Ransomware simulation
The Infection Monkey can simulate a ransomware attack on your network using a set of configurable behaviors. To simulate the behavior of ransomware as accurately as possible, the Infection Monkey can encrypt user-specific files using a fully reversible algorithm. A number of mechanisms are in place to ensure that all actions performed by the encryption routine are safe for production environments.
Workflow
1. Prepare your environment for a ransomware simulation
The Infection Monkey will only encrypt files that you allow it to. To take full advantage of the Infection Monkey's ransomware simulation, you'll need to provide the Infection Monkey with a directory that contains files that are safe for it to encrypt. The recommended approach is to use a configuration management tool, such as Ansible or PsExec, or even a Windows GPO, to add a "ransomware target" directory to each machine in your
environment. The Infection Monkey can then be configured to encrypt files in this directory.
2. Configure encryption
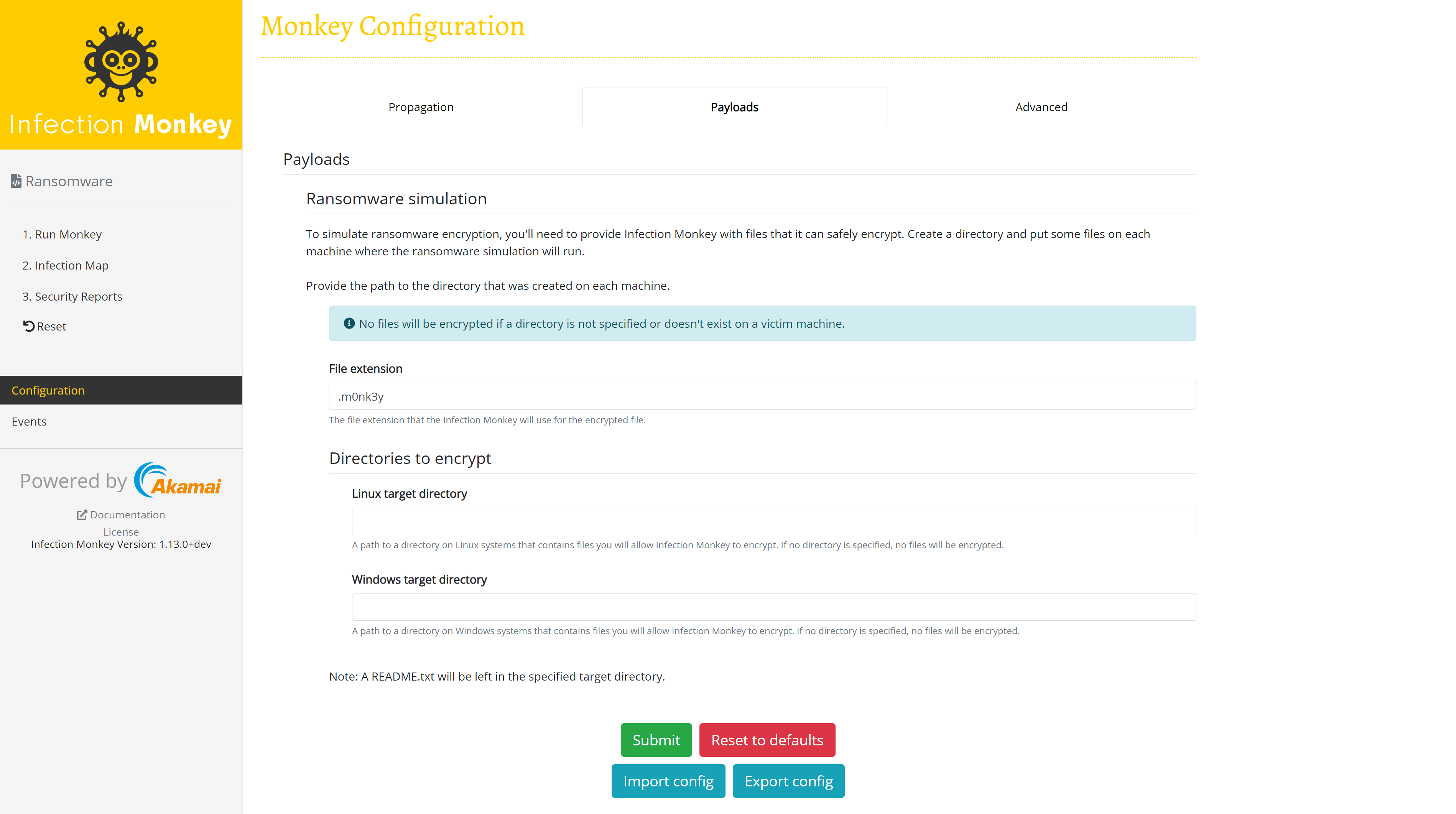
To ensure minimum interference and easy recoverability, the ransomware simulation will only encrypt files contained in a user-specified directory. If no directory is specified, no files will be encrypted.
Infection Monkey appends the .m0nk3y file extension to files that it encrypts. You may optionally provide a custom file extension for Infection Monkey to use instead. You can even provide no file extension, but take caution: you'll no longer be able to tell if the file has been encrypted based on the filename alone.
3. Configure propagation
If you would like the Infection Monkey to propagate through the network,
Configure the network settings and one or more exploiters.
4. Run the Agent
Once everything is configured to your liking, simply run the agent to begin the
ransomware simulation.
5. Clean up
After the simulation is complete, you can use the same mechanism you used in
step 1 to either remove the target directory or replace the encrypted files with unencrypted files. In most cases, there's no need to attempt to decrypt the files, as you should still have the originals.
File encryption
Files are "encrypted" in place with a simple bit flip. Encrypted files are renamed to have a file extension (.m0nk3y by default) appended to their names. This is a safe way to simulate encryption since it is easy to "decrypt" your files. You can perform a bit flip on the files again and rename them to remove the appended .m0nk3y extension.
Flipping a file's bits is sufficient to simulate the encryption behavior of ransomware, as the data in your files has been manipulated (leaving them temporarily unusable). Files are then renamed with a new extension appended, which is similar to the way that many ransomwares behave. As this is a simulation, your security solutions should be triggered to notify you or prevent these changes from taking place.
Technical details
Files being encrypted
During the ransomware simulation, attempts will be made to encrypt all regular files with targeted file extensions in the configured directory (see below). The simulation is not recursive, i.e. it will not touch any files in sub-directories of the configured directory. The Infection Monkey will not follow any symlinks or shortcuts.
These precautions are taken to prevent Infection Monkey from accidentally encrypting files that you didn't intend to encrypt.
Leaving a README.txt file
Many ransomware packages leave a README.txt file on the victim's machine with an explanation of what has occurred and instructions for paying the attacker. The Infection Monkey will also leave a README.txt file in the target directory on the victim machine in order to replicate this behavior.
The README.txt file informs the user that a ransomware simulation has taken place and that they should contact their administrator. The contents of the file can be found here.
Updated over 1 year ago
