About Request Control
The Request Control Cloudlet allows you to provide conditional access to your website or application by defining and managing allow lists and deny lists based on a number of match criteria, including the IP address and geography associated with incoming requests. In addition, you can have a branded 403 (Forbidden) page display when a user is denied access.
The default for Request Control is to give all requests access. You use your rules to restrict access.
Workflow
Here are diagrams that show how Request Control works.
For the allow list example, when a visitor requests a page and the IP address or geography is allowed based on the rules, that visitor can view the page. If the visitor's IP address or geography is not included in the rules, that visitor will receive a 403 (Forbidden) error.
Conversely, for a deny list, if a visitor requests a page from an IP address or geography that's denied based on the rules, the visitor will receive a 403 error.
The default for Request Control is to allow access to all requests. You need to set up rules in order to restrict access.
Allow list example
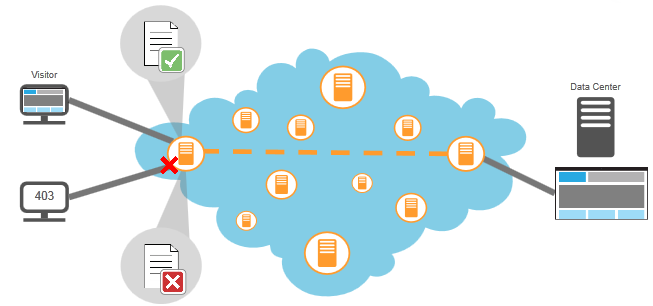
Deny list example

Use cases
The Request Control Cloudlet supports these use cases:
| Use Case | Description |
|---|---|
| Blocking Requests | |
| Illegitimate Requests | If there is a set of IP addresses that are from illegitimate sources, you can set up a simple IP deny list to prevent requests from these IP addresses. |
| Support for Business Objectives | You may want to block certain geographies for the following reasons: |
| Malicious Traffic | You may want to block geographic locations known to have a higher percentage of malicious traffic. To temporarily block a geography with suspected malicious traffic, set up a rule with a custom date range. If a geography is consistently the source of malicious traffic, select Always On when configuring the rule. |
| Allowing Requests | |
| Test/Staging Environments | If you have a test or staging environment, you want to set up rules that allow access only to the customers or vendors that should have access to these non-production environments. You can also set up an allow list for IP addresses that are part of your local network before a site/property is made public. This will ensure privacy before the site is officially launched. |
| Monitoring Tools | If you use monitoring tools (like Keynote), you will want to allow access to the IP addresses provided by the monitoring service. |
| Sites targeted to a specific geographic region | If you have a site that's specific to a certain geographic region, you may want to set up an allow list to avoid incurring the cost of delivering traffic from regions outside the target audience. |
To learn more about Cloudlets basics, see:
How Cloudlets work
Cloudlets terminology
Property and Cloudlet policy considerations
Updated about 1 month ago
