Manage an identity provider
Complete these tasks to manage or modify an identity provider (IdP).
Add an identity provider
Depending on the IdP you're setting up, review the setup process for the IdP. For more information, see:
-
Set up Active Directory Federation Services (AD FS) as a third-party SAML identity provider
-
Set up Microsoft Azure as a third-party SAML identity provider
To add an IdP:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the plus sign icon in the upper right.
-
Complete the Name and Description fields and select the provider type in the Provider Type field. Then click Continue.
-
Configure identity server General settings:
-
Go to the General settings section or click the General tab.
-
Select Use Akamai domain.
If your organization is licensed for Enterprise Application Access (EAA), you can select Use your domain. If you choose to use your domain, you need to configure certificates in EAA.
-
Enter the external hostname that you want to use for the login portal. If you can select the Use your domain option, you can enter the FQDN.
-
In the Akamai Cloud Zone, select a cloud zone that is closest to the user base.
-
-
To configure session settings for the login page:
-
Go to the Session settings or click the Session tab.
-
In the Session Idle Expiry field, enter a time that is 35 minutes or more.
-
If you want to limit session time, make sure Limit Session Life is enabled.
-
In the Max Session Duration field, enter the maximum number of days for the session.
-
-
Consider whether you want to challenge users with multi-factor authentication for Internet access. Even if you require MFA for SIA, you may decide not to require MFA for Internet access. You can choose built-in MFA capabilities or a third-party MFA provider.
-
To configure a built-in MFA policy, go to the Authentication section or click the Authentication tab.
-
Enable IDP MFA Policy. This setting enables a global multi-factor authentication policy.
-
In the MFA Timeout field, enter the number of days that end user devices are registered.
-
In the Organization Name field, enter the organization name that you want presented in emails or text messages that are sent to users with token codes. This applies when Email and SMS are selected as MFA factors.
-
Select the factor that you want to use for multi-factor authentication. You can select more than one factor.
-
-
If your organization is licensed for Enterprise Application Access, you can do the following:
-
To enable EAA Client, turn on the Enable EAA Client toggle.
-
To use device posture, select Enable Device Posture.
EAA Client is required for device posture.
-
-
Customize the Login Portal. For more information, see Customize the Login Portal.
-
To configure IdP advanced settings:
-
Go to the Advanced section or click the Advanced tab.
-
To preserve the authentication cookie regardless of whether the browser is closed, confirm that Persistent Cookie is enabled. This cookie ensures that users don't need to enter credentials again after the browser window is closed.
-
If you want to allow lockout after failed login attempts, enable Temporary Account Lockout on Login Failures. Complete these steps:
-
In the Account Lockout Failed Attempts field, enter the maximum of failed login attempts.
-
In the Account Lockout Duration field, enter the amount of that's allowed for the lockout.
-
-
To associate a directory with the IdP:
-
Click the Directories tab.
-
Click the plus sign icon in the upper right.
-
On the window that displays, select one or more directories and click Associate.
-
-
Click Save to save your IdP or click Save and Deploy to both save and deploy the IdP.
If a "Deployment Not Ready" message displays when you try to deploy the Idp, you need to correct the issue as described in Make IdPs Deployment Ready.
Next steps
-
If you save the IdP without deploying it, you can use these options to deploy it.
-
Deploy IdP configuration changes as described in Deploy configuration changes.
-
In the IdP configuration, you can click the icon next to the Ready for Deployment status. A deployment icon also appears next to a failed deployment status in case you need to deploy the IdP again. This action starts the deployment process.
-
-
Assign the IdP to a policy. For more information, see Require authentication to access a website or web application.
Edit an identity provider
To edit the settings of an IdP:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Click the name of the IdP that you want to modify.
-
In the Settings tab, modify any of the settings.
-
In the Login Portal tab, define the appearance and language settings for pages in the Login Portal. For more information, see Customize the Login Portal.
-
In the Directories tab, associate or disassociate the IdP with a directory:
-
To associate a directory, click the plus (
 ) sign in the upper right. Then select one or more directories and click Associate.
) sign in the upper right. Then select one or more directories and click Associate. -
To disassociate a directory, hover over the directory and click the minus sign. Then click Disassociate on the window that displays.
-
-
Click Save to save your changes, or click Save and Deploy to save and deploy the IdP.
If a "Deployment Not Ready" message displays when you try to deploy the IdP, you need to correct the issue as described in Make IdPs Deployment Ready.
Next steps
If you saved your changes without deploying, you can deploy the IdP using these options:
-
If you're trying the new Enterprise Center interface, in the IdP configuration, click the icon next to the Ready for Deployment status. A deployment icon also appears next to a failed deployment status in case you need to deploy the IdP again. This action starts the deployment process.
-
Deploy IdP configuration changes in the list of Pending Changes. For more information, see Deploy configuration changes.
Delete an identity provider
You cannot delete an IdP if it is used by a policy to perform authentication. To delete such an IdP, navigate to the policy's Settings tab and choose a different provider in the Identity Provider field or set the Authentication Mode field to None.
To delete an IdP:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
Hover over the IdP and click the trash can icon that appears.
The trash can icon does not display if the IdP cannot be deleted.
-
On the window that displays, confirm the deletion.
Next steps
Deploy this update. For more information, see Deploy configuration changes.
Delete multiple identity providers
You can complete this action for IdP that are currently down.
To delete IdPs in bulk:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
In the IdP top menu, select the bulk action icon.
-
Select Delete Identity Providers.
-
Select the IdPs that you want to delete.
-
Click Delete Identity Providers.
-
Confirm the delete action, and click Yes.
Next steps
Deploy this update. For more information, see Deploy configuration changes.
Make IdPs Deployment Ready
A number of steps are required to deploy an IdP. The cloud icon on the main provider page indicates if all necessary steps are complete.
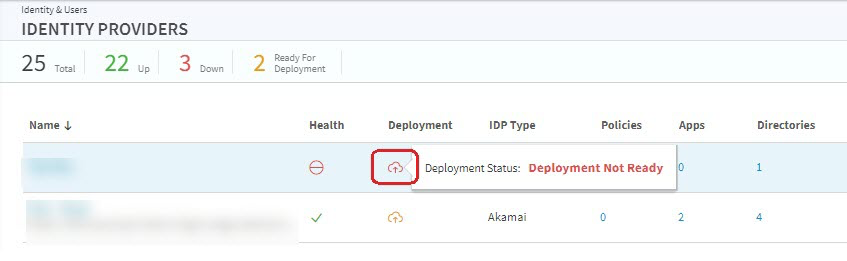
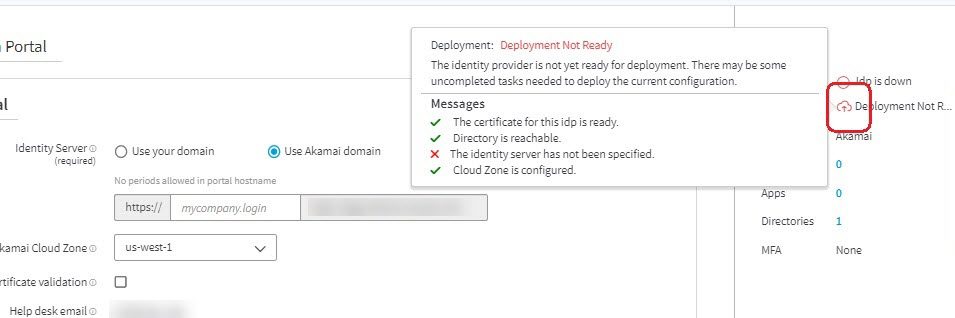
To see what steps are needed to make the IdP ready for deployment, navigate to the IdP and hover over the cloud icon in the far right of the page.
Deploy multiple identity providers
You can deploy multiple IdPs at once. This requires that you complete a deploy bulk action. You can deploy a maximum of five IdPs in each bulk action. To complete this action, an IdP needs to be ready for deployment.
To deploy multiple IdPs:
-
In the Threat Protection menu of Enterprise Center, select Identity & Users > Identity Providers.
-
In the IdP top menu, select the bulk action icon.
-
Select Deploy Identity Providers.
-
Select the IdPs that you want to deploy.
-
Click Deploy Identity Providers.
Add identity provider domains to an exception list
Depending on the type of IdP you set up, you need to add specific domains to an exception list and assign the list to the appropriate policy. This allows domains that are used by your IdP to bypass SIA.
To add IdP domains to an exception list:
-
In the Threat Protection menu of Enterprise Center, select Policies > Lists.
-
On the Custom Lists page, click the plus sign icon, and select New Custom Exception List.
-
Enter a name and description for the list.
-
In the Exception List Domains tab, enter the domains that apply to your IdP:
| Identity Provider Type | Domain or URL |
|---|---|
| Okta |
where <your-account>.okta.com is the domain that your organization uses for Okta. |
| PingOne |
|
| AD FS for Third-Party SAML | https://<adfs_server>/adfs/ls where <adfs_server> is the FQDN of your AD FS server or AD FS portal. |
| Microsoft Azure AD for Third-Party SAML |
|
- Click Save. If you want to save and deploy the list, click Save and Deploy.
Next steps
- If you haven't deployed the list, deploy it to the SIA network. For instructions, see Deploy configuration changes.
- Assign the exception list to the policy where you assigned the IdP. For instructions on assigning a list to a policy, see Add a Block list to a policy.
Updated over 2 years ago
