Basic configuration of an IdP
With Enterprise Application Access (EAA) as your service provider (SP), you must identify identity providers (IdP) within EAA and assign them to an application in order to authenticate SAML and Single sign-on (SSO) authentication for those applications.
When it comes to directories, if you use either EAA's Cloud Directory or an Active Directory (AD), you can use EAA as both your SP and IdP. This does not generate any SAML.
Decide which IdP provider type to use up to the preference of your business. If no IdP has been used before, you can use a custom SAML IdP type. Add a new IdP and use it to authenticate multiple applications.
In EAA you can use a third-party SAML IdP or EAA as the SAML IdP to authenticate access to your applications. When an IdP such as EAA and a SP such as a SaaS application both implement SAML, they are able to authenticate accredited users associated with the IdP to use the SP.
Identity provider types supported by Enterprise Application Access:
- Akamai
- Microsoft Azure AD
- Okta
- OneLogin
- PingOne
- Third party SAML
- Third party OIDC
Note:
You can add a new IdP, add directory, and assign the IdP to an Application for authentication.
Or alternatively,
You can also try out adding Identity Ruleset to Application Access Groups. For more information, see our Beta feature, Connector Pools, Application Access Groups (AAG).
Add a new identity provider
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Click Add Identity provider (+).
-
Enter a name, description, and select the provider type as Akamai.
-
Click Continue. The Identity Provider Details page appears.
-
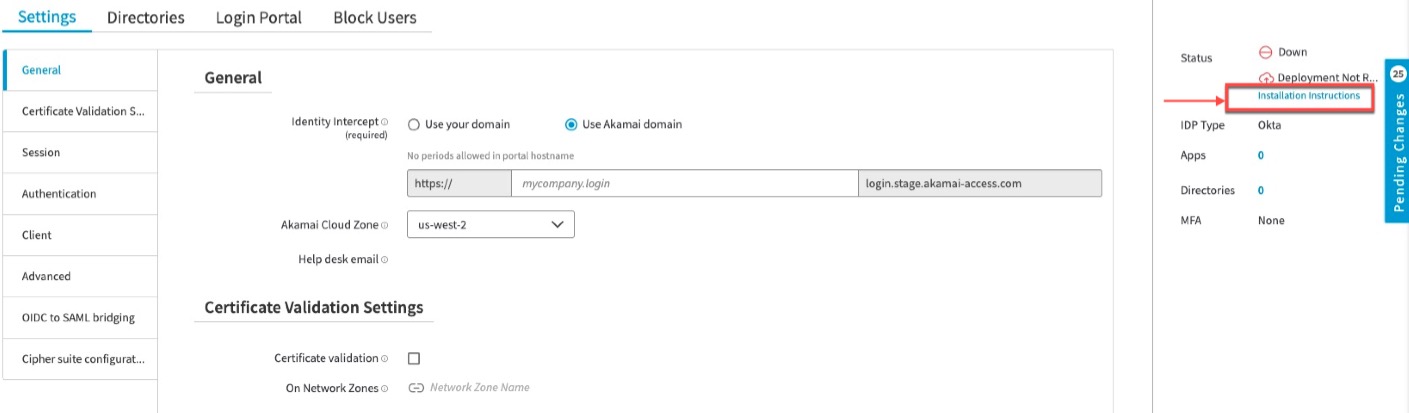
In Settings > General enter a URL for the Identity Server for Akamai IdP or Identity Intercept for a third-party IdP.
You can select Use Akamai domain or Use your domain. If you use your own domain use a self-signed certificate, or use the uploaded custom certificate.
If you are adding a new, third-party IdP, Okta, or Microsoft Azure AD as IdP, click Installation Instructions on the right, for portal type specific instructions to configure Enterprise Application Access as the SP with that IdP.
14 days before the certificates expire, an IdP changes the Deployment Status to Deployment Not Ready and will be IdP Down count. You should renew the certificate before expiry and deploy again the IdP, although the IdP would work fine during the expiration warning period.
- For the identity provider, in the general settings, choose the Akamai Cloud zone closest to the majority of the users base. It is in the
Client-*form, for exampleClient-US-East, or justUS-East, since the identity provider can be used for Client-access applications or client-less applications in any cloud zone. For tcp-type or tunnel-type client-access applications use Akamai Cloud zone , for exampleClient-US-East, orClient-US-West, closest to the application in the data center. - To save the changes click Save.
Next, add a directory to an identity provider.
Add a directory to an identity provider
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Select your identity provider to open it.
-
Click Directories tab.
-
Click Add Directory (+).
-
Select the directory from the list. You can also filter by the directory name.
If you are a first time user, select the Cloud Directory .
-
Click Add Directory.
The selected directory appears in Directories.If you have more than 20 directories configured, only the first 20 directory cards are listed in Directories.
-
You can leave the default settings in the Login portal.
-
Click Save.
On the right panel, for Deployment you will see , Ready for deployment .
Assign identity providers to an application
Prerequisites:
-
Make sure the identity provider you want to use is set up in Enterprise Application Access. See Add a new identity provider. Then, Add a directory to an identity provider.
-
With Enterprise Application Access (EAA) as your service provider (SP), you must identify identity providers (IdPs) within Enterprise Application Access and assign them to applications in order to authenticate SAML and single sign-on for those applications.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Select the application to open it.
-
To add authentication to the application, select Authentication.
-
Enable Authentication.
-
In Identity provider select an identity provider from the list.
-
Click Assign Directory and select one or more directories from the list.
-
Click Associate.
The directory appears under the Assigned Directories and the application summary. -
Click Save.
-
To set up services, select Services.
-
Click Save.
Deploy the identity provider
Put configuration changes to an identity provider (IdP) into effect. Changes to identity providers (IdPs) in Enterprise Application Access (EAA) go into effect after you deploy the IdP, similar to the deployment of applications. After you create or change the configuration of an IdP in EAA, deploy the IdP.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Select your identity provider to open it.
-
Hover over to Deployment of the identity provider, and if there are no errors, you see Ready for deployment.
-
Click Deploy IDP.
Pending Changes appears. All the pending deployment changes are shown. Make sure thatIDP2is selected. If you select any other identity providers, they are simultaneously deployed. -
Click modified, to check the changes you have done with the previous version.
-
Click Deploy and add a Deploy Confirmation message in the dialog box, and click Deploy. The deployment may take several minutes to complete. After it is done, you see the completed deployment flow.
Identity provider health and deployment status
Interpret the health and deployment status of the identity provider based on icons on the identity provider page. The identity provider (IdP) health status and deployment status information is available in the identity providers section of the EAA Enterprise Center.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Identity & Users > Identity Providers.
-
Select your identity provider to open it.
The health and deployment statuses are independent of one another and both appear as icons. -
To determine the health status of an IdP, check the icons and corresponding descriptions in the Health column. Red indicates that the IdP is down and green indicates that the IdP is up.
-
To determine the deployment status of an IdP, check the icons and corresponding descriptions in the Deployment column. Red indicates that the IdP is down, yellow means that you can deploy the IdP, and green indicates that the IdP is up.
-
IdP is deployed. A green cloud means the IdP is successfully deployed and can be used with applications.
-
Ready for deployment. A yellow cloud means the IdP is configured correctly, but admin needs to [deploy the IdP] (doc:add-new-idp).
-
Deployment not ready. A red cloud means the IdP is not configured correctly.
-
Deployment failed. A red cloud means the IdP deployment failed. This happens if any of the configurations were not set correctly and you pressed Deploy identity provider.
-
-
To see more details, open the selected IdP and hover over the Deployment icon.
You can troubleshoot some of the configuration issues from IdP deployment status page.
Updated 11 months ago
