Get started with a TCP-type client-access application
If you want to secure access to a single TCP application with a single hostname, you can use a TCP-type client-access application. This type of application, such as Microsoft Outlook, is created for a single TCP application (perApp) and supports TCP only. All TCP-type client-access applications are fully backward compatible with the latest Enterprise Application Access Cloud.
TCP-type client-access app lets you set up access control rules or services like the Enterprise Application Access solution used for secure access for HTTP applications.

For each application (1), a WebSocket tunnel is created, and the traffic is directed to the Enterprise Application Access Cloud (2). Unlike a VPN, this tunnel does not provide access to the entire network. It only establishes connectivity to the authorized application. From the Enterprise Application Access Cloud, traffic is directed to the connector through the firewall (3). Traffic is then forwarded to the application server (4). For example, if you configure the Outlook client as a client-access application, this traffic is directed to the Microsoft Exchange server.
With this workflow, a single TCP application is secured by Enterprise Application Access. Users are able to access the application with the configured internal host. If there are multiple desktop applications, then multiple TCP client applications need to be configured.
Set up a TCP-type client-access application and learn how to:
-
Create and install a connector in the Amazon AWS environment.
-
Add users to the Enterprise Application Access Cloud directory.
-
Create an Akamai identity provider (IdP) with EAA Client and Device Posture settings enabled.
-
Associate the directory and deploy the IdP.
-
Configure a TCP-type client-access application with Device Posture risk tiers and tags as ACLs. With tiers and tags, you can restrict users that try to access the TCP-type app on risky or compromised devices.
-
Add authentication with the IdP for the TCP-type application.
-
Verify that a user can access the TCP-type application using the external hostname.
Depending on the user's operating system you need to:
Start with a simple configuration:
-
Use the cloud directory in Enterprise Application Access (do not use any other Active Directory or LDAP).
-
Use the Akamai cloud domain (do not use any custom external domain). You do not have to configure and upload certificates.
Create, download and install an Access Identity Connector
Create and deploy a connector for the Amazon AWS environment to be used for any TCP-type client-access application.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Clients & Connectors > Access and Identity Connectors.
-
Click Add New Connector (+).
-
Enter a connector name and an optional description.
-
Select a connector package type.
The package type corresponds to the virtual environment where you are installing the connector. For example, if you install the connector on the Amazon AWS environment, select package type Amazon AWS EC2/VPC. -
Enable Debugging.
-
Click Save Connector (✓).
The status of the connector changes to Created (Download CloudFormation Template). -
Click the connector status.
The connector file opens in a separate browser window. -
Download and save the connector file.
The connector file is used later to set up the connector in the virtual environment. -
Log in to your AWS console and click AWS services menu > AWS CloudFormation > CREATE STACK.
-
Under Create Template select Upload a template to Amazon S3.
-
Click Choose File and select the downloaded CloudFormation template file.
-
Enter a stack name, NAT instance type, VPC ID and subnet information and click Next.
For the NAT instance type recommended minimum is of
m4.large.- Complete the configuration of tags, storage, and other features as needed. Since AWS does not use swap space for storage use a minimum of 12 GB RAM.
-
-
Click CREATE.
Once the stack creation is complete, the connector instance starts and automatically connects to the EAA Cloud. -
Return to the Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Clients & Connectors > Access and Identity Connectors.
-
Search for your connector and click Approve next to it.
-
Verify that the connector shows the private and public IP addresses assigned to it. This may take a few minutes.
The connector reaches out to the EAA Cloud after installation. The status changes to Ready. Connector is running.
The connector can do dialouts from the data center to the EAA Cloud, connecting the application inside the data center to the Internet through the EAA Cloud and the user.
Next, add users to the cloud directory.
Add users to the cloud directory
You need to add users who can access the web application to the cloud directory.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Directories.
-
Select Cloud Directory.
-
In Users click Add New User (+).
-
Enter email, first name, and last name.
-
Click Send Invite. New users receive an email to create a password and complete their account authorization.
-
-
Click Save User Changes (✓).
New users are now added to the Enterprise Application Access default directory - EAA Cloud directory.
Next, create an Akamai Identity provider (IdP).
Create an Akamai Identity provider (IdP), associate the cloud directory, and deploy the IdP
Identity providers (IdPs) manage user identity information and provide single sign-on (SSO) and multi-factor (MFA) authentication.
Associate IdP to the previously created directory to allow users to authenticate to your TCP-type client-access application.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Identity & Users > Identity Providers.
-
Click Add Identity provider (+).
-
Enter a name, description, and select the provider type as Akamai, for example,
IDP2. -
Click Continue.
-
-
In Settings > General > Identity server enter a URL.
-
In Client select both Enable EAA Client and Enable Device Posture.
With this configuration, you can set access control rules (ACLs). -
Click Save.
-
-
In Directories click Associate (+).

-
Select Cloud Directory and click Associate.
The cloud directory appears under Directories. -
Leave the default settings in the Login portal.
-
Click Save.
Hover over the Status of the Identity provider, if there are no errors, Ready for deployment appears.

-
Click Deploy IdP.
Pending Changes appears. All the pending deployment changes are shown. Make sure that
IDP2is selected. If you select any other IdPs, they are simultaneously deployed.
You can click modified, to check the changes you have done with the previous version.

-
Click Deploy and add a Deploy Confirmation message in the dialog box and click Deploy.
The deployment may take several minutes to complete. When it's ready, the completed deployment flow and IdP is Deployed appear.

The cloud directory is now associated with the identity provider. This enables users from the directory to access applications associated with the identity provider.
Next, configure your application.
Configure a TCP-type client-access app with Device Posture ACLs
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Click the Add Application (+).
-
In Type select Client-Access App and in Mode select TCP mode (single port, port mapping, load-balancing options).
-
Enter application Name and optional Description.
-
-
Click Add Application and in App Settings configure the following:
-
Application Host. Enter the hostname of the client access application. This is the hostname that the native client uses to communicate with the application or application server. For example, if you are configuring a client like Outlook, this would be the hostname that is associated with Outlook accounts in your organization such as
mail.mydomain.com, and is used to communicate with Microsoft Exchange. -
Port. Specify the same port number, as you are going to add for the application App Server IP/FQDN. The EAA Client listens for traffic on this port from the user's computer.
-
Endpoint Host. Enter the external host of your application. This is the cloud endpoint for all
communications between the client access application and Enterprise Application Access.

-
Additionally, select one of these domains:
-
Use your domain. If you use your own custom domain, provide a certificate configured as a complete bundle with all the subordinates (having the full chain of trust), otherwise you get a web-socket error. To use an uploaded certificate, select Use uploaded certificates and select the previously uploaded certificate.
-
Use Akamai domain. If you use an Akamai domain no certificate is needed. For the purpose of this Get Started Guide, let's select the Akamai domain.
-
Akamai Cloud Zone. The cloud zone should be a geographic location that is closest to the data center where your application server resides. The Akamai Cloud Zone can start with
Client-*like inClient-US-East,Client-US-West. It is the zone closest to the application in the data center.
-
Click Save.
-
To add connectors to the application go to Connectivity, Authentication and Access section. Click Connectors.
More than one connector is recommended for high availability and load balancing.
- Click Add connector and select one or more connectors. Click Add Connector.
To remove a connector, click Remove Connector next to it.
The associated connector appears under the Connectors.
The connector should run to deploy the application.

- Click Add connector and select one or more connectors. Click Add Connector.
-
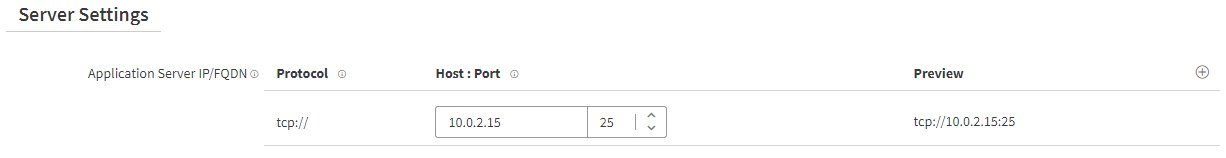
To add Application Server IP/FQDN and Port to the application configure the following:
-
In Application Server IP/FQDN enter the IP address or fully qualified domain name (FQDN).
-
In Port enter the port of the TCP application. It should be the same port number as you entered in the previous steps in the App Settings.
-
To configure multiple applications servers for load balancing, click Add New Server (+). Enterprise Application Access supports various load balancing techniques including round-robin, session or cookie stickiness, and source IP hash in Advanced.
-
To add an access control rule (ACL) to the application in Access enable Access.
For Device Posture ACLs to work, set up EAA Client with Device Posture enabled. -
To create a new rule, click Add Rule (+) in Deny Access Rules.
-
To edit an existing rule, click Edit Rule.
The rule settings dialog appears.-
In Rule Name enter a name for the rule and click Add.
-
In Type select Device Risk Tier.
-
In the Operator menu leave
is. It is the default value for Device Posture risk tiers. -
In Value select High.
-
-
Click Add Criteria (+) and configure the following:
-
In Type select Device Risk Tag.
-
In the Operator menu, appears
is not, that is the default value for Device Posture risk tags. -
In the Value select a tag. For example, you can apply a tag that groups devices that are not IOS devices.
-
Click Add.
-
-
Click Save Rule.
With this ACL configuration, a user accessing the TCP-type client-access application from a machine that falls into a high-risk tier, and is not a IOS mobile device, that's basically a Windows PC with a low risk tier is allowed to access to the application.

Next, configure the authentication source and deploy your application.
Configure the authentication source, and deploy the application
Assign the previously deployed IdP and directory to the TCP-type client-access application and deploy your app.
-
Log in to Enterprise Center.
-
In the Enterprise Center navigation menu, select Application Access > Applications > Applications.
-
Click your application.
-
To add authentication to the application in Authentication enable Authentication.
-
In Identity provider, select your identity provider.
-
Click Assign Directory and select one or more directories.
-
Click Associate.
The directory appears under the Assigned Directories.

-
Leave the default configuration in History and click Save.
Hover over the Deployment symbol, if all configurations are correct, Ready for Deployment appears.

-
Click the Deploy Application.
Pending Changes appears. All the pending deployment changes are shown. Make sure that the application you just configured is selected. If you select any other applications, they are simultaneously deployed. -
Click Deploy and add a Deploy Confirmation message in the dialog box, and click Deploy.
The deployment may take several minutes to complete. When it's ready, the completed deployment flow App Deployed appears.
Next, verify if you can access your application.
Verify you can access the TCP-type client-access application from the EAA Login Portal
-
Open a new tab and enter the external URL you created for the app in the previous steps. For example
https://mail.mydomain.stage.akamai-access.com. -
Log in with your username and password you created and added to the cloud directory.
You should be able to securely access the TCP-type client-access app.
If the user accesses themail.mydomainapp on a computer that was qualified as a high-risk device, they are denied access, since you set a corresponding ACL.
Updated about 1 year ago