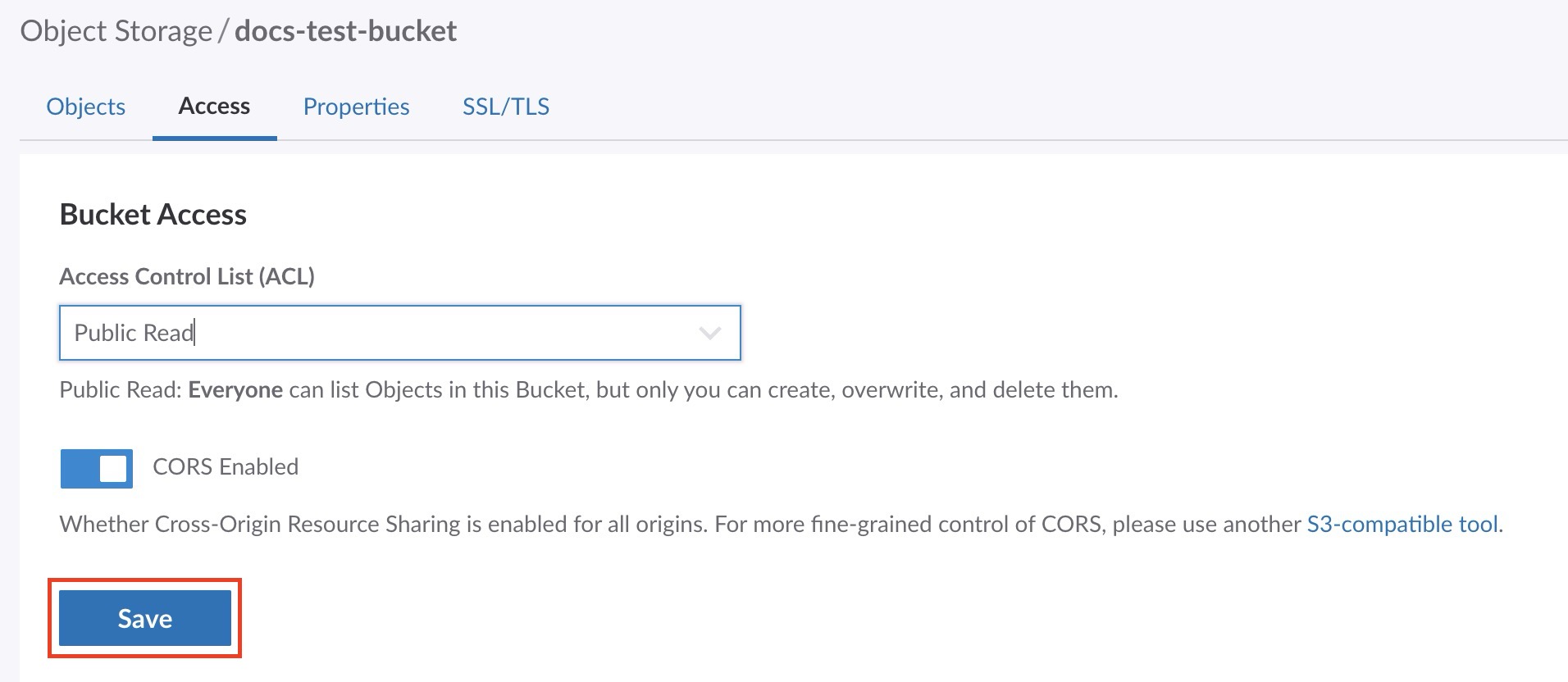
Bucket level ACLs in Cloud Manager
Existing buckets and any new bucket created in Cloud Manager have a default ACL permission setting of Private.
-
If you have not already, log in to the Cloud Manager.
-
Click the Object Storage link in the sidebar, and then click on the bucket you wish to edit the ACLs for.
- The Object Storage Bucket detail page appears. Click the Access tab.
- The Object Storage Bucket Access Page appears.
-
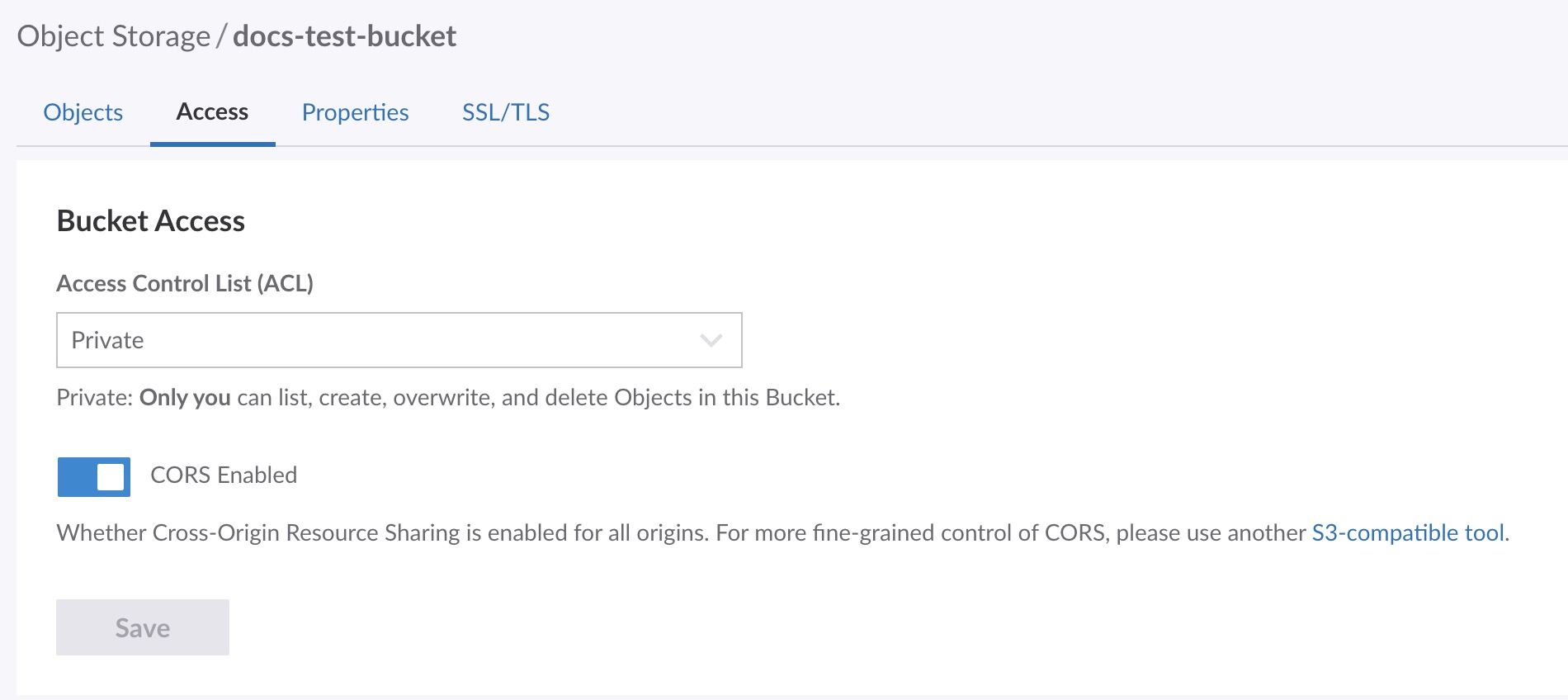
On this page you can select the ACL for this bucket as well as enable CORS.
CORS is enabled by default on all existing buckets and on all new E0 and E1 endpoints. CORS is not available for E2 and E3 endpoints. Go to the Product limits topic for more information.
-
Select the ACL for this bucket from the dropdown menu.
-
Click the Save button to save these settings to the bucket.
Object level ACLs in Cloud Manager
Endpoint types E2 and E3 do not support object ACLs.
Existing objects and any new objects created in Cloud Manager have a default ACL permission setting of Private.
-
If you have not already, log in to the Cloud Manager.
-
Click the Object Storage link in the sidebar, and then click on the bucket that holds the objects that you wish to edit the ACLs for.

-
The Object Storage Bucket detail page appears and displays all the objects in your bucket.
-
Click on the object you wish to edit the ACL settings for.
-
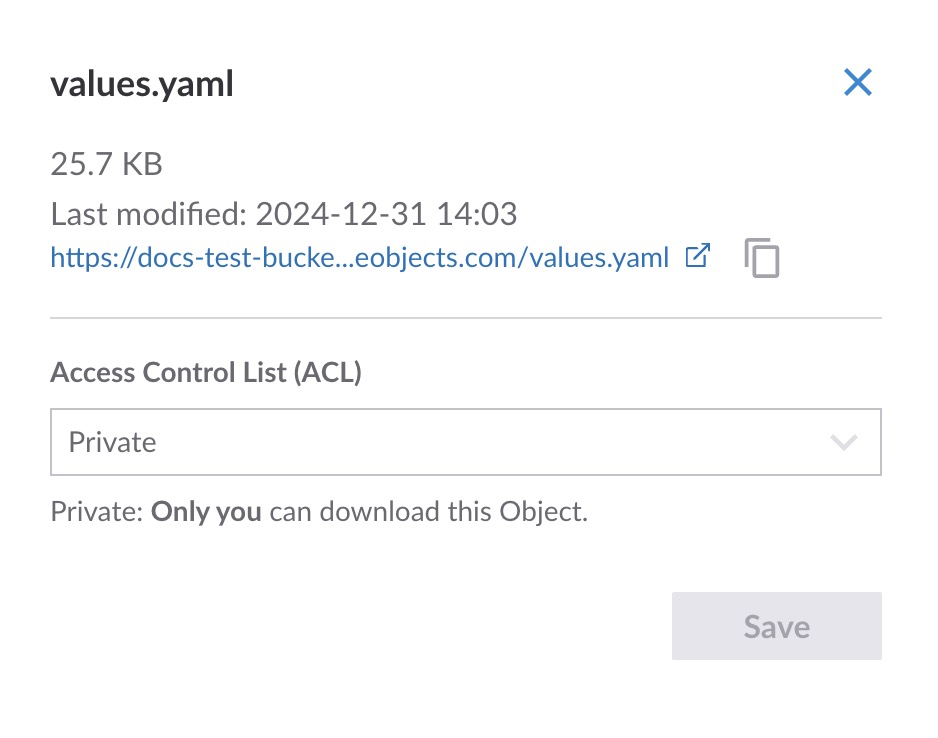
The Object ACL panel opens.
-
Select the ACL you wish to set for this object from the dropdown menu.
-
Click the Save button. The panel closes and the ACL is applied to the object.
ACLs with s3cmd
With s3cmd, you can set a bucket to be public with the setacl command and the --acl-public flag:
s3cmd setacl s3://acl-example --acl-public
This causes the bucket and its contents to be downloadable over the public Internet.
To set an object or bucket to private, you can use the setacl command and the --acl-private flag:
s3cmd setacl s3://acl-example --acl-private
This prevents users from accessing the bucket's contents over the public Internet.
Granular permissions for s3cmd
The more granular permissions are:
| Permission | Description |
|---|---|
| read | Users with can list objects within a bucket |
| write | Users can upload objects to a bucket and delete objects from a bucket. |
| read_acp | Users can read the ACL currently applied to a bucket. |
| write_acp | Users can change the ACL applied to the bucket. |
| full_control | Users have read and write access over both objects and ACLs. |
Setting a permission: To apply granular permissions for a specific user with s3cmd, use the following setacl command with the --acl-grant flag:
s3cmd setacl s3://acl-example --acl-grant=PERMISSION:CANONICAL_ID
Substitute acl-example with the name of the bucket (and the object, if necessary), PERMISSION with a permission from the above table, and CANONICAL_ID with the canonical ID of the user to which you would like to grant permissions. See Find the canonical user ID for an account for details on finding the canonical ID.
Revoking a permission: To revoke a specific permission, you can use the setacl command with the acl-revoke flag:
s3cmd setacl s3://acl-example --acl-revoke=PERMISSION:CANONICAL_ID
Substitute the bucket name (and optional object), PERMISSION, and CANONICAL_ID with your relevant values.
View current ACLs: To view the current ACLs applied to a bucket or object, use the info command, replacing acl-example with the name of your bucket (and object, if necessary):
s3cmd info s3://acl-example
You should see output like the following:
s3://acl-bucket-example/ (bucket):
Location: default
Payer: BucketOwner
Expiration Rule: none
Policy: none
CORS: b'<CORSConfiguration xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><CORSRule><AllowedMethod>GET</AllowedMethod><AllowedMethod>PUT</AllowedMethod><AllowedMethod>DELETE</AllowedMethod><AllowedMethod>HEAD</AllowedMethod><AllowedMethod>POST</AllowedMethod><AllowedOrigin>*</AllowedOrigin><AllowedHeader>*</AllowedHeader></CORSRule></CORSConfiguration>'
ACL: *anon*: READ
ACL: a0000000-000a-0000-0000-00d0ff0f0000: FULL_CONTROL
URL: http://us-east-1.linodeobjects.com/acl-example/
The owner of the bucket always has the
full_controlpermission.
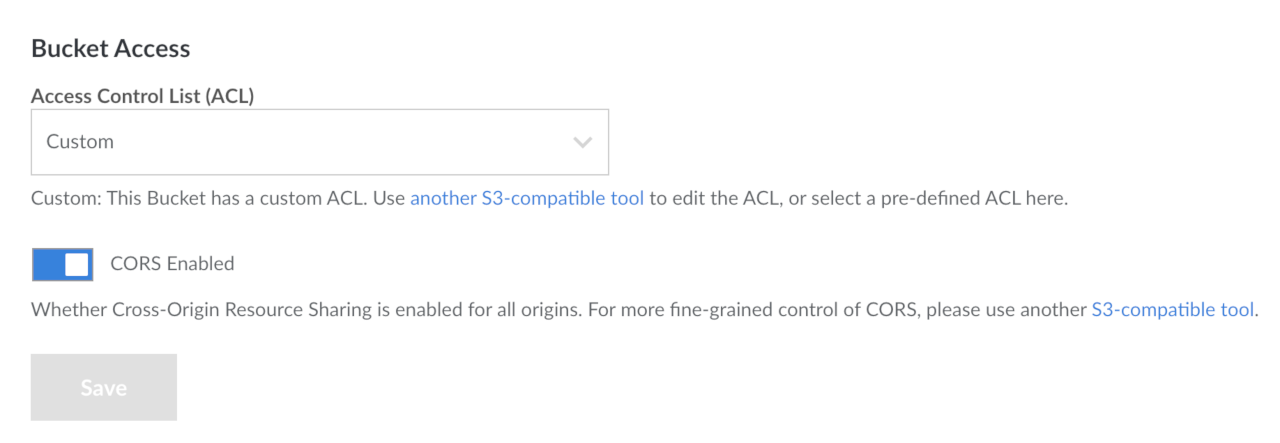
If you set an ACL that does not map to an ACL in Cloud Manager, Cloud Manager displays this as
Custom.
Updated 9 months ago