Security Connector as an HTTP Forwarder
When you configure Security Connector as an HTTP Forwarder, it acts as an in-network proxy that forwards web traffic to SIA Proxy. Similar to the proxy chaining method that chains an enterprise proxy to SIA Proxy, you can use Security Connector as your enterprise proxy. HTTP Forwarder is another method of implementing the full web proxy in your network.
The SIA Proxy man-in-the-middle (MITM) CA certificate is required for SIA Proxy to intercept and scan web traffic. For more information on the proxy, see About SIA Proxy. To learn more about the certificate and how to create an SIA Proxy certificate, see SIA Proxy MITM certificate.
To support different network topologies, you can configure HTTP Forwarder as an explicit forward proxy or a transparent proxy.
-
Explicit Forward Proxy. Configuration where enterprise devices forward traffic to HTTP Forwarder and this traffic is then directed to SIA Proxy. This mode requires that you configure HTTP Forwarder as the proxy on the user device. You can use a proxy auto-configuration (PAC) file or your organization’s management tool to modify the system proxy settings.
-
Transparent Proxy. Configuration where the router forwards web traffic to the HTTP Forwarder. An administrator configures policy-based routing rules on their organization’s router. Unlike the explicit proxy, the transparent proxy does not require that you modify settings on user devices.
When adding Security Connector in SIA, you can select to configure it as an HTTP Forwarder or a sinkhole. After you select the forwarder option, the type of HTTP Forwarder that’s used within your network is determined by your port configuration:
-
For an explicit proxy, you set the port in the Security Connector console. By default, port 8000 is configured in the Security Connector console. However, you can modify this setting based on your organization’s network requirements or policies. When you modify the proxy settings on a device or browser with a PAC file or an organization management tool, this port is configured on the user’s device and used to connect to HTTP Forwarder.
-
For a transparent proxy, you can use any of the default origin ports that are allowed for the full web proxy or you can configure a new port. The default ports include 80 to 84, 443, 4443, 8080, 8443, and 8888. If you want to specify new ports or port ranges, for example, if you have application traffic going through a different port, you can configure them in the origin ports field of a policy. This allows the HTTP Forwarder to forward traffic to the proxy.
Explicit forward proxy
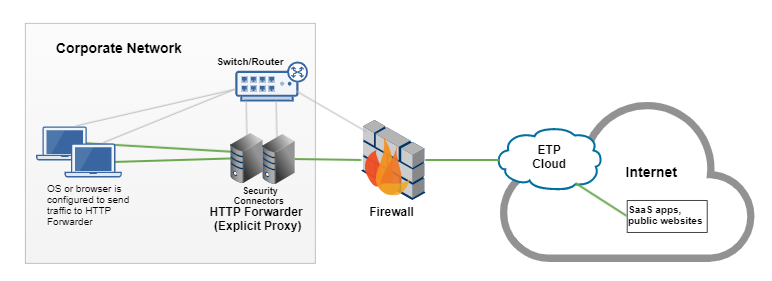
For an explicit proxy, you configure HTTP Forwarder as the system or browser proxy. You can change proxy settings on devices by distributing a PAC file URL or by manually modifying system or browser settings. After the client connects to the HTTP Forwarder, the forwarder directs web traffic to SIA Proxy for analysis. For more information on distributing the PAC file configuration, see Distribute the PAC File URL.
This graphic illustrates how HTTP Forwarder directs traffic to SIA when the device operating system or browser is configured to send traffic to HTTP Forwarder.
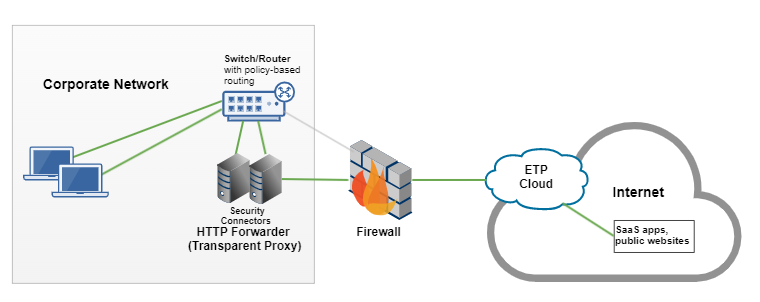
Transparent proxy
With a transparent proxy, web traffic is directed from HTTP Forwarder through policy-based routing rules that you configure on the router. You configure the router to forward traffic to HTTP Forwarder. Traffic is directed to the SIA Proxy based on the origin ports that are defined in an SIA policy.
Best practices for setting up HTTP Forwarder
Before you deploy Security Connector as an HTTP Forwarder, review these best practices.
- When you configure the en1 interface (formerly the data interface), consider a static IP address. If you select a dynamic IP address, you should use a sticky MAC address assignment. Depending on the type of HTTP Forwarder you set up, this IP address may be used on user devices for an explicit proxy or on network equipment for a transparent proxy. As a result, this IP address should not change.
- Deploy multiple HTTP Forwarders to ensure high availability and load balancing. For more information on load balancing, see HTTP Forwarder load balancing.
- Make sure that enterprise or corporate resolvers continue to forward requests to SIA DNS. This configuration is completed as part of SIA setup and continues to apply for the HTTP forwarder.
- Make sure you enable encryption on the hypervisor or software that you use to deploy Security Connector.
- If you’ve configured Security Connector as a sinkhole, do not configure it also as an HTTP proxy on user devices or browsers.
- Make sure your enterprise firewall does not use rules or have rate limits that limit the traffic from a single IP address.
Limitations of HTTP Forwarder
Consider these limitations:
- If you’re configuring an explicit proxy, you configure the port in the Security Connector. If you are configuring a transparent proxy, you configure the ports in the origin ports field of an SIA policy.
- HTTP Forwarder does not support IPv6 traffic.
- HTTP Forwarder captures 100 logs per second. Logs that exceed this amount within a second time frame are not captured. You can view log data reflected in the Security Connector activity report.
- HTTP Forwarder uses the enterprise resolver to translate an internal IP address to a device name. If the enterprise resolver takes too long to respond, activity reports may not show the device name.
HTTP Forwarder load balancing
To distribute the load of traffic and ensure high availability of HTTP Forwarder, make sure you:
-
Deploy at least two HTTP Forwarders.
-
If you are setting up an explicit proxy, set up load balancing through the PAC file.
-
To provide failover, you can specify all forwarders in the PAC file. For example, if the first forwarder is unavailable, the PAC file indicates that traffic should connect to the second forwarder.
return "PROXY IP_HTTP_FORWARDER_01:PORT01; IP_HTTP_FORWARDER_02:PORT DIRECT"where:
-
PROXY IP_HTTP_FORWARDER_01 is the IP address and PORT01 is the port of one HTTP Forwarder
-
PROXY IP_HTTP_FORWARDER_02 is the IP address and PORT02 is the port of another HTTP Forwarder.
You can enter an IP address and port for each forwarder in your network.
-
-
To distribute traffic, you can apply a DNS round-robin configuration where you assign HTTP Forwarder to a hostname with multiple A records. In this case, one hostname is used for all the forwarders, and DNS randomly selects the HTTP Forwarder IP address.
-
-
If you are setting up a transparent proxy, you can implement load balancing by configuring active-passive redundancy on your router where one HTTP Forwarder is active and the other HTTP Forwarder is on standby in case of failure. For more information, see the official documentation of your router.
-
In the Security Connector console, you configure how you want HTTP Forwarder to behave if the SIA Proxy is not reachable or not in a healthy state. This behavior is defined with the direct-to-origin failover mode setting. When this setting is enabled, the traffic from HTTP Forwarder is directed to the origin. When disabled, users are shown an error message. By default, this setting is enabled.
Traffic statistics
After you set up HTTP Forwarder, you can view traffic statistics both on the Security Connector page in SIA and in the Security Connector console.
In SIA, this information is shown:
- Proxy requests. Requests that are directed to SIA Proxy
- Bypass requests. Requests that bypass SIA Proxy.
- Internal requests. Requests the forwarder determined are for internal resources and will not be forwarded to the proxy.
- Failed requests. Requests that are dropped. This can occur as a result of a resource constraint or any other issue.
The status details also include information about the virtual machine, including percentages of the CPU load and how much of the disk is used.
You can also view similar data in the Security Connector console. The Security Connector shows traffic statistics for HTTP Forwarder. This includes:
- Number of requests received by HTTP Forwarder
- Number of successful responses
- Number of failed responses
- Number of requests that were handled by an explicit proxy configuration
- Number of requests that were handled by a transparent proxy configuration
- Number of errors
- Number of rate limit drops
- Number of interface errors
These statistics are collected when the connector is started, and they reset when the Security Connector device restarts.
To view the traffic statistics for HTTP Forwarder, see View traffic statistics.
Updated about 1 year ago
