Connectors
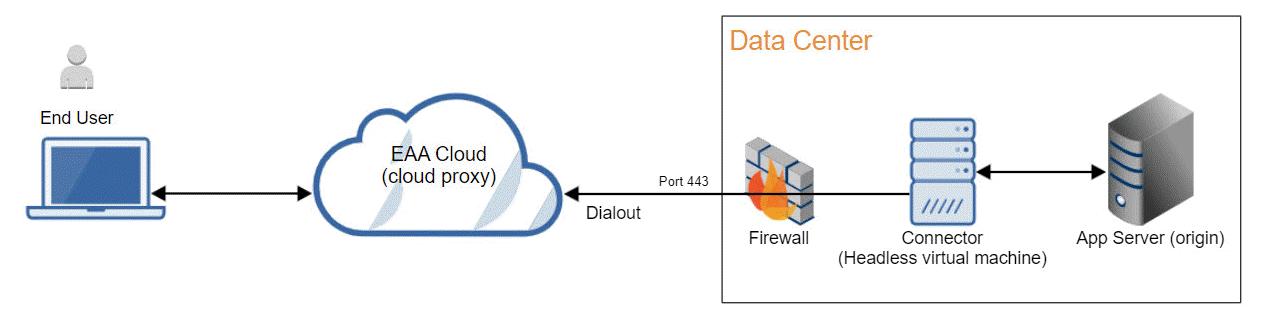
The Enterprise Application Access (EAA) connector is a virtual appliance deployed behind the firewall in your data center or in hybrid cloud environments. It connects an authenticated user with assigned enterprise applications. Connectors behave like Lightweight Directory Access Protocol (LDAP) clients. They communicate with your Active Directory (AD) or Lightweight Directory Access Protocol (LDAP) servers, and synchronize your AD users for authentication (EAA does not store any passwords).
You can deploy multiple connectors for redundancy and scaling. Connectors are cryptographically unique and devoid of any management interface or UI. As soon as you create a connector and power it on, it dials out on port 443 outbound and checks in with the EAA service for its configuration settings.
You can configure an application to be associated with several connectors for high availability. If a server or VM with a running connector fails, your application is still secured by at least one other running connector. Any additional connectors are separate resources as they each take up an instance or VM.
Connectors work to load balance application traffic. Ensure that all connectors required to secure a given application are able to reach the application.
You can grant a user a connector administrator role to configure connectors or a custom administrator role to manage the administration tasks for multiple resources with role-based access control in Akamai Control Center.
NoteEnterprise Application Access does not support any modification to the connector image, including download and install any other software modules, or scripts, for any purpose, except initial network configuration, unless approved by Akamai and the customer.
You can install the EAA connector on Virtual machines (VMs) and these cloud platforms. See instruction based on the platform of your data center:
Install connector in VMware and use the VM console for configuring the network
Install connector in OpenStack/KVM
Install connector in Microsoft Hyper-V
Install connector in Amazon Web Services (AWS)
Install connector in Google Cloud Platform (GCP)
Install connector in Microsoft Azure
Install connector in Docker for EAA Access Applications
Also, you can do security update for your connectors and have multiple connectors for applications for high-availability.
If you use a VM or cloud platform not included in the above list, or you need to allow service IPs to ensure connectivity with EAA connectors, please contact support.
Note:You can add connectors to Connector Pools and associate them to applications directly. For more information, see the limited availability feature, Associate Connector Pool to an Application.
Alternatively, you can associate your Connector Pools to an Application Access Group and associate Applications to the AAG. For more information, see our Beta feature, Application Access Groups (AAG).
Updated 2 days ago
