Disk encryption
Disk encryption ensures that your data stored on Linodes is secured. In addition to Akamai's information security compliance with standards such as SOC 2, disk encryption provides further protections by keeping data encrypted, even if the disk is removed, decommissioned, or disposed of.
The platform manages the encryption and decryption for you.
By default, disk encryption is enabled on all Linodes.
How disk encryption works with different services and features
| Service or Feature | Disk Encryption Behavior |
|---|---|
| Backups: automatic full file-based snapshot of your disks taken during your preferred scheduled time slot while the Linode is still running. | Attention: Backups are not encrypted even when they are taken from an encrypted disk. When a backup is restored, and if encryption is enabled, the data stored on the disk is encrypted again. |
| Images: allows you to store custom disk images in the Cloud. These images can be preconfigured with the exact software and settings and can be deployed to new or existing Linodes. | New images are automatically encrypted. Existing unencrypted images can be recreated to enable encryption. |
| Clone: allows duplication of a Linode to a new or existing instance. | |
| Create: Linodes equipped with a tailored set of resources designed to run any cloud-based workload. | Disk encryption is enabled by default if it's available in a region. You can change the disk encryption setting (Encrypt Disk) if the Linode is not part of a LKE node pool. After a Linode is created, changing the Encrypt Disk setting requires a Rebuild. |
| Migration: moves your Linode to another data center. | During migration, a new disk is created on the destination host. Decrypted bits are copied over from the source to the destination. The new disk is encrypted if the destination host has disk encryption enabled. |
| Rebuild: start over with a fresh Linux distribution or use a backup. | You can change the Encrypt Disk setting by performing a Rebuild. During a Rebuild, the previous encryption setting is used unless it's changed. The Encrypt Disk setting for Linodes attached to an LKE node pool can not be changed. |
| Rescue: boot your Linode into Rescue Mode to perform system recovery tasks and transfer data off the disks when you suspect a corrupt file system. | When a rescue image is deployed, and if encryption is enabled, the data stored on the disk is encrypted again. |
| Resize: changing a Linodes plan to resize your instance. |
Considerations
-
You can enable disk encryption on existing, non-encrypted Linodes by using Rebuild.
-
After a Linode is created, changing the Encrypt Disk setting requires a Rebuild.
-
Disk encryption is enabled by default for Linodes in distributed regions, and cannot be disabled.
-
Disk encryption is disabled by default for nodes in LKE clusters. Contact Support to enable this feature on your account.
-
Encryption in general, can increase CPU overhead and decrease realized throughput.
- For performance-sensitive workloads on Linodes, you can opt-out of disk encryption or disable Encrypt Disk by performing a Rebuild.
Check if disk encryption is enabled on a Linode
-
Log into Cloud Manager and click the Linodes link in the sidebar.
-
Click on a Linode from the list to view more details.
-
Within the top Summary section, you can view if the Linode is
EncryptedorNot Encrypted.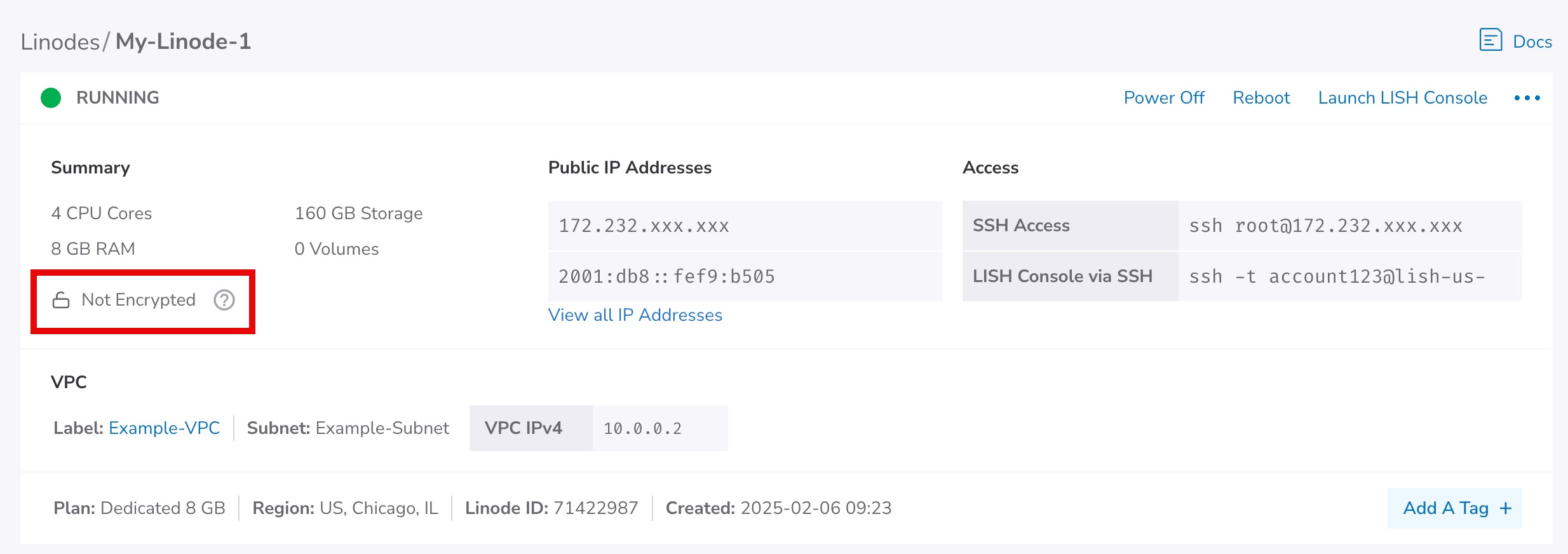
Check if disk encryption is enabled on a cluster's node pools
-
Log into Cloud Manager, click Kubernetes in the left menu, and select the cluster you wish to view.
-
Scroll down to the Node Pools section. This lists all node pools for your cluster and their encryption status.
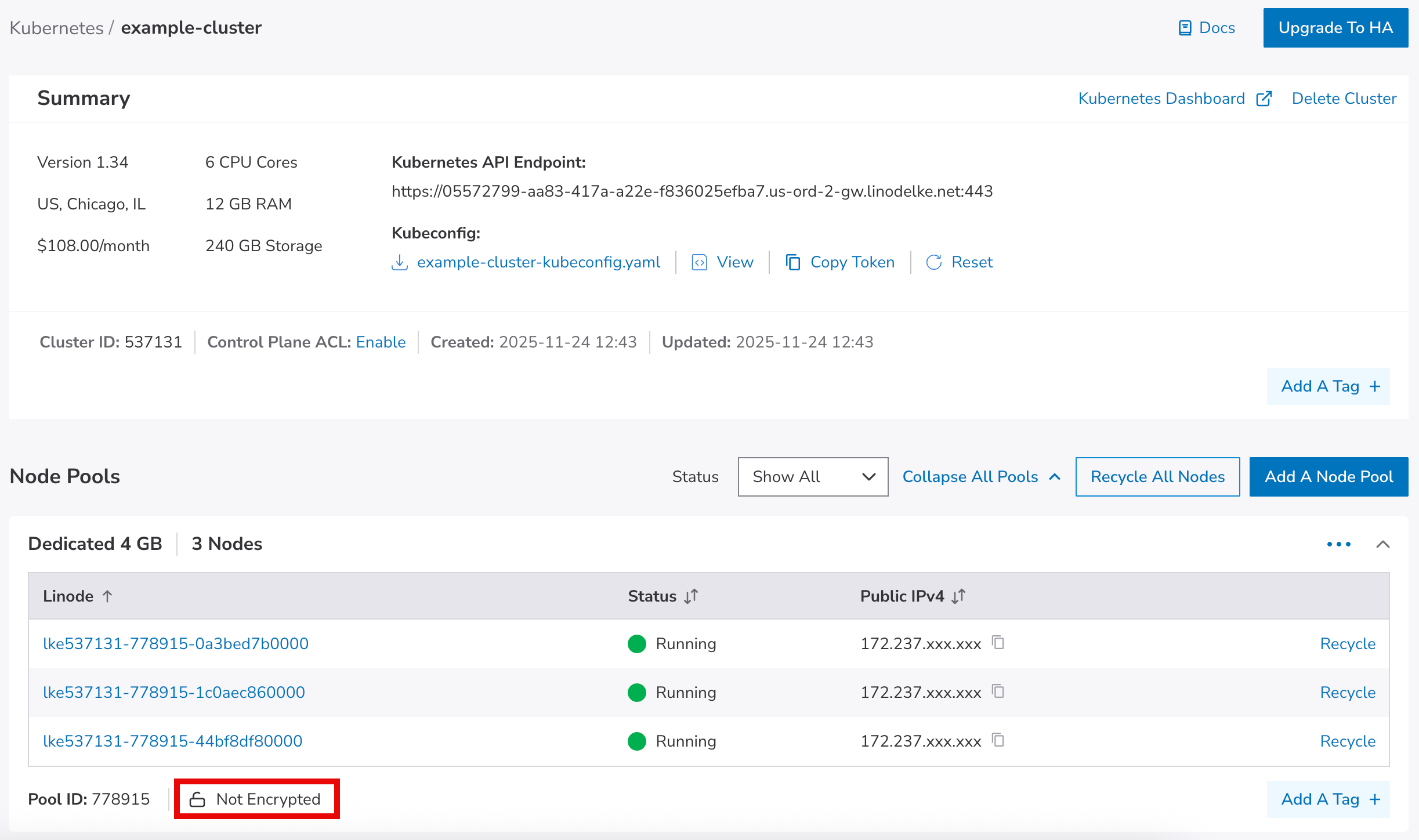
Disk encryption support on LKE
Disk encryption is disabled by default for nodes within an LKE cluster. To enable this feature, contact Support.
Updated about 1 month ago
