Ransomware report
Check out the Infection Monkey's ransomware simulation documentation and the documentation for other available reports.
The Infection Monkey can be configured to simulate a ransomware attack on your network. After running, it generates a Ransomware Report that provides insight into how ransomware might behave within your environment.
The report is split into three sections:
Breach
The breach section shows when and where the ransomware infection began.
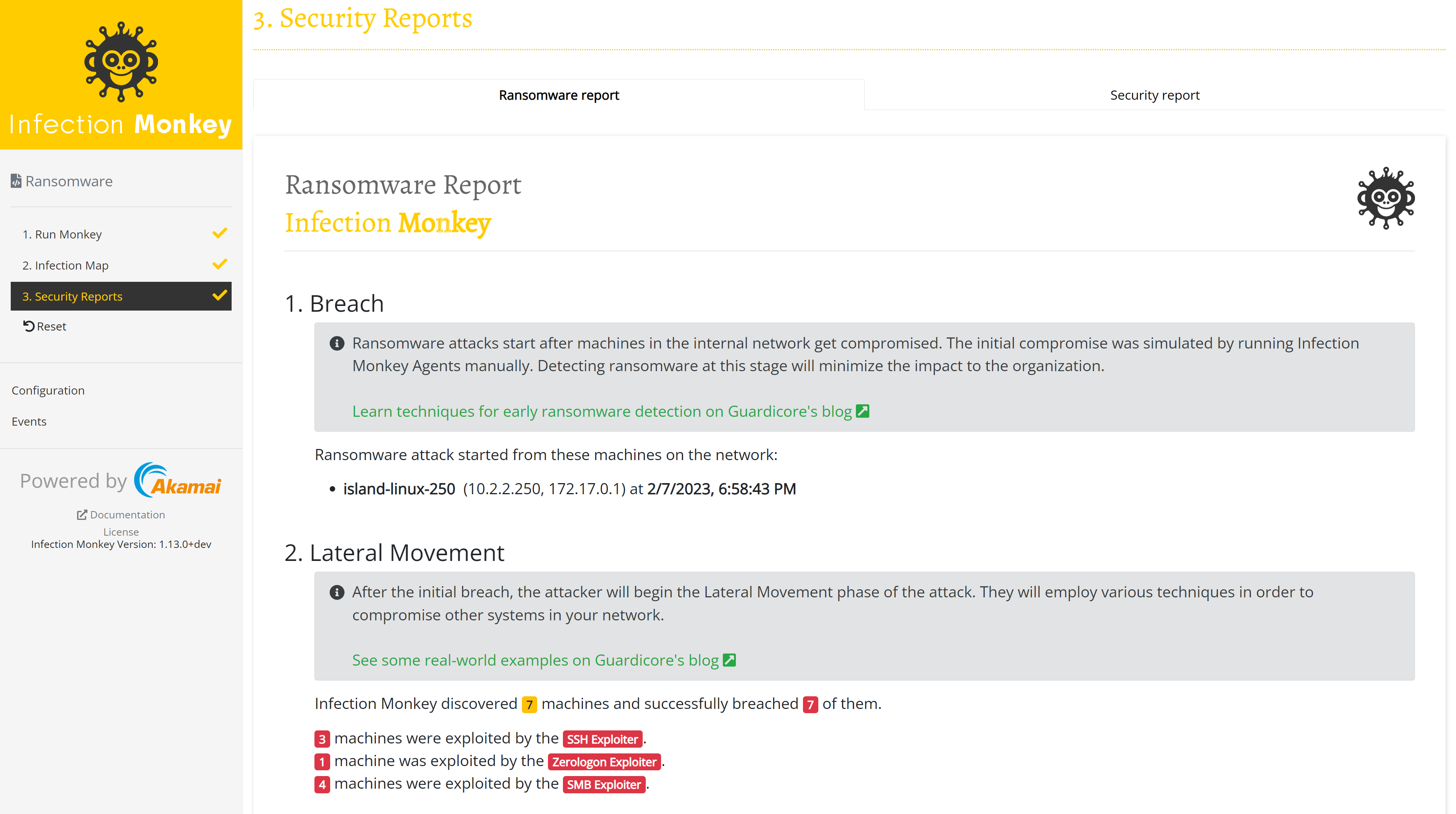
Lateral movement
The lateral movement section provides information about how the simulated ransomware was able to propagate through your network.
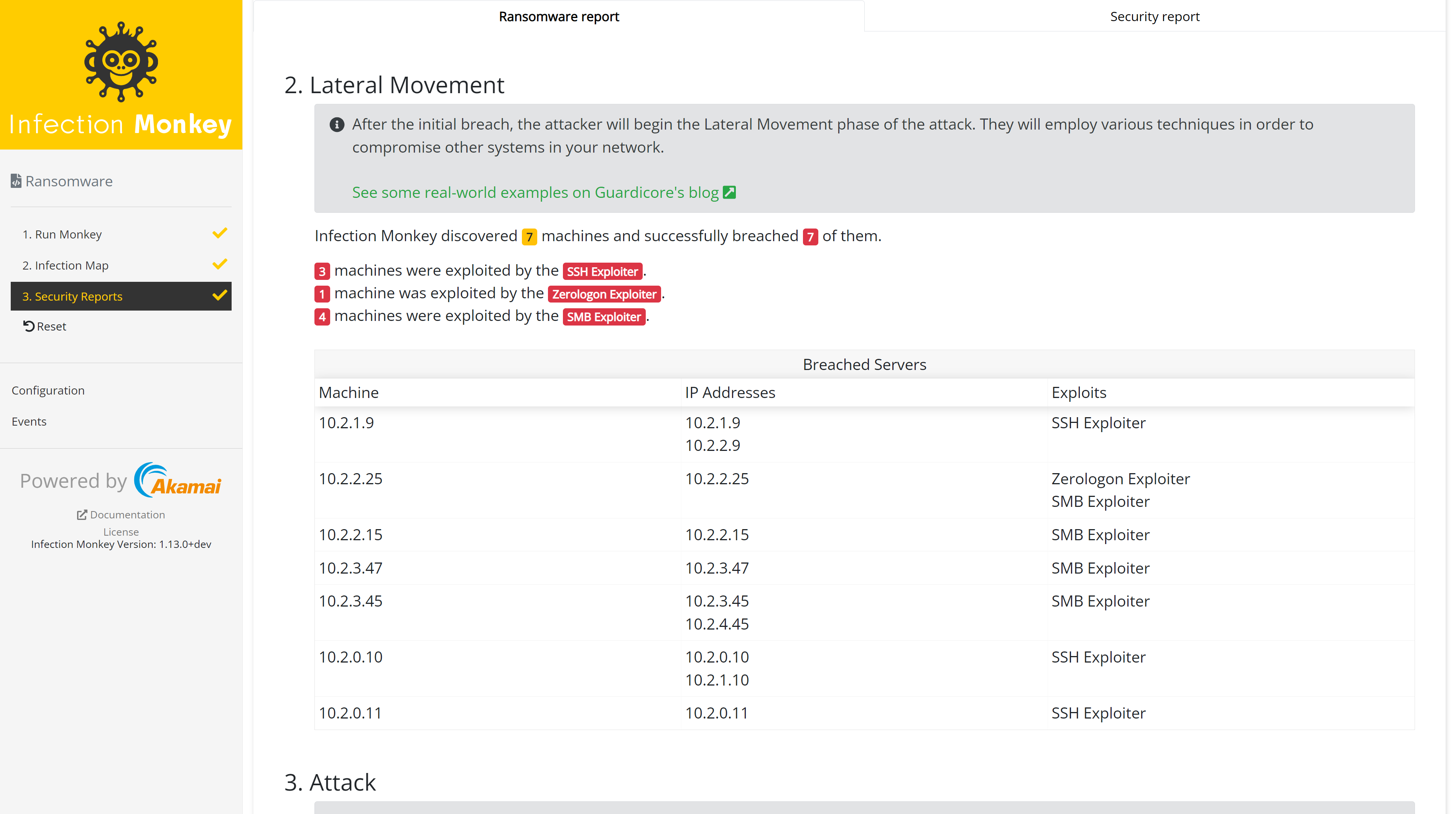
Attack
The attack section shows the details of what the simulated ransomware successfully encrypted, including a list of specific files.
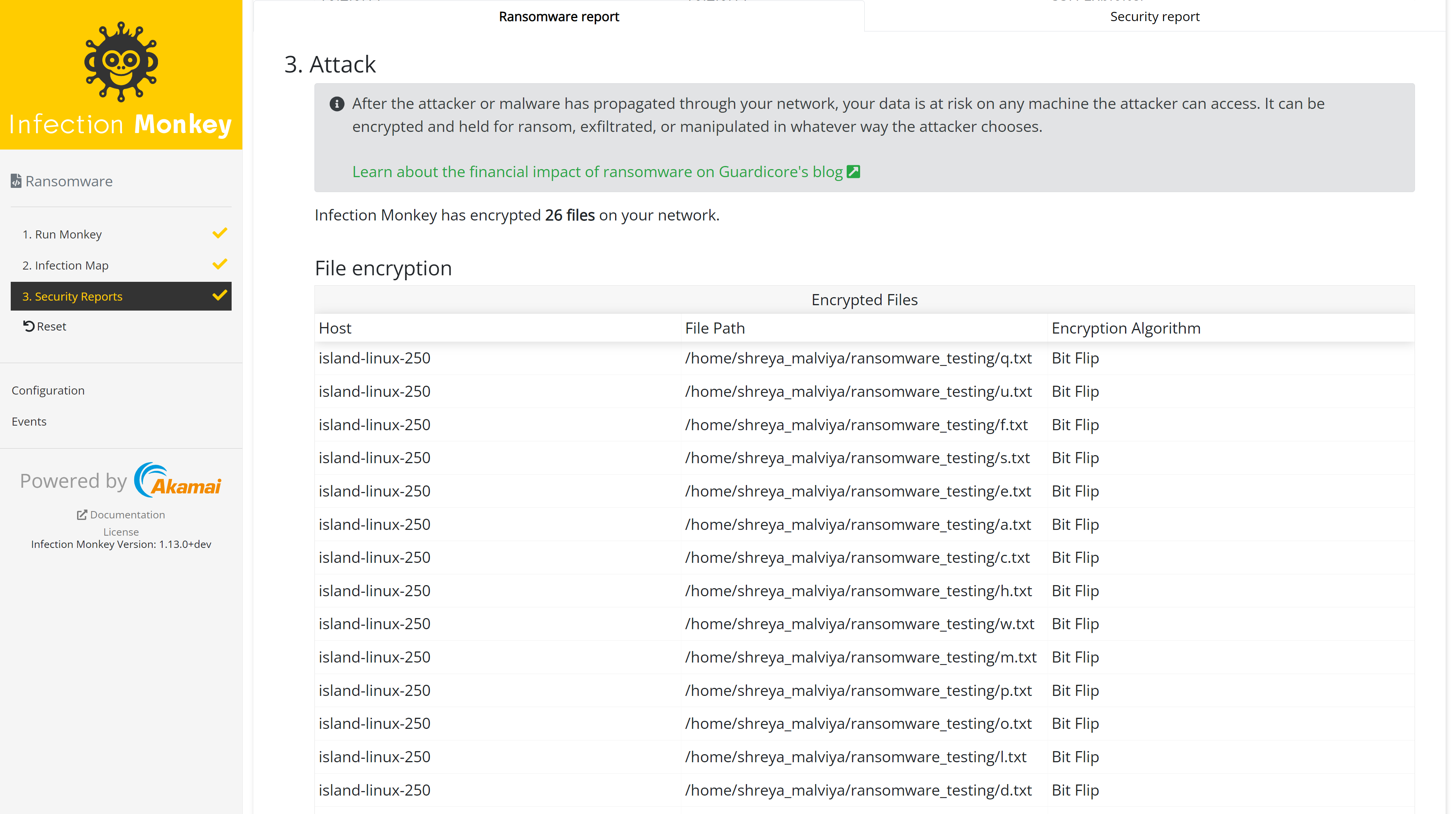
Updated over 2 years ago
