AD, LDAP, or AD-LDS Directory
EAA also supports popular third party directory services like AD (Active Directory), LDAP (Lightweight Directory Access Protocol), and AD-LDS(Active Directory Lightweight Directory Service).
Here are the tasks that you can perform with the these types of directory services.
Configure a LDAP, AD or AD-LDS directory and import groups
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
To add a new directory, click Add New Directory (+).
-
Enter a name and description, and select the Service Type. Select either LDAP, AD, or AD LDS.
-
Select and configure one of the following:
a. Use SSL protocol with directory certificate validation (recommended).
-
Host with ldaps (default). Enter a fully qualified domain name (FQDN)/IP of your native directory. By default, the port is 636 as per the standard. See, Directory server certificate validation rules and use cases.
-
Verify Origin Server Certificate (on-by-default). Allows you to verify the authenticity of the directory service provider using the origin server's certificate. Also provide these two fields:
-
Host Aliases (optional). If you are using multiple domain controllers or if you have an IP address for the Host field, provide the Subject Alternative Name (SAN) or Common Name (CN) from your server certificate. This is used to validate the server side certificate. For more information, see Directory server certificate validation rules and use cases.
-
ROOT CA Certificate (mandatory). Select the certificate issued by the certificate authority (CA) with the full bundle that you have uploaded into EAA. For more information, see Upload a ROOT CA certificate for origin server validation
b. Use SSL protocol and not do directory certificate validation. This uses SSL protocol but the origin directory server is not validated since the verify origin server certificate is disabled.
Host with ldaps. Enter fully qualified domain name (FQDN)/IP address of your native directory. By default, the port is 636 as per the standard.c. Not use SSL protocol and not do directory certificate validation.
Host with ldap. Enter fully qualified domain name (FQDN)/IP address of your native directory. By default, the port is 389 as per the standard.If firewalls are used, allow the ports so that Enterprise Application Access can communicate with the LDAP or LDAPS FQDN and port for authentication & password change/reset operations.
-
-
In General settings complete the configuration:
A. Fill in one of the following:
AD domain. Enter the domain where your directory is located.
LDAP domain. Enter the LDAP domain where your directory is located.
B. Admin Account. Enter an administrator account that EAA can use to connect to this directory. The administrator account should have read-only access or higher. For example, use the format
NetBiosDOMAIN\administrator. For a Microsoft Windows AD integration, enter Distinguished Name from the Microsoft Windows AD.C. Admin Password. Enter the password for the Admin account.
D. Login Preference. Select the identifier for the user's principal in the directory. This is the input the user provides when accessing an application through the Enterprise Application Access Login Portal. For an AD directory type choose one of these: email, SAM account name, user principal name (UPN), or Domain/SAM account name. For an LDAP directory type choose one of these: email, UID. For an AD LDS directory type choose one of these: email, UID, or user principle name.
-
Click Add Connector.
The list of connectors appears. -
Select the connectors to associate with the directory. Your connector should run in Ready status.
-
Click Add connector.
-
Go to the right side bottom corner, you see a Deployment section with the deployment state. If the connectors are reachable and all of the required configurations are done, you will see the Ready to deploy icon:
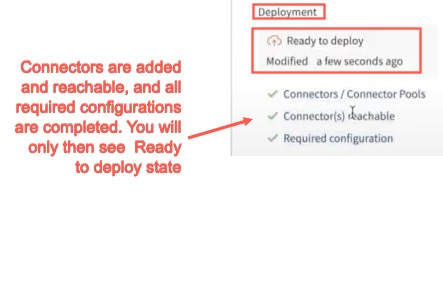
Note: At least one connector must be assigned, it must be reachable, and all configurations must be done, then the Directory is deployable, otherwise you will see:
![]()
- Click Save and Deploy, to save the changes and deploy the directory. Or click Save, then Deploy Directory. Add a Deployment Confirmation message, and click Deploy. Under Deployment section, you will see the icon change to Deploying (
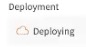 ). After the Deployment is successful, the Deployment version is added to it. If it is the initial Deployment of the Directory, you will see Deployed Version: 1
). After the Deployment is successful, the Deployment version is added to it. If it is the initial Deployment of the Directory, you will see Deployed Version: 1

- Now Test and Add Groups gets activated.
Connectivity Test and Directory Diagnostics window opens. A test is run to check if the connector can communicate with the directory server. If the connectivity is successful, the Test Status returns Success. If the connector is unreachable or if you have multiple connectors associated and even if one of them is unreachable, a Test Status returns Failure. To resolve this issue, see Troubleshoot an unreachable connector. Next, click Retest. After the connectivity to the connector succeeds, you can add users and groups, overlay groups, or organization units (OU). In the User Or Groups Validation section under Search User, you can search and add users, and under Search Groups, you can search and add groups. Select the users or groups, click Add, to add them. - Click Save, to save the directory.
- Click the Users tab to view the users assigned to the directory. You can click the number in the Groups column to view the groups a user is associated with.
- Click the Groups tab to view the groups that are configured in this directory. You can view the users that are assigned to the group. You can also click the sync icon to synchronize EAA with the latest group information from your directory.
- To import a group from an AD, LDAP, or AD LDS:
a. In the Groups tab, click the plus sign.
b. In the provided text field, enter the group name. You can use wildcards to perform the search. You add an asterisk (*) on one or both ends to your search terms. Group searches are case sensitive.
c. Click Search Group.
d. Select the group or groups that you want to import, and click Add.
- Click Save, to save the changes. Click Save and Deploy, to save and deploy the changes.
Note: You cannot see staging information in the deployment process of directories.
- As you make any additional edits to the Directory, the Directory version is incremented and you can see the earlier versions of the Directory by going to the History tab. See Directory Versioning for more details
Directory server certificate validation rules and use cases
Use Host and Host Aliases for Directory origin server certificate validation.
EAA connector performs a directory (either AD, LDAP, AD LDS) origin server validation using the CA certificate that you upload into Akamai Enterprise Center. EAA connector does a hostname validation against the directory server to confirm its identity.
EAA connector uses the Host and Host Aliases fields in the directory configuration to validate the LDAPS origin server identity.
For this, the EAA connector does a match of server identity presented in the server certificate's DNS name in the Subject Alternative Name (SAN) or the Common Name (CN) in the Subject against Host in directory configuration in Enterprise Application Access, with SAN having the highest priority. If the server certificate includes a SAN of type DNS name, only that is considered for doing the host match, otherwise the server certificate's CN (the subject field) is considered. If you have multiple domain controllers or you entered an IP address for the Host, you can use the Host Aliases field to match the LDAPS server's identity.
Use cases:
- Use Case 1. A single domain is represented by two domain controllers (DC1 and DC2). Host matches SAN (DNS name). CN is ignored. Host-aliases is not needed.
In Enterprise Application Access to configure the directory, provide the domain name for the Host:

Both domain controllers have the domain name mydirectory.mycompany.com in the SAN.
Domain Controller1's server certificate has these values for CN and SAN:


Domain Controller2's server certificate has these values for CN and SAN:


Since the Host matches SAN, CN is ignored. Host Aliases is not needed in the configuration. Since there is a server match, the origin server is validated.
- Use Case 2. A single domain is represented by one domain controller (DC1). Host has an IP address. Server certificate for DC1 only has a CN that represents the FQDN of DC1. So use Host-Aliases with the CN value.
In Enterprise Application Access to configure the directory, provide an IP address for the Host:

Domain Controller1's server certificate has a CN and does not have a SAN:

You provide the CN value in Host-Aliases field:

Since there is no SAN, CN value provided in the host-aliases is considered a host match and origin server is validated.
- Use Case 3. A single domain is represented by two domain controllers (DC1 and DC2). Host has a different domain name that does not match the CN in both server certificates. SAN is absent in both server certificates. Use Host-Aliases with CN values of both certificates.
In Enterprise Application Access to configure the directory, provide the domain name for the Host:

Let's assume each domain controller has it's own domain controller certificate. This domain name is not there in any of the domain controller certificates.
Domain Controller1's server certificate has a CN and does not have a SAN:

Domain Controller2's server certificate has a CN and does not have a SAN:

You can use Host Aliases to configure the host names that match the server identity. Since, SAN is absent, you can provide the CN values of the two domain controllers:

CN values of the certificates of both the domain controllers (DC1 and DC2) are provided in the host-aliases as comma-separated values. Since there is no SAN, if Enterprise Application Access reaches any of the domain controllers, it is considered a host match and origin server is validated.
Alternatively, if you don't configure Host Aliases, the EAA connector does a DNS lookup on the Host value for resolving the DNS and if it returns a single or multiple CNAMEs, the EAA connector use them for host match.
EAA connector supports also a wildcard match for the hostname validation.
Delete a directory
Complete this procedure to delete a directory in EAA.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
On the directory list page, hover over the directory you want to delete.
-
Click the trash can icon.
-
In the confirmation window, click Delete.
You're directory will be deleted from EAA.
Sync a directory
Complete this procedure to sync the users, groups in a directory in EAA.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
On the directory list page, hover over the directory you want to sync.
-
Click Sync Directory. Wait two to five minutes for the directory configuration to sync across the cloud.
Users and groups will be synced in the directory.
Note. The automatic directory synchronization takes place every 6 hours. If you want the directory changes to take immediate effect, you should sync it manually.
Force Delete of Groups
You might have created groups in your directories and associated them with applications through the identity provider. To delete these groups you will need to use the force delete option.
- Log in to Enterprise Center.
- In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
- Select the directory that's associated with the application.
- Click the Groups tab.
- Click Delete Group in the row of the Group name you wish to delete.
- Click Delete.
If the group is associated with an application, you will see the message,Failed to delete group. Action not allowed - This group is presently assigned to an application. - Click Dissociate and Force Delete. The group is deleted and dissociated from the application/s.
Note
If the users of this group belong to another group, then the users are not deleted. If the users are not in any other groups assigned to other applications, then they are deleted.
Overlay groups
To add users to different groups in the Active Directory (AD) or Lightweight Directory Access Protocol (LDAP), you can create a new group in the AD or LDAP or an overlay group. For already imported user groups, you can add users to the overlay group and give them permissions through the overlay group. Overlay groups can be thought of as a shortcut to creating a group in the AD or LDAP. Overlay groups are limited to one EAA directory.
Create an overlay group
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Select your directory to open it.
-
Click Groups.
-
In the Groups menu, select Overlay Groups.
-
Click Add New Group (+).
-
Enter an Overlay Group name.
-
Click Save group changes and next Save.
You return to the Directory Groups page. -
Click Sync Directory.
Whenever you create a group, you trigger a directory synchronization. This automatic sync occurs every six hours.
Next, add users to the overlay group.
Add users to an overlay group
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Select your directory to open it.
-
Click Groups.
-
In the Groups menu, select Overlay Groups.
-
Identify the overlay group to edit.
-
To add a user to the group, click the down indicator next to the number of group members.
A list of existing users displays.
-
Filter and select users from the list. Click Associate.
-
Click Save.
-
Click Sync Directory.
The automatic directory synchronization takes place every 6 hours. If you want the directory changes to take immediate effect, you should sync it manually.
Delete an overlay group
To delete an overlay group:
Note that you cannot delete an overlay group when the directory is associated to an IdP.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
On the directory list page, click the name of the directory that contains the overlay group you want to delete.
-
Click the Groups tab.
-
Click the Overlay Groups tab.
-
Hover over the overlay group that you want to delete.
-
Click the trash bin icon. A confirmation window appears.
-
Click Delete.
-
Click Save.
Organizational Units
An organizational unit (OU) is subdivision within your organization that's used to manage users, groups, or resources like computers and servers. OUs may also be based on department, geographic location, branch offices, etc.
You can search for OUs in your AD, LDAP, or AD LDS and import them into EAA.
Import an organizational unit from a directory
To find an OU in your enterprise and add it to your directory configuration:
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Click the directory where you want to import an OU.
-
Click the Groups tab.
-
Click the OUs tab.
-
Click the Add OU (plus sign icon).
-
In the Search OU dialog window, enter the exact name of the organizational unit and click Add OU.
-
Select the OU and click OK.
-
Click Save.
Delete an OU
This operation deletes the OU from EAA. It does not delete the OU from the directory service.
To delete an OU from the directory configuration in EAA:
Note that you cannot remove an OU in EAA when the directory is associated to an IdP.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Click the name of the directory that contains the OU you want to delete.
-
Click the Groups tab.
-
Click the OUs tab.
-
Hover over the OU that you want to delete.
-
Click the trash bin icon. A confirmation window appears.
-
Click Delete.
-
Click Save.
Sync users to organizational units
To sync OUs from the directory service:
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Click the name of the directory that contains the OU you want to sync.
-
Click the Groups tab.
-
Click the OUs tab.
-
Hover over the OU that you want to sync.
-
Click the sync icon.
Updated 11 months ago
