MFA for third-party Identity provider
Note:
This feature is currently in Limited-Availability (LA) and can be enabled in your contract by contacting Akamai Support.
EAA supports multi-factor authentication (MFA) for SAML based identity providers like Okta, Microsoft Azure AD, PingOne, OneLogin, and Third Party SAML providers. MFA is not supported for Third Party OIDC and Google identity providers.
You can only use either Akamai MFA, Duo MFA, or both as the MFA methods for third party identity providers. If you select both, the end users can select the primary method to receive the MFA tokens on their second factor device after registration.
Enable MFA for third-party Identity provider
You can use MFA with third party SAML based identity providers like Okta, Microsoft Azure AD, PingOne, OneLogin, and Third Party SAML providers.
Follow this procedure to enable MFA:
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Select the third party identity provider to open it. It can be Okta, Microsoft Azure AD, PingOne, OneLogin, or Third Party SAML providers.
-
Click the Directories tab. Click Add Directory. Select the third-party Okta Directory, Azure Cloud Directory, or LDAP associated with your third party identity provider. Click Add Directory.
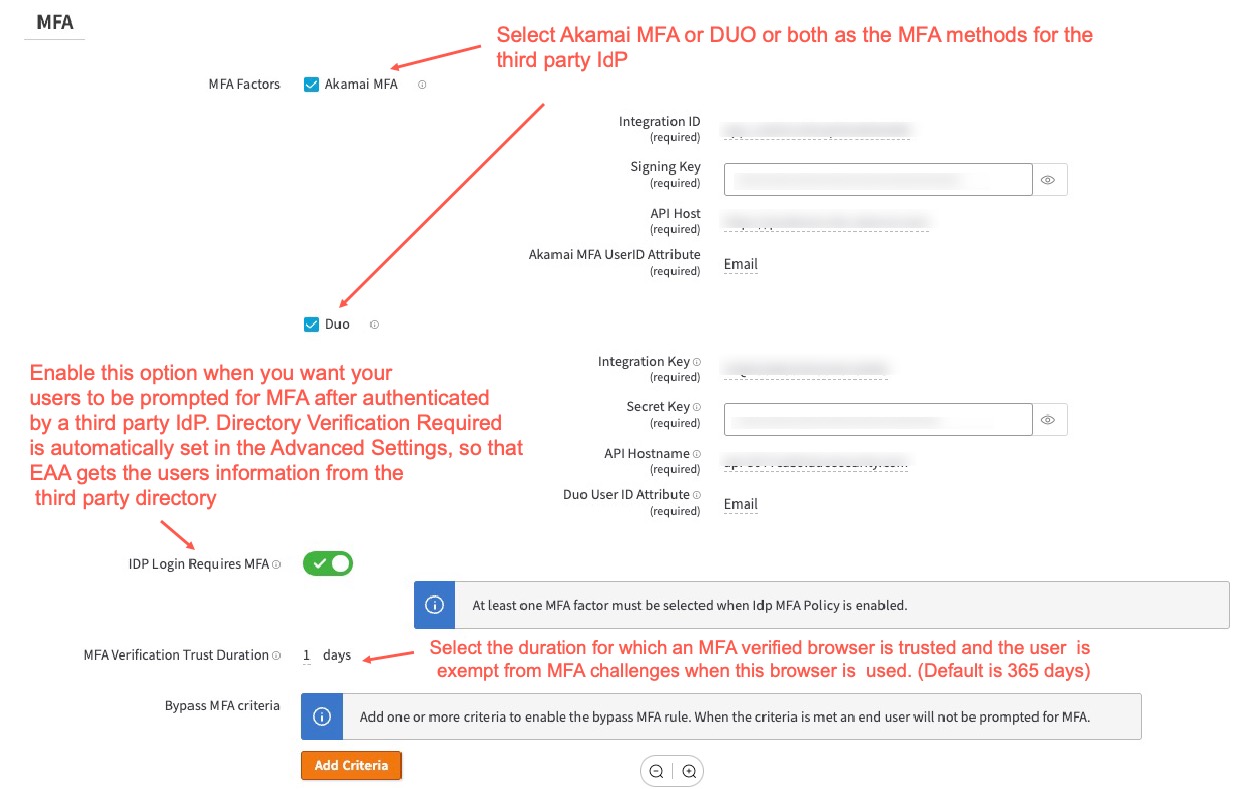
-
In Settings > MFA enable IDP Login Requires MFA. This should automatically enable Directory Verification Required in the Advanced Settings. This allows EAA to sync users and apply MFA policies to the users in the third-party directory.
-
Select any of the MFA factors to apply like Akamai MFA or Duo. You can select one or both of these MFA methods:
- For DUO, see Use Duo MFA.
- For Akamai MFA see Use Akamai MFA.
If you select both Akamai MFA and Duo, the end-user will see both these two MFA methods. They can follow the onscreen guidance to select the primary method and the backup methods for receiving MFA tokens for authentication.
-
Set MFA Verification Trust Duration. The user is prompted for MFA verification the very first time they use the browser. Then, within the trust duration period, the user is exempt from MFA challenge if they use the same browser. The default is 365 days.
-
Click Save.
-
Deploy the identity provider.
Note: The Application level MFA, Directory level MFA can be applied within EAA. The inheritance rules are the same as Akamai IdP.
Updated 11 months ago
