Define device risk tiers
With Device Posture risk tiers, you can assess the risk of devices accessing your applications and classify each device into one of three risk tiers: low, medium, or high.
First, you need to configure criteria and rules to assign devices to risk tiers. Once you define risk tiers, you can continuously monitor your device population and verify their security posture. Risk tiers may be used as a way of controlling application access or for monitoring your device population independent of application access.
You can use criteria to set parameters you wish a device should meet in order to satisfy a rule. A rule is a set of criteria. You can configure one or more rules for each tier. Akamai provides you with pre-configured rules for low- and medium-risk tiers. These values are a suggested starting point, but you can review and adapt them to your needs.
When you add multiple criteria to a rule, they are evaluated with the AND logic operator. If a device meets all the criteria, it satisfies the rule.
When you add multiple rules to a tier, they are evaluated with the OR logic operator. If a device meets any of the rules, it is classified as part of the tier.
For example, you may want to edit an existing rule for the medium tier by adding additional criteria to that rule. Criteria are evaluated with the AND operator. So a device needs to meet all criteria to be classified as a medium-tier device. Refer to the figure Add multiple Device Posture criteria. Next, you add a new rule and save the updated tier configuration. Since multiple rules are evaluated with the OR operator, a device needs to meet at least one of the existing rules to be classified into the tier. Refer to the figure Add multiple Device Posture rules.
-
In the Enterprise Center navigation menu, select Application Access > Device Posture > Tiers.
-
In the Medium tier panel, click Edit Rules to configure additional criteria.
-
Click Add Criterion (+).
-
In Criteria, select conditions that medium-tier devices have to meet. Select Anti-malware Profile.
-
In Value, select one of the previously configured anti-malware profiles, for example, Any Vendor.
-
Let's add one more condition. Click Add Criterion (+).
-
In Criteria, select Disk Encryption. Next, select Enabled, which is the single allowed value for this criterion.
The rule now contains three criteria that a medium-tier device must meet. To add multiple criteria select all the required values.
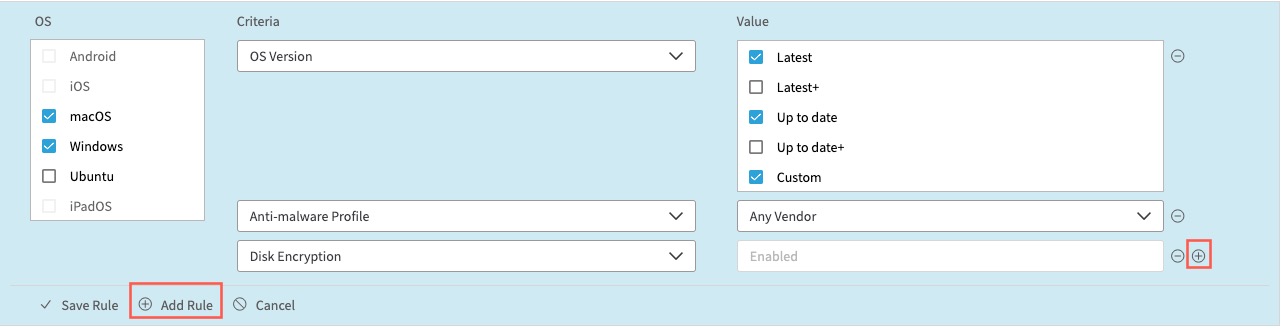
Figure: Add multiple Device Posture criteria
Note
For some criteria, like the operating system or browser version, you may select more values. For others, for example, the firewall status, there's only a single allowed value. So you only need to select the criteria, and the single allowed value is automatically populated.
The rule now contains three criteria that a medium-tier device must meet. To add multiple criteria select all the required values.
- Now you can add a new rule to the medium tier. Click Add Rule.
- When creating a new rule, first you need to specify the operating system (OS) of devices you want the rule to apply to. This new rule is for mobile devices. In OS, select Android.
You can see that when you select one operating system—for example, Android—the OS options for desktop devices become inactive.
Since Device Posture collects different signal types from desktop and mobile devices, you may select either a desktop or mobile operating system, but not both.
- For the first criterion: In Criteria, select Biometrics. Next, select Enabled, which is the single allowed value.
- Click Add Criterion (+).
- For the second criterion: In Criteria, select Jailbroken. Next, select Not Detected, which is the single allowed value.
You can click Delete Criterion (-) to remove unnecessary conditions.
Click Delete Criteria Rule to remove the entire rule. - Click Save Rules.
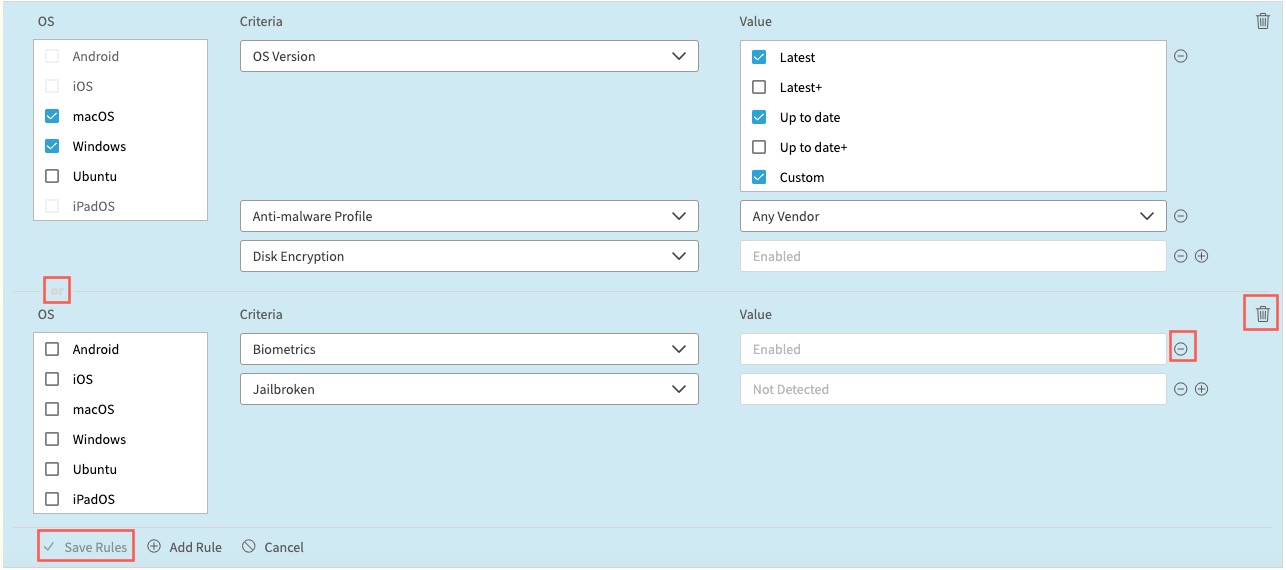
Figure : Add multiple Device Posture rules
The Save Device Posture Rule dialog appears, displaying the number of devices that would be grouped into each tier with the new configuration. Device Posture calculates and displays the change in the number of devices from the current configuration and displays this value in parentheses. This lets you preview changes to see what type of impact they may have before you save them and make them active.
- Click Save Rule to create the rule or Cancel to delete the changes.
Next steps:
-
Use the configured risk tiers to set up application access controls. See EAA access control rules.
-
Monitor your device inventory using the Device Posture dashboard. On the dashboard, you can check all configured tiers and verify how many devices meet their criteria. See Device Posture dashboard.
If you need more details, hover over and click a selected tier. For example, you can click the high-risk tier on the tiers chart. This redirects you to the Device Posture inventory report filtered to show only the devices in the high-risk tier. See Create an inventory report.
Updated 11 months ago
