Security report
Check out the documentation for other reports available in the Infection Monkey.
The Infection Monkey's Security Report provides you with actionable recommendations and insight into an attacker's view of your network.
The report is split into the following categories:
- Overview
- Segmentation Issues
- Machine-related Recommendations
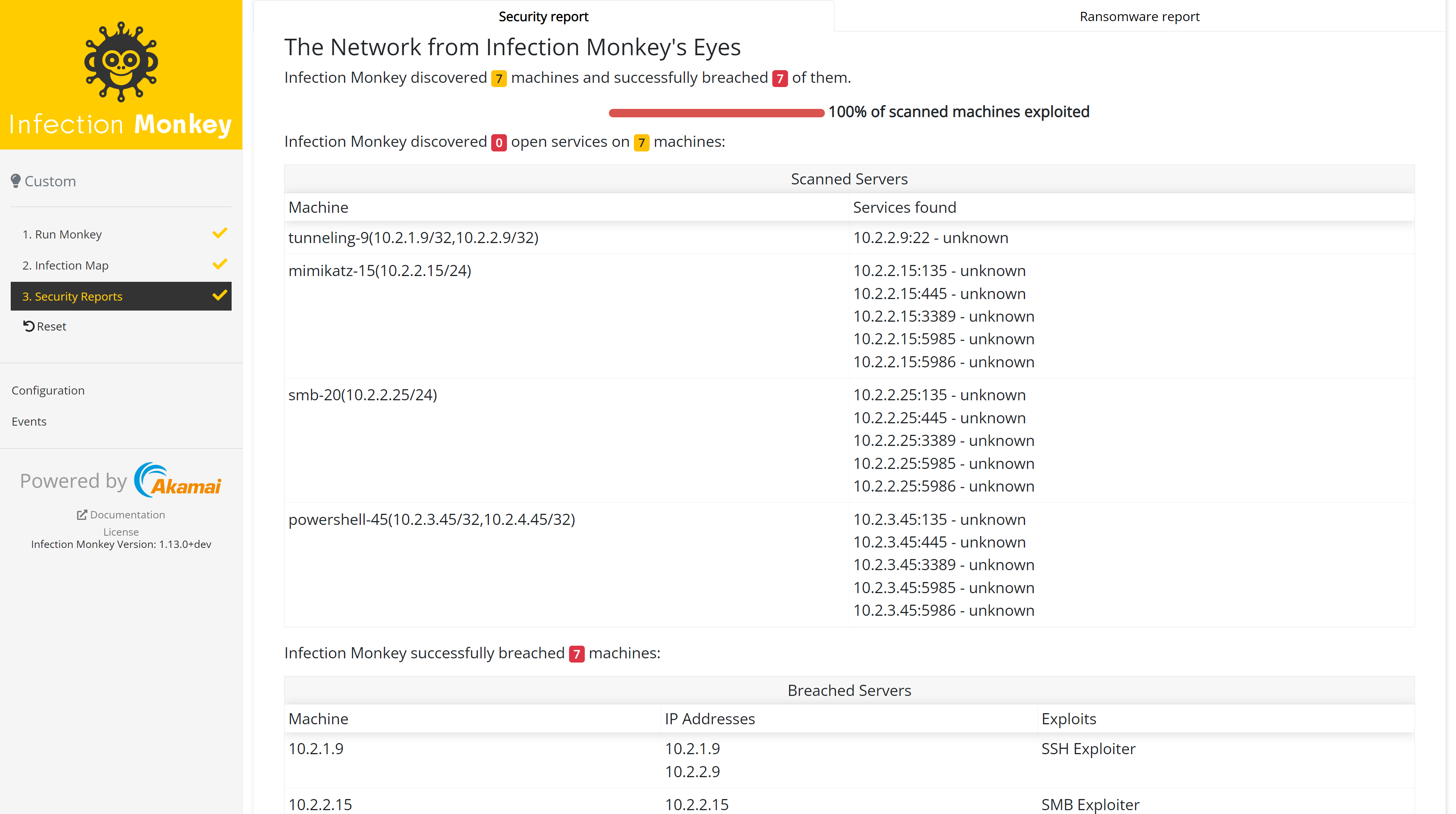
- The Network from Infection Monkey's Eyes
Overview
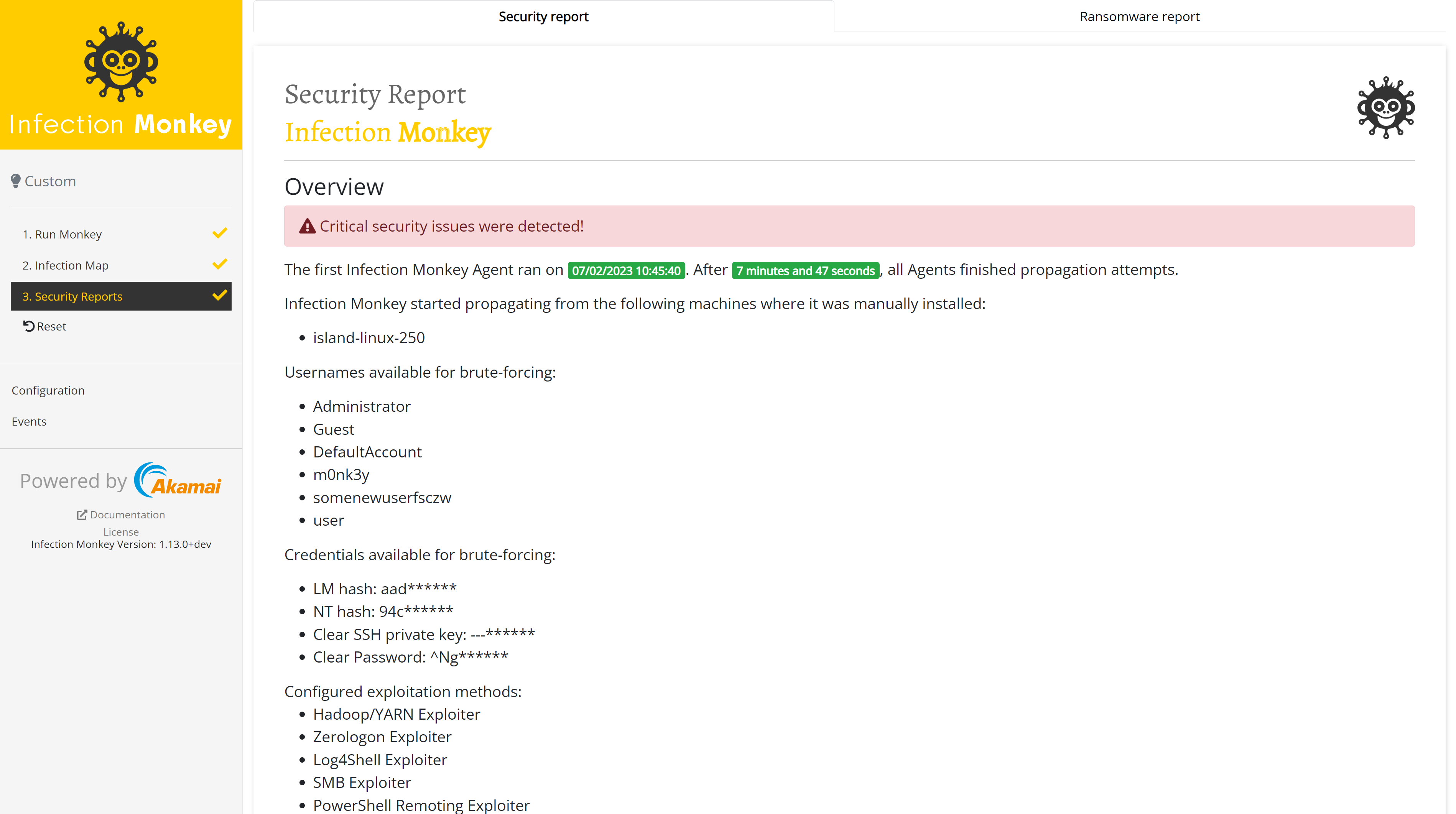
The Overview section of the report provides high-level information about the Infection Monkey's execution, including the machines from which the infection originated, how long the breach דimulation took, and the configuration of the Agents.
High-level information
This section shows general information about the Infection Monkey's execution, including which machine the infection originated from and how long the breach simulation took.
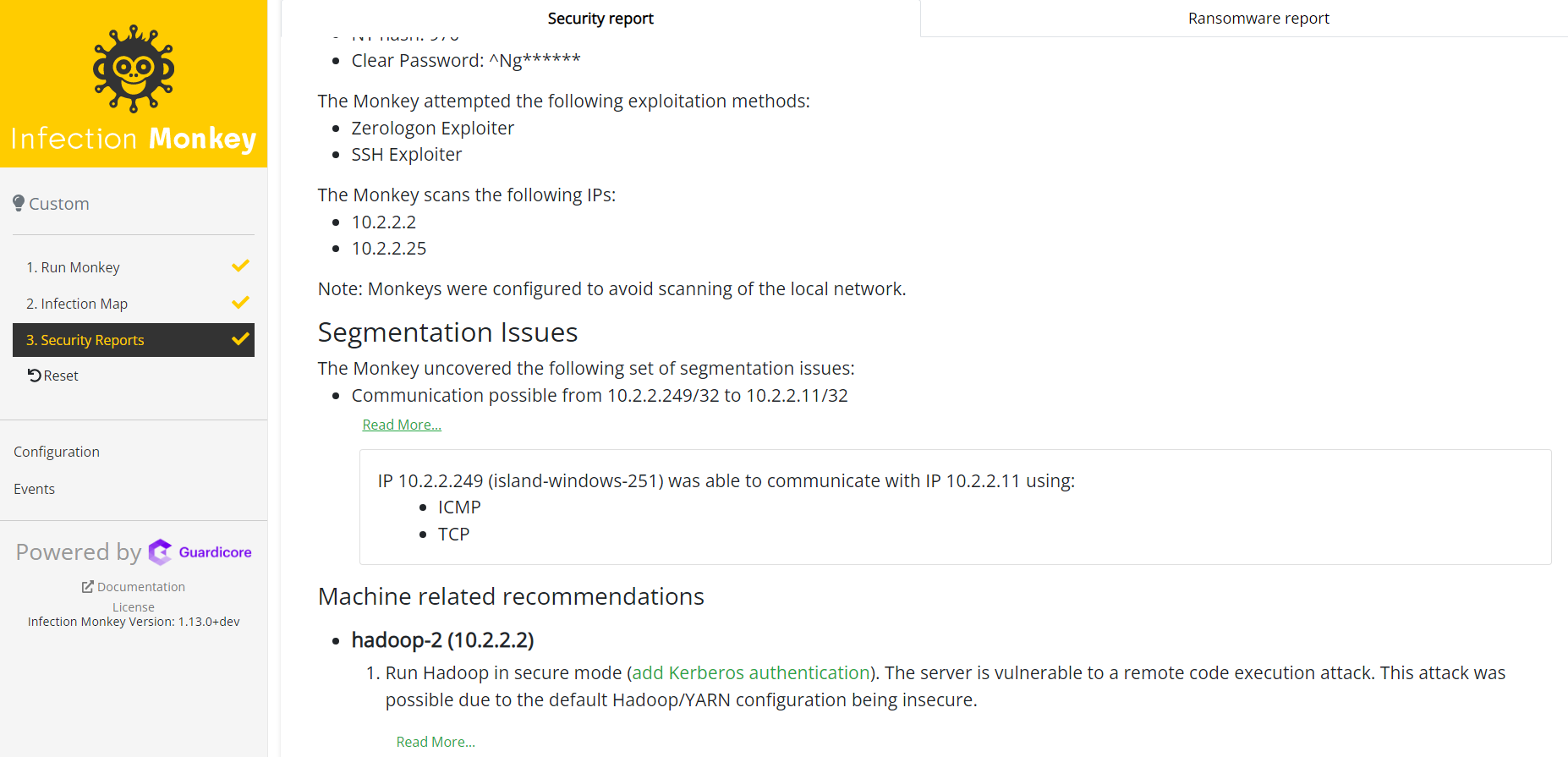
Segmentation issues
This section reports the segmentation issues in your network.
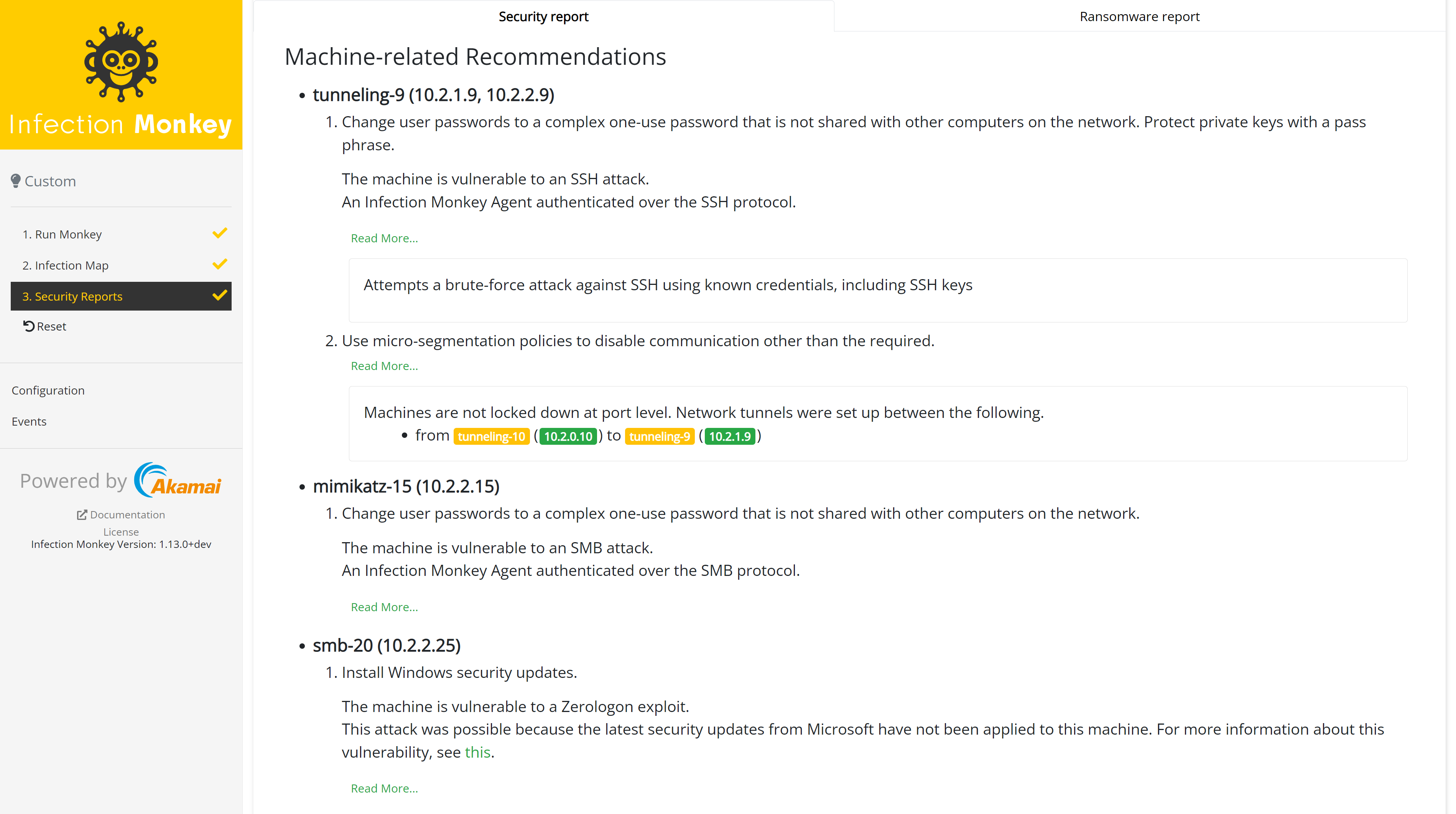
Machine-related recommendations
Here, you will find recommendations for improving your network's security, including actionable mitigation steps.
The network from the Monkey's eyes
This section contains a summary of what Infection Monkey found, including details of scanned servers, breached servers, and stolen credentials.
Updated over 2 years ago
