Configure firewall rules
Firewall as a Service (FWaaS) is a cloud-based firewall that protects your network from unauthorized access. You can apply FWaaS capabilities by configuring firewall rules in a policy.
Firewall rules define how outbound web and non-web traffic is handled in your organization’s network. This feature lets you specify the Internet destinations that you want to allow or block. By configuring the TCP and UDP traffic that’s allowed to leave your network, you prevent your network devices, applications, or services from attempting connections that are not authorized. For example, firewall rules can prevent communication with malware or command and control servers.
Firewall rules are applied to traffic that travel through an IPsec tunnel. To learn more about IPsec tunnels and how to set them up, see Set up IPsec tunnels.
When creating a rule, you can configure web and non-web traffic that is bound for the Internet. Non-web traffic includes traffic that is not DNS, HTTP, or HTTPS. It is:
- Traffic from services that use TCP, UDP, or both. For example, the Network Time Protocol.
- TCP traffic using ports that are not 80 or 443. For example, SSH.
- Applications that use a combination of UDP and TCP, such as unified communications. For example, this includes traffic from applications like Cisco WebEx, GoTo Meeting, Zoom, and more.
In a policy, you configure rules based on the following:
-
IP Address. When creating rules based on IP addresses, you can provide the:
-
Destination or Source IP address, or both.
-
Protocol. You can select from TCP, UDP, or TCP/UDP
-
Port or Port Range.
For an IP address rule, you must provide either the source IP address, the destination IP address, or the port/port range.
-
-
Application. You can select specific applications, such as Zoom, GoTo Meeting, and more. You can also provide the source IP address of the client or the device that’s making the request.
-
Service. Standard network services that use well-known ports and protocols. These services include NTP, SSH, and more. You can also provide the source and destination IP addresses.
You configure a rule with one of these actions:
- Allow. Traffic bypasses SIA or the SIA Proxy and is directed to the origin.
- Block. Traffic is blocked by SIA.
You also set the default action that applies when traffic does not match any of the firewall rules you provided. Rules are prioritized in a policy.
This graphic illustrates the flow of traffic with this feature:
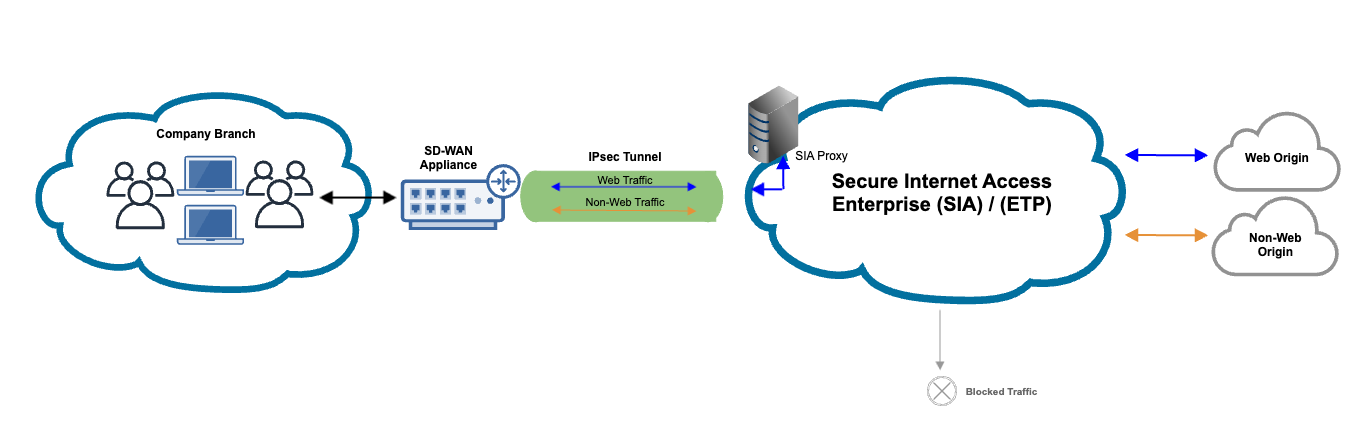
- With IPsec in place, both web and non-web traffic travel through the IPsec tunnel.
- Web traffic is directed to the proxy, while non-web traffic is directed to SIA.
- Based on the Firewall rules in a policy configuration, traffic to the IP address, services, and applications in the rules are either allowed or blocked. Allowed traffic is directed to the origin. If web traffic is blocked, an error message appears. If non-web traffic is blocked, the connection is closed.
This feature is currently in beta. To participate in the beta, contact your Akamai account representative.
When configuring firewall settings, know the following:
- By default, all web traffic is allowed by the firewall unless there is a firewall rule that specifically blocks traffic (for example, traffic based on source IP address or a destination IP address).
- Traffic that’s allowed is still directed to SIA proxy where it’s scanned and analyzed for threats.
FWaaS event report
If a connection is attempted to traffic that is blocked by a firewall rule, an event is logged in the FWaaS Event report. In addition to the filters that you configure in the report, this report automatically shows the number of events that occur within a five-minute period. For more information about the report, see Events. To learn about the data in the report, see Dimensions for FWaaS events and FWaaS event details.
Limitations
These limitations apply:
- IPv6 traffic is not supported.
- Voice over Internet Protocol (VoIP) traffic is not supported. However, you can configure a rule that uses the IP address of the VoIP application.
Create firewall rules
Before you begin:
- Make sure SIA Proxy is enabled. For more information, see Set up SIA Proxy.
- Make sure that you configured an IPsec tunnel. For more information, see Set up IPsec tunnels.
Complete this procedure to configure firewall rules for Internet-bound traffic. This procedure assumes that you are modifying an existing policy. To configure a new policy, see Create a policy.
To create firewall rules:
-
In the Threat Protection menu of Enterprise Center, select Policies > Policies.
-
Click the name of the policy where you want to configure firewall rules.
-
Click the Firewall tab.
-
Turn on the toggle for Enable Firewall Rules.
-
Select the default action. This action is applied to traffic that does not match any of the rules you specify.
-
Click the plus sign icon to add a new rule.
-
Select the rule type. You can select IP address, Application, or Service.
-
Enter a rule name.
-
Select an action for the firewall rule. You can select the Allow or Block action.
-
If you selected IP address as the rule type, complete these steps:
-
In the Protocol menu, select TCP, UDP, or TCP/UDP.
-
Enter either the source or destination IP addresses or CIDR ranges, or both. If the destination or source IP address field is empty, any IP address is accepted.
-
Enter the port or port range.
In an IP address rule, you must provide either the source IP address, destination IP address, or the port or port range.
-
Click Add to List.
-
-
If you selected Application as the rule type, complete these steps:
-
Click the link icon for Applications.
-
Select an application or applications. Use the filter to narrow the application list.
-
Click Associate.
-
Enter the source IP addresses or CIDR ranges of the client. This is not a required field. If the source IP address field is empty, any IP address is accepted as the source of traffic.
-
Click Add to List.
-
-
If you selected Service as the rule type, complete these steps:
-
Click the link icon for Services.
-
Select a service or services. Use the filter to narrow the service list.
-
Click Associate.
-
Enter the source and destination IP addresses or CIDR ranges. These fields are not required. If the source or destination IP address fields are empty, any IP address is accepted as the source or destination of traffic.
-
Click Add to List.
-
-
To add another rule, click the plus sign icon and complete steps 7-12. After you add more than one rule, you can modify the priority of the rule.
-
To modify the priority of a rule, select a specific rule and change the priority to a lower or higher number. You can also drag and drop rules by clicking the icon next to the priority number.
-
To disable any rule, turn off the toggle for that rule.
-
Click Save. If you want to save and deploy the policy, click Save and Deploy.
Next steps:
If you haven’t deployed the policy, make sure you deploy it to the SIA network. For instructions see Deploy configuration changes.
Updated almost 3 years ago
