Mobile client
The mobile client extends SIA protection to mobile devices. You deploy the mobile client in your enterprise to scan mobile traffic and enforce SIA policy to mobile applications.
If you enable the proxy, you can define how mobile traffic is handled. These settings are configured in a policy as part of the AUP and AVC configuration under Access Control. Based on the mobile device operating system, SIA allows you to select the proxy type or configure a walled garden for your mobile traffic. For Android devices, you can further send only browser traffic to SIA Proxy for scanning. For more information on these mobile settings, see Mode for mobile devices.
These terms apply:
-
Administrators configure the same policy settings and ETP Client configuration settings for the mobile client as they do for the desktop version. For example, you can configure the setting that allows end users to disable the client.
-
The mobile client is supported on Android, Apple iOS, iPadOS, and Google Chrome OS. For more information about supported operating systems and devices, see Supported mobile operating systems.
-
The mobile client is available in the app stores specific to the device and operating system. You can use your organization's MDM solution to deploy the client from app stores to supported mobile devices across your network.
-
You need to use an entitlement code to activate mobile clients that are distributed with MDM solutions. For instructions, see Distribute the mobile client.
-
End users can activate the mobile client on their personal device with an activation code. For more information, see Bring your own device (BYOD) support.
-
If you plan to allow MITM TLS Inspection by SIA Proxy, you can use your organization's MDM solution to distribute the SIA Proxy TLS MITM certificate to your mobile devices.
Note the following:- Some Android devices only support certificates that are in PEM format. If a specific Android device does not support the PEM format, try downloading the certificate in DER format and then rename it to use the .cer file extension.
- Some iOS devices only support certificates that are in DER format.
After the mobile client is installed and set up on a user's device, it acts as a VPN client. ETP Client protects user's devices whether it is on a wireless network or the cellular network. By default, the mobile client disables itself when another VPN client is enabled. To avoid this, you need to configure the MDM solution to restrict use of VPN clients and prioritize the ETP Client.
The mobile client now supports mobile network operators and internet service providers that use only IPv6 in their network.
Supported mobile operating systems
Mobile ETP Client supports these operating systems:
| Operating System | Device | Version |
|---|---|---|
| iOS iPadOS | Apple iPhone Apple iPad | Version 13 or later |
| Android | N/A | Version 6.0 or later |
| Chrome OS | Chromebook | Version 76 or later |
Mobile client statuses
Like the desktop client, the mobile client reports when a device is protected or unprotected. This status is visible in the mobile client. The client can report these statuses:
-
Protected indicates mobile requests are protected with SIA. The following protected statuses are possible:
-
Protected via Secure DNS-over-TLS. Indicates that mobile requests are protected with DoT. For more about DoT, see DNS over TLS.
-
Protected via DNS over UDP. Indicates that mobile DNS requests are protected with the UDP. DNS over UDP (DoU) is used in situations where DoT can't be used and the client is forced to fall back to DoU. This can occur if DoT is blocked by a firewall or by enterprise middleboxes. It can also occur when DoT is disabled; or the administrator configures the client to Always Attempt a DoT connection, and this connection cannot be established.
-
Protected via Local Network. Indicates mobile requests are protected only when the device is on the corporate network that's configured to forward DNS requests to SIA. In this case, the local DNS server handles requests. This status also appears if ETP Client cannot send requests to SIA because outbound UDP port 53 is blocked in the enterprise firewall.
-
-
Unprotected indicates that ETP Client is disabled or disconnected, or that the connection is interrupted. This status may also indicate that the client cannot reach the Akamai infrastructure, including SIA configuration, SIA DNS, or SIA Proxy. Depending on the situation, the following unprotected statuses are possible:
-
Unprotected! Initializing, please wait. Indicates the mobile client is still loading and establishing a connection.
-
Unprotected! No network. Indicates the mobile client is unable to connect to a network.
-
Unprotected! Disabled by User. If you allow end users to disable the client, this status indicates that the client was disabled by the user.
-
Unprotected! Suspended by Admin. Indicates the mobile client was disabled by an administrator.
-
Unprotected! Service is Unavailable. Indicates that ETP Client cannot reach Akamai infrastructure, including SIA configuration, SIA DNS, or SIA Proxy.
-
Unprotected! Another VPN is active. Indicates that device is using another VPN. The user needs to disconnect the VPN to use ETP Client.
-
Unprotected! Disabled when hotspot is on. This status applies to Android devices only. The client does not support hotspot on Android devices.
-
ETP Client stats
The mobile client allows end users to view the number of requests that are scanned and the number of requests that are blocked by the client.
Users are also given graphical data to show the top domains or applications based on operating system that are scanned and blocked in the past seven days and four weeks.
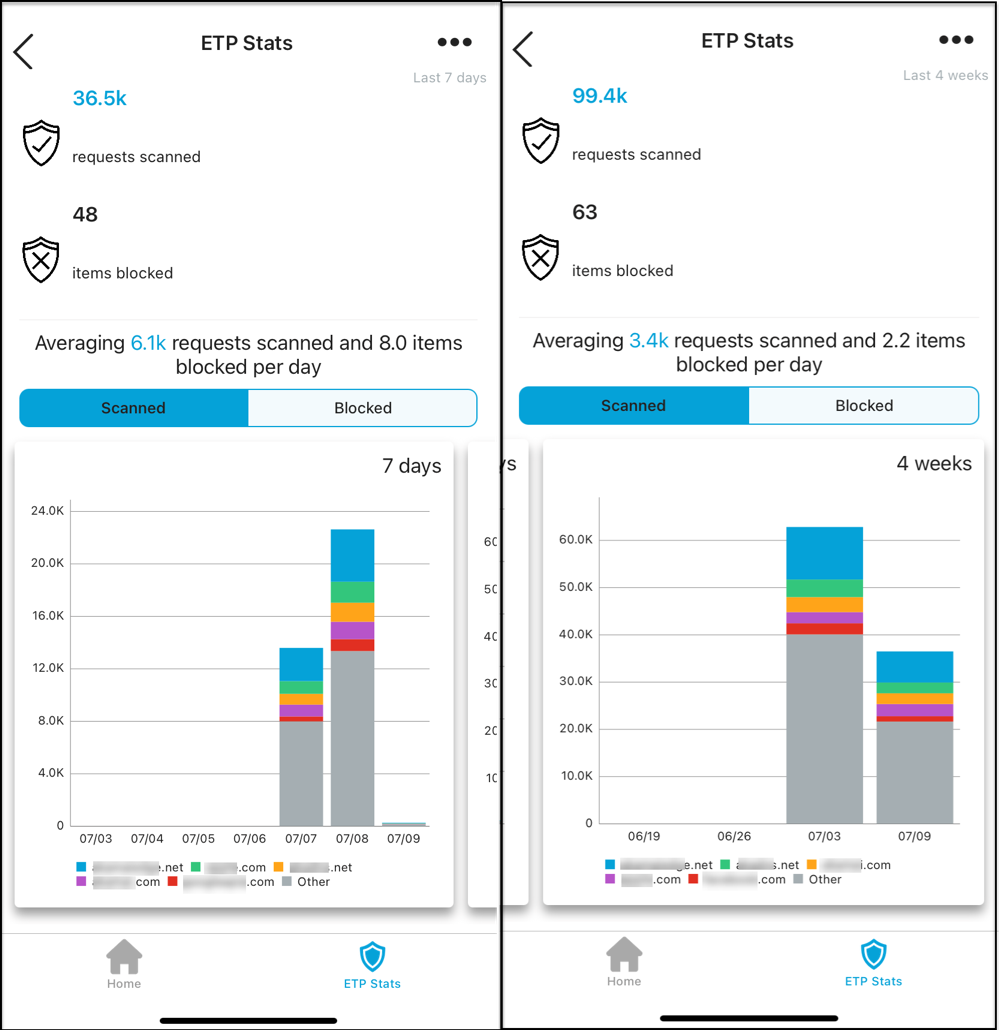
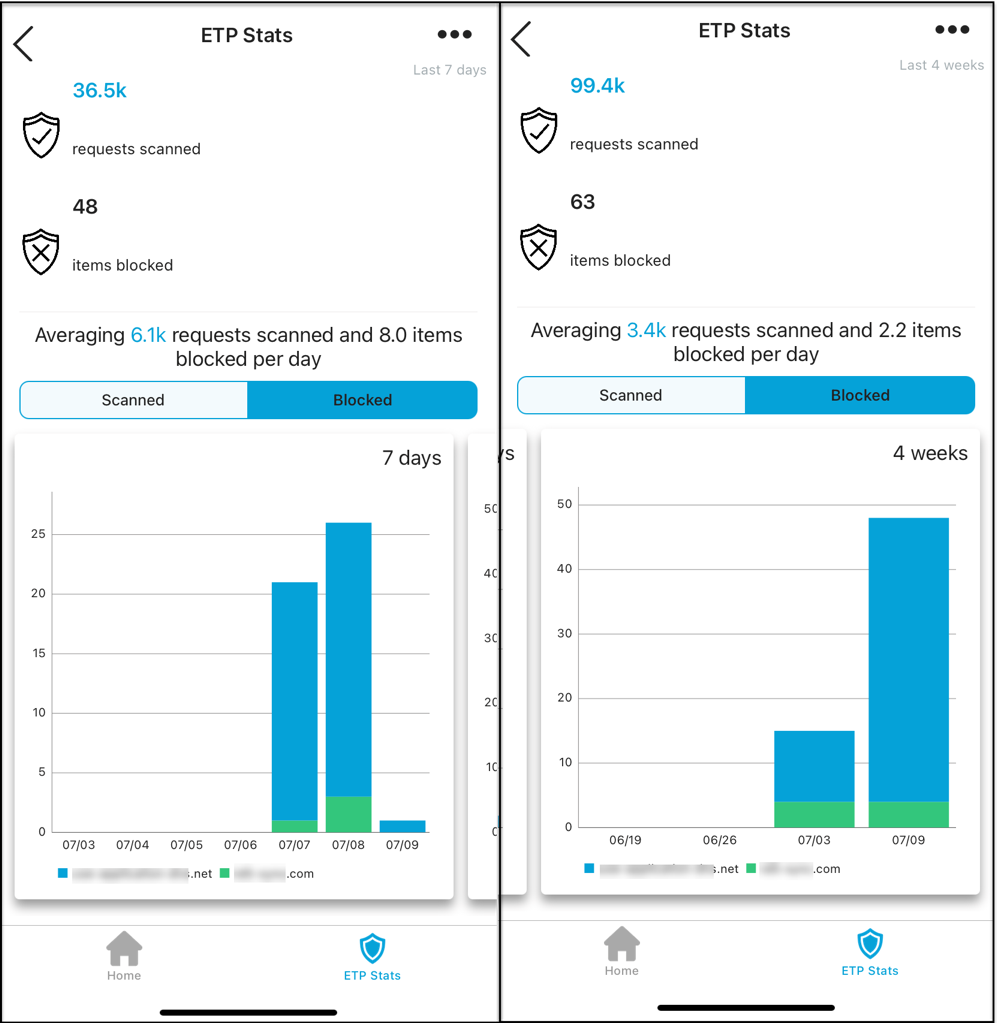
As shown, the client also indicates the average number of requests that are scanned and the average number of potential threats that are blocked per day.
The following applies:
- The stats report the number of blocked DNS requests. This number represents requests where a user was shown a block notification.
- When viewing a website, ETP Client may block URLs that the user has not attempted to access. For example, a blocked URL may be a link that's on an allowed website. In this situation, the user is shown a block notification for the URL and the block is counted in the stats.
- A blocked domain is counted only once every 30 seconds for the same network. If more events occur for the same domain within the 30 second time frame, the additional blocks are not counted in the stats. As a result, it is possible that the number of blocked requests in the stats is different from the number of events in SIA reports.
- A user can receive only one notification in a 30 second time frame. If multiple domains generate events within the 30 seconds, only one notification appears to avoid overwhelming the user with alerts.
Limitations of the mobile client
These limitations currently apply to mobile client:
-
A VPN client application cannot run simultaneously with the mobile client. If a VPN client is activated on the device, SIA client app automatically disables itself. To protect users with the mobile ETP Client, you can use your organization's MDM solution to restrict use of another VPN client and prioritize the mobile client.
-
Any user and group that is set up for authentication and configured as exceptions to a blocked AVC risk level, category, category operation, application, and application operation, are not granted access. These authentication settings do not apply to traffic that goes through the mobile client. This also applies to other areas of the policy, including user and group exceptions configured for a custom list or DLP.
-
When an administrator makes policy changes or other configuration changes to SIA, these updates are communicated to the mobile client and take effect within a five minute interval.
-
Certificate pinning is used by many mobile applications to validate that TLS certificates presented by web servers are known. These pinned certificates may be incompatible with the TLS man-in-middle certificate that is used for SIA Proxy. As a result, the SIA policy is applied differently if traffic comes from a mobile browser or a mobile app, as follows:
-
On an Android operating system version 10 and later, mobile traffic from mobile browsers is forwarded to SIA Proxy and TLS inspection is performed with the SIA Proxy certificate.
-
A selective proxy is applied to traffic from Apple iOS, iPadOS, Android apps, as well as any Android OS that is earlier than version 10. In this case, only known domains, AUP and AVC configured with block error page action, and risky domains and customer lists configured with the Allow or block action are sent to SIA Proxy. All other domains are handled on DNS level by SIA DNS.
-
-
If your organization sets up proxy chaining for the full web proxy and you use the mobile client, make sure you configure the local proxy to copy the Akamai-User-Agent header Mobile Clients send and forward it to the proxy.
-
When selecting a mode for mobile devices, consider the following:
-
If the mobile mode is set to Walled Garden for a device, make sure you also select Walled Garden as the default operating mode in the policy.
-
If you select the full proxy for any mobile device or you select Proxy (Browser Only) mode for Android, make sure the default operating mode is not set to Walled Garden.
For more information about the default operating mode, see Default operating mode and Mode for mobile devices.
-
-
After a device is restarted or shut down, ETP Client may not start running by default. Make sure the ETP Client app is set to start automatically. For example, on some Android devices you can do the following to enable the Autostart option:
- On the Android device, go to Settings > More Settings > Permission management > Autostart.
- Check to see that this setting is enabled for ETP Client.
-
On a mobile device, SIA assigns a pseudo-MAC address. If you uninstall and reinstall ETP Client on an Android device, SIA will track the device with a new pseudo-MAC address. This means that SIA reports contain multiple entries for the same device. Data related to the original installation of the client is shown with the original pseudo-MAC address, while data related to the new client installation is tracked with a new pseudo-MAC address. Entries for the original client are visible until they’re retired from our database.
Distribute mobile ETP Client
This section provides instructions for distributing the mobile client with a MDM solution.
Although the mobile client is available for download from the Google Play Store and the Apple App Store, no direct download is required. The MDM solutions in this section allow you to import the mobile client directly from the app stores.
Before you begin
Make sure you complete ETP Client preparation steps. For more information, see Prepare for ETP Client setup.
| Solution | Operating System | Instructions |
|---|---|---|
| Google Workspace Endpoint Management | Android, iOS, ChromeOS | Distribute the mobile client with Google Workspace Endpoint Management |
| Microsoft Intune | Android, iOS, iPadOS | Distribute the mobile client with Microsoft Intune |
| VMware Workspace ONE Unified Endpoint Management (UEM) Powered by AirWatch | Android, iOS | Distribute the mobile client with Workspace ONE UEM |
| MobileIron | Android, iOS | Distribute the mobile client with MobileIron |
Updated about 2 years ago
