Configure EAA as an IdP for a custom SaaS application
Configure EAA as the IdP for a custom SaaS application
Configure Enterprise Application Access (EAA) as the identity provider (IdP) for a SaaS application.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Click Add Application (+).
-
In Type select New SaaS App and type name and description for your application.
-
In Protocol select SAML 2.0 and click Add Application.
Settings opens. -
In Settings configure the following:
-
If your app is configured under identity provider (IdP), select an application icon and category.
-
In the Application URL, enter the URL of the application.
The application URL is the path that users get to access the application. For example,www.salesforce.com. -
Select an IdP Signing Certificate that signs the SAML request. By default, a self-signed certificate generates. Alternatively, you can upload your own certificate.
-
For the remaining required fields follow the procedure to configure access parameters for an application.
-
-
In Authentication enable Authentication.
-
In Identity provider select an identity provider from the list.
-
Select Assign Directory, select one or more directory sources, and click Associate.
The directory appears under the Assigned Directories and the application summary. -
Select SAML Settings.
The IDP Information fields are filled and are not editable. You can upload or use the metadata information to configure the SAML service provider (SP).

-
To view or download the IdP metadata file, click View or Download.
-
Fill in the remaining SAML service provider (SP) fields.

-
Configure user attribute declarations that are passed as SAML attributes. User attribute declarations are needed if the application requires specific attributes in addition to the default AD attributes. You may need to declare the attributes first before you map them to AD attributes.
After the user attributes are created, they appear as new fields in the User Attributes section of the Active Directory (AD).

Atlassian application as SP and EAA as IdP
Set up Atlassian applications as service providers (SP) and Enterprise Application Access (EAA) as the identity provider (IdP). Extend the single sign-on (SSO) functionality through Enterprise Application Access use of a third-party SAML plug-ins for the Atlassian Suite.
Prerequisite:
Atlassian applications integrated with Crowd SSO.
There are several SAML plug-in providers for Atlassian. In this example, plug-ins are from Kantega. The following applications are supported:
- JIRA Server
- Confluence Server
- Bitbucket Server
- Bamboo Server
- Fisheye/Crucible
The below steps are required to integrate Confluence as an SP and Enterprise Application Access as an IdP. Follow this procedure for other compatible Atlassian applications.
-
Disable Crowd SSO functionality. When you first try to configure the Kantega plug-in, you receive a warning that the
seraph-config.xmlfile needs to be updated to use the standard Confluence authenticator, rather than the Crowd SSO authenticator which was configured as part of the Crowd SSO setup process. To resolve this error:-
Shut down the Confluence instance.
-
Locate the
seraph-config.xmlconfiguration file. For example, in Windows directoryC:\Program Files\Atlassian\Confluence\confluence\WEB-INF\classes. -
Comment out the line that sets the Crowd SSO authenticator and uncomment the line which sets the default Confluence authenticator. For example, a working configuration in
seraph-config.xmlshould look like this:
-
<!-- Default Confluence authenticator, which uses the configured user management for authentication.
<authenticator class="com.atlassian.confluence.user.ConfluenceAuthenticator"/>
<!-- Custom authenticators appear below. To enable one of them, comment out the default authenticator above and uncomment the one below. -->
<!-- Authenticator with support for Crowd single-sign on (SSO).
<!-- <authenticator class="com.atlassian.confluence.user.ConfluenceCrowdSSOAuthenticator"/>
-
Start the Confluence again and log in with a Crowd directory user.
You should no longer get any warning messages about an invalid authenticator being used when you check the Kantega Single Sign-on Configuration page. -
To configure Confluence access the Kantega SSO add-on, and under the SSO with SAML option, select Any SAML 2.0 Identity Provider.

-
Copy ACS URL, Entity ID, and Certificate, save them in a notepad, and click Next.
-
Create a new Access App in EAA. Follow the procedure to configure EAA as the IdP for a custom SaaS application to complete the regular application configuration in the application Settings.
-
In the Authentication, enable Authentication and select an Identity Provider and Directory that contains the same user information as your Atlassian Crowd directory.
-
In the Advanced > Application-facing Authentication Mechanism select SAML 2.0, and select whether you want to use a self-signed (default) or a custom certificate to sign SAML Responses.
-
In the SAML Settings do the following:
-
Click Download to download the IdP metadata file.
-
Paste the Kantega ACS URL and Entity ID values you copied earlier into the corresponding fields.
-
Modify NameID Format and NameID Attribute to control how the user (Subject) is identified in the SAML Assertion. For example, if your Crowd directory users use their domain
userPrincipleName (UPN)as their username, pasteuserPrincipleName (UPN)in the NameID Attribute.
You can leave Default Relay State blank. -
Click Signed Request to indicate that the SAML Request from Confluence will be signed. Paste the certificate you copied earlier from the Kantega configuration into Request Signing Certificate .
-
Leave Response Encryption unchecked.
-
-
The rest of the configuration options can be left as default. Click Save.
Next, continue to configure Confluence as the SP:
-
Upload the EAA IdP metadata file to the Kantega configuration, and click Next.
-
Name the IdP, and click Next.
The SSO redirect URL should be automatically set from the metadata file. -
Verify the IdP signature, and click Next.
-
Decide what happens if Confluence receives a SAML Assertion for a user without an existing Confluence account.
For example, select Accounts already exist in Confluence when logging in, and click Next.

-
Verify that the IdP configuration summary is correct, and click Finish.
-
In the Kantega SAML Configuration Menu, select Settings > Known Domains, and add a list of trusted domains that users are expected to log in with or alternatively, trust logins from all domains.

-
In the Settings > Redirect Mode, decide how you want the redirection from Confluence to the EAA IdP to occur. For the most seamless experience, choose Always redirect users to this provider (do not show the login page).

-
Click Save.
After the EAA application is successfully deployed and the Kantega configuration is finished, you can use the EAA published application URL to test access.
Example:
Go to https://mr-confluence-quincy.go.akamai-access.comwhere you are first redirected to EAA IdP to complete authentication and log in with a valid user account using the UPN name format. After this initial login has been completed, the SSO process between Confluence and Enterprise Application Access completes and you get authenticated access to Confluence without any additional login.
If you now access another Atlassian application that has been published through Enterprise Application Access as the SAML IdP, SSO completes and you gain authenticated access without any additional login steps.
Cisco WebEx Spark as SP and EAA as IdP
Set up the Cisco WebEx Spark application as a service provider (SP) and EAA is the identity provider (IdP).
Complete the following steps to configure Cisco WebEx Spark as the SP and EAA as the IdP.
-
Access Cisco WebEx Spark.
-
Register for a Cisco WebEx trial account.
-
You receive an email prompting you to fill out the fields to create an account.
-
You receive your own WebEx URL. For example,
eaa.my.webex.com.
-
-
Create a new Access App in Enterprise Application Access. Follow the procedure to Configure EAA as the IdP for a custom SaaS application to complete the regular application configuration in the application Settings. Do not deploy your application.
-
Select SAML Settings.
The IDP Information fields are filled and are not editable.-
Copy Entity ID, Single sign on (ACS) URL, Single logout URL, and Signing certificate and save them in a notepad.
You need this data to configure the Cisco WebEx Spark SP. -
Click Download to download the IdP metadata file.
-
Do not deploy the application yet.
Next, configure WebEx Cisco Spark as the SP.
-
Log in with your Cisco WebEx trial account credentials at Cisco WebEx Control Hub.
-
Select Settings > Authentication, and click Modify.
The Enterprise Settings SSO page appears.

-
Click Integrate 3rd party identity provider (Advanced), and click Next.
The Enterprise Export Directory Metadata page appears. -
Click Download Metadata File and save it. You need this file to complete the EAA IdP configuration. Keep this page open for the next steps.

-
In the EAA IdP application select SAML Settings to complete the setup.
-
Extract the SAML setting information from the metadata file you downloaded. You can use the cat command from a terminal window and copy the required lines from the file.

-
In SAML Settings paste the extracted information into the Entity ID, SSO (ACS) URL, Request signing certificate, and Single logout URL, and click Save. Do not deploy the application.
-
-
Go back to the Spark page you keep open.
-
Click Next.
The Enterprise Settings Import IdP Metadata page appears.

-
Import the EAA IdP metadata file you saved earlier, and click Next.
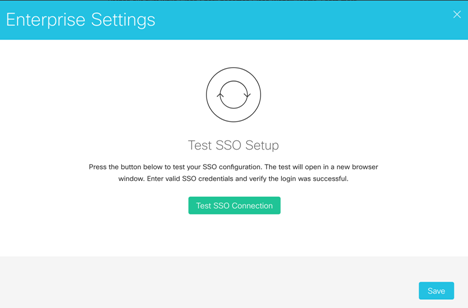
If the upload was successful the Test SSO Setup page appears. Do not do anything on this page now.
-
Deploy the EAA application.
-
Go back to the Test SSO Setup page and click Test SSO.
EAA Login Portal opens. After you log in, the success message:Single sign-on succeededappears. -
Go back to Spark, click Enable Single Sign On, and click Save.

-
To verify the Spark setup, access your own WebEx Cisco Spark URL. For example,
eaa.my.webex.com. -
Click Sign in.
Session starts.
At this time you cannot verify the EAA IdP setup on Spark.
GitHub SP and EAA as IdP
Set up the GitHub Enterprise application as a service provider (SP) and EAA as the identity provider (IdP).
-
Access GitHub Enterprise.
-
Click Start a free trial. Enter all the required information to complete registration.
-
Click Download your trial.
You receive an email with information to set up your portal account. -
Access your personalized site from the tenant URL and with your credentials.
-
After validating your credentials the GitHub home page appears.
-
Click Download at the top of the page.

Try GitHub Enterprise page appears. -
In Step 1: Download License click Download your license.
-
In Step 2: Download the Appliance click Get the latest release of GitHub Enterprise.

Download GitHub Enterprise page appears.
h. Based on your requirements, select either GitHub On-Premises or GitHub in the Cloud.
In these steps, Amazon Web Services from the GitHub in the Cloud menu is used as an example.

i. Select an AWS region from the menu.

-
Your AMI ID appears. Use it to create the instance in AWS.

-
Log in to your AWS account to create the instance, and configure the instance. To do so, follow instructions in the Installing GitHub Enterprise on AWS guide.
- Copy the VM's Public DNS (IPv4) URL and paste it into a web browser. When prompted, upload your license file and set a management console password.
-
Create a new application in Enterprise Center. For instructions see Configure EAA as the IdP for a custom SaaS application. Do not deploy your application.
- From SAML Settings, copy Entity ID, Single SignOn (ACS) URL, and Signing Certificate and save them in a notepad, or copy or download the metadata file to your computer.
You need this data to configure the GitHub Enterprise SP. You need to fill the SAML settings with GitHub data before you deploy the application.
- From SAML Settings, copy Entity ID, Single SignOn (ACS) URL, and Signing Certificate and save them in a notepad, or copy or download the metadata file to your computer.
-
Configure GitHub Enterprise as the SP.
- Log in to the GitHub Enterprise management console.
For example, use the management URL, from the previous steps, from Public DNS (IPv4):
`https://ec2-54-218-112-247.us-west-2.compute.amazonaws.com:8443/setup/unlock?redirect_to=/settings`After you log in, the Settings page appears.
b. In the Settings page click Authentication.
c. In the Authentication page, select SAML as the authentication method.

d. In Single sign-on URL and Issuer paste the EAA IdP metadata from previous steps.
e. Upload the valid certificate from the IdP metadata. It is used to verify the SAML response.

f. Configure the user attributes that use SAML to update the user profile information.

- Log in to the GitHub Enterprise management console.
-
Return to the Enterprise Center EAA IdP application and configure SAML Settings.
-
Add the Entity ID, SSO (ACS) URL, and other GitHub information from previous steps required for the SAML settings.
-
Click Save and Deploy.
-
-
Configure the GitHub application as an access application in EAA.
-
In Enterprise Center create a new EAA access application, and configure the following: Application server IP, External hostname.
-
Click Add or remove connector to assign the connector.
See Install a connector in Amazon Web Services if you need to create a connector. -
Assign the IdP and required directories for the application access. Configure Authentication and Services as you need.
-
Select SAML from the Application-facing authentication mechanism and configure other Advanced settings as you need.
-
Google G Suite as SP and EAA as IdP
Set up the G Suite application as a service provider (SP) and Enterprise Application Access as the identity provider (IdP).
-
Create an admin account at G Suite.
G Suite requires you to have admin access to your domain. You can buy a domain from a third-party provider such as GoDaddy.com. -
Confirm with your EAA account administrator access to the SaaS application feature.
-
Configure EAA as the IdP for a custom SaaS application. Do not deploy your application.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
You need this data to configure the G Suite SP. You need to fill the SAML settings with G Suite data before you can deploy your application.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
-
To configure G Suite as the SP sign in to G Suite with your admin account.
-
Click Security on the Admin console.
-
Click Set up single sign-on (SSO) in the Security subsection.
-
In Sign-in page URL paste data from Single SignOn (ACS) URL SAML Settings IDP, from previous steps.
-
In Sign-out page URL enter your login portal hostname (for example,
https://jp-t3.login.stage.akamai-access.com/api/v2/logout). -
Upload the verification certificate you downloaded in the previous steps.
-
Leave the rest of the settings unchanged and click Save Changes.

-
-
Return to Enterprise Center to EAA application you created in previous steps.
- In SAML Settings configure the following:
| Field | Value |
|---|---|
| EntityID | google.com |
| Single SignOn (ACS) URL | https://www.google.com/a/t3akamai.com/acs (replace with your domain name) |
| NameID Format | |
| NameID Attribute | user.email |
| Default Relay State | / (required) |
| Signed Request | Unchecked (not supported by Google) |
| Response Encryption | Unchecked (not supported by Google) |
| Response Signature Algorithm | N.A (leave default) |
| Single LogOut Binding | Redirect |
| Single LogOut URL | https://accounts.google.com/Logout |
| Verify Single LogOut | Checked |
- Click Save and Deploy.
Next, verify the EAA IdP initiation.
-
Access the Identity Portal URL and log in using your AD credentials.
-
Click the icon for the G Suite application.
This opens a new tab and with a session for users without requesting login credentials.
When the user logs out from the Identity Portal, the session with the G Suite application is also ended.
Also, verify the G Suite SP initiation.
-
Access the Google application using your domain and specific service. For example:
https://www.google.com/a/t3akamai.com/ServiceLogin?continue=https://mail.google.com. -
Users are redirected to the EAA login page. Upon successful login, users can access the Google app.
Meraki as SP and EAA as IdP
This procedure describes how to set up the Meraki application as a service provider (SP) and EAA as the identity provider (IdP).
Complete the following steps to configure Meraki as the SP and EAA as the IdP.
-
Access Meraki.
-
Click Login to create or access your account.
-
Make sure your Meraki account has System Manager service enabled or set up a trial for System Manager.
-
-
Configure EAA as the IdP for a custom SaaS application. Do not deploy your application.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
You need this data to configure the Meraki SP. You need to fill the SAML settings with Meraki data before you can deploy your application.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
-
To configure Meraki as the SP log in to your company Meraki dashboard with your admin credentials.
-
In Organization > Settings > SAML Configuration select SAML SSO enabled.

-
Click Add a SAML IdP to configure the required parameters for Meraki SAML SSO from the previous steps.
-
Copy the Signing Certificate from the previous steps into a file and get the SHA1 fingerprint for it. Use the
opensslcommand. For exampleopenssl x509 -fingerprint -in <Meraki EAA IDP cert file> -noout. -
Paste the fingerprint into X.509 cert SHA1 fingerprint.
-
Paste the Single logout URL from the EAA IDP info, from previous steps into SLO logout URL.

-
Click Save Changes to save the SAML SSO settings.
-
In Organization > Settings > SAML Configuration copy the Meraki Consumer URL and save it.

-
In Organization > Administrators > SAML Administrators add SAML roles for all SAML SSO users.

-
Click Add SAML role. A dialog appears to add a SAML role.

-
Click Save Changes.

-
-
Return to the Enterprise Center EAA application you created and add the Entity ID, SSO (ACS) URL, and other information required in SAML Settings:
-
In the Entity ID field enter
https://dashboard.meraki.com. -
In SSO (ACS) URL paste the Meraki Consumer URL.
-
Add the required SAML attributes for the Meraki dashboard to use for user auto-provisioning or the SSO user. For username, enter the user's email address. For role, enter the SAML role configured in the previous steps.
-
Click Save and Deploy.
-
-
Next, test the SAML SSO.
The Meraki Dashboard only supports IdP-initiated SAML SSO.
-
Open your EAA IdP user portal.
The login page of you EAA IdP portal displays. -
Log in the EAA IdP portal with valid login credentials and click Login.
-
Click the Meraki app card displayed in your user portal.

The EAA IdP should SSO you to the Meraki Dashboard application.
-
O365 as the SP and EAA as the IdP
This procedure describes how to set up the O365 application as the service provider (SP) and Enterprise Application Access (EAA) as the identity provider (IdP).
-
Set up a domain that you have admin access to:
-
Buy and create a domain using a third-party provider such as GoDaddy.com (for example,
t3akamai.net). -
Create an O365 admin developer account at Microsoft Developer Program (for example,
jdoet3akamai.onmicrosoft.com). -
Go to the O365 admin portal. Click Admin Home > Domains > Add a domain to add your domain.
-
Complete the setup wizard and log in as you domain administrator.
The wizard automatically updates the DNS settings on your domain. -
In Home > Domains - if it is set as the default change it to
.onmicrosoft.com. -
Confirm the EAA account administrator request access to the SaaS application feature.
-
Install the Windows server and set it as the domain controller for your domain.
-
-
Configure EAA as the IdP for a custom SaaS application. Do not deploy your application.
- In SAML Settings copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
You need this data to configure the O365 SP. You need to fill the SAML settings with O365 data before you can deploy your application.
- In SAML Settings copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information or download it as a text file.
-
Configure Microsoft Azure as the SP.
-
Download and install Microsoft Azure Active Directory Connect on the Active Directory (AD) server.
-
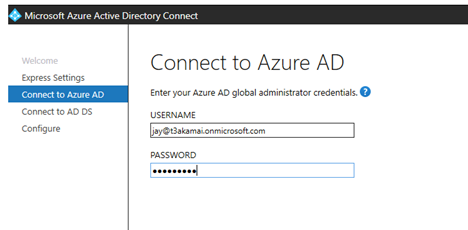
Click Express Settings and complete the setup wizard. Click Connect to Azure AD and enter your username and password.
-
Click Connect to AD DS and enter your username and password, and then click Configure to complete the configuration.

You should see users in AD synced to the O365 admin portal. -
Download and install the Azure Active Directory PowerShell on the AD server. You can also use the GDrive download the installation file.
-
-
Open the Azure AD PowerShell console and run the commands and make the following changes:
-
Replace all occurrences of
t3akamai.netwith your domain name. -
Replace
jp-t3.login.stage.akamai-access.comwith the URL from the EAA IdP configuration. -
Replace the
MIIDyzCCArOgA...certificate with the Signing certificate you copied from the EAA IdP.
Make sure to remove white spaces/line breaks in the certificate. Microsoft PowerShell does not work with spaces in certificates.
-
PS C:\Users\Administrator\Desktop> `Connect-MsolService`
PS C:\Users\Administrator\Desktop> `Get-MsolDomainFederationSettings -domainName t3akamai.net | Format-List *`
PS C:\Users\Administrator\Desktop> `Set-MsolDomainAuthentication -DomainName t3akamai.net -Authentication Managed`
PS C:\Users\Administrator\Desktop> `$domainname = "t3akamai.net"`
PS C:\Users\Administrator\Desktop> `$logoffuri = "https://jp-t3.login.stage.akamai-access.com/saml/idp/slo"`
PS C:\Users\Administrator\Desktop> `$passivelogonuri = "https://jp-t3.login.stage.akamai-access.com/saml/idp/sso`"
PS C:\Users\Administrator\Desktop> `$cert = "MIIDyzCCArOgAwIBAgIQWtsG8SYkRQWGu+
MIID3zCCAsegAwIBAgIQQChS3L+pSuiLa1UzTamz9DANBgkqhkiG9w0BAQsFADBi
MQ0wCwYDVQQDDARTb2hhMRswGQYDVQQKDBJTb2hhIFN5c3RlbXMsIEluYy4xEjAQ
BgNVBAcMCVN1bm55dmFsZTETMBEGA1UECAwKQ2FsaWZvcm5pYTELMAkGA1UEBhMC
VVMwHhcNMTgwNjI3MTMyNzA0WhcNNDMwNjI4MTMyNzA0WjB9MTYwNAYDVQQDEy10
ZXN0LWlkcC1jdXN0b20ubG9naW4uc3RhZ2UuYWthbWFpLWFjY2Vzcy5jb20xDTAL
BgNVBAoTBFNvaGExEjAQBgNVBAcTCVN1bm55dmFsZTETMBEGA1UECBMKQ2FsaWZv
cm5pYTELMAkGA1UEBhMCVVMwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQDG7ON1hXVr7VGNP9qJSF0ymy7RLNlIAPdXNTzvD6/XD5rELUdBSm0VwKyfZzw+
PQgOTwdlcaPBHGXN0i/EQVcorkLraRwTRJZgSW4Vqzq5Crh14tqdHxj1P7ZfndcZ
VTP4cPBdvOHNrcQEi1GhtUL8N1ZKUim5DKXkIcHJo5Yzjdu9V9PRz82Xt63EdU2w
zYUYPX2u+Zu+MgQW/l1P67G39IV8K3kdeAchP9E9eS1twW3TkQAlrA62rierr5PI
QEffmHMh8IFeuCNc7F/WCqlA6oFxfNCCT3K+DY16rqUUJaaVTEcXcfAy+6bizAHm
eOanF27ZMF4qtc5/BGADv5ijAgMBAAGjdjB0MAwGA1UdEwEB/wQCMAAwCwYDVR0P
BAQDAgeAMDgGA1UdEQQxMC+CLXRlc3QtaWRwLWN1c3RvbS5sb2dpbi5zdGFnZS5h
a2FtYWktYWNjZXNzLmNvbTAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
DQYJKoZIhvcNAQELBQADggEBAA+8f0QBA1jFYANWN1IROKo3tom/ph4UWENOK2a/
4q+0oglrLl+NTir5S445/wayLleAY4N6VXpv2iE3aqX5oGZ4xKLRnJO/rKTYef20
U+2ZBSSixkRVYE5QVtWpl4B/GlJh0zQ22Lokdtvj2+CFkRRZCFW2ZJs7kiAqcxtF
2GKke9kyextIs2aaqijfpiJvHEPjKqp4cSs1Q2NUo0qTgptajYNyVKPGsLwdqq8m
5F4xJfUHehUjHbv9y3Jpdfom1V7gYoAcfWuruK8FkDA0sXUrDzK3QufAWcj4XHli
bOk96K7LGRomG9amW2JbSxHiE1EGqEScq9GKWxV9FDPS79Y="`
PS C:\Users\Administrator\Desktop> `$issueruri = "https://jp-t3.login.stage.akamai-access.com/saml/idp/sso"`
PS C:\Users\Administrator\Desktop> `$protocol = "SAMLP"`
PS C:\Users\Administrator\Desktop> `Set-MsolDomainAuthentication -DomainName $domainname
-FederationBrandName $domainname -Authentication Federated -IssuerUri $issueruri -LogOffUri $logoffuri
-PassiveLogOnUri $passivelogonuri -SigningCertificate $cert -PreferredAuthenticationProtocol $protocol`
- Verify the configuration with this command:
PS C:\Users\Administrator\Desktop> `Get-MsolDomainFederationSettings -domainName t3akamai.net | Format-List *`
ExtensionData : System.Runtime.Serialization.ExtensionDataObject
ActiveLogOnUri : http://dummystsurl.microsoftonline.com/dummyurl
DefaultInteractiveAuthenticationMethod :
FederationBrandName : AkamaiT3
IssuerUri : https://jp-t3.login.stage.akamai-access.com/saml/idp/sso
LogOffUri : https://jp-t3.login.stage.akamai-access.com/saml/idp/slo
MetadataExchangeUri :
NextSigningCertificate :
OpenIdConnectDiscoveryEndpoint :
PassiveLogOnUri : https://jp-t3.login.stage.akamai-access.com/saml/idp/sso
PreferredAuthenticationProtocol : Samlp
PromptLoginBehavior :
SigningCertificate :
MIIDyzCCArOgAwIBAgIQWtsG8SYkRQWGu+VNC2taYjANBgkqhkiG9w0BAQsFADBiMQ0wCwYDVQQDDA
RTb2hhMRswGQYDVQQKDBJTb2hhIFN5c3RlbXMsIEluYy4xEjAQBgNVBAcMCVN1bm55dmFsZTETMBEG
A1UECAwKQ2FsaWZvcm5pYTELMAkGA1UEBhMCVVMwHhcNMTcxMTI5MTg1MzI3WhcNNDIxMTMwMTg1Mz
I3WjBzMSwwKgYDVQQDEyNqcC10My5sb2dpbi5zdGFnZS5ha2FtYWktYWNjZXNzLmNvbTENMAsGA1UE
ChMEU29oYTESMBAGA1UEBxMJU3Vubnl2YWxlMRMwEQYDVQQIEwpDYWxpZm9ybmlhMQswCQYDVQQGEw
JVUzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAPOTc5gR/4GpJ2lTjq9bH/1qZWMXFfeV
2hgDIp9Wpdi5koty23szajBqQ40UK6qli2/k0HAUa6clWpxEGy7tXw4HGkbsjmENnNQk24PMwJuEFG
QQmlxwwjk7WATQWvrbQR5im/h3Tk1N9Hc00RTUi0ni/Z3DCBLSPLICCDFgEaQOQBGrlp65SJfJmHJ1
c0hpJh7C9EcLWqzZPGj9jYIOFdCvUVKSm3F0YZA5vz3/f5sp/pNPSBOQaMH8zYewPjbrlP65UR9vhc
jKSnlASt3SiTUtUohOtQf40UxC+BorVPBc/h5Gp0ofrAqINhLEudrlHcJvbpIO30u7Ak4FnSiF2pEC
AwEAAaNsMGowDAYDVR0TAQH/BAIwADALBgNVHQ8EBAMCB4AwLgYDVR0RBCcwJYIjanAtdDMubG9naW
4uc3RhZ2UuYWthbWFpLWFjY2Vzcy5jb20wHQYDVR0lBBYwFAYIKwYBBQUHAwIGCCsGAQUFBwMBMA0G
CSqGSIb3DQEBCwUAA4IBAQAzFYts4Y1hU5ZmGpZRtcTEbdZxhlo1FF3NmFcCEDgaVppdG0w8S+N0h9
Dv79KtdXmchs6QczQG3aMPx23ouX98vy1gZYeq4jXyAcHZ155JsO6cQdsWN77TeVFwCwEmQM2FHuAH
Dnnvg58H1KG13kVUsdw2qgFvbods6niieUosU2QHMbN4CY91i+qJNhU5Sk4w1lXZm5Jy9JRMtJAZmo
YeVfXv9m9Drp9hrAr0O4s1SLob0qOegcB3kUUeMgG0YFpbcXsoJKJTpDfAbae/HMxPBPsnoEFPSZe3
NuBxsF7iddbdaD5gJAXx9H7dVgUveTFxlKUfy7ssp7aiMQgCRkNV
SigningCertificateUpdateStatus :
SupportsMfa :
-
Return to your EAA application you created in the previous steps.
- In SAML Settings configure the following:
| Field | Value |
|---|---|
| Single SignOn (ACS) URL | https://login.microsoftonline.com/login.srf |
| NameID Format | Persistent |
| NameID Attribute | Custom script { "immutable-id" : [{"$" : "user.persistentId"}]} |
| Default Relay State | blank |
| Signed Request | Unchecked |
| Response Encryption | Unchecked |
| Response Signature Algorithm | SHA1 |
| Single Logout Binding | Redirect |
| Single Logout URL | https://www.office.com/estslogout?ru=%2F |
| Verify Single LogOut | Unchecked |
-
Add an attribute statement as shown in this example:
Attribute name :
IDPEmail, Format: Unspecified, Value:user.userPrincipleName. -
Next, verify the EAA IdP setup.
-
Access the Identity Portal URL and log in with your AD credentials.
-
Click on the icon for the O365 application.
A new tab appears and provides you with a session without requesting your login credentials. -
When you log out from the Identity Portal, the session with the O365 application is also terminated.
-
-
Also, verify the O365 setup.
-
Access O365 and enter your username (for example,
user1@t3akamai.net).
You are redirected to the EAA login page. -
Log in to access the O365 application.
-
For more information, see:
- SP metadata file
- O365 developer program account
- O365 admin portal
- Use a SAML 2.0 identity provider to implement single sign-on
- Remove a domain from Microsoft O365
Salesforce as the SP and EAA as the IdP
How to set up the Salesforce application as the service provider (SP) and Enterprise Application Access (EAA) as the identity provider (IdP).
-
Access Salesforce. Log in if you have an account. If you do not have an account, contact the EAA account administrator to request access to the SaaS application feature.
-
Configure EAA as the IdP for a custom SaaS application. Do not deploy your application.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information. Click Download and save the metadata file.
You need this data to configure the Salesforce SP.
- In SAML Settings, copy Entity ID, Single SignOn (ACS) URL, Single Logout URL, and Signing certificate and save this information. Click Download and save the metadata file.
-
To configure Salesforce as the SP access the Salesforce admin account.
-
In Settings > Company Settings click My Domain.

-
Enter the domain name and follow the steps on screen to complete the process.
Your domain is ready for testing. -
In My Domain edit Authentication Configuration and check Authentication Service for your domain. This provides users with an option to have SP-initiated authentication.

-
In Settings > Identity click Single-Sign On Settings.

-
Click Edit and select SAML Enabled.
Enabled SAML allows you to view the SAML SSO settings. -
Click New from Metadata File and select the metadata file you downloaded in the previous steps, and click Create.
The information required fills with data from your file. -
In SAML Identity Type select Assertion contains the Federation ID from the User object.

-
Click Save.
-
Click Edit, and in Just-In-time User Provisioning select User Provisioning Enabled for Standard type provisioning.
This provisions new users in Salesforce upon successful login. -
Copy the Entity ID, Login URL, and Logout URL data.
You need this to complete the EAA SAML settings configuration.

-
If you do not use user provisioning and just want to use SSO functionality, for the SAML Identity Type you can use a Salesforce username or user ID from a user object.
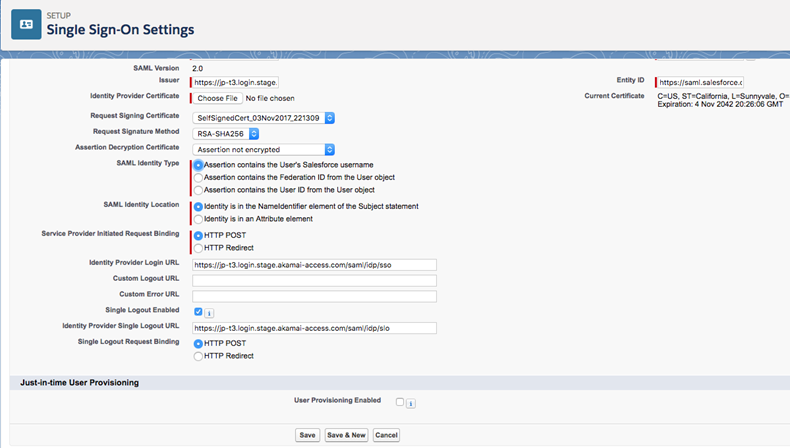
-
Click Request Signing Certificate, and click Download Certificate on the next screen.
You need this certificate to complete the EAA SAML settings configuration.
-
-
Return to Enterprise Center EAA IdP application and configure the SAML settings:
-
In SAML Settings enter the required Salesforce information you copied in previous steps into: Entity ID, Single SignOn URL, and Single Logout URL.
-
In NameID Format ID select email.
Make sure to map the NameID attribute to the corresponding AD field containing the email address. -
Select Signed Request and add the certificate information you downloaded in the previous steps.
-
In Response Signature Algorithm select SHA1.
-
In Single LogOut Binding select Redirect.
-
Map the required attributes for this application to order to successfully perform SSO and User provisioning. Attribute mapping is required only if you want to do user provisioning (for example, create a user in Salesforce upon successful login). See Manage user attributes for more information.
-
-
Next, verify that the EAA IdP is initiated.
-
Access the Identity Portal URL and log in using AD credentials.
-
Click on the icon for the Salesforce application.
This opens a new tab with a session for users without requesting login credentials.
When the user logs out from the Identity Portal, the session with the Salesforce application also ends.
-
-
Also, verify that the Salesforce SP is initiated.
-
Access the Salesforce portal using your domain. For example,
https://jpt3-dev-ed.my.salesforce.com. -
Click on your domain button rather than entering your username and password. This opens the EAA login portal and you can sign in there.
-
ServiceNow as the SP and EAA as the IdP
Set up the ServiceNow application as a service provider (SP) and Enterprise Application Access (EAA) as the identity provider (IdP).
-
Access ServiceNow Developer portal.
-
Click REGISTER and enter the information.
-
Check your mail for an activation message.
-
Access your personalized site with your log-in information.
You have created a developer account on the ServiceNow application.
If you have a trial account, it lasts only for 24 hours and then goes into hibernation. If the trial account is not used within five days, it is decommissioned.
-
-
Create a ServiceNow developer instance.
-
Click Request an Instance. Choose Latest Release from the available options.

-
Select Latest Release from the available options. Close the pop-ups.
-
Save the instance-specific URL and admin credentials.

You have created a developer instance of the ServiceNow application. The number in your URL is a ServiceNow customization for your URL.
-
-
In a new browser window access the customized URL, with your user name and password, to make sure it works.
A password reset is required. -
Configure EAA as the IdP for a custom SaaS application for ServiceNow. Do not deploy the application.
-
In the Settings set the application URL to ServiceNow instance-specific URL (for example
https://devxxxxx.service-now.com/), choose the application icon and category. -
Click Assign identity provider and select the identity provider for the application.
-
Click Assign Directory and choose the directory with users for the application.
-
In SAML Settings click Download and save the metadata as
saml_idp_data.txt. Use any text editor.
-
-
To configure ServiceNow as a Service Provider (SP) log in to your ServiceNow developer instance.
-
Search for "Plugins" and open it.
-
Search for "Integration - Multiple Provider Single Sign-On Installer" and install it.

-
Click Activate/Upgrade link and confirm activation.
-
Search for "Multi-Provider SSO". The plugin should be installed. Add it to your favorites as you need to access it again in later steps.

-
Reset the filter. To back to the instance Homepage click the ServiceNow logo, and click User Administration.
-
To create a new user click Users > New, and user set up window appears. Confirm that the email matches the directory integrated with IdP in Enterprise Application Access.
-
Go back to the "Multi-Provider SSO" you added as favorites. In Administration select Properties, enable all the three options and Save.

-
To create a new SAML identity provider in ServiceNow go to Identity providers, click New and select SAML.

-
In a pop-up window for "Identity Provider Metadata" select XML. Paste the contents from
saml_idp_data.txtfrom into Enter the XML. Click Import.

-
Select the EAA IdP URL as the Default option.

-
Update the NameID Policy to email address. Modify it from
urn:oasis:names:tc:SAML:2.0:nameid-format:transienttourn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress. -
Click Save and Update.

-
Next, since the "Test Connection" feature in ServiceNow is not currently compatible with Enterprise Application Access, you need to disable it.
-
Set the
glide.authenticate.multisso.test.connection.mandatoryproperty to false.
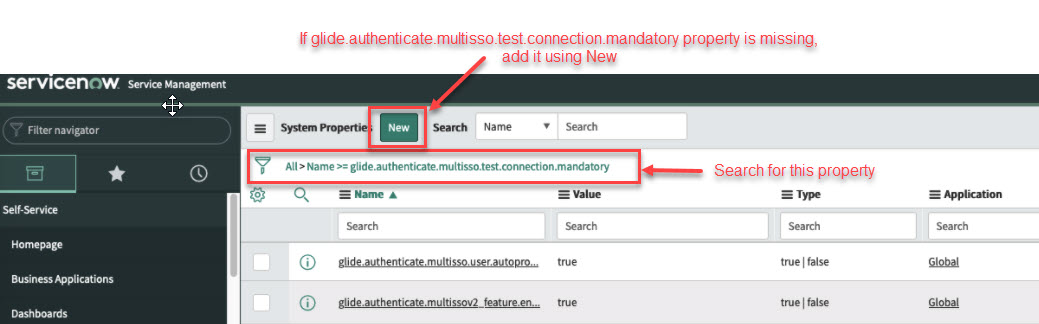
-
Search for
sys_properties.listto get all properties. Confirm if the settings from the previous step work.
If not, click New, add the property and set the type to False, and click Submit.

-
Go back to the "Multi-Provider SSO" you added as favorites. Click on the Identity provider you created and activate it.

The ServiceNow application is configured as a Service Provider (SP).
-
-
Return to your Enterprise Center EAA application.
-
In SAML Settings confirm that the following settings match for ServiceNow:
-
Entity ID should match the value of Entity ID /Issuer in the ServiceNow identity provider config, for example,
https://devxxxx.service-now.com. -
SSO (ACS) URL should match the value of ServiceNow Homepage in the ServiceNow identity provider config, for example,
https://devxxxx.service-now.com/navpage.do. -
Ensure that you use the same SHA algorithm in Enterprise Application Access and ServiceNow. If you use
SHA-1algorithm in ServiceNow, set Response signature algorithm toSHA1in Enterprise Center.
Alternatively, if you useSHA-256algorithm in ServiceNow set Response signature algorithm toSHA256in Enterprise Center. -
Single logout URL should match the value of SSO (ACS) URL, for example,
https://devxxxx.service-now.com/navpage.do. -
Click Save and Deploy.
-
-
Next, verify that Enterprise Application Access as IdP and ServiceNow as SP work seamlessly authenticate accredited users associated with the IdP to use the ServiceNow SP.
-
Go to your ServiceNow instance URL on a web browser and click Use external login.

-
Log in as admin with your customized password.
You should be redirected to the EAA IdP login URL. -
Enter the user credentials matching AD or Cloud Directory for the user.
You are on your ServiceNow account landing page.

-
ShareFile as SP and EAA as IdP
Set up the ShareFile application as a service provider (SP) and Enterprise Application Access (EAA) as the identity provider (IdP).
-
Log in to your ShareFile account or set up a free trial account.
-
Create a new application in Enterprise Center. Do not deploy the application.
-
In the SAML Settings find the IDP information:
-
Copy Entity ID, Single SignOn (ACS) URL, and Single Logout URL and save to configure the ShareFile SP.
-
In Signing certificate click Download and save the downloaded XML file.
You need this data to configure the ShareFile SP.
-
-
To configure ShareFile as the SP log in to ShareFile using your admin credentials at
https://<*yourcompany*>.sharefile.com/. -
In Settings > Admin Settings* > Security <<CHARMENU_DELIMITER>> *Login & Security Policy_ > * Single Sign-on / SAML 2.0 Configuration Settings select Yes** to enable SAML.
-
Copy the Assertion Consumer Service (ACS) URL, SP-Initiated Login URL, and ShareFile Issuer / Entity ID URLs.
You need this data to complete the EAA IdP configuration.

-
Configure the required parameters for the ShareFile SAML SSO. Use the data you copied from the EAA IdP application in the previous steps.
-
Paste Identity ID into the ShareFile IDP Issuer / Entity ID.
-
Click Change and paste Signing certificate into ShareFile X.509 Certificate.
-
Paste SSO URL into the ShareFile Login URL.
-
Configure the ShareFile Logout URL as
https://<your EAA IDP user portal>/api/v2/logout(ShareFile did not participate in the SAML Single Logout).

-
-
Click Save to save the SAML SSO settings in ShareFile.

-
Return to the Enterprise Center EAA IdP application and configure SAML Settings.
-
Paste Issuer/Entity ID into Entity ID.
-
Paste Assertion Consumer Service (ACS) URL into SSO (ACS) URL.
-
-
Click Save and Deploy.
-
Test the SAML SSO to ShareFile.
ShareFile does not support IDP-initiated SAML SSO. ShareFile also does not support auto user provision from SAML Response so you have to first add users to ShareFile before you try to test user SSO with the Enterprise Application Access SAML IdP.
-
Open the browser to your ShareFile SP-Initiated Login URL:
https://<yourcompany>.sharefile.com/saml/login. -
Log in to the EAA IDP portal with a valid username and password.
EAA IdP should SSO you to ShareFile.
-
Set up Slack as SP and EAA as IdP
This procedure describes how to set up Slack as a service provider (SP) and EAA as the identity provider (IdP).
Complete the following steps to configure Slack as the SP and EAA as the IdP.
-
Access Slack to create a Slack workspace and a Plus plan account. Plus account is required to complete the procedure.
-
Click Getting Started for workspace creators and create a workspace:
-
After you register, check your mail for a confirmation code.
-
Follow the steps to set up a profile and manage your workspace.
-
-
Configure EAA as the IdP for a custom SaaS application for Slack. Do not deploy the application.
-
To configure Slack as the SP log in, click on your workspace name and do the following:
-
Select Administration>Workplace settings>Authentication.
-
Click Configure next to SAML authentication and choose your SAML provider.
-
Click Configure again and fill in the SAML fields using the available information from the EAA IDP info from SAML settings :
- In SAML 2.0 Endpoint (HTTP) enter SSO URL.
- In Identity Provider Issuer enter Entity ID.
- In Public Certificate paste text copied from Signing certificate text.

-
-
Click Expand next to Advanced Options. Choose how the SAML response from your IDP is signed. Select Sign AuthnRequest because you need an end-to-end encryption key.
The certificate shows. Copy it to complete the EAA IdP configuration. -
Check the following: Responses signed, Assertions signed and select the default option password protected transport for
AuthnContextClassRef. -
Enter https://slack.com as the Service Provider Issuer.
-
In Settings, decide if members can edit their profile information (like their email or display name) after SSO is enabled. You can also choose whether SSO is required, partially required, or optional.
-
In Customize, enter Sign In Button Label.
For example, if you type EAA, the button label changes to Sign in with EAA. -
Click Save Configuration.
-
Return to the EAA application.
-
In the SAML Settings > SAML settings fill in the following fields:
- Entity ID
- SSO (ACS) URL
- NameID enter persistent
- NameID attribute enter user.email
- Response Signature Algorithm enter SHA1.
- Single Log Out Binding enter Post
-
Select Signed Request, and paste the Slack certificate from previous steps into the Request signing certificate.
-
In SAML Settings > Attribute statements add an attribute statement.
-
Click Save.
-
To verify the IdP initiated setup:
-
Access the Identity Portal URL and log in using your AD credentials.
-
Click on the icon for the Slack application.
It opens a new tab with a session for users without requesting login credentials. -
When a user logs out of the Identity Portal, the session with the Slack application expires.
-
-
To verify the SP initiated setup:
-
Access the Slack portal using your domain such as
https://eaatalk.slack.com. -
Click on the label button (instead of entering your username and password). This opens EAA Login Portal. Log in.
-
Tableau as SP and EAA as IdP
Set up the Tableau application as a service provider (SP) and <<PRODUCT_NAME> (EAA) as the identity provider (IdP).
-
Access Tableau.
-
Click TRY IT FOR FREE and enter the information to register.
-
After you register, check your mail for an activation message.
-
Access your personalized site with your login information.
-
-
Configure EAA as the IdP for a custom SaaS application for Tableau. Do not deploy the application.
-
To configure Tableau as a service provider (SP) log in to your Tableau.
-
In Settings > Authentication > Authentication types, select both Enable an additional authentication method and access.com (SAML).

-
Click Edit Connection... to expand the screen to complete the steps to set up SAML for single sign-on.

-
In Export metadata from Tableau Online, select Export metadata, copy and save the metadata information.
Next, select Copy the Tableau Online Entity ID and Assertion Consumer Service URL (ACS) URLs and Download Certificate.
Use the information for the EAA SAML settings in the next steps. -
Return to the EAA application and do the following.
-
In SAML Settings > SAML settings import the Tableau metadata file from the previous step, or manually enter the Entity ID, ACS URL, and certificate information.
-
The IDP Information fields are filled and are not editable. Copy Entity ID, SSO URL, Single logout URL, and save them in a notepad. Download Signing certificate.
You need this data to configure the Tableau SP. -
Configure user attribute name declarations that are passed as SAML attributes. User attribute declarations are needed if the application requires specific attributes in addition to the default AD attributes. You may need to declare the attributes first before mapping them to AD attributes. See Create user attributes in EAA. You need this information to complete the next step.
-
-
Return to the Tableau.
-
In the Authentication field, paste the information from the previous steps into the Import metadata file into Tableau Online fields for the IdP entity ID and SSO Service URL or browse for the certificate file that you save into the IdP metadata file field.
-
Configure the Match attributes names (assertions) with the corresponding EAA attribute names.
-
-
In the EAA SAML Settings > SAML settings enter the required information to complete the setup (Entity ID, SSO (ACS) URL, NameID format, NameID attribute, and Single Logout URL), and other required information.
-
Click Save.
Zendesk as SP and EAA as IdP
Set up the Zendesk application as a service provider (SP) and Enterprise Application Access ( EAA as the identity provider (IdP).
-
Access Zendesk.
-
Register on the *Let's get started page**.
-
Check your mail for an activation message.
-
Access your personalized site with your login information.
-
-
Configure EAA as the IdP for a custom SaaS application for Zendesk. Do not deploy the application.
-
To configure Zendesk as a service provider (SP), log in to your Zendesk account.
-
Select SETTINGS from the left panel, and select Security.
-
Enable Single Sign-on (SSO) and select SAML.
-
Configure the required SAML parameters: SAML SSO URL, Certificate fingerprint, and Remote Logout URL. This information is in your EAA application in SAML Settings > IdP information.
You need the ACS URL located under the SAML SSO URL field to configure EAA IdP.
-
-
Return to the EAA application.
-
In the SAML Settings > SAML settings enter the required Zendesk information to complete the setup (Entity ID, ACS URL, NameID format, NameID attribute, Response signature algorithm, and Single logout tracking), and other required information.
-
Click Save.
Updated 7 months ago
