SAML Logout for third-party SAML IdP
EAA supports SAML based logout when you use a third-party SAML identity provider. This works with IdP provider type Third Party SAML only. This feature does not work with Okta, PingOne, OneLogin, Google, Microsoft Azure AD types of identity provider in this release.
With this feature, EAA sends a signed SAML Logout request to the third party SAML IdP and the user is logged out of all the sessions from all applications using SAML logout service. In earlier releases, EAA allowed you to configure a Logout URL and EAA would make a get request to the specified URL. It wasn’t persistent across all sessions and not based on SAML logout service.
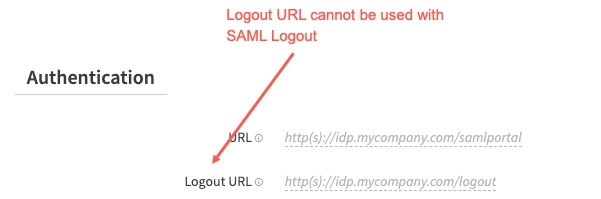
Note: You cannot use the SAML Logout feature with Logout URL.
The procedure to use SAML Logout is:
- Log in to the Enterprise Center.
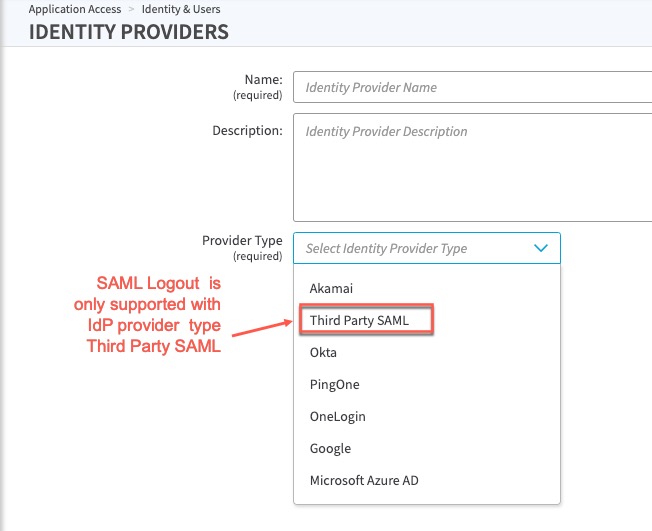
- In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
- Select the identity provider of IDP type: Third Party SAML for which you want to add SAML based logout.
- Go to Settings > Authentication
- If you were using the Logout URL before, you must remove the value in it.
- Select SAML Logout.
- Signing and Encryption Certificate option appears. Upload the certificate that will be used for signing and encrypting SAML requests.
- You can use a self-signed certificate. Or, if you have uploaded the certificate, select Use uploaded certificate and select it. See Add, edit, or delete certificates.
- Click the Choose file next to Upload IDP metadata file and upload it. The IDP metadata file must contain a valid .xml file that has the logout service endpoint and a SAML post to that endpoint. For example, your XML file should look like this:
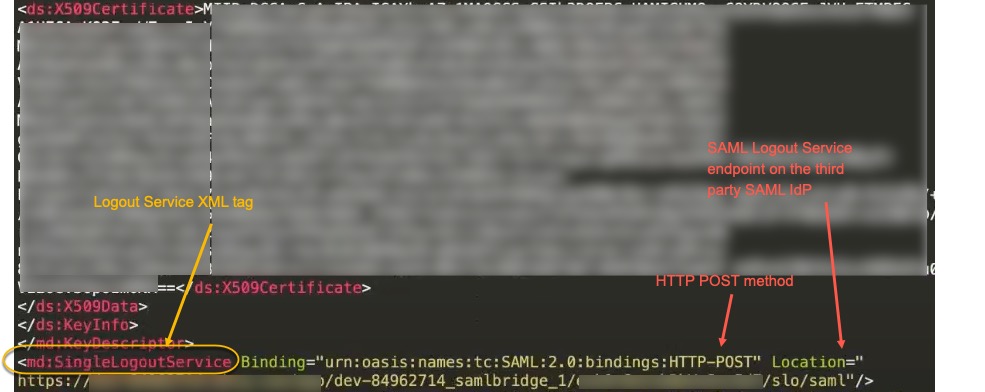
After you upload, you will see a message that the metadata file is valid or if there are errors. If there are errors you need to fix it.
Note: You cannot use the SAML Logout feature with Logout URL. So, once you enable SAML Logout, Logout URL is hidden from the page.
- Save and Deploy the identity provider.
Updated 11 months ago
