SAML to SAML Bridging
SAML to SAML Bridging Overview
Note:
This feature is currently in Limited-Availability (LA) and can be enabled in your contract by contacting Akamai Support.
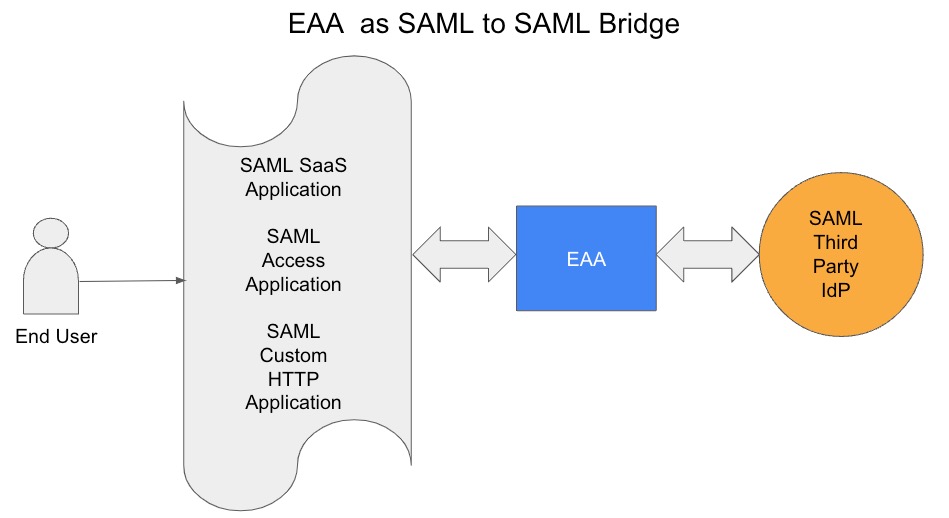
EAA allows you to use single sign-on (SSO) into your SAML-based EAA applications using any SAML identity provider. EAA acts as a bridge between your SAML application and the SAML identity provider to provide user access to enterprise applications.
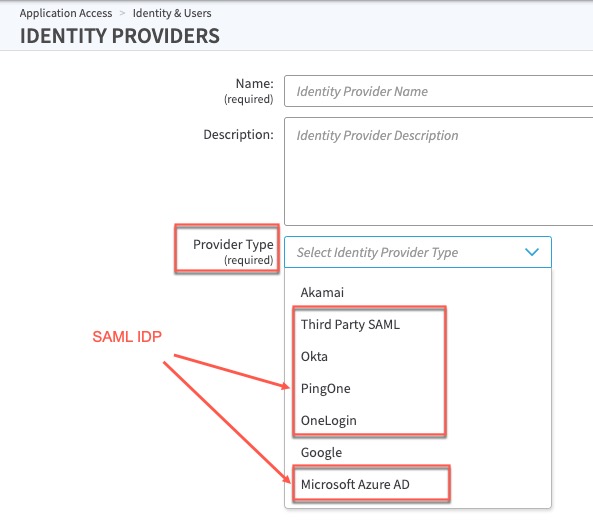
The SAML IDP can be of IdP Provider Type Third Party SAML, Okta, PingOne, OneLogin, or Microsoft Azure AD:
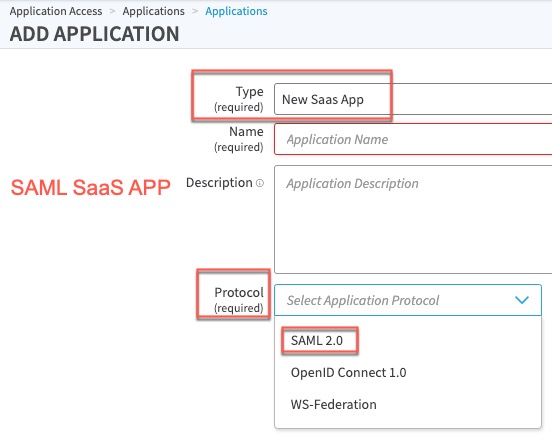
The SAML applications can be a SaaS Application using SAML 2.0, Access Application or a custom HTTP Application using Application-facing Authentication mechanism as SAML 2.0 as indicated below:
SAML SaaS APP: These are SAML applications that are internet facing and do not have a EAA connector.
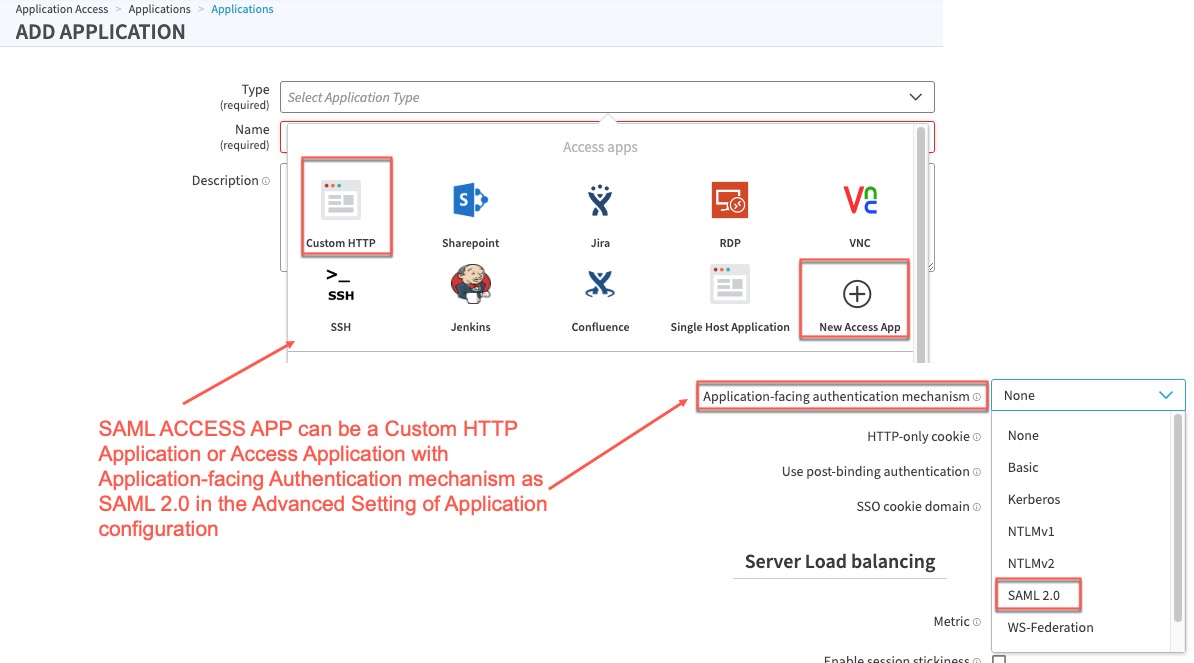
SAML ACCESS APP: These are applications that need an EAA Access Applications and an EAA Connector, and use SAML 2.0 as the authentication for the application.
When you use any of the above SAML IDP as the authentication source for your SAML APP (either SAML SaaS APP or SAML ACCESS APP), EAA behaves as a SAML to SAML bridge.
If you set Directory Verification Required in the Advanced setting s of the SAML IDP, then the user attributes are known to EAA and therefore you do not need to pass attributes between the IDP and EAA.
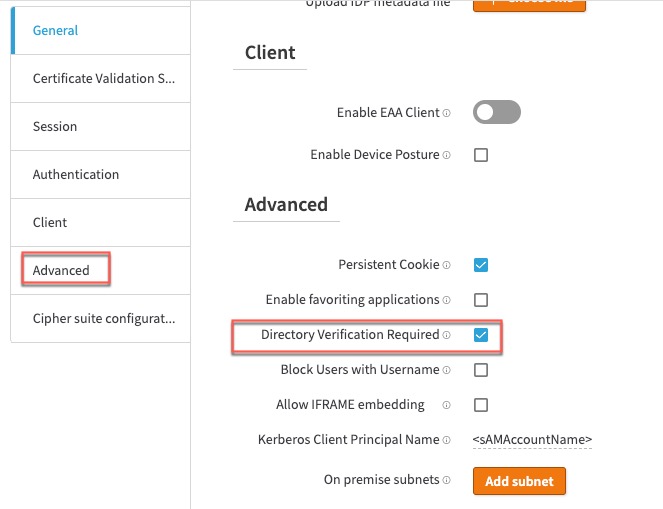
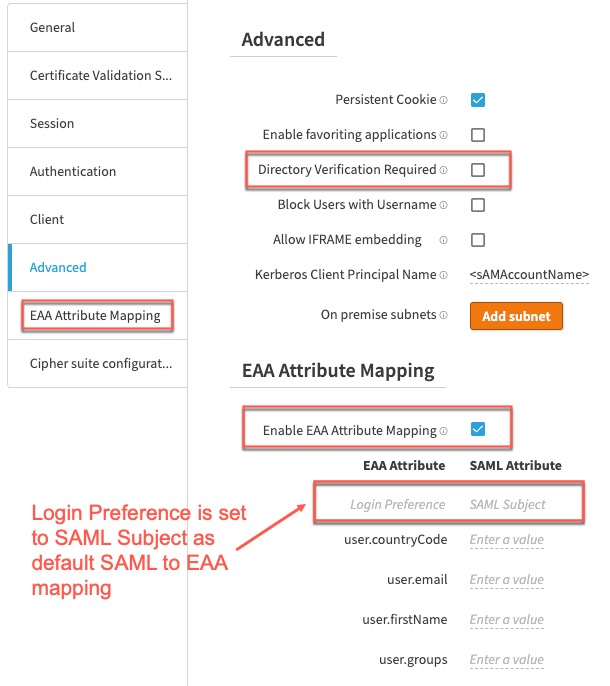
If you do not set Directory Verification Required in the Advanced settings of the SAML IDP, then the user attributes are not known to EAA, then you must set Enable EAA Attribute Mapping and manually map the EAA attributes to the SAML attributes between the IDP and EAA.
Configure SAML IDP for an SAML SaaS Application
Follow the steps described in Configure EAA as the IdP for a custom SaaS application. For the Authentication, (step 7) select the SAML IDP as the authentication source, instead of Akamai IdP.
If you set Directory Verification Required in the Advanced SAML IDP, then the user attributes are known to EAA and therefore you do not need to pass attributes between the IDP and EAA.
If you do not set Directory Verification Required in the Advanced SAML IDP, then the user attributes are not known to EAA, then you must set Enable EAA Attribute Mapping and manually map the EAA attributes to the SAML attributes between the IDP and EAA. If you do not manually map the attributes and you access the SaaS application with this third-party SAML IDP you get a 545 error.
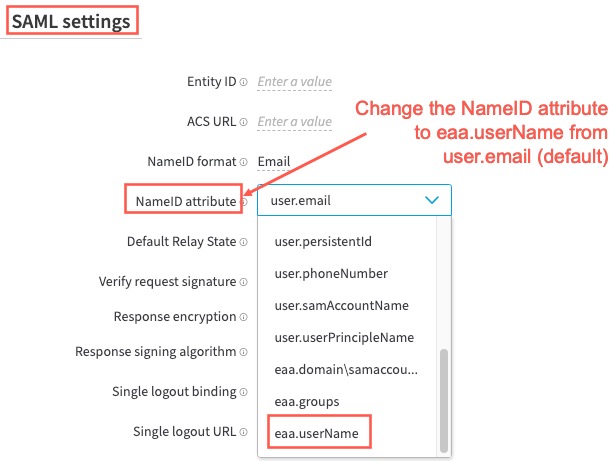
In addition, go to the SAML SaaS application, click the SAML settings tab. The NameID attribute indicates what EAA attribute is sent in the SAML response subject. The default selection for this field is user.email. When a SAML-based IdP is associated with this app, you must update this value to eaa.userName.
Configure SAML IDP for an SAML Access Application
Follow the steps described in Configure Access parameters for an Application. For the Authentication, (step 11) select the SAML IDP as the authentication source, instead of Akamai IdP.
If you set Directory Verification Required in the Advanced SAML IDP, then the user attributes are known to EAA and therefore you do not need to pass attributes between the IDP and EAA.
If you do not set Directory Verification Required in the Advanced SAML IDP, then the user attributes are not known to EAA, then you must set Enable EAA Attribute Mapping and manually map the EAA attributes to the SAML attributes between the IDP and EAA.
In addition, go to the SAML SaaS application, click the SAML settings tab. The NameID attribute indicates what EAA attribute is sent in the SAML response subject. The default selection for this field is user.email. When a SAML-based IdP is associated with this app, you must update this value to eaa.userName.

Limitations
- For any third-party SAML IDP without a logout URL configured, if a SAML SP logout is performed, a 545 error is encountered.
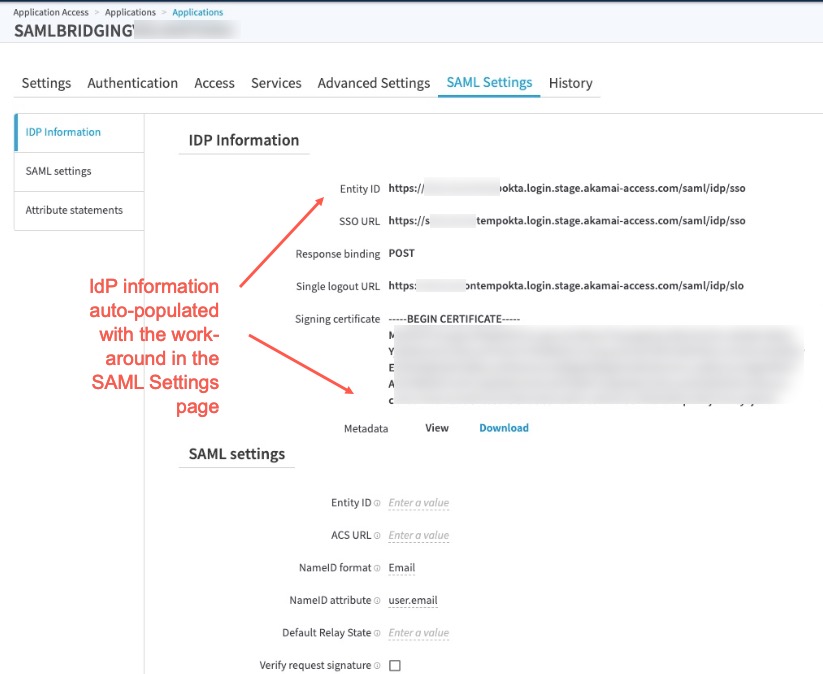
- When using a third-party IDP is selected SAML application, Enterprise Center does not auto-populate the IDP Information in SAML Settings tab:
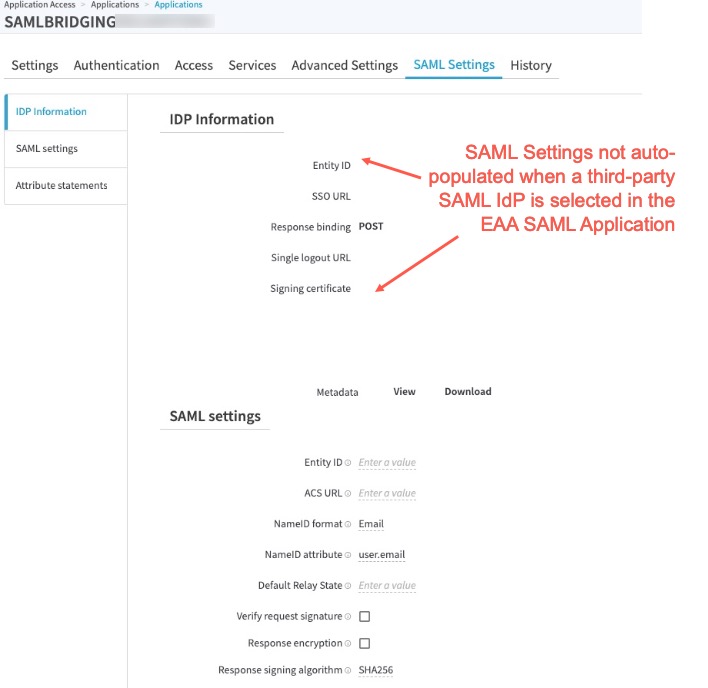
As a work-around, the administrator should navigate to the Authentication tab, select a non-third-party IDP as the IDP within the SAML application, and save the settings. Then, select the correct third-party SAML IDP, and save the settings. Then, they can proceed with the SAML Settings page.
Updated 11 months ago
