Configure Device Posture integrations
On the Device Posture Integrations page, you can configure the third-party integrations.
You can configure up to 12 entities for CrowdStrike or VMWare Carbon Black signals. Each entity can be a newly acquired company or sub-organization of the parent organization. Configuring entities allows the parent organization to use the acquired company's credentials, and use the device posture signals for device posture reports for all users including the acquired company, till the acquired company is integrated into the parent organization.
Important Note
Device posture integration has been tested with VMware Carbon Black signals for a single entity. However, you may be able to use up to 12 entities. If you have any issues, contact Akamai Support for assistance. However, Device posture integration has fully tested to support up to 12 entities for CrowdStrike signals.
Integrate with CrowdStrike
With the CrowdStrike integration, you get access to additional signals that you can use to monitor corporate devices and allow or deny application access. CrowdStrike offers Falcon cybersecurity software for endpoint devices.
With the EAA-Crowdstrike integration, you can use Device Posture to calculate the status of the CrowdStrike Agent (CrowdStrike Falcon sensor) running on the user's device. The Agent's status can be reported as healthy if the CrowdStrike Agent is running on the device and communicating regularly with the CrowdStrike server, or unhealthy if the Agent is inactive. The CrowdStrike Agent status is included in the Device Posture security evaluation.
CrowdStrike data that you can monitor in the Integration tab of the Device Details report:
| CrowdStrike Signal | Description |
|---|---|
| AID (Agent ID) | Identifies each installation of a Falcon sensor. If the sensor is updated or reinstalled, the host gets a new AID. For this reason, a single host can have multiple AID values over time. Agent ID is also called a Sensor ID. |
| CID (Customer ID) | Identifies your company's account with CrowdStrike. |
| AID/CID Status | Displays a status based on the validity of the AID and CID in the CrowdStrike cloud. If AID and CID are valid this signal returns a valid value, otherwise, its value is invalid. |
| Version | Reports the current version of the CrowdStrike Falcon sensor installed on a device. |
| Agent Status | Displays the health status of the CrowdStrike Falcon sensor. If the sensor communicates regularly to the CrowdStrike cloud, the status is set as healthy. Otherwise, the status is indicated as unhealthy. |
| Last Contact | Indicates the time that the CrowdStrike cloud last received contact from the Falcon sensor on a given device. The time indicated corresponds to the local time zone of Akamai Control Center user. Device Posture uses the value of the Last Contact signal to calculate the status of the CrowdStrike Agent Status. |
This integration requires that user devices are running the EAA Client and the CrowdStrike Falcon endpoint protection software. It also requires access credentials to the CrowdStrike administrator portal.
Additionally, in order for the anti-malware detection feature to detect CrowdStrike as an anti-malware product, Crowdstrike Prevention Policy should have Quarantine & Security Center Registration enabled. To enable this setting go to, Prevention Policies > Your Policy Name > Next Gen Antivirus > Type: Quarantine in the CrowdStrike portal.
Prerequisites:
-
Access credentials to your CrowdStrike administrator portal.
-
Install EAA Client on the user desktop macOS and Windows devices.
-
Install and run the CrowdStrike Falcon Sensor on user devices. The Falcon sensor must be properly associated with the customer account used to access and configure the CrowdStrike portal mentioned above.
-
Authentication to the CrowdStrike API requires a Client ID and Client Secret. You can generate these credentials from the CrowdStrike portal.
-
CrowdStrike integration is only supported for desktop (Windows and macOS) devices.
-
In order for the integration to work correctly on macOS, the CrowdStrike Falcon utility and OS sysctl utility must be installed and accessible. See CrowdStrike documentation for further details.
To integrate with CrowdStrike:
-
Configure CrowdStrike cloud to allow API access via Akamai Control Center.
-
Configure Akamai Control Center for CrowdStrike integration.
Configure CrowdStrike cloud to allow API access via Akamai Control Center
Complete this procedure in the CrowdStrike portal to obtain your CrowdStrike Client ID and Client Secret for each sub-organization or entity.
-
Log in to the CrowdStrike portal.
-
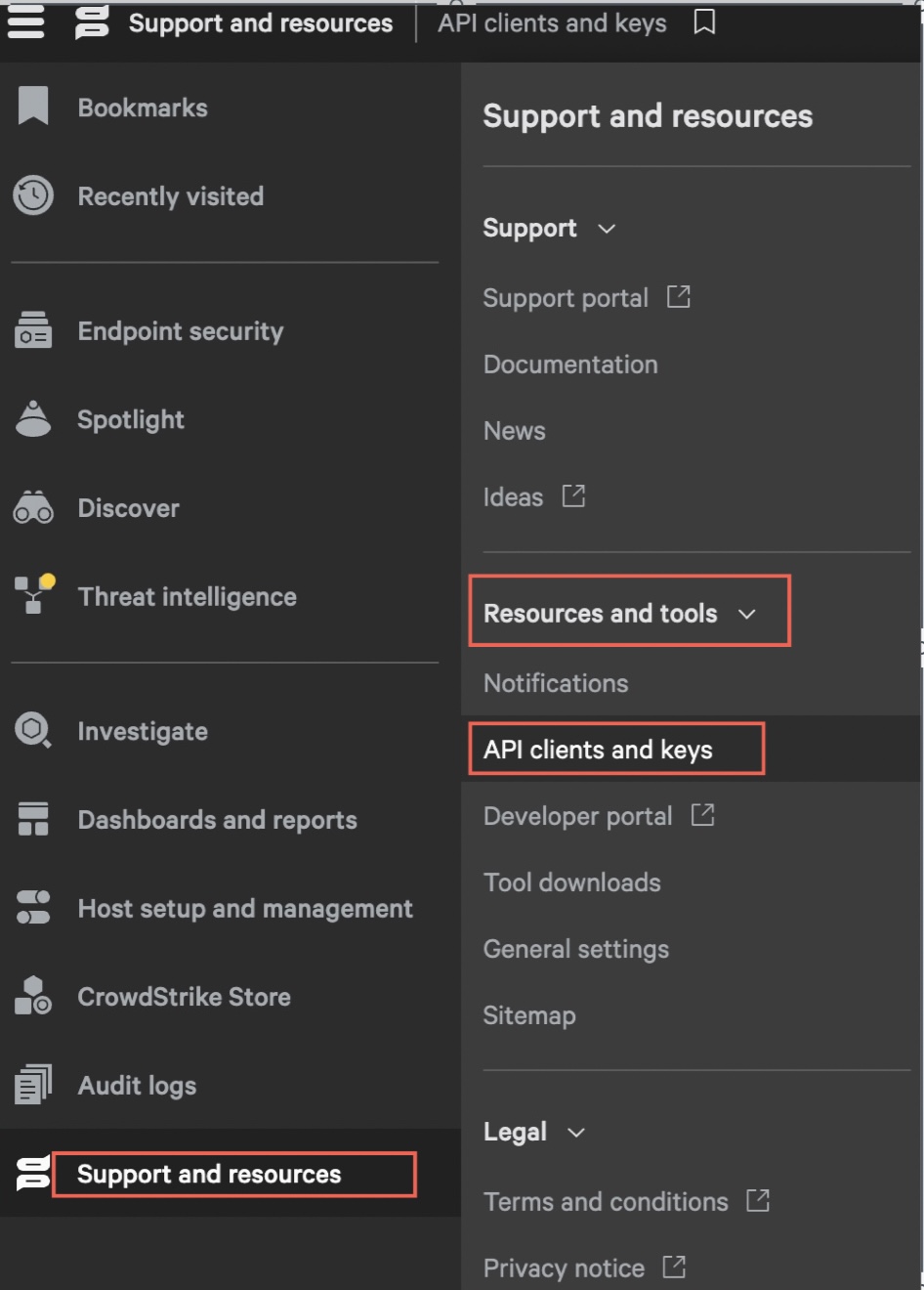
Select Support and resources > Resources and tools > API Clients and Keys.
The API Key page appears.
-
In API Clients, click Add new API Client.
The Add new API client dialog appears. -
In Add new API client:
a. In Client Name enter a unique name for the API client.
b. In Description enter a description for the API client (optional).
-
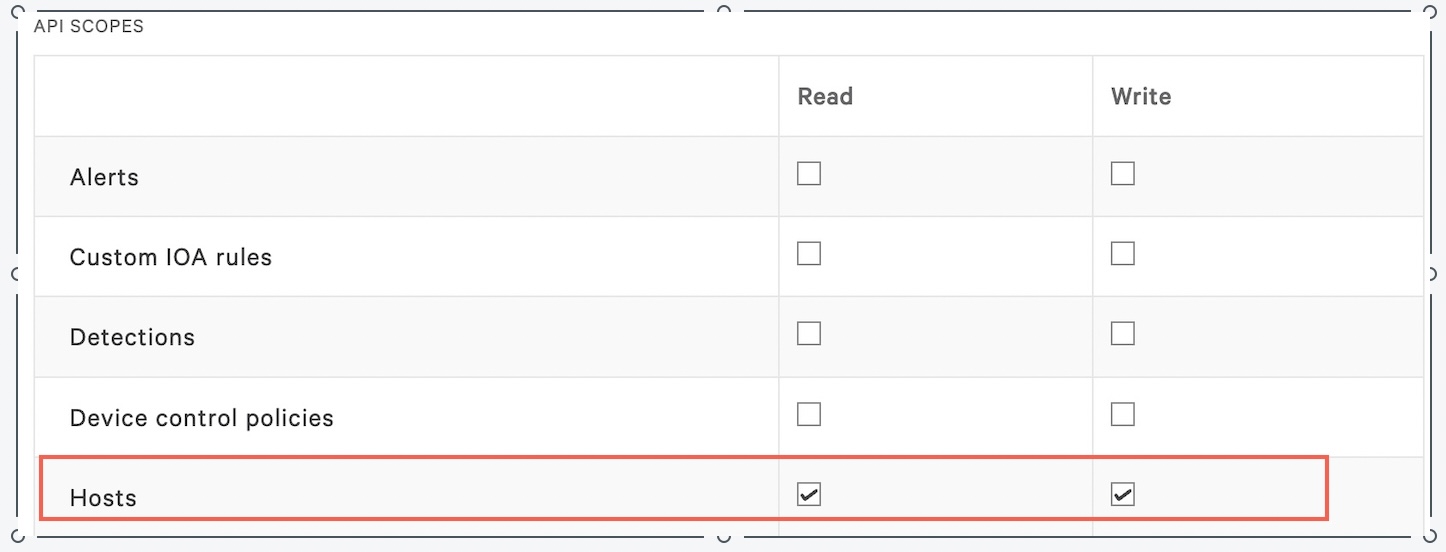
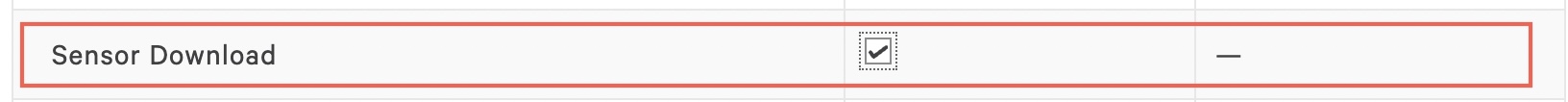
Akamai needs to be able to check the host by batch, enable Hosts, and Sensor Download using the Crowdstrike API.
a. In API Scopes set Hosts with Read and Write permissions.
b. In API Scopes set Sensor Downloads with Read permissions.
-
Click Add.
The API client create dialog appears. -
From the API client created window copy CLIENT ID and SECRET values.
Copy the SECRET now as you won't be able to retrieve its value later.
-
Click Done.
Note
Akamai recommends that the Read permission for Sensor Downloads for existing and new credentials be enabled on the CrowdStrike Portal. If the Read permission for Sensor Downloads for existing and new credentials on the CrowdStrike Portal is not enabled and if one or more credentials expire, the devices belonging to those specific CrowdStrike integrations will have stale data in the Integrations tab in inventory reports. If the device was successfully reporting status to Crowdstrike before the credentials expired, EAA will mark it as healthy for up to 50 minutes after the last time EAA saw that the device reported to Crowdstrike (40 minutes for Crowdstrike and 10 minutes for EAA).
Configure Akamai Control Center for CrowdStrike integration
Complete this procedure in Akamai Control Center to integrate with the CrowdStrike cloud and get access to signals reported by the Falcon client. You can add one or more entities, up to 12 entities
-
In the Enterprise Center navigation menu, select Application Access > Device Posture > Integrations.
-
Click the Add Entity to add a new tenant.
-
Select CrowdStrike and fill in the following fields:
| Field | Description |
|---|---|
| Enabled | Select Enabled to use CrowdStrike signals in tiers and tags.
If the CrowdStrike integration is not enabled, the CrowdStrike Status Healthy signal is not displayed neither in tiers nor in tags criteria. The agent status also does not appear in the inventory reports including filter criteria and device details. |
| Base URL | Enter your entity-specific Base URL |
| Client ID and Client Secret | Enter the CLIENT ID and SECRET.
To get your values, go to Support and resources > Resources and tools > API Clients and Keys > OAuth2 API Clients > Add new API Client from the entity or sub-organization. |
-
Click Test Credentials to ensure the values are correct. A confirmation message appears if credentials' values are successfully tested.
-
Click Save.
-
To add more entities, repeat steps 2 to 4, till all of the sub-organizations are added to the parent organization.
Next steps:
After you configured the CrowdStrike integration, you can:
-
Use the CrowdStrike Status Healthy to configure risk tiers and tags. See Configure tiers and tags for more information.
-
Use the CrowdStrike Healthy criterion to filter inventory reports for healthy and unhealthy devices. See Create an inventory report for more information.
-
View the Integration section of the Device Details report to check the CrowdStrike information.
Integrate with VMware Carbon Black
With VMware Carbon Black integration you can monitor endpoint activity data and block potential threats.
With this integration, you can use Device Posture to calculate the Carbon Black client status running on the user's device. The Carbon Black client status can be reported as healthy if the Carbon Black client running on the device is communicating regularly with the Carbon Black server, or unhealthy if the client is inactive. Additionally, Device Posture can verify if the user's device is assigned to a specific Carbon Black policy. Both of those signals are included in the Device Posture security posture evaluation.
The following is the list of Carbon Black data that you can monitor in the Integration tab of the Device Details report:
| Carbon Black Signal | Description |
|---|---|
| Policy Name | The name of the policy assigned to the device. |
| Status | The status sent by the VMware Carbon Black server. |
| Version | The current version of the VMware Carbon Black software installed on the device. |
| Last Contact | The date and time of the last contact with the VMware Carbon Black server in your local time zone.
Note: Device Posture uses the value of the Last Contact signal to calculate the status of the Carbon Black client. |
Prerequisites:
-
User devices must install and run the VMware Carbon Black agent. Only the Carbon Black Defense product is supported.
-
Authentication to the VMware Carbon Black API requires an API Secret Key and the API ID. You can generate the API Secret Key and API ID from the VMware Carbon Black Defense console.
-
VMware Carbon Black rules are only supported for desktop (Windows and macOS) devices.
To integrate with VMware Carbon Black:
-
Configure VMWare Carbon Black cloud with a Custom Access Level.
-
Configure Akamai Control Center for VMware Carbon Black integration.
Configure VMware Carbon Black cloud with a Custom Access Level
Complete this procedure to obtain your Carbon Black API ID and API Secret Key for each entity or sub-organization.
-
Log in to the Carbon Black Dashboard. You can find your Dashboard URL at the VMware Carbon Black community page.
-
In Settings > API Access click Access Levels.
-
Click Add Access Level.
-
On the Add Access Level page:
-
Enter Access Level name and description
-
Scroll down the Access Level table and set Read permission type as General information for a Device category.
-
-
Click Save.
-
In Settings > API Access click API Keys.
-
Click Add API Key.
-
In the Add API Key dialog:
-
Enter a unique API Key name.
-
In Access Level type select Custom.
-
In Custom Access Level select the Access Level that you previously created.
-
-
Click Save.
-
The API Credentials dialog that appears contains your API ID and API Secret Key. Copy this data and use it in the following step. See Carbon Black documentation to learn more.
Note
If one or more of the Carbon Black credentials expire, the devices belonging to those specific Carbon Black integrations will have stale data in the Integrations tab in inventory reports. If the device was successfully reporting status to Carbon Black before the credentials expired, EAA will mark it as healthy for up to 20 minutes after the last time EAA saw that the device reported to Carbon Black (up to 10 minutes each for Carbon Black and EAA).
Configure Akamai Control Center for VMware Carbon Black Integration
Complete this procedure in Akamai Control Center to integrate with VMware Carbon Black API ID and API Secret Key that you obtained in the previous step of configuration for each entity or sub-organization. You can add one or more entities up to 12 entities.
Note
Device posture integration has been tested with VMware Carbon Black signals for a single entity. However, you may be able to use up to 12 entities. If you have any issues, contact Akamai Support for assistance.
-
In the Enterprise Center navigation menu, select Application Access > Device Posture > Integrations.
-
Go to VMware Carbon Black and fill in the following fields:
| Field | Description |
|---|---|
| Enabled | Select Enabled to use VMware Carbon Black signals in tiers and tags.
Note: If this field is not selected, VMware Carbon Black criteria do not display on the UI pages where you define tiers and tags or generate reports. |
| API Hostname | Select the URL for the API Hostname.
Your Portal Hostname is based on your region, when you configured your VMware Carbon Black account. |
| API Secret Key and API ID | Enter your API ID and API Secret Key used to access the API.
To get values of those credentials, go to Settings > API Access > API Keys in the VMware Carbon Black Cloud console. |
| ORG Key | Enter the ORG Key that can be found in the VMware Carbon Black console under Settings > API Access > API Keys in the VMware Carbon Black Cloud console. |
-
Click Test Credentials to ensure the values are correct.
-
Click Save to save the information.
-
To add more entities, repeat steps 2 to 4, till all of the sub-organizations are added to the parent organization.
Next steps:
After completing these steps, use the following criteria when defining tiers/tags and when generating reports:
-
Use VMware Carbon Black Policy and VMware Carbon Black Status Healthy to define tiers and tags, and to generate inventory reports. See Configure tiers and tags and Create an inventory report for further details.
-
View the Integration section of the Device Details report to check the Carbon Black information.
Updated 11 months ago
