Malware Masquerade
Description
Masquerade- to assume the appearance of something one is not.
[Source: Merriam Webster].
A common way of detecting and identifying an executable as malware is to write a detection rule (as found in a tool like YARA) that checks for strings or unique byte sequences within a file. The Malware Masquerade feature allows users to specify strings or arbitrary data (bytes) that will be injected into the Agent binaries. This enables Infection Monkey Agents to masquerade as specific types of malware. This is particularly useful for anyone writing their own detection rules and need a way to test them, or anyone looking to improve malware simulations' fidelity.
Using Malware Masquerade
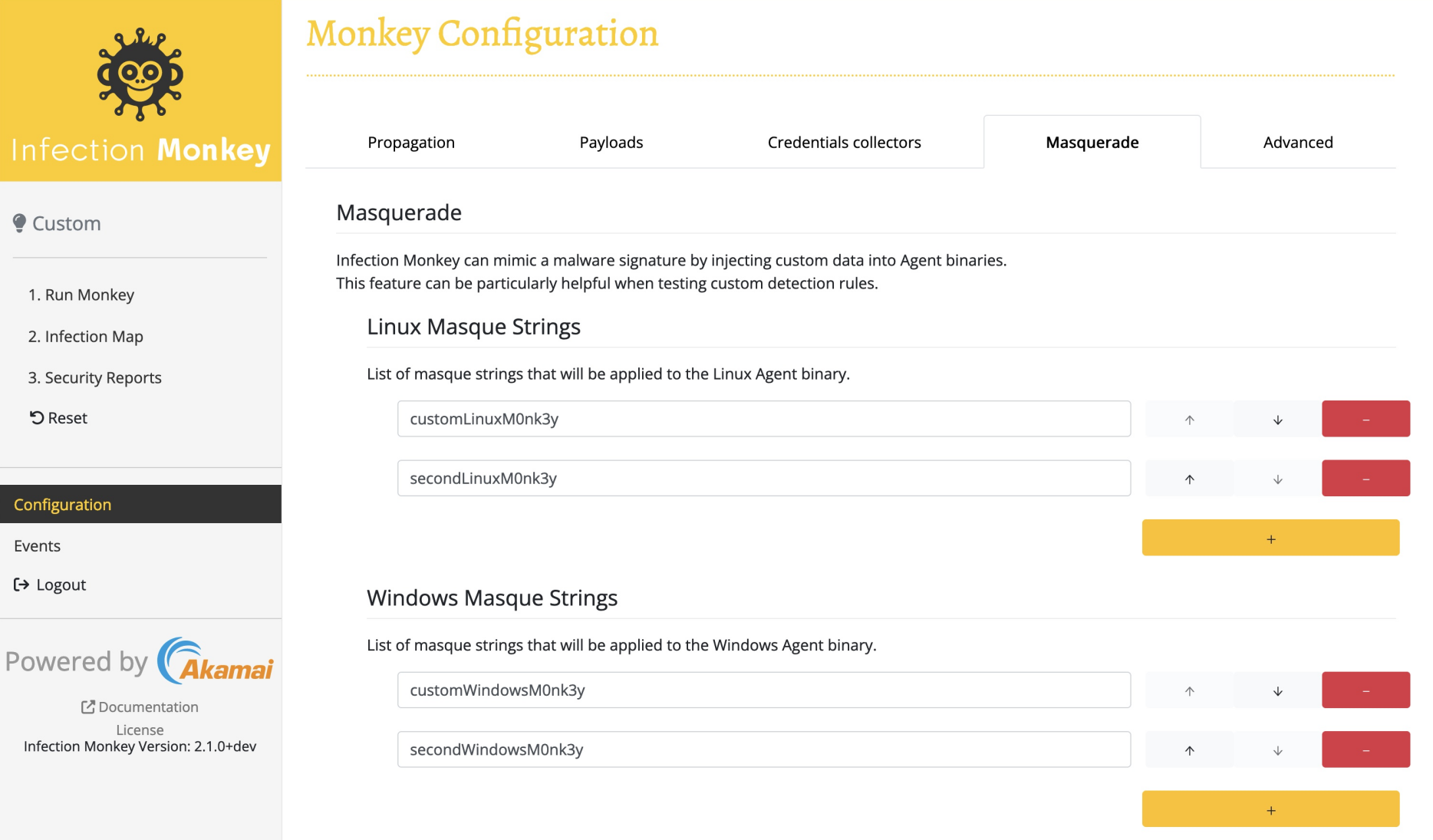
Configuring strings
The UI allows you to specify any number of strings to include within the Linux or Windows Agent binaries. It's as simple as adding these strings to either list in the "Masquerade" tab of the "Configuration" screen and clicking "Submit". You can verify the success of this operation by downloading the binary and using the Linux strings command
```bash
curl https://<SERVER_IP>:5000/api/agent-binaries/linux -k -o monkey-linux-64 && strings monkey-linux-64 | grep <MY_STRING>
```
Updated over 2 years ago
