Set up Active Directory Federation Services (AD FS) as a third-party SAML identity provider
Before you begin
-
Select a fully qualified domain name (FQDN) for your AD FS portal. For example,
https://<federation-service-name>/adfs/lswhere <federation-service-name> can appear in the format
adfs.yourdomain.com -
Install and configure AD FS in a Microsoft Windows operating system (2016 version). For more information, see AD FS product documentation.
Active Directory Federation Services is software installed on a Microsoft Windows Server operating system. It provides SSO and identity management, allowing authorized users to access websites and applications.
To set up AD FS as a third-party SAML IdP:
-
Add AD to SIA. Make sure you import groups into SIA. For more information, see Add a directory.
-
Download and deploy an identity connector. For more information, see Create and download an identity connector.
-
Associate the identity connector with the AD you created. For more information, see Associate an identity connector with a directory.
-
Assign the AD that you created in SIA to the AD FS IdP. For more information, see Assign AD to AD FS identity provider.
-
Add the URL of the AD FS server to an exception list. For more information, see Add identity provider domains to an exception list.
-
Authenticate SIA with AD FS. This process involves these steps:
-
Configuring Akamai Enterprise IdP as an AD FS endpoint. See Set up relying party trust in AD FS.
-
Configuring which AD attributes are sent from AD FS to SIA. The SIA administrator creates claim rules and adds them to the relying party trust. In AD FS, you can create claim rules that use the default claims template to send attributes like the email or username. You can also use custom claims to send group members from AD FS to SIA. See Use claims to send LDAP attributes from AD FS to SIA and Use custom claim description to send group membership from AD FS to SIA.
-
-
Enable signed SAML requests between SIA and AD FS. This is an optional step. It is required only if you want to use signed SAML requests.
-
Enable encrypted SAML responses between SIA and AD FS. This is an optional step. It is required only if you want to encrypt SAML responses for additional security
Add AD FS as a third-party SAML identity provider
To add AD FS as a third-party SAML IdP:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the plus sign icon.
-
Configure basic IdP settings:
-
In the Name and Description fields, enter a name and description of the IdP.
-
In the Provider Type menu, select Third-Party SAML.
-
Click Continue.
-
-
Complete these steps to configure general IdP settings:
-
Go to the General settings section or click the General tab.
-
For Identity Intercept, select Use Akamai domain. Enter a hostname. The identity intercept is the URL for the authentication page that is presented to users.
-
In the Akamai Cloud Zone, select a cloud zone that is closest to the user base.
-
-
Complete these steps in the Session section:
- For the Session Idle Expiry setting, enter a time that is 35 minutes or more.
- Use the default settings for the Limit Session Life and Max Session Duration settings.
-
To enable client certificate authentication, select the checkbox and configure the required parameters.
-
In the URL field of the Authentication section, enter the URL of the AD FS portal:
https://<federation-service-name>/adfs/lswhere <federation-service-name> is the fully qualified domain of the AD FS portal.
-
In the Advanced Settings section, select Enable Authorization.
-
Click Save.
Next steps
-
Add AD to SIA. Make sure you import groups into SIA. For instructions, see Add a directory.
-
Download and deploy an identity connector. For instructions, see Create and download an identity connector.
-
Associate the identity connector with the AD you created. For more information, see Associate an identity connector with a directory.
-
Assign AD to the AD FS IdP. For more information, see Assign AD to AD FS identity provider.
Associate an identity connector with a directory
Before you begin
Create, download, and set up an identity connector. For more information, see Create and download an identity connector.
An identity connector allows SIA to synchronize with your directory service. You may want to associate more than one identity connector to a directory for redundancy and scaling.
How to
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Directories.
-
Click the directory that you want to edit and associate with a new identity connector.
-
Click the Connectors tab.
-
Click the plus (
 ) sign in the upper right. Then select one or more connectors and click Associate.
) sign in the upper right. Then select one or more connectors and click Associate. -
Click Save.
Assign AD to AD FS identity provider
Before you begin
Confirm that you:
-
Added AD to SIA. For instructions, see Add a directory.
-
Downloaded and deployed an identity connector. For instructions, see Create and download an identity connector.
-
Associated the identity connector to AD. For instructions, see Associate an identity connector with a directory.
To review the overall setup process for adding AD FS as a third-party SAML IdP, see Set up Active Directory Federation Services (AD FS) as a third-party SAML identity provider.
To assign your AD to your AD FS third-party SAML IdP:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the name of the AD FS IdP.
-
Click the Directories tab.
-
Click the link icon and select the AD that you added.
-
Click Associate.
Next steps
-
Add the URL of the AD FS server to the SIA network configuration. For more information, see Add identity provider domains to an exception list.
Set up relying party trust in AD FS
Before you begin
Make sure that you set up AD FS as a third-party SAML IdP, add AD, and deploy an identity connector. For instructions, see Set up Active Directory Federation Services (AD FS) as a third-party SAML identity provider.
To allow Akamai Enterprise IdP to redirect users to the AD FS login portal for completing authentication, you need to setup Akamai Enterprise IdP as an AD FS endpoint. This is done with a relying party trust.
Relying party trust is a term used in Microsoft Windows Server system to identify service providers that can communicate with an AD FS endpoint. In this procedure, you configure Akamai Enterprise IdP as an AD FS endpoint.
To learn more about creating a relying party trust in AD FS, see Microsoft's documentation.
To set up relying party trust in AD FS:
-
From the AD FS Manager, select the Relying Party Trusts folder and add a new trust.
-
In the Add Relying Party Trust Wizard window, select Claims aware and click Next.
-
In the Select Data Source window, select Enter data about the relying party manually, and click Next.
-
Select Specify Display Name tab. Complete these fields:
-
Display name. Enter a name. For example,
IDP-RPT -
Notes. Enter optional notes. For example,
IDP is relying party.
-
-
Skip the Configure Certificate tab.
-
Select Configure URL tab. Complete these fields:
-
Select Enable support for SAML 2.0 Web SSO protocol.
-
For the Relying party SAML 2.0 SSO service URL, enter the URL as
https://<idp-fqdn>/saml/sp/response, where is the FQDN of the IdP you created.
-
-
Select the Configure Identifiers tab. Enter the same value as the previous step for Relying party trust identifiers. Enter
https://<idp-fqdn>/saml/sp/response. -
Select the Choose Access Control Policy tab. You can configure all users, users of a specific AD, and users of a specific group, as shown in this example:
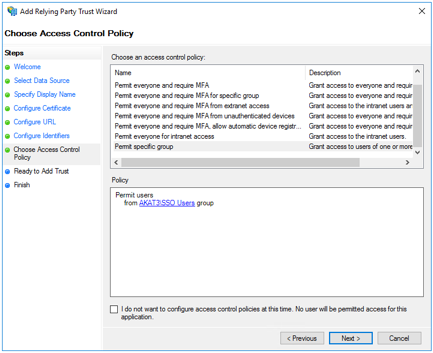
The SIA administrator can add multiple attributes for different access control policies.
- Click the Finish tab. This completes adding SIA as a Relying party trust in AD FS using the Add Relying Party Trust Wizard.
Next steps
-
If you are sending simple Lightweight Directory Access Protocol (LDAP) attributes from AD FS to, see Use claims to send LDAP attributes from AD FS to SIA.
-
If you are sending complex attributes like group membership from AD FS to SIA, see Use custom claim description to send group membership from AD FS to SIA.
Use claims to send LDAP attributes from AD FS to SIA
Before you begin
Set up relying party trust in AD FS.
To redirect users to the AD FS login portal to complete authentication, you also need to configure the LDAP attributes that are sent from AD FS to Akamai Enterprise IdP using claims.
Claims rules control which AD attributes are returned to the relying party endpoint once a user authenticates.
To match an LDAP attribute to the Name ID outgoing claim type:
-
Right-click on the relying party (for example, IDP-RPT) and select Edit Claims Issuance Policy.
-
Click Add Rule...
-
Select the default Send LDAP Attributes as Claims template. This template allows the IT administrator to use any of the LDAP attributes for claim rules. The Add Transform Claim Rule wizard appears.
-
Complete these fields:
-
Claim rule name. Enter a custom claim rule name.
-
Attribute store. Select Active Directory.
-
Map an LDAP attribute to the Name ID Outgoing Claim Type.
Note the LDAP attribute you select needs to match the login preference that you specified for the directory in SIA. For example, if you selected User Principal Name for the login preference, select User-Principal-Name.
-
-
Click Finish.
-
Click OK to save in the Edit Claim Rules dialog box.
Next steps
Upload AD FS metadata to SIA IdP.
Use custom claim description to send group membership from AD FS to SIA
Before you begin
Set up relying party trust in AD FS.
To redirect users to AD FS login portal for completing authentication, you also need to configure the LDAP attributes that are sent from AD FS to SIA using claims.
Claims rules control which AD attributes are returned to the relying party endpoint once a user has been authenticated. For example, it could be the application user's email address or user's AD group membership information. The minimum requirement for SIA is the user's email address. It needs to be returned as a part of the Name ID attribute.
The IT administrator can create a custom claims description in AD FS, associate it with the correct LDAP attribute, and add it to the relying party trust. This allows AD FS to send the user's group membership to SIA.
To use custom claim description to send group membership from AD FS to SIA:
-
Go to Server Manager > Tools > AD FS Management.
-
Expand Service and select Claim Descriptions.
-
On the right, click Add Claim Description....
-
Complete these fields in the Add a Claim Description window:
-
Display name. Enter a display name. For example, Group (SIA)
-
Short name. Enter a short name. For example, groupetp.
-
Claim identifier. Enter
Group. -
Description. Enter a description. This is optional.
-
Click OK.
-
-
Right-click on the relying party trust (for example, IDP-RPT) and select Edit Claims Issuance Policy.
-
Click Add Rule
-
Select the default Send LDAP Attributes as Claims template. This template allows the IT administrator to use any of the LDAP attributes for claim rules. The Add Transform Claim Rule wizard appears.
-
Complete these fields:
-
Claim rule name. Enter a custom claim rule name.
-
Attribute store. Select Active Directory.
-
Map an LDAP attribute to an Outgoing Claim Type. Select Token-Groups for LDAP attribute and Group (SIA) from step 4a.

This associates your custom claim description to the Token-Groups LDAP attribute, enabling the handling of group memberships between AD FS and Akamai Enterprise IdP. In this example, the IT administrator configures a claim rule called "Group Membership Attribute" that fetches the SAML group assertion attribute from the AD and sends it out to relying party trust, which is Akamai Enterprise IdP.
-
-
Click Finish.
-
Click OK to save in the Edit Claim Rules dialog box.
Next steps
Upload AD FS metadata to SIA IdP.
Upload AD FS metadata to SIA IdP
Before you begin
See Set up Active Directory Federation Services (AD FS) as a third-party SAML identity provider.
To upload the IdP metadata from your organization's AD FS domain to the SIA IdP you created:
-
Go to your organization's AD FS domain and download the IdP metadata XML file.
For example,
https://<yourdomain.com>/FederationMetadata/2007-06/FederationMetadata.xml. -
Return to SIA and open the IdP you created for AD FS:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the name of the IdP you created for AD FS.
-
-
Go to the Authentication section and complete these steps:
-
Click Choose file next to Upload IDP metadata file.
-
Browse to the location of the file on your machine.
-
Click Open.
-
Click Save.
-
Next steps
-
Deploy the IdP configuration:
-
In the SIA IdP configuration, you can click the icon next to the Ready for Deployment status. A deployment icon also appears next to a failed deployment status in case you need to deploy the IdP again. This action starts the deployment process.
-
Deploy IdP configuration changes in the list of Pending Changes. For more information, see Deploy configuration changes.
-
-
Associate the IdP with a policy that's enabled for authentication. For more information, see Require authentication to access a website or web application.
Enable signed SAML requests between SIA and AD FS
To enable communication with signed SAML requests, configure both SIA and AD FS. This is an optional configuration:
-
Configure SIA for signed SAML requests
-
Configure AD FS for signed SAML request
Configure SIA for signed SAML requests
To configure SIA for signed SAML requests:
-
Return to your AD FS IdP in SIA.
-
Under Authentication Configuration settings, select Sign SAML Request.
-
Copy the certificate text to a new file called cert.pem and convert to a DER encoded certificate called cert.cer. Based on the machine, execute one of these commands based on your OS:
-
For a Windows machine, open a command window and enter:
CertUtil -decode cert.pem cet.cer -
For a Linux machine, open a terminal and enter:
Openssl x509 -outperform der -in cert.pem -out cert.cer
-
-
Click Save.
Next steps
-
Deploy the IdP configuration:
-
In the SIA IdP configuration, you can click the icon next to the Ready for Deployment status. A deployment icon also appears next to a failed deployment status in case you need to deploy the IdP again. This action starts the deployment process.
-
Deploy IdP configuration changes in the list of Pending Changes. For more information, see Deploy configuration changes.
-
Configure AD FS for signed SAML requests
To configure AD FS for signed SAML requests:
-
Return to the relying party trust. For example, IDP-RPT.
-
In AD FS manager, edit properties of relying party trust.
-
Under Signature tab, click Add.
-
Add the cert.cer file.
-
Click OK.
-
Since SIA uses internal CA certificates to sign SAML requests and AD FS does not trust them, disable revocation checking of the SAML response for SIA in the AD FS server:
-
Open a PowerShell window.
-
Type this command to disable AD FS from doing revocation checking for SAML responses from SIA:
Get-AdfsRelyingPartyTrust -Identifier https://<idp-fqdn>/saml/sp/response | Set-AdfsRelyingPartyTrust -SigningCertificateRevocationCheck None -EncryptionCertificateRevocationCheck None
-
Enable encrypted SAML responses between SIA and AD FS
To enable communication with encrypted SAML responses, configure both SIA and AD FS. This is an optional configuration:
-
Configure SIA to send encrypted SAML responses.
-
Configure AD FS for sending encrypted SAML responses.
Configure SIA to send encrypted SAML responses
To configure SIA to send encrypted SAML responses:
-
Return to SIA and open the IdP you created for AD FS:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the name of the IdP you created for AD FS.
-
-
Under Authentication Configuration settings, select Encrypted SAML Response.
-
Click Save.
Next steps
-
Deploy the IdP configuration:
-
In the SIA IdP configuration, you can click the icon next to the Ready for Deployment status. A deployment icon also appears next to a failed deployment status in case you need to deploy the IdP again. This action starts the deployment process.
-
Deploy IdP configuration changes in the list of Pending Changes. For more information, see Deploy configuration changes.
-
Configure AD FS for sending encrypted SAML responses
To configure AD FS for sending encrypted SAML responses:
-
Return to the relying party trust. For example, IDP-RPT.
-
In AD FS manager, edit properties of relying party trust.
-
Under the Encryption tab, click Browse.
-
Navigate to the certificate file cert.cer file.
-
Click OK.
Updated about 1 year ago
