Create an upload account
Add an upload account
You use an upload account to access a specific storage group. Do this by associating it with an upload directory that's set up in the storage group, then assigning it an access method. Use the NetStorage wizard or Configuration API to create a new upload account.
- Open the application. Go to ☰ ⇒ ORIGIN SERVICES ⇒ NetStorage
- Access the Upload Accounts entity and click the + icon to access the Create a new upload account wizard.
Here's a short summary. You can find more details below.
- Basic information. Here, you define a name and contact information for the account.
- Access methods. These define how you want the upload account to access its storage group. Each tab represents a unique Access Method:
- Upload directory association. Here, you select a "root" directory for the upload account and assign optional settings:
- Directory limit. Define an alternative root-level directory other than the default.
- Default directory. Define the default working directory upon connection.
- Subdirectory restrictions. Limit the upload account’s ability to manage content to one or more specific directories.
- Advanced settings. This includes various optional settings for the account, such as select existing ACL rule sets.
- Finally, you need to review the Summary. All of the settings you've applied for the account are revealed, and you use this window to save them.
Remember that propagation takes time to complete
Changes require propagation to the NetStorage network, and this can take from 60 – 120 minutes to complete. Any changes you make are not accessible until this propagation completes.
Take caution when editing an existing upload account.
If you're implementing any automated processes that use an active account (for example, calls issued via the NetStorage Usage API), or if other users are using this account, their access may be interrupted, based on the changes you make. As a best practice, it's recommended that you create a new upload account and apply changed settings there to avoid a potential interruption in access.
Basic information
- Upload account ID. Create an "Upload Account ID" for the upload account. It serves as an identifier and you'll use it for logging in to non-secure access methods.
- Contact email address. Specify an email address to receive relevant status and propagation notifications regarding the account.
- Additional contact information. Specify additional information to contact the owner of this upload account. You can use an existing Control Center user or use a technical contact. You can also click the Contact details button to add a new contact.
Access methods
Set the Access mode slider switch to the desired access level for the account:
- Read-Write. The upload account will have full access to content in its associated storage group. For example, the account can be used to view, upload, download, overwrite and delete content.
- Read-Only. The upload account will only be able to view content in its associated storage group.
Access methods define how you want the upload account to access its storage group. Each tab represents a unique Access method:
Upload directory association
Here, you give an upload account access to storage groups.
This is accomplished by selecting an upload directory—a root directory in the storage group that is named using a unique Content Provider (CP) code numeric value. During generation of a storage group, at least one CP code is provisioned for its use, and set as an upload directory.
You must know the storage group's Name, as well as the applicable Upload Directory (CP code root) in that storage group.
Multiple upload directories and storage groups
You can give an upload account access to multiple upload directories from different storage groups.
Steps to select an upload directory for use
- Input either the storage group's name or its upload directory (CP code) in the Filter field to filter results in the table.
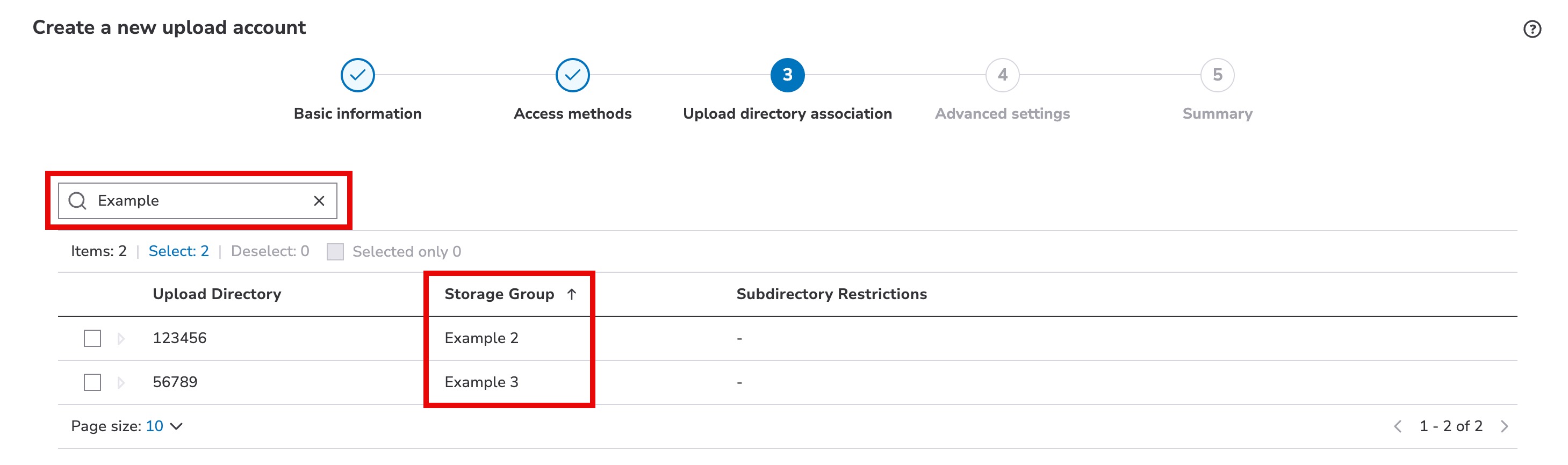
- Select each upload directory you want this upload account to have access to.
- You can optionally define a Default directory, establish Subdirectory restrictions, and if the account has a single upload directory—a Directory limit.
If your upload account is assigned to multiple upload directories, directory limits are removed.
Caveats apply if you combine Directory Limit, Default Directory or Subdirectory Restrictions.
Directory limit
A directory limit is used to establish a “change root” (chroot) for the upload account. This is used if you wish to establish a directory other than the storage group’s actual "CP code root" as the root for the upload account. Access for the upload account will be limited to this directory (and any existing subdirectories). No other directories in the tree above this one will be accessible to the upload account, and protocol-based operations used to return to the root will return to this directory.
- Select the appropriate CP code root from the Directory Limit drop-down.
- Use the associated field to input the complete path to the desired subdirectory.
- Click Save.
Directory limits don't apply to File Manager or the NetStorage HTTP API access methods. The NetStorage HTTP API should use Subdirectory Restrictions instead.
Aspera Upload Acceleration is not supported for use in upload accounts that incorporate a directory limit, default directory or subdirectory restriction. If you intend to use Aspera Upload Acceleration, you can't configure any of the settings discussed here.
Default directory
A default directory is the default access point for the upload account. Whenever the upload account connects with the storage group, the directory named here will be the default point of access. For example, after logging in with a supported protocol, this will be revealed as the current working directory.
- Select the appropriate directory from the Default Directory drop-down. If you’ve specified a Directory Limit or Subdirectory Restriction, that path will be automatically displayed here, because a Default Directory must exist within these paths.
- Use the associated field to input the complete path to the desired subdirectory.
- Click Save.
Subdirectory restrictions
Subdirectory Restrictions allow you to limit the upload account’s ability to manage content to one or more specific directories. With each restriction set, the account will only be able to upload, download, move, or delete content within the specified subdirectory. All other subdirectories off of the root (the CP code Root or the Directory Limit) will block the account from performing these and other content management operations.
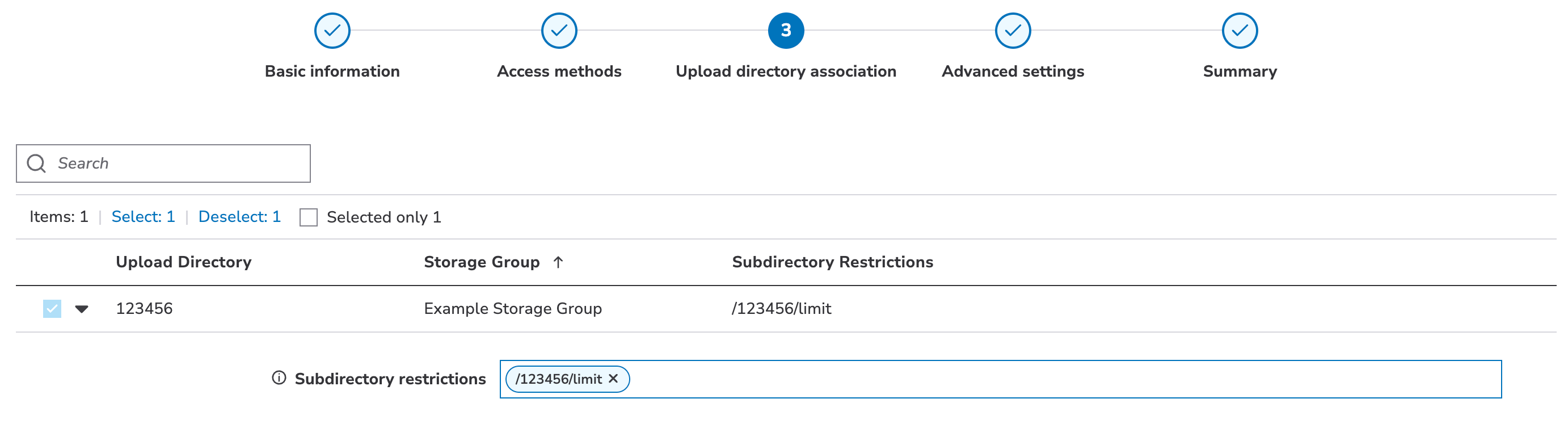
- In the upload directory table, expand the options by clicking .
- In the Subdirectory Restrictions field that is revealed, click Add.
- Input the complete path to the desired subdirectory. If you have defined a Directory Limit, each Subdirectory Limit must exist within that path.
- Repeat Steps 2-3 to add more subdirectories.
- Click Save to finalize your changes.
Caveats apply if you combine directory limits
If you intend to combine any or all of these functions for use in an upload account, specific caveats apply.
- If you set a directory limit, a default directory setting must exist within that directory. If you set your directory limit as
/<CP code root>/files, a default directory must be this directory limit path, or a subdirectory of it. For example,/<CP code root>/filesor/<CP code root>/files/new/could be the default directory. - If you set a directory limit and don't set a default directory. The directory limit path will automatically serve as the default directory.
- A subdirectory restriction must exist within a directory limit. If you set a directory limit for the upload account, a subdirectory restriction can only be applied to a child of the directory limit.
- The directory limit serves as the root for the account, so you can't use a directory that exists above it in the tree. Anything above a directory limit is inaccessible to the upload account.
- A default directory must exist within a subdirectory restriction. If you set up one or more subdirectory restrictions, the default directory must be set within one of them. It can exist as a child directory of a restriction, or be a specific subdirectory restriction.
- A default directory exists within a subdirectory restriction which in turn exists in the directory limit.
- A subdirectory restriction does not limit access, it limits management of content. Once you have set a subdirectory restriction, the upload account can still navigate to, and view content in any subdirectory off of its established root, either what you have set as the directory limit, or the actual CP code root, if one was not set.
- A subdirectory restriction limits the upload account’s ability to manage content (upload, download, move, or delete) to the subdirectory specified.
- Recommended order of operation. If combining these options, it is recommended that you implement them in this order:
- Set up a directory limit. This defines the root for the upload account.
- Set up subdirectory restrictions if needed. This is done to limit management of content to specific directories within the defined directory limit.
- Set up a default directory if needed. A default directory must exist within a specified directory limit, and if you've set subdirectory restrictions, a default directory must also be within one of these restrictions.
Here are some examples of the various combinations of these three options in a storage group. In them, “123” is the CP code used for the root.
| Configured Restriction | Configured Default Directory | Configured Directory Limit | Resulting Default Directory | Resulting Writeable Tree | Resulting Readable Tree |
|---|---|---|---|---|---|
| Subdirectory Restrictions 1 | Default Directory 1 | Directory Limit | Default Login Directory | Writeable Directory Trees 2 | Readable Directory Trees 2 |
| None | None | None | /123 | /123 | /123 |
| None | None | /123/a | /123/a | /123/a | /123/a/ |
| None | /123/a/y | None | /123/a/y | /123 | /123 |
| None | /123/a/y | /123/a | /123/a/y | /123/a | /123/a |
| /123/a/x,/123/a/y | None | None | /123 | /123/a/x,/123/a/y | /123 |
| /123/a/x,/123/a/y | None | /123/a | /123/a | /123/a/x,/123/a/y | /123/a |
| /123/a/x,/123/a/y | /123/a/y | None | /123/a/y | /123/a/x,/123/a/y | /123 |
| /123/a/x,/123/a/y | /123/a/y | /123/a | /123/a/y | /123/a/x,/123/a/y | /123/a |
1 Paths in subdirectory restrictions and a default directory are relative to the directory limit you have set, if you have set one. If you have not set one, they are relative to the CP code root. This also applies to paths used by the “upload” action via the NetStorage Usage API.
2 All subdirectories off of the displayed path are also accessible.
Advanced settings
Functionality here is used to configure optional ("advanced') settings for the upload account.
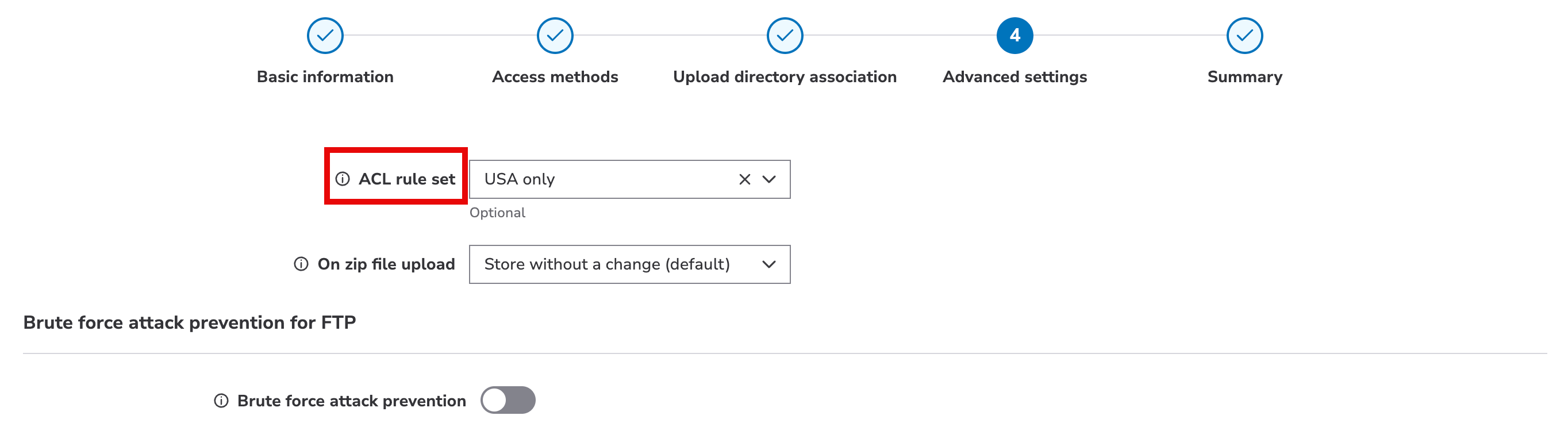
ACL rule set
Access Control List (ACL) rule sets are collections of IP addresses or geographic regions ("Geos") that you create to either allow or block their access to a storage group. These help to prevent "man-in-the-middle password sniffing."
You need to create an ACL rule set before they are available for selection.
Click the ACL rule set field and select the desired ACL rule set from the drop-down. If you aren't sure that an existing set meets your requirements, or you need to create one, leave this field blank and finish adding the upload account. You can then create an ACL rule set with your desired specifications, and edit the upload account to apply it.
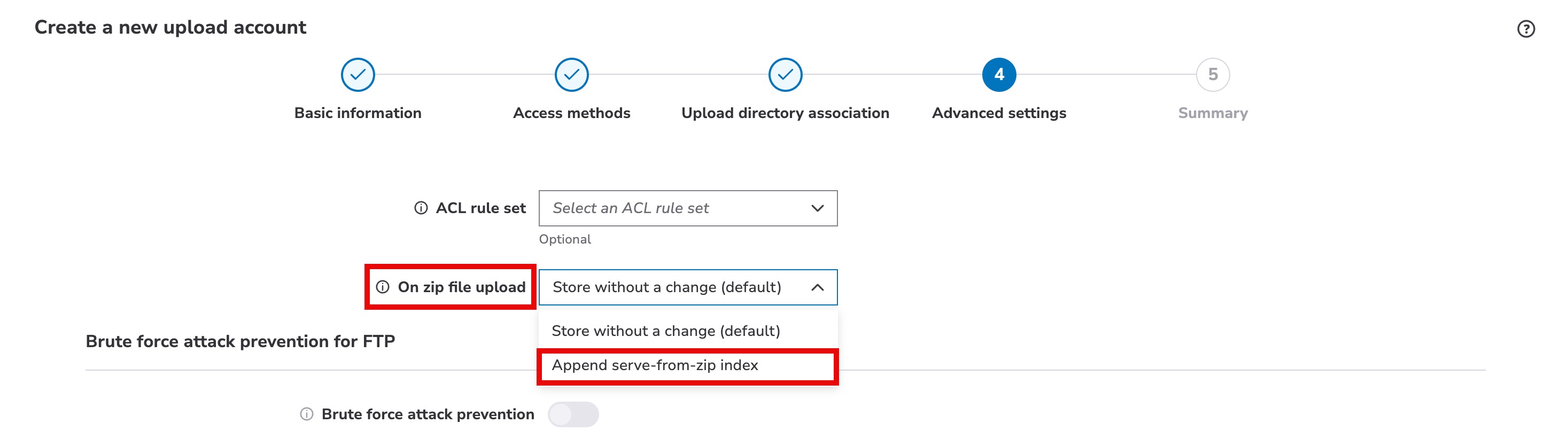
On zip file upload
Enable this on your upload account to automatically index zip files for use with the Serve from Zip feature. Select the Append serve-from-zip index option to automatically apply an index to zip files during upload to NetStorage.
You must enable serve content from zip files for your upload directories (CP codes) to serve content from within the indexed zip files.
Enabling auto-indexing will change the zip files that you upload. Downloaded zip files will look corrupt and unusable for their original purpose.
Protocols that support auto-indexing:
- Aspera
- Rsync
- SCP
- SFTP
- FTP
Brute force attack prevention for FTP
This protection allows you to defend the target storage group from excessive incorrect FTP login attempts. An offending client IP address using this upload account is blocked from access for a specified amount of time, after a specified number of bad login attempts.
If you haven't enabled FTP as an access method for the upload account, this functionality is disabled.
Use the switch to enable it and reveal additional settings:
- Number of failed login attempts. Select the number of failed login attempts required to trigger the lockdown for an offending client IP address.
- Minimum lockdown period. Select the amount of time an offending client IP address should be blocked from further access attempts.
Updated 11 months ago
