Configure SSH access for Linode Managed
To troubleshoot an issue with a failed monitor check, our support team needs access to your system. Access can be provided by using the unique public key generated for your account. You can upload this key to any system user and then configure the SSH access settings for each Linode so our support team is aware of how they should log in. To start using your public key, follow these steps for each Linode on your account.
- View your account's public key.
- Install the public key on your preferred system user.
- Edit the SSH access settings for the Linode.
If you don't want to use this public key, you can also configure credentials in the form of usernames and passwords.
View your public key
Akamai generates a unique public/private key pair for your account when you enable Linode Managed. You can access the public key on your account so that you can add it to each Linode. Our support team uses the private key to access your system whenever an issue requires investigation.
To locate your public key:
-
Log in to Cloud Manager and select Managed from the sidebar.
-
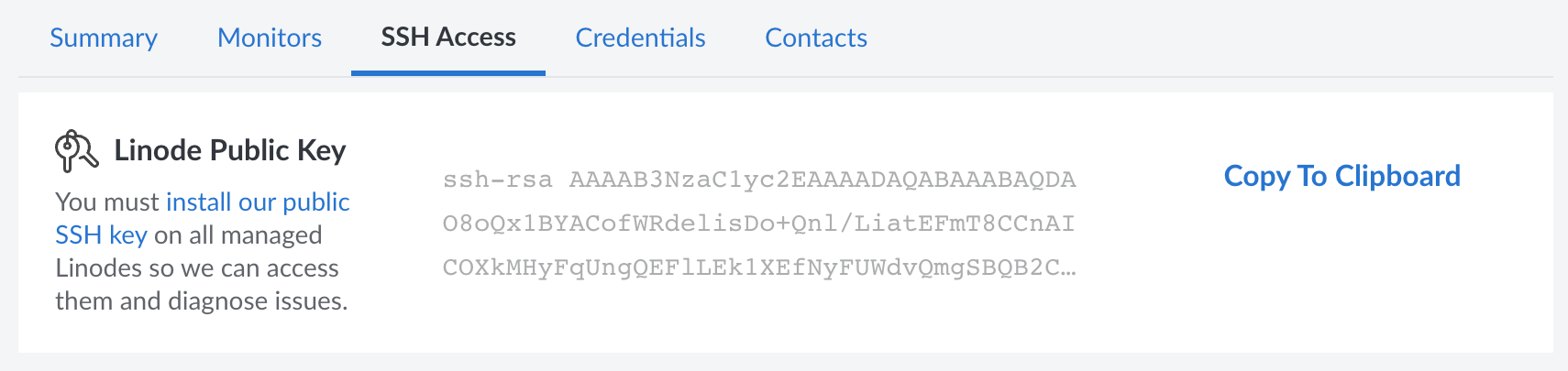
Select the SSH Access tab. Your public key is displayed at the top of this tab.
-
Hover over the public key box to view the full public key and click Copy to clipboard button.
Add the public key to your Linode
Installing the public SSH key for the root user is the easiest way to add the Linode's public key to your server.
If your server's SSH configuration doesn't allow root login, you can skip to the next section to add the public key to another user's account.
-
Edit the SSH authorized keys file for whichever user account you want the Support Team to use when logging in.
-
Root user. Issue this command:
sudo nano /root/.ssh/authorized_keysIf you followed the instructions in the Securing Your Server guide to disable root login via SSH, you need to re-enable that feature. Follow the relevant instructions within the Set Up and Secure guide to edit the
sshd_configfile and re-enable root login via SSH. -
Limited user (To edit the home directory as needed). Run this command:
sudo nano /home/example_user/.ssh/authorized_keysIn general, sudo privileges are needed to run many of the troubleshooting commands our Support Team might use. Whenever possible, you should grant the limited user sudo privileges. The Adding a New User guide shows how to add your user to the
sudogroup (orwheeloradmingroup, depending on your distribution).After adding the limited user account to the sudo group, you need to either provide the user's password to the Support Team (see Add Credentials) or enable passwordless sudo by following the instructions below.
-
Edit the
sudoersfile. The following command opens the file using the Nano text editor.nano sudoers -
Navigate to the User privilege specification section of the file using arrow keys.
-
Add the following line, replacing
example_userwith your user name:example_user ALL=(ALL) NOPASSWD: ALL -
Make sure that this user is not in any other groups listed in /etc/sudoers, as this may override the passwordless sudo setting.
-
Press CTRL+X and then Y to save the changes.
-
-
-
If the
.sshdirectory doesn't exist for your user or the root user, you can create it with the following command, replacing [directory] with/home/example_user/.ssh/or/root/.ssh/, adjusting the path as needed for your user.mkdir [directory] -
Paste your public key to a new line in the file.
-
Save the changes to the file and exit your text editor. In the
nanoeditor, typeCtrl>X>Y.
Once you've added the public key to your preferred user, you may need to allow access from our infrastructure (see Configure Firewall Rules to allow access for more information.) If you wish to confirm that everything is properly configured, open a support ticket to have the Support team confirm that they have access. Repeat this process on every Linode you want to monitor.
Edit SSH access settings for each Linode
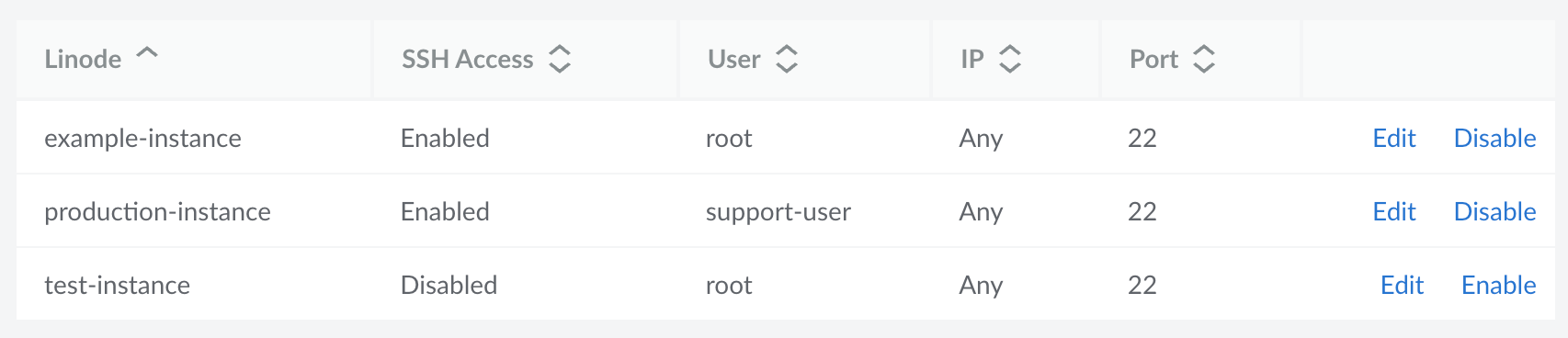
After adding your public key to each Linode you want to monitor, make sure to edit the SSH access settings for those Linodes (and any other iLinode on your account). These settings are used to confirm that SSH access has been enabled and, if so, on which user and port. The following settings can be specified:
-
SSH Access. Specifies if SSH access is enabled for the Linode (default: Enabled).
-
User. The user account that the Support team should use (default: root).
-
IP. The IP address that the Support team should use (default: Any). This is only needed if your Linode has multiple IP addresses and only certain ones allow SSH connections.
-
Port. The SSH port on the system (default: 22). Only change this if your system is using a non-standard port for SSH connections.
Modifying these SSH access settings for a Linode does not change anything internally on your system. These settings are only used to communicate access details to the Support team.
Follow the steps below to edit the SSH access settings for each Linode.
-
Log in to Cloud Manager and select Managed from the sidebar.
-
Select the SSH Access tab and scroll down to view a list of Linodes on your account.
-
Locate the Linode you want to modify and click Edit.
-
Update the SSH access details with the appropriate values for your system. Once you're done, click the Save Changes button.
Updated 6 months ago
