Use Unified Log Streamer to integrate EAA and SIEM
You can integrate Enterprise Application Access (EAA) with any Security and Event Management (SIEM) using the Unified Log Streamer (ULS). The ULS is designed to simplify SIEM integrations for all Akamai Secure Enterprise Access Products:
-
Enterprise Application Access (EAA)
-
Enterprise Threat Protector (ETP)
-
Akamai Multi Factor Authenticator (MFA)
The modular design of ULS allows out-of-the-box integration with many SIEM solutions such as Splunk, Graylog, or Sumologic platform.
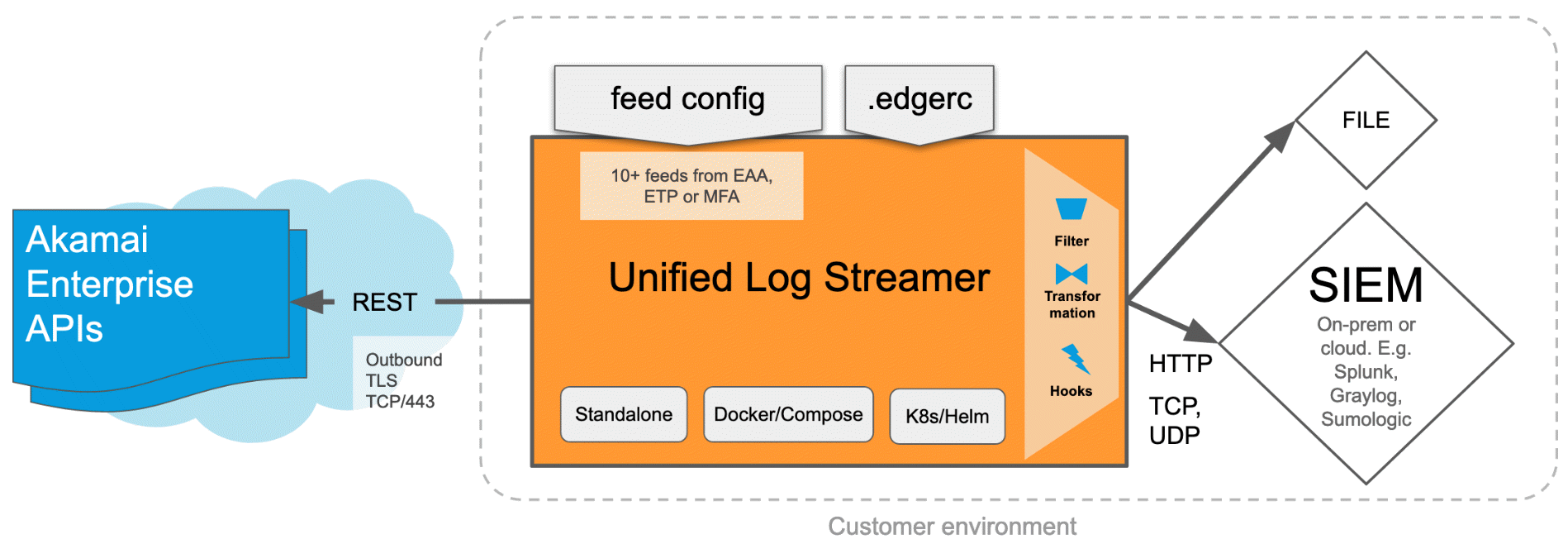
The ULS tool does REST API calls to Akamai Enterprise APIs and transports the data or security events which can be easily alerted by the customer's SIEM environment.
It is very flexible to deploy and operate the ULS. It can be run as a docker container or hosted standalone in your environment. It also supports the Helm deployment tool for Kubernetes, output Filter, Transformation, and Hooks, including the popular, flat "File" format. ULS can send data into any SIEM that supports either TCP, UDP or HTTP ingestion, both on-premises and cloud. Also, it is easy to get started since no coding or learning of the EAA APIs are required.
In Enterprise Application Access (EAA), we provide different data feeds like:
-
EAA access logs
-
EAA admin audit logs
-
EAA connector health
-
EAA Device Posture Inventory
You can choose any or all of these data feeds for your preferred SIEM solution.
You can find more information about the ULS open-source code on github at ULS repository.
You can find more information about documentation for any of the SIEM platforms at: SIEM repository.
To use the ULS tool in your SIEM environment:
-
You will need to setup EAA API credentials for ULS
-
Clone the binary from github ULS repository. Host it either as a Docker container or as a standalone binary on a host machine running Linux, macOS (Intel CPU).
Windows OS is not supported.
-
Configure any of the different feeds that you want to observe in your SIEM platform and obtain alerts for.
Updated 3 months ago
