Multifactor authentication
Multifactor authentication (MFA) is an access control method where multiple, separate pieces of evidence are required for identification before access is granted. Typically at least two of the following categories must be satisfied for MFA: knowledge (something they know), possession (something they have), and inherence (something they are). Using two different components to confirm identity is known as two-factor authentication (2FA).
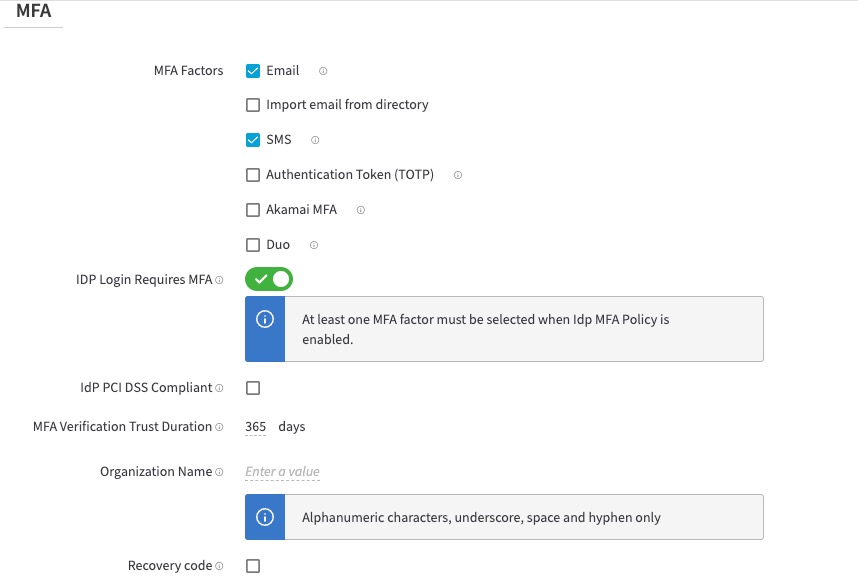
You can configure MFA by selecting an Akamai identity provider on the IdP list page, and clicking on the MFA tab. There are different MFA methods like Akamai MFA, Duo, and other native methods like email, SMS, Authentication token (TOTP) for receiving authentication tokens by the end-user. For time-based one-time password(TOTP) authenticator, the end-user must set up a third-party app like Google authenticator on their device where they wish to receive second-factor tokens. EAA also allows the end-user to receive recovery codes from the admin if they do not have access to the registered second-factor device after the organization validates the authenticity of the user for the native methods.
Note
New customers will only see Akamai MFA and Duo in your contract. Existing customers will be able to see other native methods.
SMS and email messages will have the format <Organization name>:<OTP code>. Organization name is obtained from the value you provide for the Organization Name.
If you enable MFA to access EAA applications and SMS is the registered MFA scheme, SMS message is sent at the time of registration and when you receive onetime password (OTP) code for authentication.
Example of the registration SMS:
Phone verification code from <Organization name>: <OTP code> This SMS may incur charges from your telephone operator.
Example of the SMS sent as OTP for authentication:
Access code from <Organization name>: <OTP code> This SMS may incur charges from your telephone operator.
Enable a global MFA for Login Portal users
When you enable MFA for an Akamai identity provider, it is a global MFA policy. This policy is applicable to all applications and directories associated with this identity provider. To enable MFA when as user logs into the Login Portal or IdP follow this procedure:
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Select your identity provider to open it.
-
In Settings > MFA enable App Login Requires MFA. This ensures that the user is challenged with MFA to be logged into the IdP session.
-
Select any of the MFA factors to apply like Email, SMS, TOTP, Akamai MFA, or Duo. You can select one or more of these MFA methods:
- For email, you can import the email from the directory by checking the option.
- For receiving authentication tokens on a time-based one-time password (TOTP) authenticator, the end-user must install google authenticator for TOTP.
- For DUO, see Use Duo MFA.
- For Akamai MFA see Use Akamai MFA.
Note: Do not select the IdP PCI DSS Compliant checkbox. If you want to use PCI DSS Complaint MFA see PCI DSS compliant MFA
If you select multiple MFA factors, the end-user is prompted to the enrollment options page where they are shown all the MFA methods including Akamai MFA. They can use the onscreen guidance to select the primary method and the backup methods for authentication. See Set up MFA to receive tokens on the end-users device for how end-users can set up multiple MFA methods.
- Set MFA Verification Trust Duration. The user is prompted for MFA verification the very first time they use the browser. Then, within the trust duration period, the user is exempt from MFA challenge if they use the same browser. The default is 365 days.
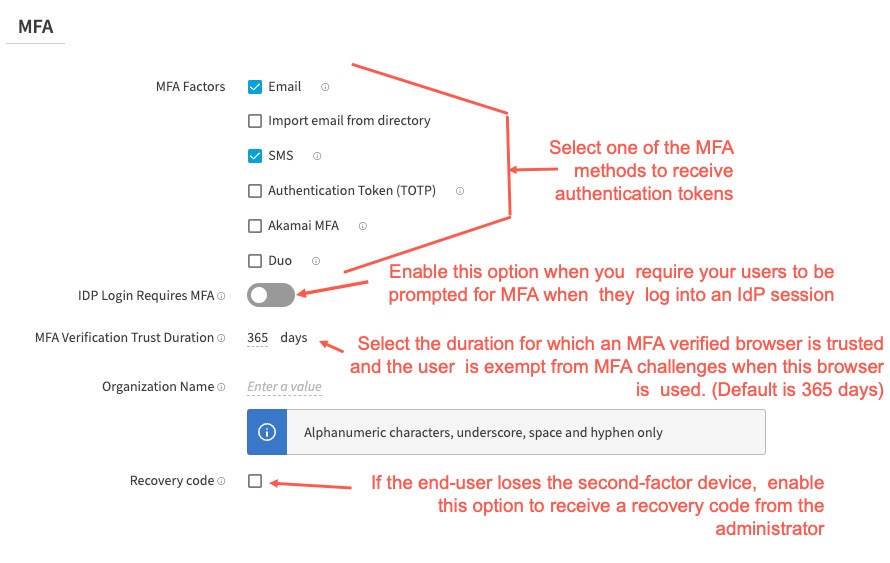
- Click Save.
- Deploy the identity provider.
Note: If you configured the IdP login portal to support a different primary language other than English, then the MFA is received in that language.
Enable or disable MFA for each application
Enable or disable multifactor authentication (MFA) per application. Apply disable bypass MFA criteria per application. This procedure is useful when you need global MFA for an identity provider (IdP) but you need to exclude an application from using the MFA policy of the IdP. Or, you do not have a global MFA policy, but you want to add a custom MFA policy for only one application. Or, if you've set bypass MFA criteria in the IdP, and you want to override it for an important application even if the user is with the corporate network, using a managed device, or using IWA, you can set the disable bypass MFA criteria. Then, the user is prompted for MFA required for accessing that application.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Select your application to open it.
-
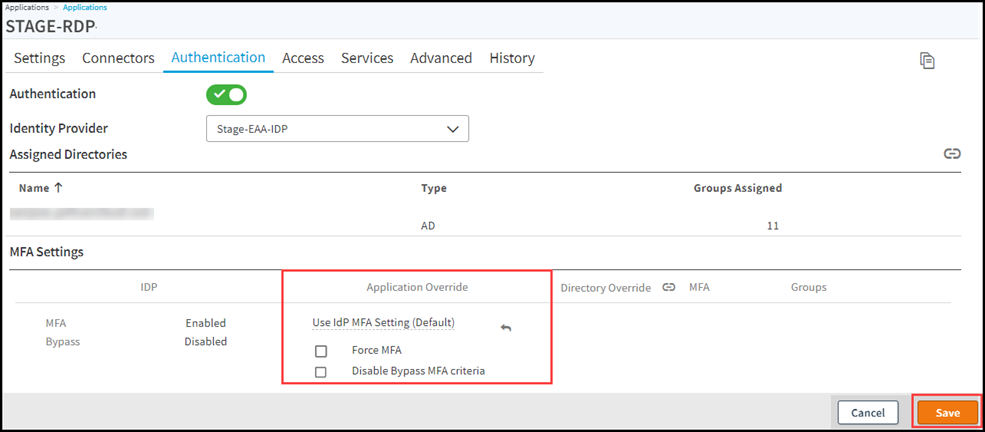
In Authentication > MFA Settings IDP section displays settings that you configured when you enabled MFA for your identity provider.
In Application Override select one of the choices:-
Enable. You might want to require users to use MFA for just this application, although the IdP might not have MFA.
-
Disable. You might want to not require users to use MFA for just this application, although other applications keep the MFA settings of the IdP.
-
Use IdP MFA Setting (Default). You might want to keep the same MFA settings as set in the IdP and not change it.
-
Force MFA. If you want your users to be prompted for MFA every time they login to the application.
-
Disable Bypass MFA criteria. Select this option if you want to disable the evaluation of bypass MFA criteria you set in the IdP. Then, the user is prompted for MFA for this application even if any of the criteria is met.
Select this option, only if you have set any Bypass MFA criteria in the identity provider.
-
- Click Save.
- Deploy the application.
Enable or disable MFA for each directory or a certain group
Enable or disable multifactor authentication (MFA) for each directory on an application or for some groups within the directory. By default, the directory inherits the MFA settings from the application. You can override this in the directory MFA settings.
If you have two active directories (ADs) assigned to the IdP of an application, for example, one is AD San Francisco and the other is AD New York, use this procedure to select just one directory to have MFA for the application.
Or, you can have MFA for users who are members of certain groups within the directory. Then MFA is prompted for users in those groups. All other users in other groups in that directory are not asked for MFA.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Select your application to open it.
-
Select Authentication > MFA Settings.
The MFA Settings section contains the configured IdP and application data. -
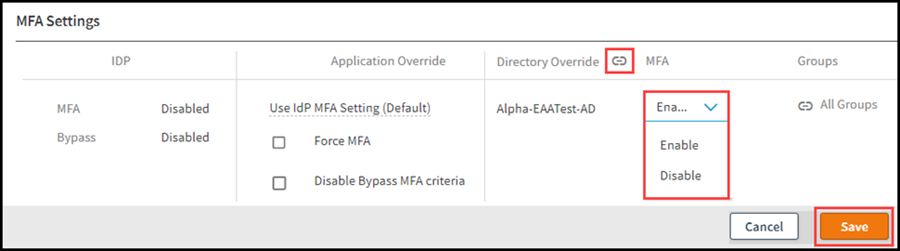
Click Select Directory to override MFA and select the directory that you want to configure. Click Associate.
-
For the selected directory, you can select one of the MFA configuration options:
-
Enable. If you want all users in this directory to be prompted for MFA before accessing this application.
-
Disable. If you want all users in this directory to not be prompted for MFA before accessing this application. All other applications under the IdP keep the same MFA settings.
-
-
Click Assign Directory and enable the selected MFA Settings for specific groups. Filter and select users and click Associate. Use this option if you want users belonging to specific groups in the directory to use MFA.
-
Click Save.
When you’re enabling MFA for a specific group, you can filter for the groups you want using the entering few characters of the groups name. Select the groups and click Save. To apply MFA to all groups, select the checkbox next to Search field and click Associate. To make changes or deselect all click the same checkbox.
For example, you have 11 groups in this directory. The admin has allowed MFA for only the RDP and Engineers groups. The other users will not be prompted for MFA although they belong to the same directory.
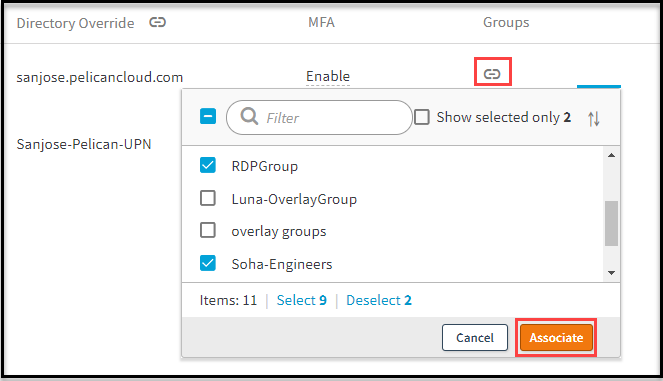
- Click Save.
- Deploy the application.
Inheritance rules for MFA policy between identity provider, applications, directory, and groups.
When you configure MFA for an Akamai identity provider (IdP), it is a global setting. It is inherited by all applications and directories associated with the IdP (by default). The global IdP MFA settings can be overridden for each application. The application MFA settings is inherited by the directory MFA settings (by default). The application MFA settings can be overridden for each directory or a group within a directory.
Updated 11 months ago
