Frequently asked questions
Below are some of the most common questions we receive about the Infection Monkey. If the answer you're looking for isn't here, talk to us on our Slack channel, email us at support@infectionmonkey.com or open an issue on GitHub.
Where can I get the latest version of the Infection Monkey?
For the latest stable release, visit our download page. This is the recommended and supported version!
If you want to see what has changed between versions, refer to the releases page on GitHub. For the latest development version, visit the develop version on GitHub.
I updated to a new version of the Infection Monkey and I'm being asked to delete my existing data directory. Why?
The data directory contains the Infection Monkey's database and other internal data. For the new version of Infection Monkey to work flawlessly, you need to set up a data directory with a compatible structure.
If you would like to save the data gathered from the Monkey's previous runs, you can make a backup of your existing data directory before deleting it.
How can I use an old data directory?
To use the data stored in a data directory from an older version, reinstall the version of the Monkey Island which matches your data directory's version. Then, copy the backup of your old data directory to the appropriate location.
How long does a single Infection Monkey Agent run? Is there a time limit?
The Infection Monkey Agent shuts off either when it can't find new victims or it has exceeded the quota of victims as defined in the configuration.
How long does it take to stop all running Infection Monkey Agents?
On the Infection Map page, when Kill All Monkeys is clicked, the Agents try to finish execution safely. This can take up to 2 minutes, but will be much shorter on average.
Is Infection Monkey a malware/virus?
Infection Monkey is not malware, but it uses similar techniques to safely simulate malware on your network.
Because of this, some antivirus solutions flag Infection Monkey as malware during installation. If this happens, verify the integrity of the downloaded installer first. Then, create a new folder and disable antivirus scan for that folder. Lastly, reinstall the Infection Monkey in the newly created folder.
How do I reset the Monkey Island password?
In order to reset the Monkey Island password, you'll need to perform a factory reset .
Should I run the Infection Monkey continuously?
Yes, this will allow you to verify that the Infection Monkey identified no new security issues since the last time you ran it.
Does the Infection Monkey require a connection to the internet?
The Infection Monkey does not require internet access to function.
If internet access is available, the Infection Monkey will use the internet for two purposes:
- To check for updates.
- To check if machines can reach the internet.
What internet queries does the Infection Monkey perform?
The Monkey performs queries out to the Internet on these separate occasions:
- While the Monkey Island Server is being set up, a GET request with the deployment
type and version number is sent to the analytics server. This information is
collected to understand which deployment types and versions are no longer used
and can be deprecated. - After the Monkey Island starts, a GET request with the deployment type is sent to the update server to fetch the latest version number and a download link for it. This information is used by the Monkey Island to suggest an update if one is available.
- When you install a plugin it is downloaded from our official repository.
Logging and how to find logs
Downloading logs
Both the Agent and Island logs can be downloaded from the Infection Map page. See how to download logs for more information.
Log locations
See the logs reference page.
Running the Infection Monkey in a production environment
How much of a footprint does the Infection Monkey leave?
The Infection Monkey leaves hardly any trace on the target system. It will leave log files in temporary directories.
What's the Infection Monkey Agent's impact on system resources usage?
The Infection Monkey Agent uses less than a single-digit percent of CPU time and very low RAM usage. For example, on a single-core Windows Server machine, the Infection Monkey Agent consistently uses 0.06% CPU, less than 80MB of RAM, and a small amount of I/O periodically.
If you do experience any performance issues please let us know on our Slack channel or open an issue on GitHub.
What are the system resource requirements for Monkey Island?
See the System requirements page.
Is it safe to use real passwords and usernames in the Infection Monkey's configuration?
Absolutely! User credentials are stored encrypted in the Monkey Island Server.
This information can only be seen by individuals who have the credentials to access the Monkey Island.
How do you store sensitive information on Monkey Island?
Sensitive data such as passwords, SSH keys and hashes are stored on the Monkey Island's database in an encrypted fashion. This data is transmitted to the Infection Monkey Agents in an encrypted fashion (HTTPS) and is not stored locally on victim machines.
When you reset the Monkey Island configuration, the Monkey Island wipes the information.
How stable are the exploits used by the Infection Monkey? Will the Infection Monkey crash my systems with its exploits?
The Infection Monkey does not use any exploits or attacks that may impact the victim system.
This means we avoid using some powerful (and famous) exploits such as EternalBlue. This exploit was used in WannaCry and NotPetya with huge impact, but, because it may crash a production system, we aren't using it.
After I've set up Monkey Island, how can I execute the Infection Monkey Agent?
Work through our tutorials or see our detailed getting started guide.
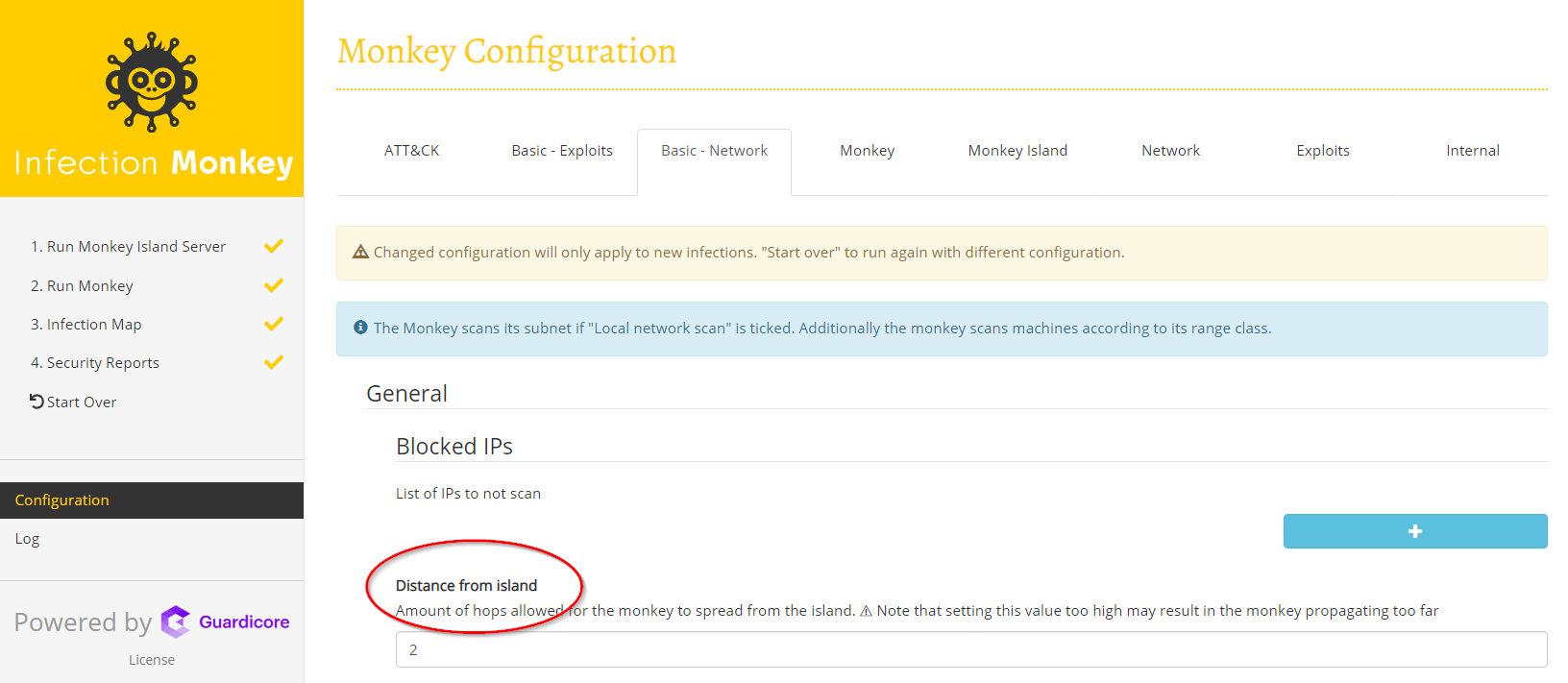
How can I make the Infection Monkey Agent propagate "deeper" into the network?
If you wish to simulate a very “deep” attack into your network, you can increase the propagation depth parameter in the configuration. This parameter tells the Infection Monkey how far to propagate into your network from the “patient zero” machine.
To do this, change the Configuration -> Propagation -> General -> Maximum scan depth configuration option:
Can I limit how the Infection Monkey propagates through my network?
Yes! To limit how the Infection Monkey propagates through your network, you can:
Adjust the scan depth
The scan depth limits the number of hops that the Infection Monkey Agent will spread from patient zero. If you set the scan depth to one, the Agent will only reach a single hop from the initially infected machine. Scan depth does not limit the number of devices, just the number of hops.
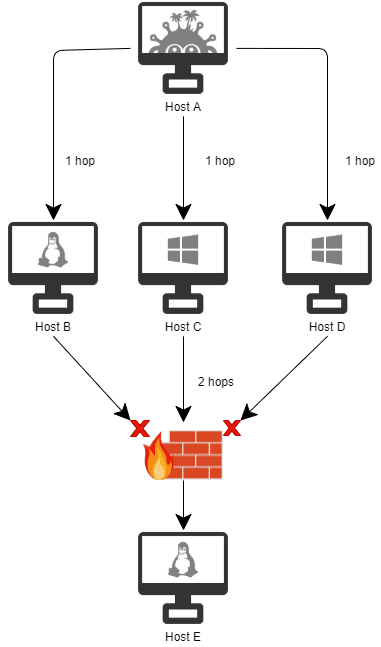
Example: In this example, the scan depth is set to two. Host A scans the network and finds hosts B, C, D and E. The Infection Monkey agent successfully propagates from Host A to Host C. Since the scan depth is 2, the agent will pivot from Host C and continue to scan other machines on the network. However, if Host C successfully breaches Host E, it will not pivot further nor continue to scan or propagate.
Enable or disable scanning the local subnet
You can find the settings that define how the Infection Monkey will scan your network in Configuration -> Propagation -> Network analysis. If enabled, the Scan Agent's networks setting instructs an Agent to scan its entire local subnet.
Add IPs to the IP allow list
You can specify which hosts you want the Infection Monkey Agents to attempt to scan in the Configuration -> Network -> Scan target list section.
Add IPs to the IP block list
If there are any hosts on your network that you would like to prevent the
Infection Monkey from scanning or exploiting, you can add them to the list of
"Blocked IPs" in Configuration -> Propagation -> Network analysis -> Blocked IPs.
How can I get involved with the project?
Infection Monkey is an open-source project, and we welcome contributions and contributors. Check out the contribution documentation for more information.
About the project 🐵
How did you come up with the Infection Monkey?
Oddly enough, the idea of proactively breaking a network to test its survival wasn't born in the security industry. In 2011, the streaming giant Netflix released Chaos Monkey, a tool designed to randomly disable the company's production servers to verify that they could survive network failures without any customer impact. Netflix's Chaos Monkey became a popular network resilience tool, breaking the network in a variety of failure modes, including connectivity issues, invalid SSL certificates and randomly deleting VMs.
Inspired by this concept, Guardicore Labs developed its own attack simulator - the Infection Monkey - to run non-intrusively within existing production environments. The idea was to test the resiliency of modern data centers against attacks and give security teams the insights they need to make informed decisions and enforce tighter security policies. Since its launch in 2017, Infection Monkey has been used by hundreds of information technology teams from across the world to find weaknesses in their on-premises and cloud-based data centers.
Updated over 1 year ago
