Application Access Groups (AAG)
Application Access Groups allow the admin to make common configuration changes in a single place and apply them to all resources like applications, directories, and Enterprise DNS. This greatly improves productivity and provides efficient management for connectors and applications.
Application Access Groups
An Application Access Group (AAG) is a group of EAA applications that are served by the same set of connectors in the Connector Pool to service the application traffic, and have the same Authentication and Authorization rules.
All of the connectors that serve the applications are associated with the same Connector Pool. When you make changes to the connectors, the changes are applied to the AAG. This makes it easier to manage your connector configuration changes. You do not have to add the connector to each of the applications, deploy the application.
If you need a common MFA policy for all of the applications in the AAG, it can be configured with an Identity Ruleset and applied to all of the applications in the AAG. It is not required to add authentication policies for each of the applications and deploy the applications individually, reducing the time required to configure authentication policy.
Also, if you need a common set of authorization rules for all your applications in the AAG, it can be configured with an Access Ruleset and applied to all of the applications in the AAG. You can specify all of the ACLs in EAA in the Access Ruleset and it can be applied to all of the applications. You do not have to add ACLs for each of the applications and deploy the applications individually, reducing the time required to configure ACLs.
In this way, managing connectors, authentication policies, and authorization rules in one place in the AAG and applying them to all the applications saves time and improves productivity.
Types of AAG
You can use different types of Application Access Groups (AAG) based on the type of applications that need to be grouped together.
There are three types of AAGs:
- Clientless Access Application. You can have Web (HTTPs), RDP, and SSH Applications in this AAG.
- Client-Access Application with Cloud Zone or Hybrid Transport. You can have TCP-type Client-Access Applications or Tunnel-Type Client-Access Applications or Tunnel-Type Client-Access Applications using Hybrid mode in this AAG.
- Client-Access Application with Edge Transport. You can have a Tunnel-type Client-Access Application using Edge Transport in this AAG.
You cannot combine clientless and client-access applications into the same AAG. SaaS applications cannot be added to AAG.
Comparison of stand-alone EAA Application versus Application associated with an AAG
- In an EAA Application, Connectors are added to Application in Settings tab in Applications Details Page:
When the Application is added to an AAG, the Connector Pool in the AAG serves traffic for the Application.
- In an EAA Application, the Authentication policies, MFA details are added to Application in Authentication tab in Applications Details Page:
When the Application is added to an AAG, the Identity Ruleset in the AAG provides the authentication policies and MFA details for the Application.
- In an EAA Application, the Access Control Lists (ACLs) or access control rules are added to the Application in Access tab in Applications Details Page:
When the Application is added to an AAG, the Access Ruleset in the AAG provides the ACLs for the Application.
AAG Workflow
The overall workflow is shown below:
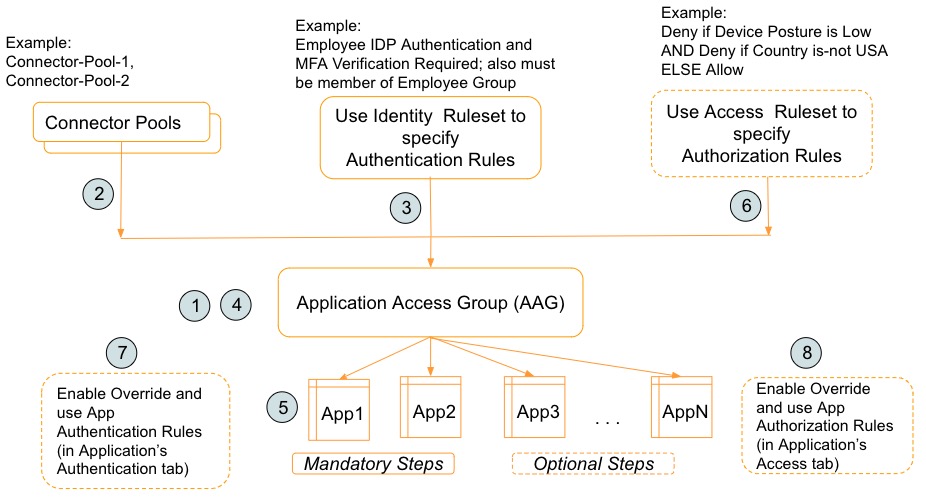
The high level steps are:
- Create the AAG.
- Associate one or more Connector Pools.
- Use Identity Ruleset to add Authentication Rules.
- Deploy the AAG.
- Associate Applications to the AAG and deploy all the Applications.
- Use Access Ruleset to add Authorization Rules (optional - Disabled by default) Deploy the AAG.
- Override the AAG’s Authentication Rules in any of your specific Apps (optional - Disabled by default) and deploy the specific Apps.
- Override the AAG’s Authorization Rules in any of your specific Apps (optional - Disabled by default) and deploy the specific Apps.
Configure AAG using the AAG wizard
STEP 1: Create an AAG
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Click on Add New Application Access Group.
- Provide these details:
- Application Access Group Name. Provide a name for the application access group.
- Description. Provide a meaningful description for the application access group.
- Application Type. Select one of the types: Clientless Access Application, Client-Access Application with Cloud Zone or Hybrid Transport, or Client-Access Application with Edge Transport. See Types of AAG and Access Ruleset for more details.
- Click Create Application Access Group. A blank wizard page is created. There are no Connector Pool, Identity Ruleset, or Access Ruleset in any of the tiles. Access Ruleset is disabled by default as shown below:
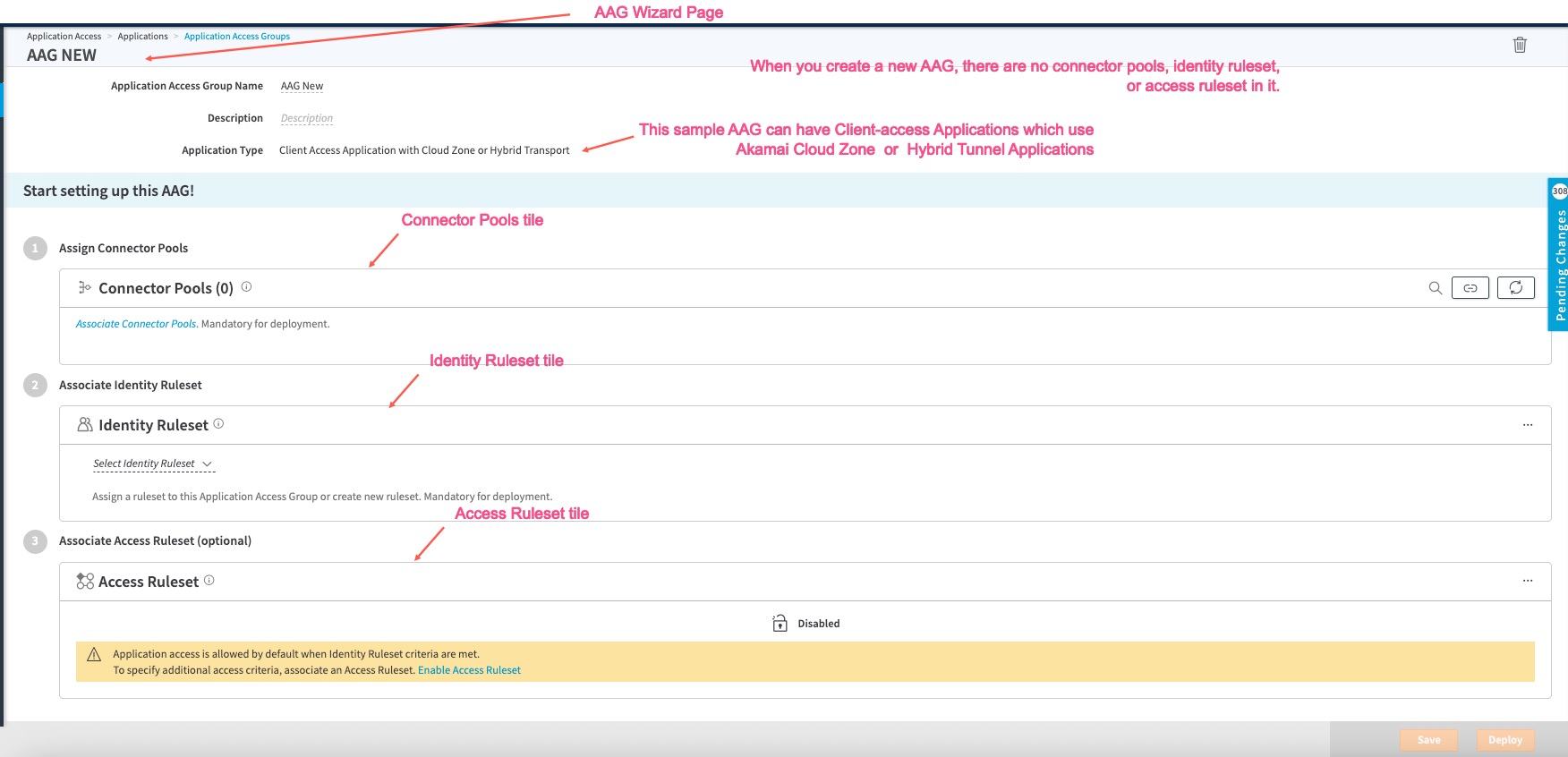
STEP 2: Associate Connector Pools to AAG
- If you’ve already created a Connector Pool, you can click Associate Connector Pools in the Connector Pool tile or click the Associate Connector Pools to the Application Access Group icon, select the Connector Pool or Connector Pools, click Associate. The Connector Pools appear in the Connector Pools tile, in the Application Access Groups page. All the connectors in the connector pool must be reachable. If you check the Deployment section on the right, AAG indicates it is not ready for deployment and if Connector Pool is okay and all connectors are reachable.
STEP 3: Create or assign a Identity Ruleset to the AAG
- Create an Identity Ruleset for the AAG. Or if you have an existing Identity Ruleset, you can assign it to this AAG using Manage Rulesets. click Select Identity Ruleset, select the ruleset you created.
STEP 4: Deploy the AAG
- Click the Deploy icon in the bottom right corner.
- You will see the AAG details page opens and it indicates the AAG is successfully deployed.
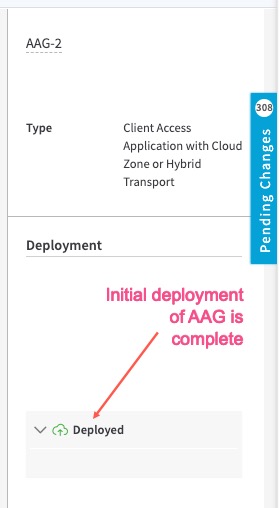
This completes the initial deployment of the AAG. Next you can add the applications to the AAG.
STEP 5: Associate Applications to the AAG and deploy them
- The AAG details page appears and the Applications tile is shown.
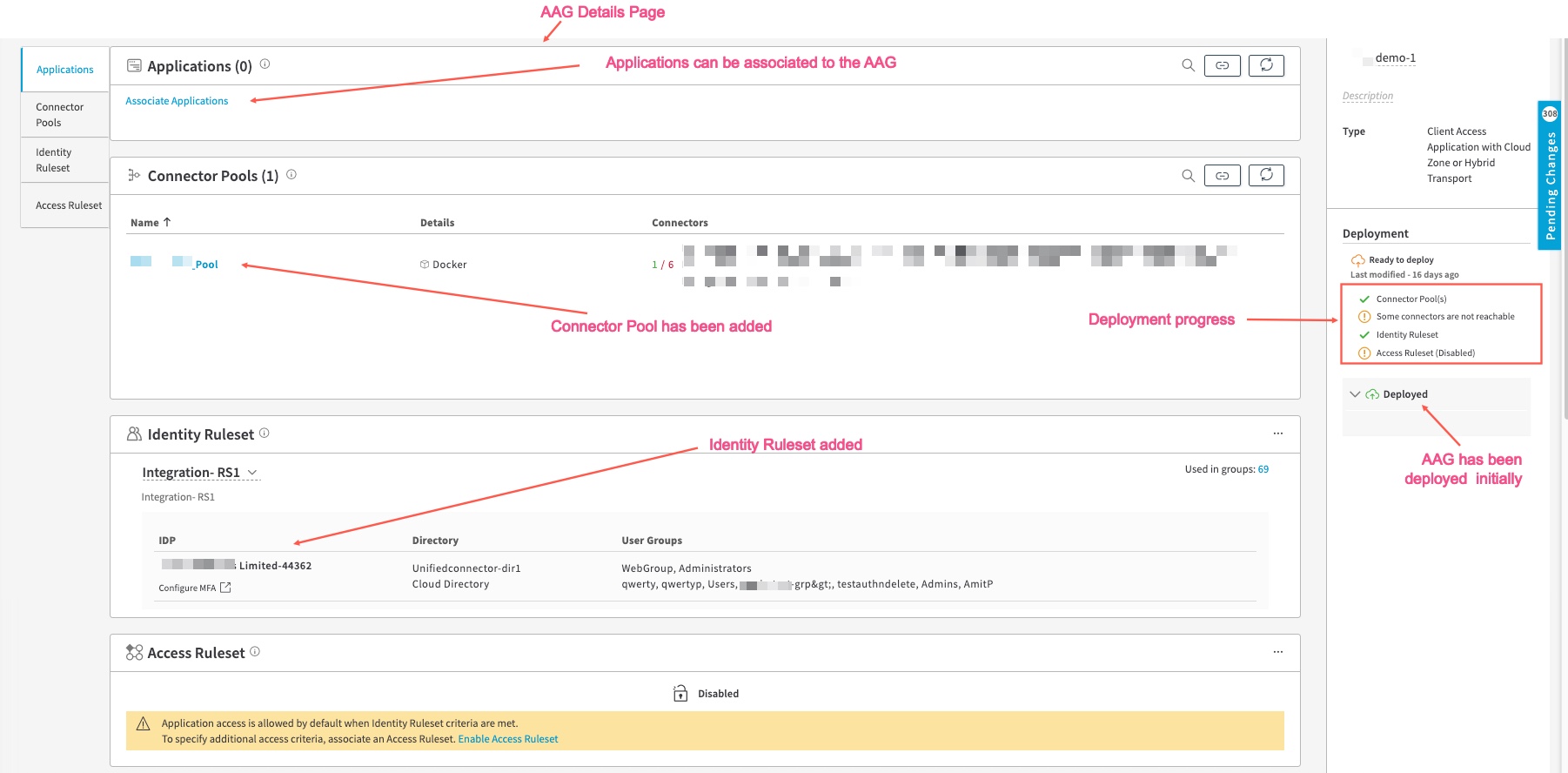
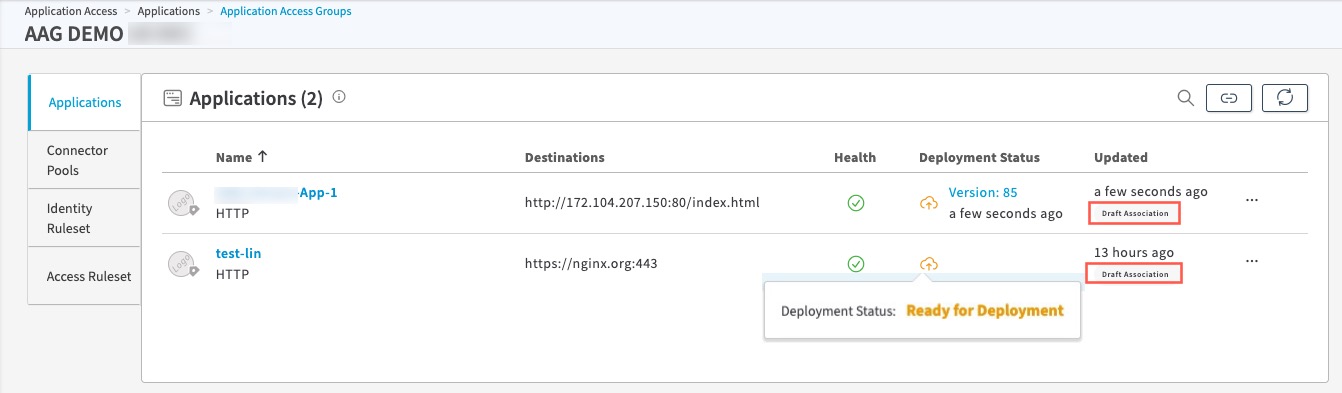
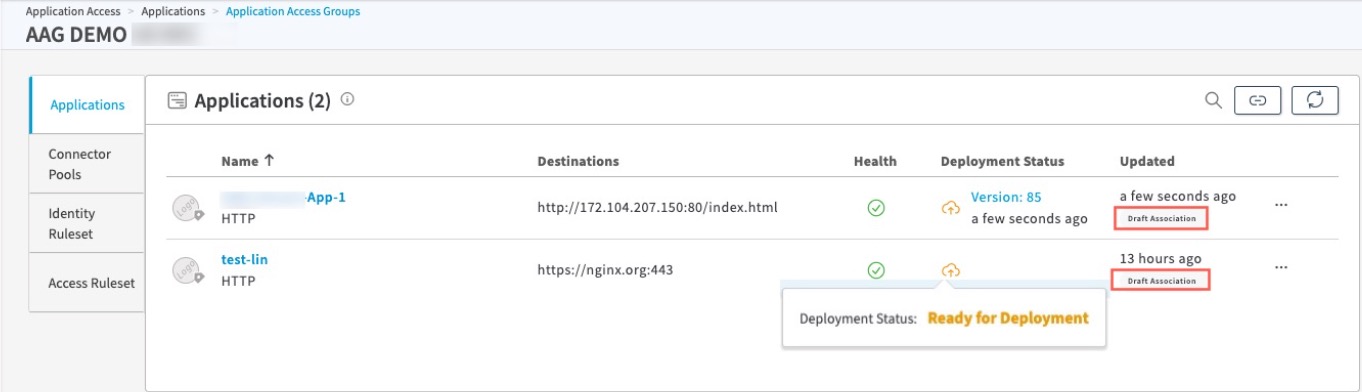
Associate Applications to the AAG. To associate applications with this AAG, click Associate in the Applications tile or click Associate Applications to the Application Access Group icon. You can select all of the Unassigned Apps by clicking the box next to it, or expand the Unassigned Apps by clicking the > mark, and individually selecting the unassigned applications in the Unassigned Apps list, or select other applications from other AAG or other AAGs. Then, click Associate. When an Application or Applications are associated with an AAG and the Applications are not yet deployed, they will appear in the “Draft Association” state.
For example, here we’ve associated two HTTP applications, App-1 and test-lin, from the Unassigned Apps to an AAG named AAG DEMO. Both are in the Draft Association state, to indicate that they must be deployed for the configuration changes to be propagated from the AAG to the Applications.
Note
If you go to any of the applications associated with an AAG that has an identity ruleset or access ruleset assigned to the AAG, and the AAG that has not yet been deployed, you will see (Draft) next to the AAG name to indicate that the AAG has to be deployed for the configuration changes to be applied to the Application.
If you want to associate other applications to the AAG, repeat this step till you have selected all of the applications that you want to associate with this AAG. All these applications will be serviced by the same connector pools, identity ruleset.
- Click the Deploy icon in the top right corner.
- The Pending Changes section opens up with the corresponding applications selected. Make sure they are all the correct applications and are selected in the Pending Changes window under Applications.
- Provide a Deploy Confirmation message.
- Click Deploy. The application deployment automatically triggers an AAG deployment. The AAG gets automatically deployed in all of the DPOP regions where the applications reside.The applications appear in the Applications tile of the Application Access Group as Deployment Status: App Deployed
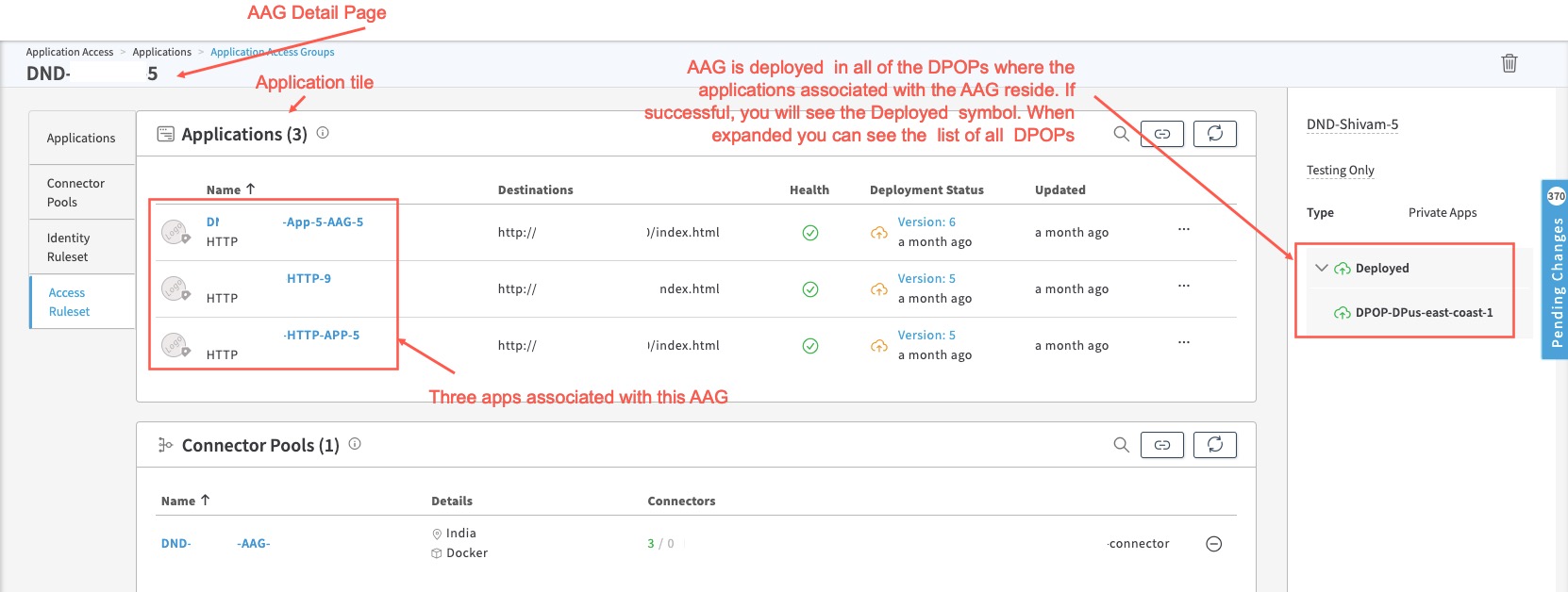
- Also, if you check the AAG detail page, you see the blue Deployed icon and when you expand it, the AAG also gets deployed on all the DPOPs where the applications associated with the AAG reside.

For example, this AAG is deployed on DPOP-DPus-east-coast-1 where the three applications associated with the AAG reside.
STEP 6: Create and assign an Access Ruleset to AAG (optional)
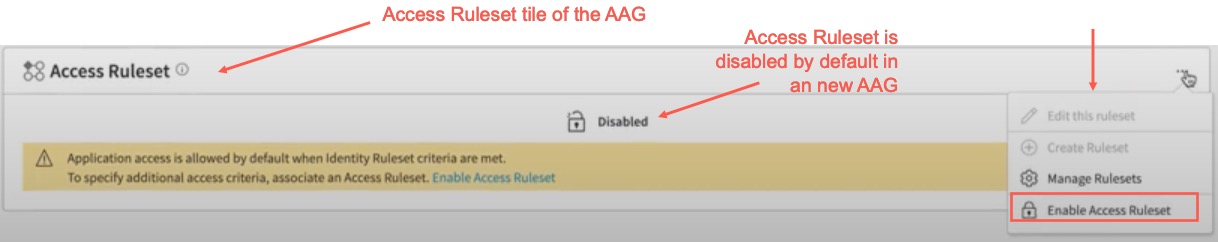
- (optional) If you want to assign an Access Ruleset, you must select Enable Access Ruleset (disabled by default in a new blank AAG) in the Access Ruleset tile of the AAG:
From the Select Access Ruleset pull down menu, select the Access Ruleset you want to assign to the AAG and click Save. To create a new Access Ruleset see Create an Access Ruleset for the AAG. Or if you have an existing Access Ruleset, you can assign it to this AAG using Manage Access Rulesets.
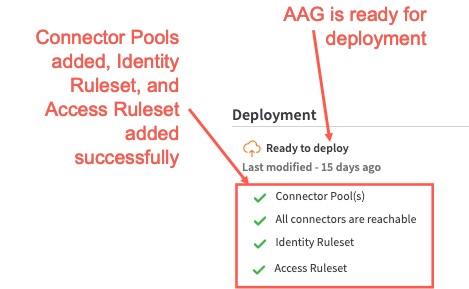
- If the access ruleset is okay, when you check the Deployment section on the right, the AAG indicates it is ready for deployment and a check mark appears next to Access Ruleset:
- Click the Deploy icon in the top right corner.
21.The Pending Changes section opens up with this AAG selected, click Deploy. - Provide a Deploy Confirmation message.
- Click Deploy. After the AAG is deployed, you will see a Deployment Status : Success in the AAG tile on the AAG list page. You can also see this in the AAG details page on the right, along with the DPOPs where it has been deployed.
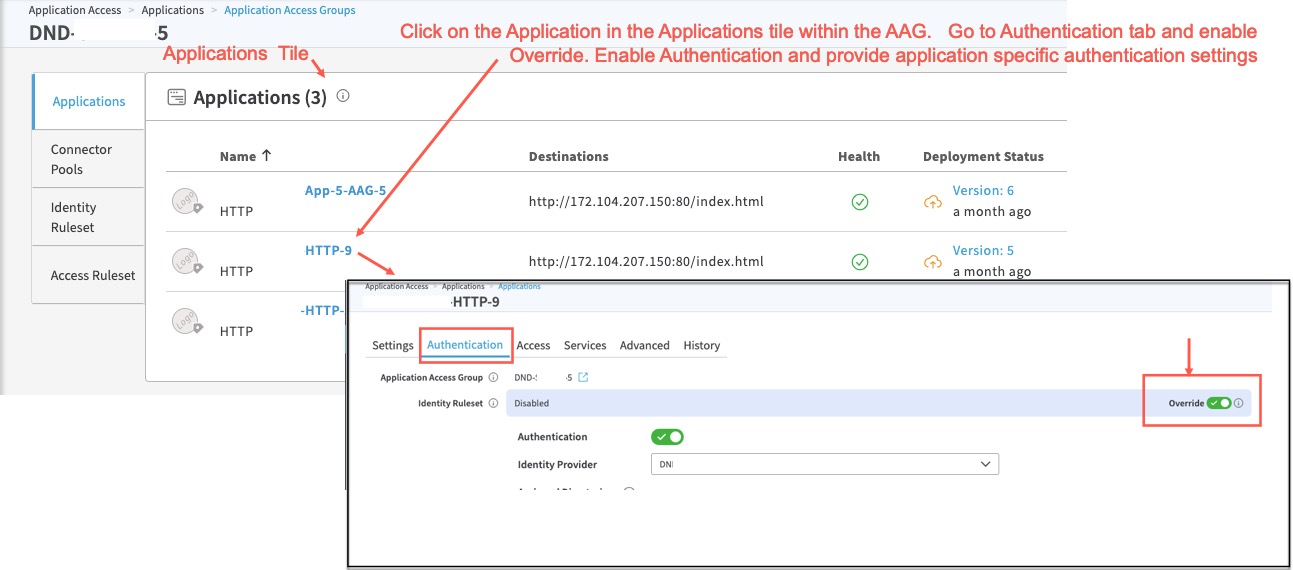
STEP 7: Override authentication rules for any specific apps in the AAG (optional)
- If you have any specific application in the AAG which should not have the authentication rules specified in the Identity Ruleset of the AAG, you can override the setting. Click on the Application within the AAG tile. Go to the Authentication tab. Enable Override. Enable Authentication. Configure any authentication settings specific for this application. You can then configure your MFA for each Application, or MFA for each directory or group associated with this Application.
Save and Deploy the application.
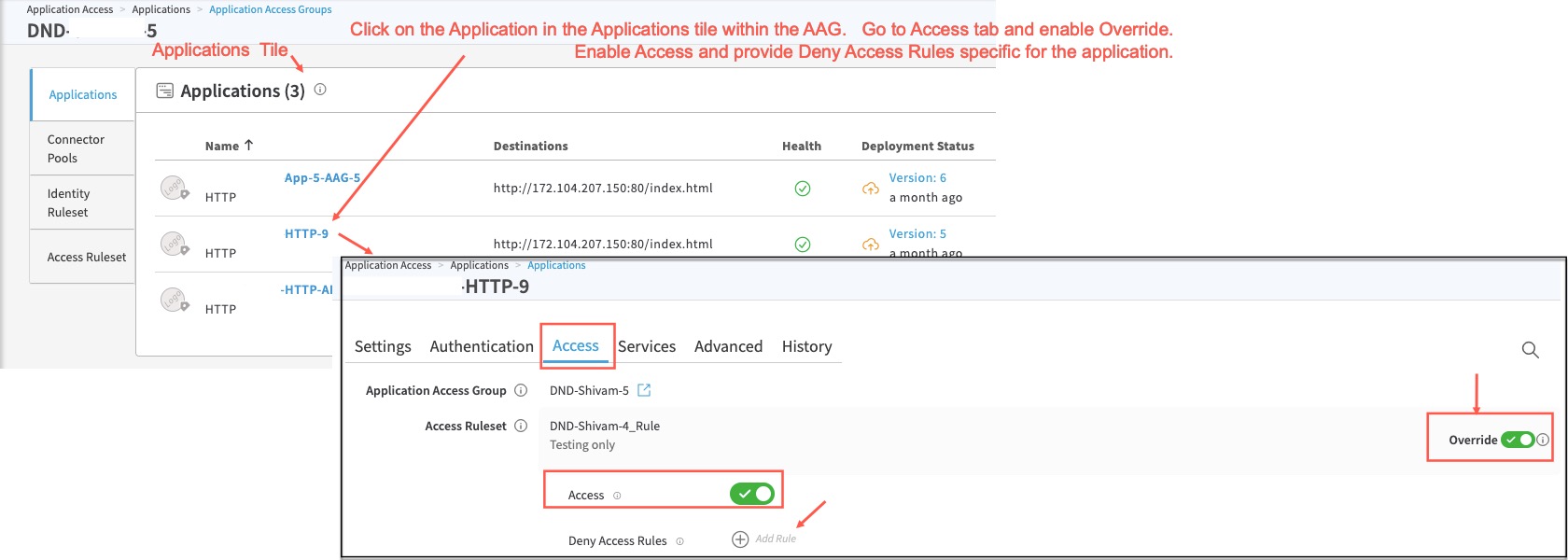
STEP 8: Override authorization rules for any specific apps in the AAG (optional)
- If you have any specific application in the AAG which should not have the authorization rules specified in the Access Ruleset of the AAG, you can override the setting. Click on the Application within the AAG tile. Go to the Access tab. Enable Override. Enable Access. Configure any ACL specific for this application Save and Deploy the application.
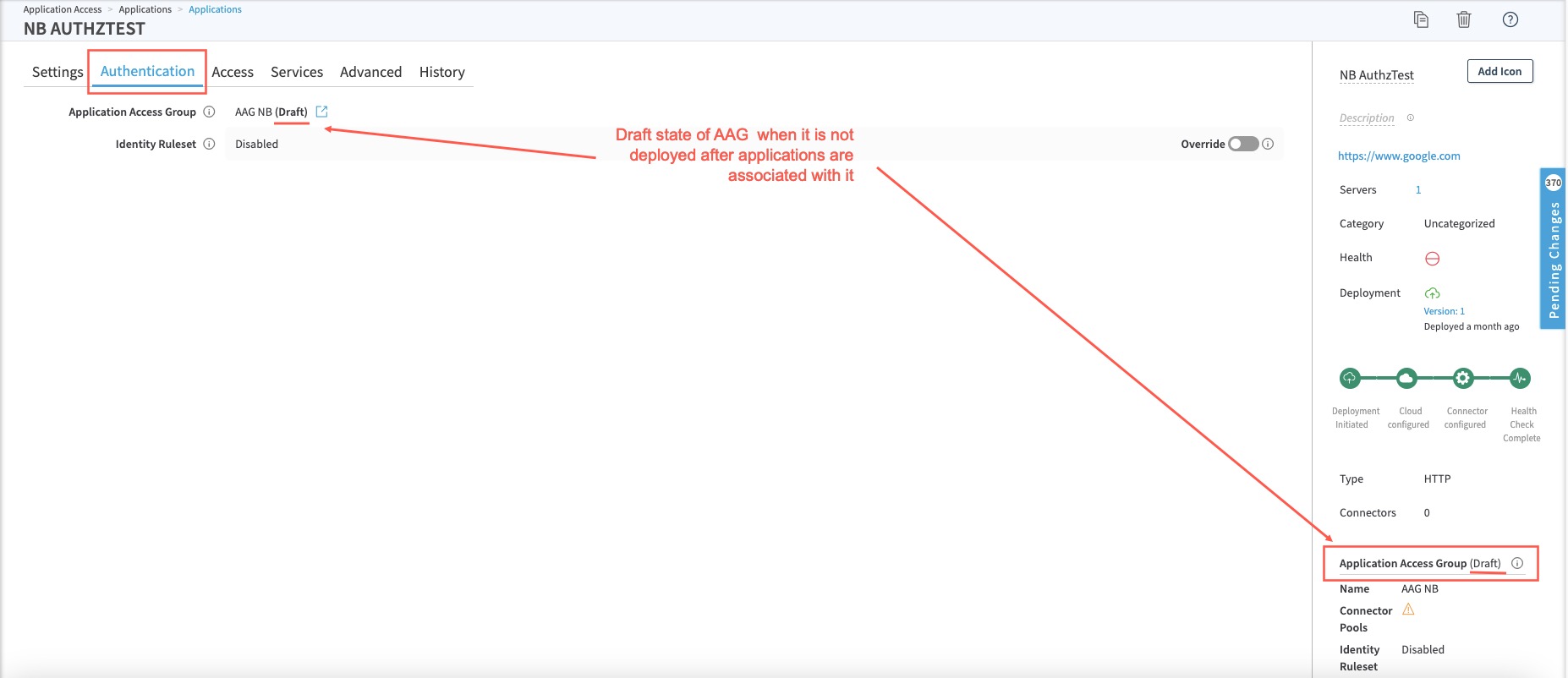
Draft Status of an AAG
If an application is associated with an AAG and the AAG is not yet deployed, you will know it is two ways:
a. If you go to the Application’s Authentication tab (if Identity Ruleset is assigned to the AAG) or Access Tab (if Access Ruleset is assigned to the AAG), you see (Draft) next to the AAG name.
b. If you go to the Application’s tile in the AAG page, you see Draft Association in the Updated column for the Application.
If all configurations are okay and you successfully deploy the AAG, the draft state will disappear in both places.
Identity Ruleset
Identity Ruleset in an AAG allows you to configure authentication policies that are applied to all applications associated with the AAG. It is mandatory to add an identity ruleset to an AAG. When you first configure a new AAG, there are no Identity rulesets present in the Identity Ruleset tile. You can create a new identity ruleset or assign an existing ruleset, if you created earlier for another AAG.
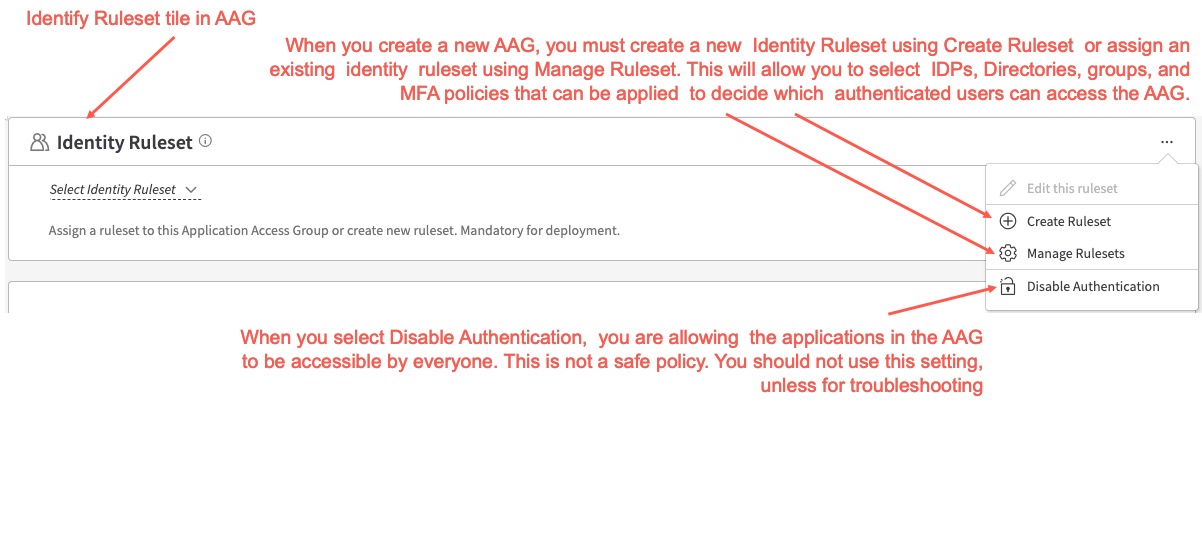
Note: If you disable the Disable Authentication setting for the Identity Ruleset tile, it means that there are no authentication policies set for the AAG, so everyone (even unauthenticated users) can access the application. Therefore you should not enable this setting unless it is for troubleshooting authorization issues.
Create Identity Ruleset
You can only have one Identity Rule associated with an Identity Ruleset.
To create a new identity ruleset follow this procedure:
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group.
- Go to the Identity Ruleset tile inside the AAG detail page.
- You can create an identity ruleset from three different places:
- From the Select Identity Ruleset menu select Create Ruleset
- From the Action menu (...) select Create Ruleset
- From the Select Identity Ruleset menu select Manage Rulesets, then select Create Ruleset.
- In the New Identity Ruleset Window, provide a Name, Description for the ruleset. Click Next>>.
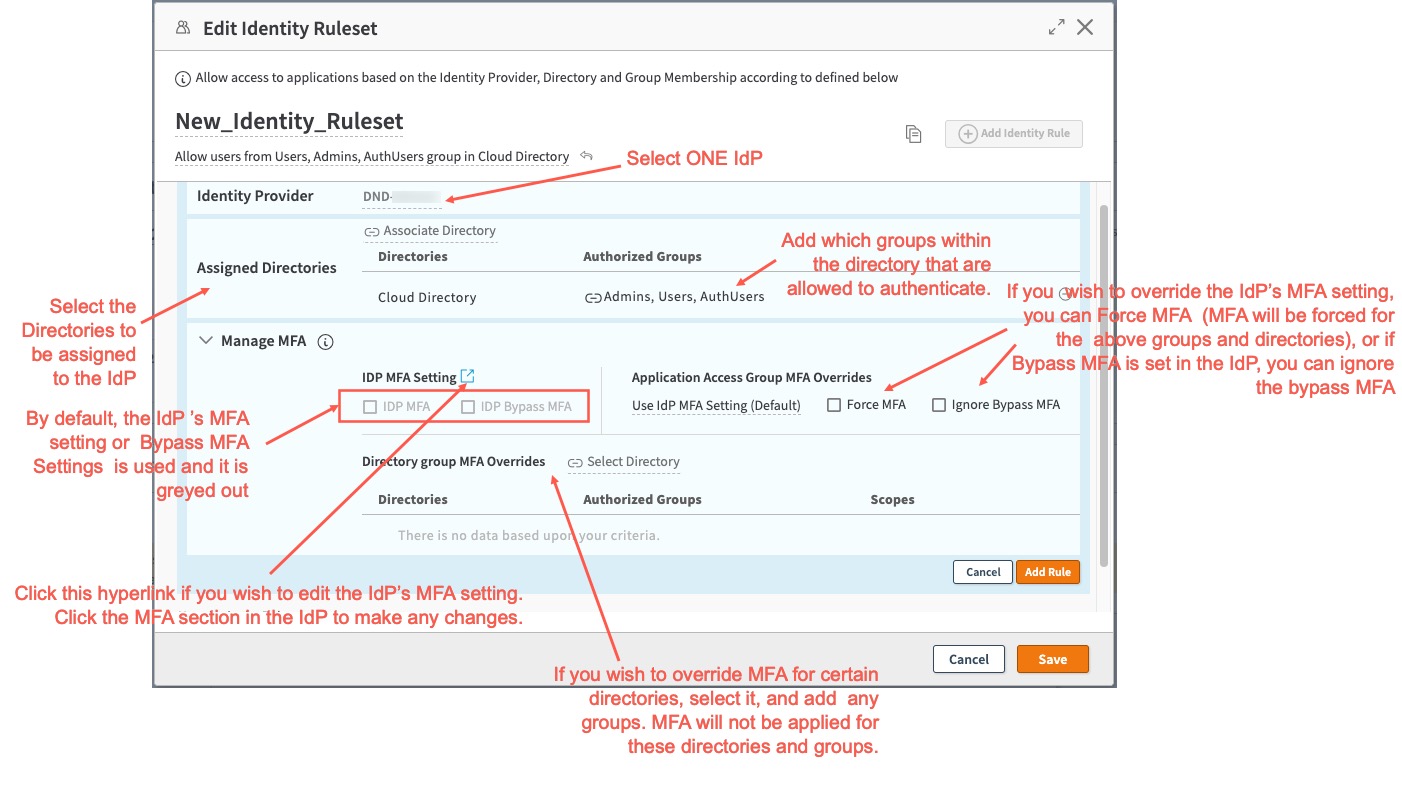
- Next you need to add the rules based on the identity provider, the directory, and group membership.
- Click Add Identity Rule
- For Identity Provider: Select an Identity provider. Note: EAA only supports one Identity Provider.
- For Assigned Directories: All directories assigned to this IdP are present. Click Associate Directory and select one or more directories that are allowed access to this AAG. Click Add Directory.
- Add desired groups to the directories: All groups of the directory are selected by default. Groups associated with each Directory can be edited under the Authorized Groups column, if required. Click Save, to add the desired groups. Check that the Authorized Groups are correct and are the ones needed to access the AAG.
- The Manage MFA section can be used to customize the MFA configuration for the rule. Click Manage MFA to expand it.
- Click Add Rule. A Rule is created and associated with the Ruleset. You can only associate one Rule with an Identity Ruleset.
- Click Save.
- In the Identity Ruleset tile, using the Select Identity Ruleset drop-down menu, select the ruleset you just created, expand it to check that all the authorization policies and permissions are correct, and it should be assigned to the AAG. You should see the IdP name, Directory name, and User Groups all listed under the ruleset name you created.
- Click Save in the bottom right corner of the AAG details page.
The Identity Ruleset is now assigned to the AAG.
Copy an Identity Ruleset from another application
If you have already created an identity ruleset for another AAG, you can copy it to another AAG, instead of creating a new one.
To copy the authentication rules from another application to a new identity ruleset follow this procedure:
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group.
- Go to the Identity Ruleset tile inside the AAG detail page.
- You can create an identity ruleset from three different places:
- From the Select Identity Ruleset menu select Create Ruleset
- From the Action menu (...) select Create Ruleset
- From the Select Identity Ruleset menu select Manage Rulesets, then select Create Ruleset.
- In the New Identity Ruleset Window, provide a Name, Description for the ruleset. Click Next>>.
- Click on Copy icon next to the Add Identity Rule
- All the EAA Applications that use this Identity Ruleset are shown. Search for the application from where you want to copy the Identity Ruleset containing the Authentication settings. Select the application. Verify the settings IdP, Directories, MFA settings are correct.
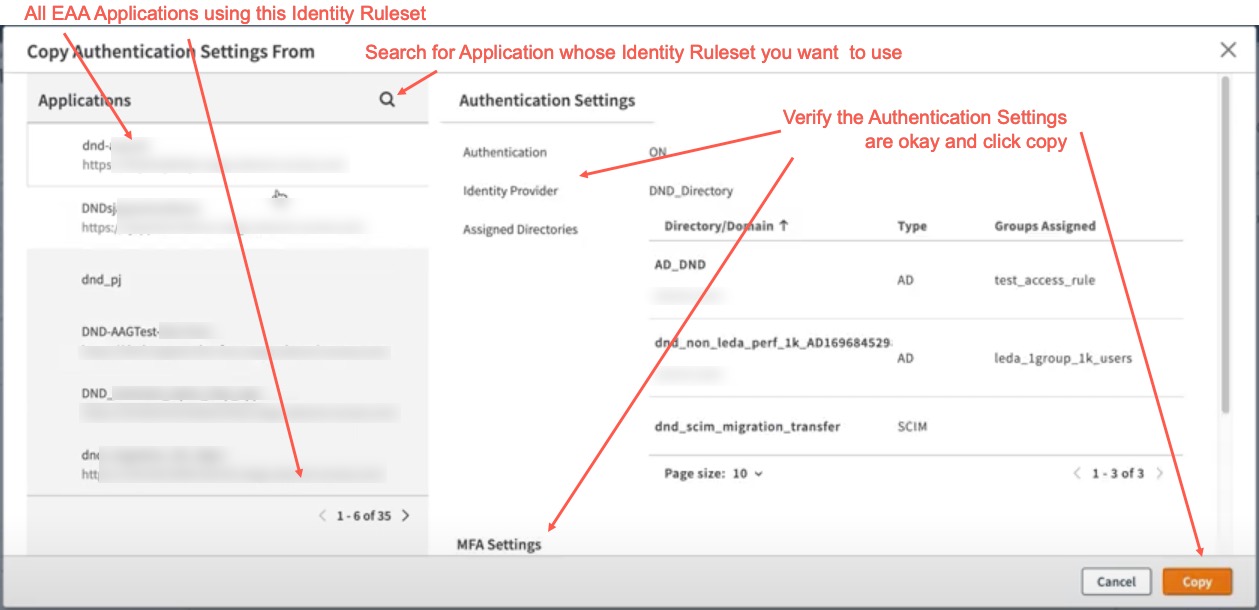
Click Copy, to populate the authentication settings into the Edit Identity Ruleset window, customize if needed (alter directories or groups). Click Add Rule, to associate this rule with this Identity Ruleset. Click Save to create this new rule set.
- In the Identity Ruleset tile, using the Select Identity Ruleset drop-down menu, select the ruleset you just created, expand it to check that all the authorization policies and permissions are correct, and it should be assigned to the AAG. You should see the IdP name, Directory name, and User Groups all listed under the ruleset name you created.
- Click Save in the bottom right corner of the AAG details page.
Manage Identity Ruleset
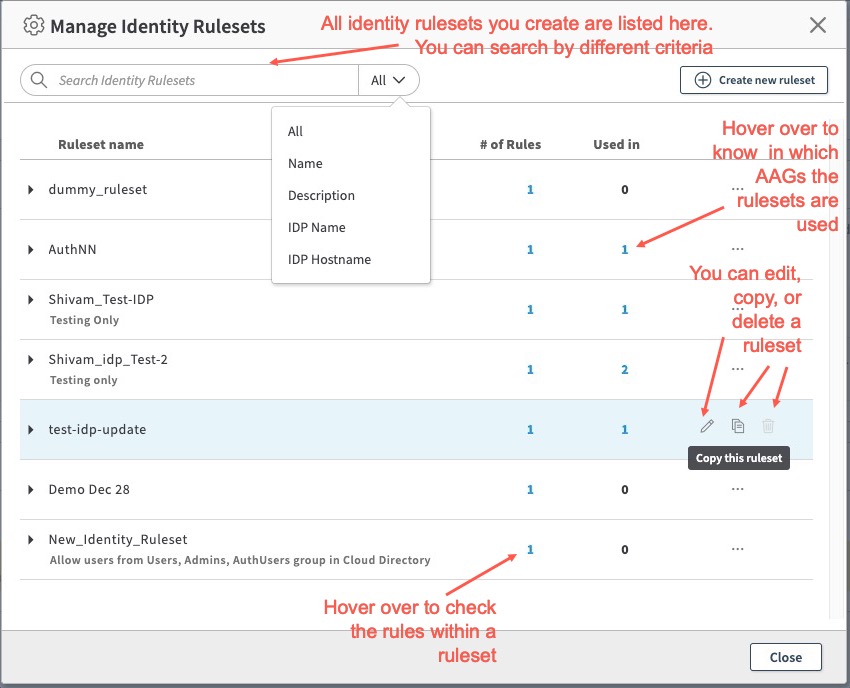
You can manage all of the Identity Rulesets you create using Manage Rulesets in the Identity Ruleset tile of the AAG detail page. It allows you to create, edit, and delete any of your rulesets and also see which rulesets are associated with which AAG, and which rules belong to a ruleset.
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group. You get to the AAG details page. You will see the Applications, Connector Pools, Identity Ruleset, Access Ruleset tiles.
- Go to the Identity Ruleset tile inside the AAG detail page.
- You can go to an Manage Ruleset from two different places:
- From the Select Identity Ruleset menu select Manage Rulesets
- From the Action menu (...) select Manage Rulesets.
- All of the rulesets you’ve created are shown. You can expand on each of the Ruleset to see the details of which IdP, directory, User groups are associated with the rule. You can click on the # under Used in column to see the number of AAG and names of the AAG that has this Ruleset. You can click on the # under the
# of Rules column, to see how many rules are in this Ruleset. - Click the pencil icon (Edit Ruleset) to edit the Ruleset and make any changes and click Save to save the Ruleset.
- Click the trash icon (Delete Ruleset) to delete the Ruleset.
- Click on the Copy this ruleset to copy it and paste it when you create a new ruleset.
- You can also create a new identity ruleset by clicking Create new ruleset inside the Manage Identity Rulesets window. Steps are the same as the Create Identity Ruleset, which has been described above.
- You can use the Search Identity Rulesets to search the Identity Ruleset by Name, Description, IdP Name, or IdP Hostname.
Access Ruleset
Access Ruleset in an AAG allows you to configure authorization policies (or access control list or ACLs) that are applied to all applications associated with the AAG. By default, if there are no ACLs, it is an Allow All policy, provided Identity Ruleset criteria is met. Therefore if you wish to add additional access rules like, for example, users from a certain country or a specific time zone or users accessing the AGG from devices with low risk device posture tiers or tags, or more you can add them with Access Ruleset. If you do not specify any Access Ruleset within the AAG, you will still be able to deploy the AAG, provided Connector Pools are added to AAG and Identity Ruleset criteria is met. Therefore when you first configure a new AAG and go to the AAG details page, you see that Access Ruleset is disabled by default. You can click Enable Access Ruleset in the Access Ruleset tile or click the Enable Access Ruleset icon.
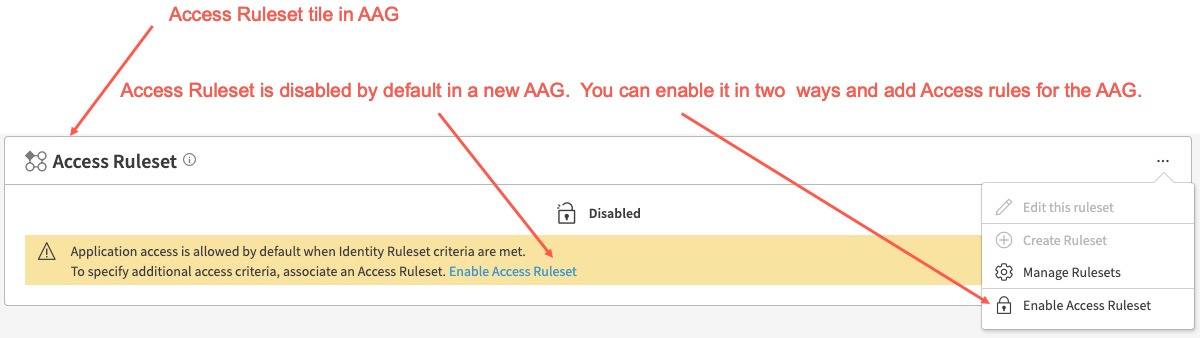
The rules in a ruleset are evaluated from top to bottom.
Types of Access Ruleset
You can create Access Ruleset and use them in your AAG. You can create different types of Access Ruleset based on what Access Control Types you wish to use for controlling authorization policies for your applications within the AAG.
If you want to use the Access Ruleset only in Clientless Applications, select the Access Ruleset Type of Clientless. This allows you to select access control types of Url, Group, User, Method, Client IP, Country, Time, Device Risk Tier, and Device Risk Tag.
If you want to use the Access Ruleset only in Cliented Applications, select the Access Ruleset Type of Cliented. This allows you to select access control types of Group, User, Client IP, Country, App Host, App Port, App Protocol, Device Risk Tier, and Device Risk Tag.
If you want to use the Access Ruleset only in both Clientless and Cliented Applications, select the Access Ruleset Type of All Apps (Default). This allows you to select access control types which are common to both Cliented and Clientless Application which include Group, User, Client IP, Country, Device Risk Tier, and Device Risk Tag.
Access Ruleset Types that can be used within AAG Types
This table describes what types of Access Ruleset Type is allowed within which AAG type:
| AAG Type | Allowed Access Ruleset Type |
|---|---|
| Clientless Access Application | Clientless All Apps |
| Client Access Application with Cloud Zone or Hybrid Transport | Cliented All Apps |
| Client Access Application with Edge Transport | Cliented All Apps |
Create Access Ruleset
You can only have one Access Rule associated with an Access Ruleset.
To create a new Access Ruleset follow this procedure:
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group.
- Go to the Access Ruleset tile inside the AAG detail page.
- You can create an access ruleset from three different places:
- From the Select Access Ruleset menu select Create Ruleset
- From the Action menu (...) select Create Ruleset
- From the Select Access Ruleset menu select Manage Rulesets, then select Create Ruleset.
- In the New Access Ruleset window provide a Name, Description , Type for the ruleset. Click Create Ruleset. You see a blank Rules page with a Default Rule of Allow, with no other rules in it. Refer to Access Ruleset Types and Access Ruleset Types that can be used within AAG types for more information.
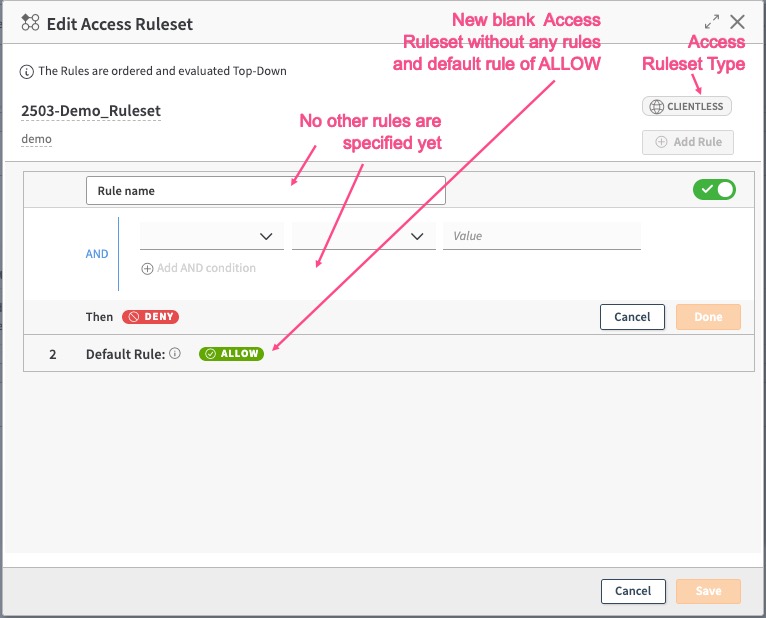
Note
If you save this Access Ruleset with no specific access rules created and assign it to the AAG in the Access Rule set tile, then since only the default rule is ALLOW, if the identity ruleset conditions are met, users will be able to access the application, with not additional access rules condition. To add additional DENY access rules, see next step.
- Provide a Rule Name.
- The Rules within the Ruleset are evaluated Top-Down. You can specify DENY rules by specifying parameter, is or is not, value. You can also AND multiple rules.
Here are a few examples of different types of Access Ruleset Types that can be used in different types of AAG:
In this example, the web application is denied access when the URL path contains /foreign/ in it. It can be used in AAG of type Clientless Access Application.
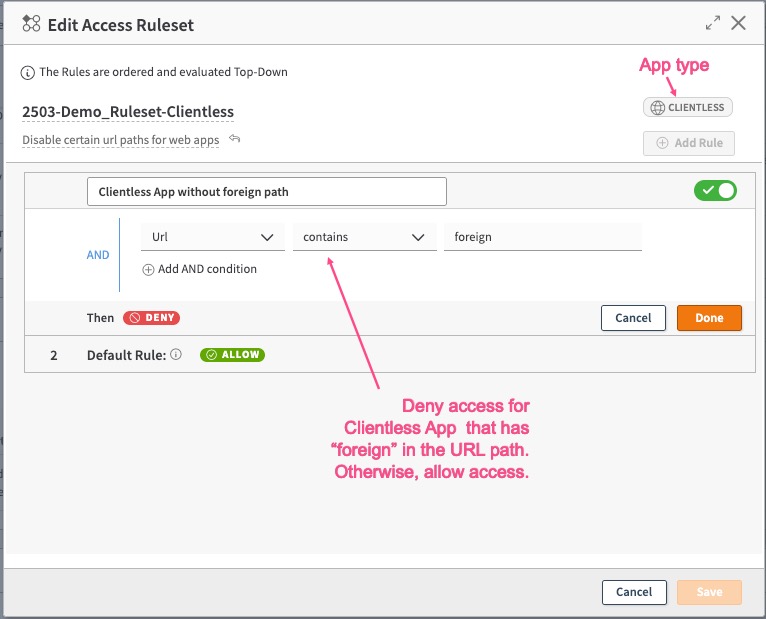
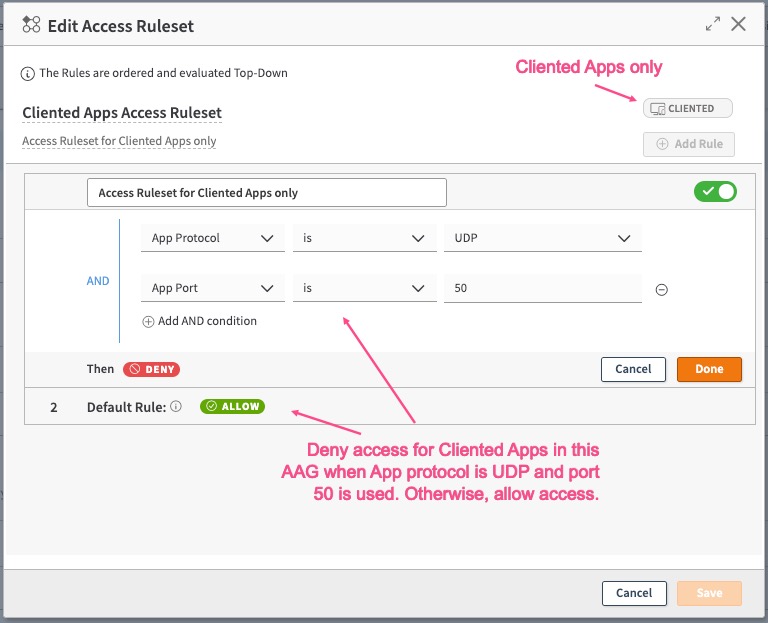
In this example, access is denied to Cliented Applications when the App Protocol is UDP and the port is 50. It can be used in AAG of type Client Access Application with Cloud Zone or Hybrid Transport or Client Access Application with Edge Transport.
In this example, access is denied to either Clientless or Cliented Applications when access is from a high risk device from Afghanistan. It can be used in any of the AAG types, namely Client Access Application with Cloud Zone or Hybrid Transport, Client Access Application with Edge Transport, or Clientless Access Application.
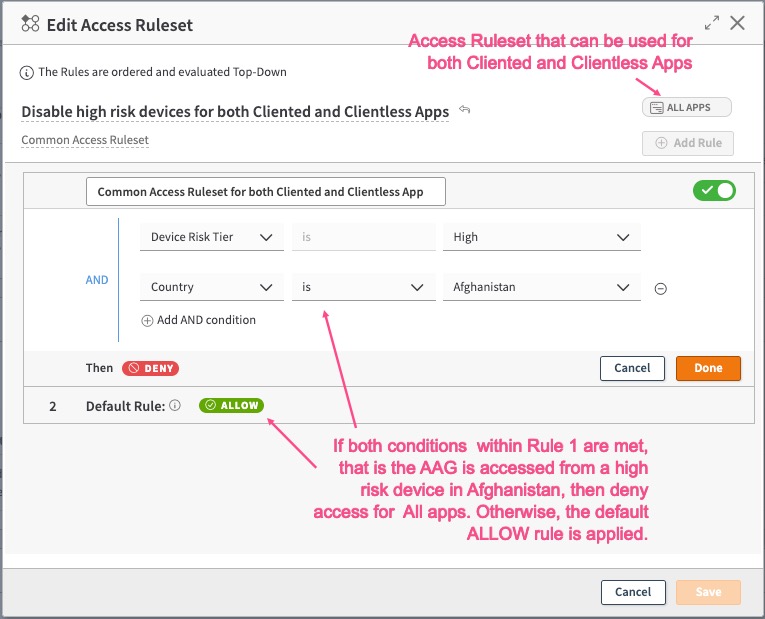
- Click Done. This associates the rule with the ruleset. Click Save.
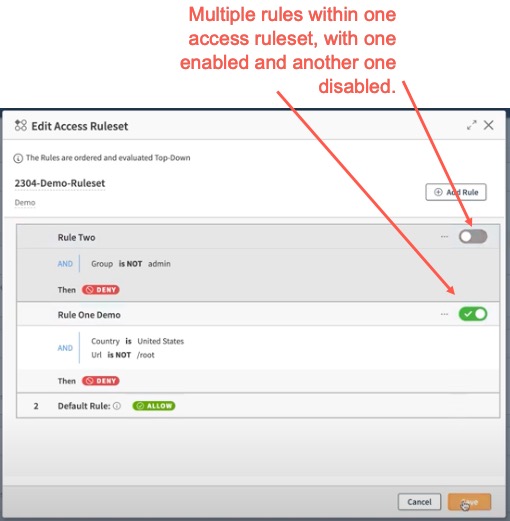
- You can similarly add multiple rules by clicking Add Rule. The rules are evaluated top-down, with the topmost rule having the highest priority.
For example, here we have two rules created within the ruleset, with Rule Two disabled and Rule One demo enabled, in the 2304 -Demo-Ruleset:
- In the Access Ruleset tile, using the Select Access Ruleset drop-down menu, select the ruleset you just created. Check that the rules are correct and click Save.
The ruleset is displayed in the Access Ruleset tile of the AAG.
Manage Access Ruleset
You can manage all of the Identity Rulesets you create using Manage Rulesets in the Identity Ruleset tile of the AAG detail page. It allows you to create, edit, and delete any of your rulesets and also see which rulesets are associated with which AAG, and which rules belong to a ruleset.
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group. You get to the AAG details page. You will see the Applications, Connector Pools, Identity Ruleset, Access Ruleset tiles.
- Go to the Access Ruleset tile inside the AAG detail page.
- You can go to an Manage Ruleset from two different places:
- From the Select Access Ruleset menu select Manage Rulesets
- From the Action menu (...) select Manage Rulesets.
- All of the rulesets you’ve created are shown. You can expand on each of the Ruleset to see the details of which IdP, directory, User groups are associated with the rule. You can click on the # under Used in column to see the number of AAG and names of the AAG that has this Ruleset. You can click on the # under the # of Rules column, to see how many rules are in this Ruleset.
- Click the pencil icon (Edit Ruleset) to edit the Ruleset and make any changes and click Save to save the Ruleset.
- Click the Delete this ruleset icon (trash) to delete the Ruleset. A Ruleset can be deleted only if it is not associated with any AAG. If the ruleset is associated with any AAG, it is grayed out and cannot be deleted. When clicked, a confirmation message is shown, select Yes, delete this Ruleset, to delete it.
- Click the Copy this ruleset icon to Copy a Ruleset. It opens the ruleset in an editable window and admin can customize if required like changing the rule name, adding a rule, deleting a rule using the edit (pencil) icon and delete (trash) icon. Then click Save, to save the copied ruleset.
- You can also create a new identity ruleset by clicking Create new ruleset inside the Manage Identity Rulesets window. Steps are the same as the Create Identity Ruleset.
- You can use the Search Access Rulesets to search the Access Ruleset by Name, Description,Rule Name, or Type in the Manage Access Rulesets.
Disable Access Ruleset
By default in EAA if you do not configure any ACLs, the default is Allow All types to traffic to the applications. Therefore we require the admin to know that this will be the access rule for the applications in the AAG when you set Disable Ruleset in the Identity Ruleset tile of the AAG details page. If you don’t enable this option, then you will be required to configure at least one Identity Ruleset before you deploy the AAG.
Deployment-ready conditions for an AAG
For an Application Access Group to be deployment ready, any of the three conditions must be met:
i) At least one Connector Pool must be associated with the AAG
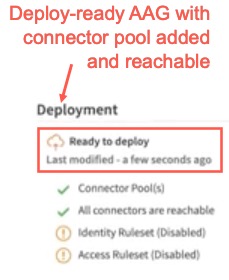
ii) A valid Identity Ruleset must be associated with the AAG. If you have not assigned a valid Identity Ruleset, you can disable it, to make the AAG deployment ready.
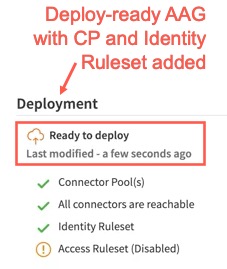
Note: This is not safe to disable the Identity Ruleset, since you are making your applications available to anyone who does not authenticate, since there are not authentication rules configured.
iii) A valid Access Ruleset must be associated with the AAG. If you have not assigned a valid Identity Ruleset, it can be left in the default state, which is Disabled (in any new AAG) to make the AAG deployable.
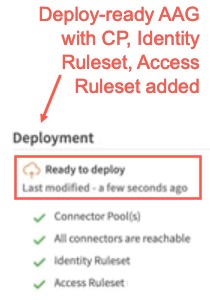
If any of these conditions are met, the AAG will be in Ready to deploy state and it can be deployed.
Delete an AAG
You cannot delete an AAG when you have active resources like Connector Pools, Applications, Identity Ruleset, and Access Ruleset associated with it. You can delete an AAG only after you remove all of the active resources.
Follow this procedure to remove any active resources and delete the AAG:
- Log in to the Enterprise Center.
- Navigate to select Application Access > Applications > Application Access Groups.
- Select the AAG from the AAG list page by clicking the pencil icon, Edit Application Access Group. You get to the AAG details page. You will see the Applications, Connector Pools, Identity Ruleset, Access Ruleset tiles. You get to the AAG details page.
- Go to the Connector Pools tile, click Dissociate (- icon) next to each connector in the connector pool. The connector does not server traffic for the applications any more. Repeat this for any other connectors in the Connector Pool.
- Go to the Applications tile, click Dissociate next to each application.
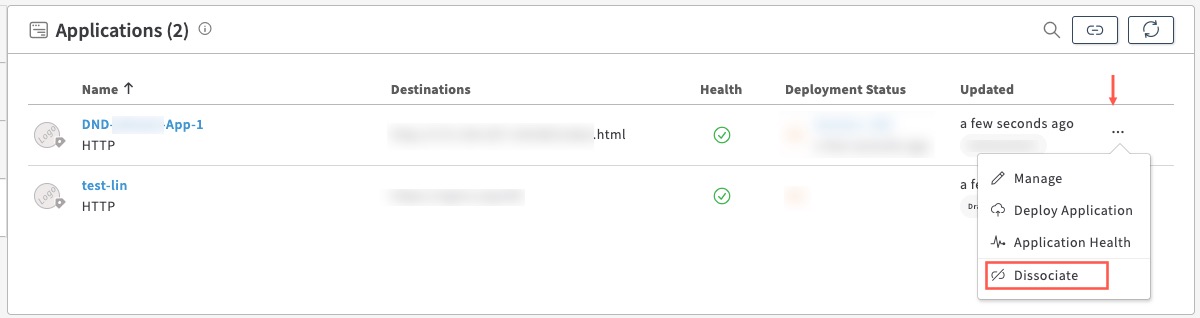
For Dissociate Application, enter Yes. Repeat this for all the applications in the Applications tile.
- Go to the Identity Ruleset tile and select Disable Authentication. For the dialog box , Are you sure you want to disable Authentication, select Disable.
- Go to the Access Ruleset tile and select Disable Authorization. For the dialog box , Are you sure you want to disable Authorization, select Disable.
- Click Save to save the AAG with all the changes.
- For Do you want to delete AAG, enter Yes.
The AAG is deleted and removed for the AAG list page.
Create a New Application and add to an AAG
You can create a new EAA Application and add it to an existing AAG. The Application inherits the Connector Pools, Identity Ruleset, and Access Ruleset from the AAG.
Follow this procedure to add a new Application to an existing AAG:
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Click Add Application (+).
-
Enter type, application name, and an optional description.
-
Click Add Application.The application configuration page opens.
-
Add all of the App Settings, Server Settings as described in Configure Access parameters for an Application.
-
Go to the Connectivity, Authentication and Access section. Select the Application Access Groups
-
Select the AAG you wish to use for this application by selecting the drop-down Select Application Access Group and picking the AAG from the list. Click Associate.
-
Select if you want to Use the Identity Ruleset, Access Ruleset of the AAG or use the Application’s Authentication Settings and Applications Access Settings in this dialog:
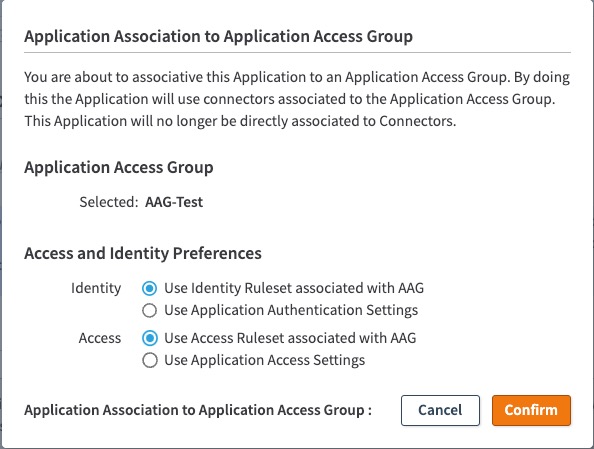
- You have two options:
1. If you selected, “Use Identity Ruleset associated with AAG” and “Use Access Ruleset associated with AAG”, the Connector Pools, Identity Ruleset, and Access Ruleset from the AAG is used for this application. It is displayed under the Application Access Group section:
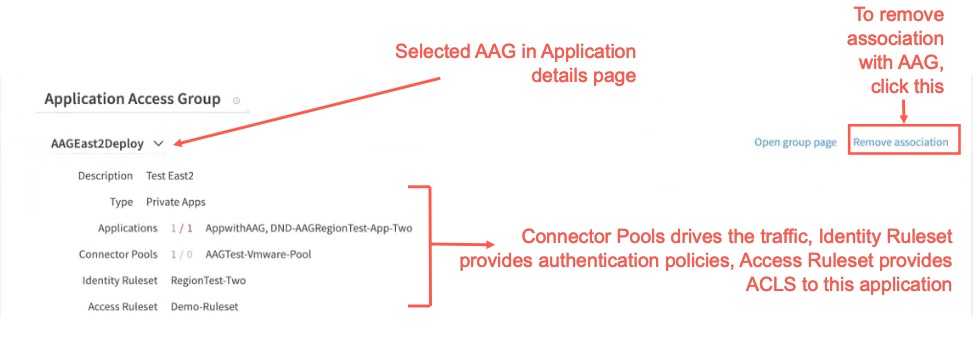
Note:
a) If you do not wish to associate the application with the AAG, click Remove association. In the dialog box, Remove Association Confirmation, click Remove.
b) If the AAG association is removed, the Connectors section appears. Click Add connector. Select one or more connectors and click Add Connector. The associated connector appears in Connectors.
b. If you selected “Use Application Authentication Settings” and “Use Application Access Settings”, you will see the Identity Ruleset, Access Ruleset as “Disabled Overridden” for the Application under the Application Access Group section:
![]()
Note:
You can also select the option to use either the “Use Identity Ruleset associated with AAG” or “Use Access Ruleset associated with AAG”, if you want only the authentication rules or Access control list from the AAG.
- Click Confirm.
- Click the Authentication tab. If you selected Use Identity Ruleset associated with AAG, the authentication policies coming from the AAG are shown. If you select Use Application’s Authentication Settings, you can configure Authentication for your application. See Step 8 in Configure access parameters for an application.
Note. An Application inherits the AAG's Identity Ruleset after association. The configuration is preserved in the Application unless you override it manually. (basically turn on the Override setting in the Authorization tab, and perform Edit Ruleset manually).
- Click the Access tab. If you selected Use Access Ruleset associated with AAG, the ACLs coming from the AAG are shown here. If you select Use Application’s Access Settings, you can configure the ACLs. See Step 9 in Configure access parameters for an application.
Note. An Application inherits the AAG's Access Ruleset after association. The configuration is preserved in the Application unless you override it manually. (basically turn on the Override setting in the Access tab, and perform Edit Ruleset manually).
- You can set up the Services, Advanced settings like any Access Application (step 10)
- Click Save and Deploy, to save and deploy the changes.
If you go to the AAG details page, this application that’s added to the AAG will be listed with other applications.
Limitations
- Identity Ruleset is not updated when Directory Verification Required is disabled on an third-party IdP, so does not work with third-party IdP.
- If you are using a docker-based connector, you cannot use the same connector pool for both clientless (HTTP, RDP, or SSH) apps and cliented (TCP-type client-access, Tunnel-type client-access) apps.
You must have two different AAGs:
- Have one AAG for clientless apps serviced by a docker based connector pool containing only docker based connectors configured for clientless traffic.
- Have one AAG for clientled apps serviced by a docker based connector pool containing only docker based connectors configured for clientled traffic.
Updated 2 months ago
