Security Connector as a DNS forwarder
Security Connector can act as an internal DNS resolver that forwards traffic to SIA DNS for resolution. With the DNS forwarder, you identify the machine that's making the request. It forwards the request to SIA where SIA policy is applied. The DNS forwarder detects this information about the client machine:
- Internal client IP address
- Internal hostname
Connections from DNS Forwarder to SIA are protected with DoT.
If there are domains that you want to forward to their destination, DNS Forwarder allows you to split this traffic and direct it to the corporate resolver for resolution. To identify this internal traffic, you configure internal domains or IP address ranges in the Local Bypass Settings. For more information, see Configure Local Bypass Settings.
You can also configure conditional forwarding to send specific DNS traffic to an internal or external DNS resolver. In SIA, you can set up rules where you identify an internal or external resolver and the traffic that you want forwarded to that resolver. Queries to the domains in these rules are not forwarded to SIA. If rules for conditional forwarding are not configured, Security Connector forwards external domains to SIA and internal domains to your local DNS resolver. Conditional forwarding is supported on Security Connector 3.9 or later. To set up conditional forwarding, see Configure conditional forwarding.
Network flow
This graphic shows how DNS Forwarder behaves in the corporate network:
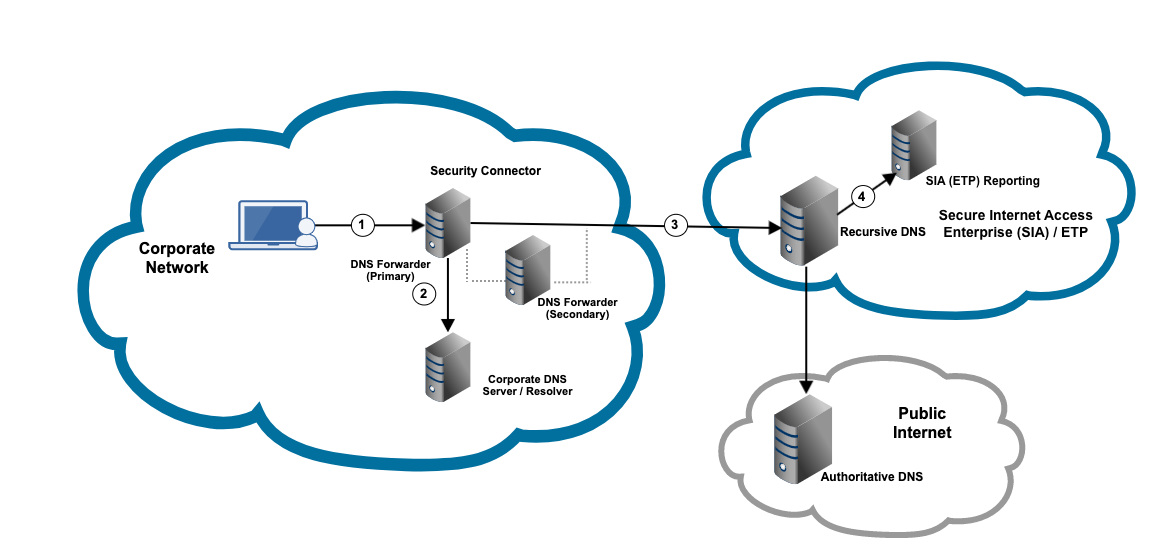
In this graphic:
-
An administrator deploys a DNS forwarder near each corporate resolver. The administrator also configures corporate machines to forward requests to DNS Forwarder.
For high availability, make sure you deploy at least two DNS forwarders, where one forwarder acts as the primary and the other is a secondary DNS forwarder. This ensures that a DNS forwarder is available in case of a failure or you upgrade Security Connector software.
-
Requests to internal domains are directed to the corporate resolver for resolution. The internal domains are identified based on the domain suffix or IP address ranges configured in the Local Bypass Settings.
-
DNS Forwarder directs requests to SIA DNS.
-
The internal client IP address and the internal hostname information are reported in SIA. This data is reported in events, as well as in the DNS Activity report.
If you’ve enabled DNS Protection in China, this data is not reported in the DNS Activity report.
Note the following:
-
If your enterprise uses ETP Client, it can coexist with DNS Forwarder.
-
For each client connecting to DNS Forwarder, DNS Forwarder can handle 2,000 queries per second (QPS). If the response is longer than 512 bytes, then replies are limited to 25,000 bytes per minute for each client.
In case of a failure or a connectivity issue, the following flow applies:
-
If DoT is unable to connect to SIA, the UDP is used to connect to SIA.
-
If UDP cannot connect to SIA, then traffic is forwarded to the corporate resolver you configured in the security connector DNS Server settings.
-
If you would like a specific authoritative DNS server to handle local DNS traffic, you can configure this server as a local DNS server for DNS Forwarder. This server is used for local DNS traffic only. It allows the DNS server you set as part of your Security Connector setup to become a fallback recursive DNS resolver that handles Internet requests when SIA is not reachable. To configure a local DNS server for DNS Forwarder, see Configure local DNS servers.
If DNS Forwarder cannot connect to SIA, it falls back to the corporate resolver whenever possible. If the forwarder cannot fall back to the resolver, the request times out. If there is a situation where DNS Forwarder is down or not reachable by clients, then the request times out.
To make sure that DNS resolution does not fail if a timeout issue occurs with a DNS forwarder, configure more than one DNS server on your client machines. If your organization uses a DHCP server, you can list the primary and secondary DNS forwarder, as well as the corporate resolver as DNS servers.
Best practices for setting up DNS Forwarder
Before you deploy Security Connector as a DNS forwarder, review these best practices:
-
When setting up Security Connector, configure the corporate resolver as the DNS name server. For more information, see Configure DNS name servers. You can also configure the corporate resolver as the static MAC address in the VM.
This also allows you to deploy DNS Forwarder in front of enterprise DNS resolvers and ensures that DNS resolvers forward requests to SIA DNS.
-
When you configure the en1 interface (formerly the data interface), make sure that you use a static IP address. The IP address of the en1 interface is the IP address of DNS Forwarder that clients connect to as a DNS server.
-
If your corporate resolver is configured with a rate limit from a single source, configure it to allow all queries from DNS Forwarder.
-
Deploy at least two DNS Forwarders to ensure one is the primary and the other is the secondary forwarder. You can deploy additional forwarders to support a large number of users.
-
Configure enterprise computers or clients to forward requests to DNS Forwarder. This is the IP address of the en1 interface. Make sure that you provide the IP addresses of the primary and secondary DNS forwarders, as well as the IP address of the corporate resolver.
-
Make sure that enterprise or corporate resolvers continue to forward requests to SIA DNS. This configuration is completed as part of SIA setup and continues to apply for the DNS forwarder.
-
If you would like a different authoritative DNS server to handle local requests instead of the DNS server configured on the Security Connector's network settings, configure a local DNS server in your DNS Forwarder configuration. This allows the corporate DNS resolver that you configured as a Security Connector's DNS Server to act as a fallback recursive resolver when SIA DNS cloud is not reachable.
-
If you need to upgrade Security Connector, make sure that you upgrade the secondary forwarder first. This allows you to confirm that the upgraded forwarder works as expected. You should also upgrade one connector at a time. This ensures that a DNS forwarder is available to handle requests while the upgrade is completed.
-
Configure the DHCP server in your enterprise to return a reachable DNS resolver in case one is not available. For example, if the primary forwarder is not reachable, the DHCP server should return the secondary forwarder as a resolver.
-
Make sure the DHCP server returns addresses in IPv4 format. DNS Forwarder does not support IPv6.
-
Depending on the port that's configured for DoT, configure your firewall to allow outbound TCP port 443 or 853 for hostname
*.akaetp.netwithdotas the ALPN. This configuration is required for DNS-over-TLS connections.
By default, DNS Forwarder uses TCP port 443. However, you can modify the DoT port in Security Connector to TCP port 853. If you modify the DoT port, make sure you allow port 853 in your firewall.
- Make sure you don't configure a loop with your resolvers where the primary DNS Forwarder directs requests to the secondary DNS forwarder and vice versa. Similarly, do not configure the corporate resolver to direct requests to the DNS forwarders. If a loop is detected, the loop is reported in the DNS Forwarder health status check report that you can run in Security Connector. In this status check, the IP address of the server where this loop occurs is shown. The overall health of DNS Forwarder is also reported on the main Security Connector screens.
Updated about 1 year ago
