Add access control rules
Access Control Types
In Enterprise Center for Enterprise Application Access you can create an access control rule to block or deny access to an application based on the criteria listed in the below table.
| Access control type | Description |
|---|---|
| URL | The web address or path requested by the user.
Note: This access control type is available with HTTP/HTTPS applications only. |
| Group | The group that a user belongs to. |
| User | The username assigned to the user |
| Method | An HTTP method such as GET, POST, PUT, DELETE, HEAD, OPTIONS, TRACE, CONNECT, or an Other method for any custom method that is used for the application. |
| Client IP | The IP address of the client that you want to restrict |
| Country | The country where you want to prevent the user from accessing the application. |
| Time | The days of the week and the exact times (based on time zone) that you want to restrict access.
Note: This access control type is available with HTTP/HTTPS applications only. |
| App Host | The hostname of the application server. Applies to tunnel-type client-access applications only. |
| App Port | The port number of the application server. Applies to tunnel-type client-access applications only. |
| App Protocol | Select TCP or UDP protocol. Applies to tunnel-type client-access applications only. |
| Device Risk Tier | Set the risk tier to Medium or High, High, or Unmanaged levels.
Note: Available only if you have access to Device Posture. |
| Device Risk Tag | Set the risk tag to iOS Device, Windows PC, Browser, OS, or CS Status Check.
Note: Available only if you have access to Device Posture. |
Creating rules with ACL
For every rule you create, you select the access control type, an operator, and then define the values for the selected type. You can choose whether an operator is or is not is restricted as a control type.
These conditions also apply to rules:
- By default, access control rules are disabled for an application. You must enable the feature and then configure the rules and the criteria you require.
- A rule can contain one criterion or multiple criteria. The criteria you provide in a rule are combined with an
ANDoperator. For example, with the following criteria, the conditions are combined to block User A from accessing the application from 1am to 2 am on a Saturday.

- If multiple rules are created for an application, these rules are combined with the
ORoperator. This allows you to use the same control types in multiple expressions and ensure there is no conflict.
For example, as shown in the Figure, if User A attempts to access the application between 1 am and 2 am or 11 pm and 12 am EST on a Saturday, they are denied access.


After you save the rules, the combined rule appears as:

- The criteria you create in a rule are combined with an
ANDoperator. This means that all conditions are applied to deny access. If you configure multiple rules, the rules are applied with anORoperator to ensure that if any of the conditions in a rule apply, access to an application is denied. - Access control rules are not applied to an application until you deploy the application. If you make changes to the access control rules, after an application is deployed, you must re-deploy the application for the new rules to apply.
When a user is denied access as a result of an access control rule, by default, an HTTP 403 Forbidden error message appears. See Application response codes, login events, and errors.
Exact matching and substring matching using ACLs
When you use Access Control Rules (ACL) with EAA Applications, exact match is used for Access Control types of Group, User, Method, Country, App Host, and App Protocol. In earlier releases, substring matching was used. This change ensures a more precise and predictable access control behavior. However, URL criteria will continue to use substring matching.
See the examples below for understanding the difference between exact matching and substring matching for different Access Control Types.
Group Access Control Type
For example, if you want to deny access to members of ERP group, you must specify the deny rule as below:
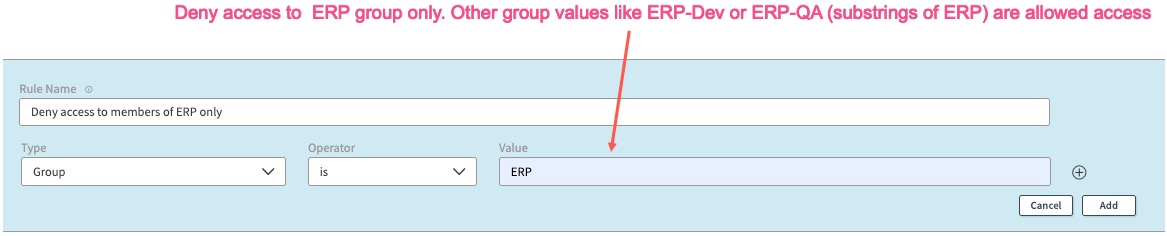
Note: If you have other related groups like ERP-Dev, ERP-QA (which are substrings of “ERP”), they will still be allowed access.
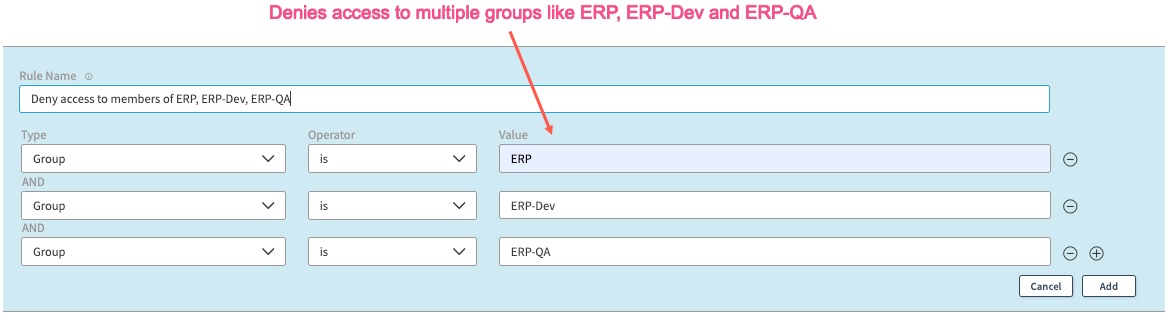
But, if you wish to deny access to members of all ERP, ERP-Dev, ERP-QA groups, you must specify a complex deny rule as below:
URL Access Control Type
In the URL Access Control type, you can configure the path value that you may use in your application URL. If you are using an URL criteria as the Access Control Type for creating your deny rules, substring match is used by default.
Let’s look at some examples to understand this behavior:
- If we create a deny rule as:
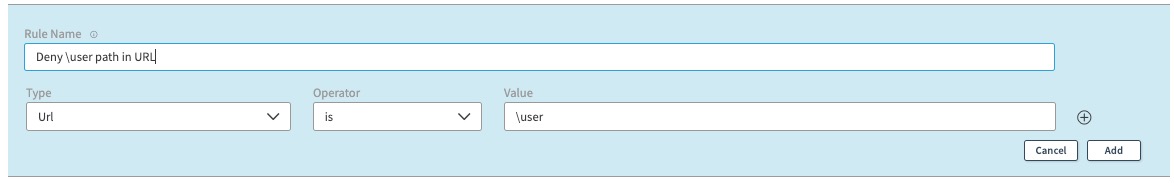
When you access the following application with these paths you will see this behavior:
| Application with path | Description | Behavior |
|---|---|---|
| <app_url>\user | The deny rule value matches URL path | Block access. 403 Error is issued. |
| <app_url>\user1234 | The deny rule value \user matches substring value \user1234, since substring match is used by default in URL criteria | Block access since it is a substring match and it is the default behavior is URL Access Control Type. 403 Error is issued. |
- If you wanted to match
www.google.com,www.google.com/docs, andwww.google.com/gmail, you would create a URL path rule as below:
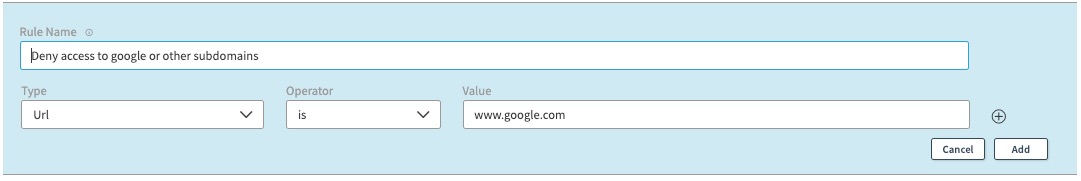
Since substring matching is allowed by default for URL path, this rule would deny access to all three paths: www.google.com, www.google.com/docs, www.google.com/gmail, and any other subdomains of www.google.com. But it would not deny access to sheets.google.com, since it is not a matching substring of www.google.com.
Note: To deny access to only www.google.com/gmail, you would specify the deny rule as:
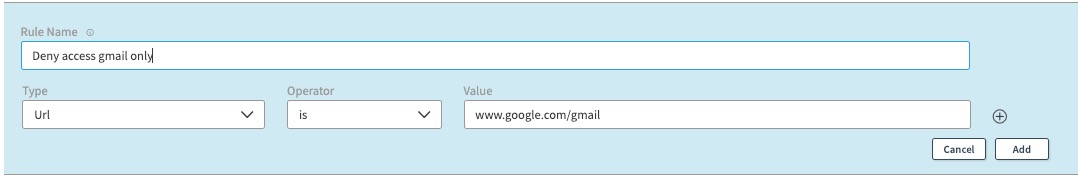
However, this rule will not deny access to www.google.com/docs or www.google.com and the user is allowed access, since they are not substrings of www.google.com/gmail.
Redirect to custom URL page or custom Access Denied page
If you want to redirect the user to a custom URL page when access to an application is denied due to an ACL (excluding Device Posture tiers, tags, or versions) , you can configure authorization failure redirect options in the advanced settings of the IdP. Or, if you redirect the user to a custom EAA Access Denied Page, when access to an application is denied due to an ACL, you can configure a custom EAA access denied page in the advanced settings of the IdP.
Note
- Using ACL with custom URL or custom access denied page, is not supported if you use Device Posture Risk Tier or Risk Tag in your ACL.
- Using ACL with custom URL or custom access denied page, only works with Akamai IdP. It is not supported on third party IdP.
Note:
You can add access control rules for an Application.
Or alternatively,
You can also try out adding Access Ruleset to Application Access Groups. For more information, see our Beta feature, Connector Pools, Application Access Groups (AAG).
- Log in to Enterprise Center.
- In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
- Locate the application you want to configure ACL for.
- Click Access tab, enable Access option.
a. To create a new rule, click Add Rule (+).
b. To edit an existing rule, click Edit Rule.
A modal window appears.
-
Enter a name for the rule and click Add.
-
Select a Type for the ACL. See Access Control Type table above.
-
In Operator select either
isoris not. -
In Value enter the value if applicable or select the value for the access control type.
a. Click Time to configure the time-based settings.
b. In Start Time and End Time enter a time in hh:mm, AM-PM format.
c. In time zone select a timezone.
d. Select the days of the week that you want to deny access.
e. Click Save Rule (✓).
The rule appears as Access Control in the Services column. -
To add another criterion to the rule click Add Criteria (+), and repeat the above steps.
-
To delete the rule, click the Delete Rule (trash icon), and click Delete.
-
To edit the rule, click the Edit Rule (pencil icon), and make the edits, and click Save Rule.
-
Click Back to Configuration Services, and save these changes.
-
Click Save and Deploy, to make these changes to go into effect.
-
(optional) If you want to set up a custom EAA Access Denied Page for access denied due to ACL, you can configure a custom EAA access denied page in the advanced settings of the IdP.
-
(optional) If you want to redirect the user to a custom URL page when access to an application is denied due to an ACL, you can configure authorization failure redirect options in the advanced settings of the IdP.
Note: If you do not configure 14, 15, when the user is denied access to the application due to ACL, they will see HTTP 403 Forbidden message.
Updated about 1 year ago
