About EAA Client
All new features and enhancements will be added to Akamai Zero Trust Client (AZT Client) instead of EAA Client. AZT Client 5.3 is in General Availability (GA).
EAA Client versions are supported for 15 months after its release. Note the following:
- EAA Client 2.8.1 on Windows, macOS, Ubuntu is supported until September 30, 2024.
Zero Trust Client combines and improves upon the functionality of EAA Client and ETP Client to provide a one-stop solution where you can secure access to enterprise applications and protect your network from threats.
To learn more about this client and how you can set it up for application access, see Zero Trust Client. You can find the latest version of Zero Trust Client by navigating to Client & Connectors > Manage & Download Clients > Version Control.
EAA Client
Enterprise Application Access (EAA) secures access to enterprise applications. The EAA solution delivers client-less access to browser-based (HTTP) applications and lets an organization secure access to remote desktop (RDP) and Secure Shell (SSH) applications.
The EAA Client is a software that you deploy on user's computer. Users may use different wireless networks and stay connected to their applications. A virtual private network (VPN) is not required to secure access. The EAA Client creates a separate network interface, and can work next to VPN.
The EAA Client provides the capabilities of single sign-on (SSO) authentication and multi-factor authentication (MFA) solution.
You can control access to applications that are not browser based, run locally on the user's computer, and communicate over the Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or both protocols.
EAA Client setup overview
The EAA Client requires setup by both an EAA administrator and an IT administrator:
-
An Enterprise Application Access (EAA) administrator enables the client in the advanced settings of the identity provider's configuration in EAA and deploys the identity provider (IdP). For more information, see Enable EAA Client in an identity provider.
-
Next, the EAA administrator creates a client-access application that is configured with an internal hostname. The internal hostname is the hostname of the application on the user's computer. The internal hostname communicates with the actual application or application server. For more information, see Client-access applications.
-
After an EAA administrator performs the required configuration in Enterprise Application Access, user can download the client from the EAA Login Portal and install it on their computer based on the operating system.
In most cases an IT administrator installs and distributes this software with the solution their organization uses to manage network devices. For a list of system and network requirements that apply to the client, see Requirements.
-
After the EAA Client is installed launch the configuration wizard and configure the client.
-
After the EAA Client is running, a loopback DNS proxy is configured to capture the system DNS requests. This means that EAA Client monitors all DNS traffic to and from the user's computer. The internal hostname is used to identify and intercept all traffic of interest to EAA Client. If EAA Client traffic is detected, the loopback proxy responds to these DNS requests. The loopback DNS proxy forwards requests that are not related to the EAA Client upstream in the network are forwarded for resolution.
EAA Client architecture
The below scheme shows high-level flow for each TCP-type client access application.
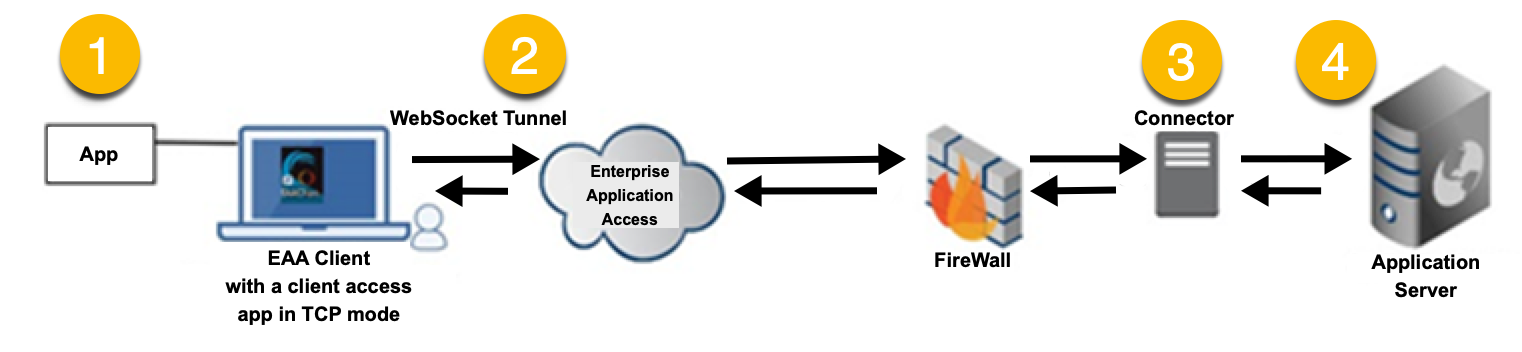
For each application (1), a WebSocket tunnel is created and the traffic is directed to the EAA Cloud (2). Unlike a VPN, this tunnel does not provide access to the entire network. It only establishes connectivity to the authorized application. From the EAA Cloud, traffic is directed to the connector through the firewall (3). Traffic is then forwarded to the application server (4). For example, if you configure the Outlook client as a client access application, this traffic is directed to the Microsoft Exchange server.
The below scheme shows high-level flow for each tunnel-type client access application.
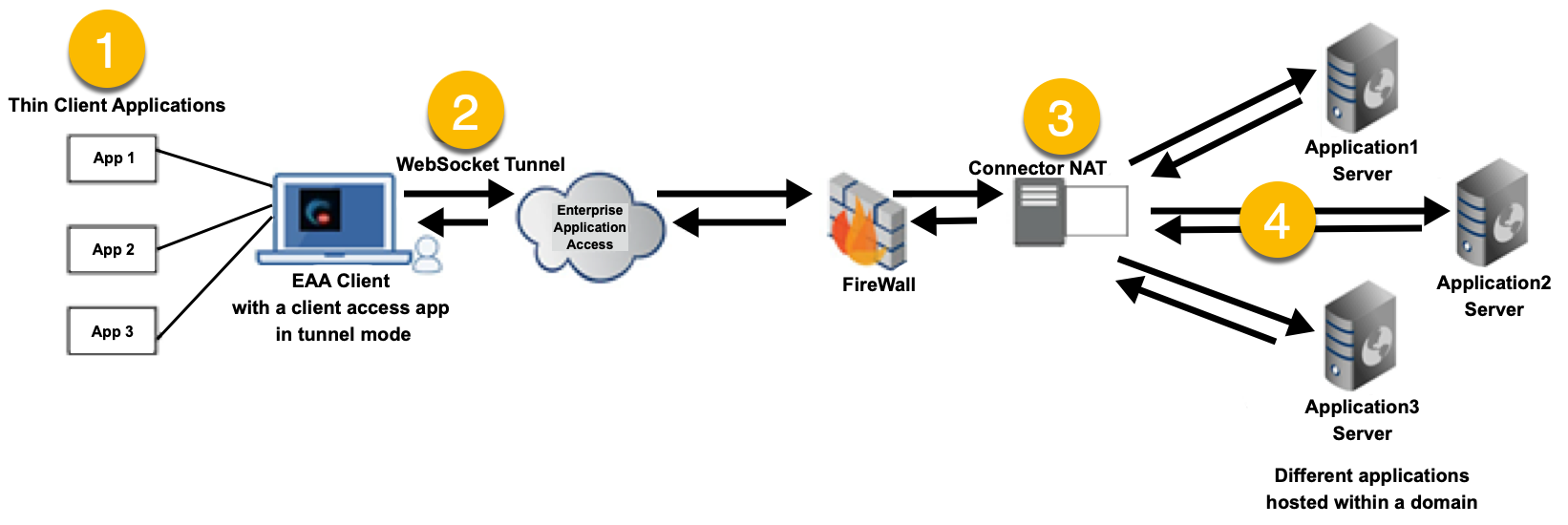
A tunnel-type client access application establishes connectivity for the entire domain or the organization. Unlike a traditional VPN, it provides secure access to one or more applications (both TCP and UDP) and to one or more groups within your organization (1). However, it does not provide secure access to the entire network. A WebSocket tunnel is created and the traffic is directed to the EAA Cloud (2). The connector (3) does a network address translation (NAT) after resolving the subdomains. This each application communicate securely with its application server respectively, through the configured internal host on the computer (4). IT administrator can selectively exclude certain applications in certain subdomains from being intercepted by the EAA Client. For more details see Set up DNS exceptions.
Updated 6 months ago
