Overview of Shield NS53
Akamai Shield NS53 is a DNS proxy that protects your origin infrastructure, such as an authoritative DNS name server, firewall, or a global server load balancer, from DNS resource exhaustion attacks. These attacks usually overwhelm DNS name servers so they can no longer respond to valid queries. Attackers flood DNS name servers with requests to nonexistent subdomains and force servers to reply with nonexistent domain (NXDOMAIN) responses.
Shield NS53 protects DNS name servers from DNS resource exhaustion attacks by handling DNS traffic on their behalf and enforcing security policies.
As a DNS proxy, Shield NS53:
- Filters traffic to block fake DNS requests, allowing only valid DNS queries to reach your DNS name servers.
- Reduces the load on DNS name servers by responding to valid DNS queries from the cache and forwarding queries to the origin server only when necessary.
- Reduces latency by using Akamai's global Names anycast network, responding to queries from the closest point of presence.
- Monitors incoming requests and limits the number of DNS requests per second if the number of requests per resolver exceeds a global limit.
- Limits large responses to prevent DNS resource exhaustion attacks targeting DNS servers.
To set up Shield NS53, you create a shield in the Control Center. As part of this configuration, you provide:
- IP addresses of your origin name servers or on-premise global server load balancers (GSLBs).
- A record that's used to confirm name server health in case a name server is unavailable. While the health check record can be any query type, Akamai recommends you use a TXT or SOA record type for this check as these records are static on your name servers. After you create the shield, you can run a health status check with this record at any time.
- List of zones that Shield NS53 filters traffic from. You select the filtering mode for each zone. The filtering mode setting determines how Shield NS53 handles DNS traffic and what traffic it forwards to the origin name servers. For more on these modes, see Filtering modes for shield zones.
Akamai assigns service fully qualified domain names (FQDNs) or IP addresses (IPv4 and IPv6 addresses) to your shield configuration as part of the setup process.
After setting up your Shield NS53 configuration, including your zone settings, you must change the delegation of your zone records to the Shield NS53 service FQDNs or IP addresses. These addresses are available in your shield configuration in Control Center. This step is necessary for Shield NS53 to receive your DNS traffic.
Depending on your DNS configuration, you can delegate traffic to Shield NS53 with one of the following methods:
- An A and AAAA record update. Update the A and AAAA record of your name servers to point to the shield service FQDNs or IP addresses.
- An NS record update. Update the NS record of your parent zone to include the shield service FQDNs or IP addresses.
NS records specify which name servers have the authority to respond to DNS requests for your domain. After making these updates, Shield NS53 receives DNS traffic for the zones you delegated. For more information on the setup process, see Set up and go live with Shield NS53.
Filtering modes for shield zones
As you create and manage a shield configuration, you can select the filtering mode for each zone. The filtering mode defines the security policy for zones and determines how Shield NS53 handles traffic. With this setting, you can block non-existent domains and only forward valid DNS traffic to your name servers.
These filtering modes are available for the zones you specify:
- Caching (Cache-based filtering). In this mode, Shield NS53 operates as a DNS resolver without applying any security policy. It forwards every DNS request to your DNS name server and obtains the response. Shield NS53 then caches these responses for the duration of the Time-to-Live (TTL) value provided by your name servers. For negative answers, Shield NS53 will default the TTL to 60 seconds.
- Manual. In this mode, Shield NS53 applies a security policy by only allowing the DNS records that you specify in the shield user interface or in the Edge DNS API. Shield NS53 drops any requests that do not match this list.
- Automatic. In this mode, Shield NS53 applies a security policy by only allowing DNS records obtained from your DNS name servers through authoritative zone transfer (AXFR). DNS records are automatically fetched from your origin server through a zone transfer agent (AXFR target IP address). Shield NS53 drops any records that do not match the DNS records. This ensures Shield NS53 blocks invalid DNS requests that are not within the specified zone.
If you select this mode, you can also configure alternate transfer targets to provide separate IP addresses that are dedicated to transferring the master zone files instead of relying on the name server to perform this task. - Deny all. In this mode, Shield NS53 drops all DNS traffic targeting the configured zone.
As you configure the shield zone and filtering mode, you can also set an apex alias. An apex alias lets you define the apex record that you want Shield NS53 to resolve instead of forwarding it to the origin name server for resolution. For example, if you set apexalias.example.com as the alias for the example.com zone, Shield resolves requests to example.com with the answer for apexalias.example.com. Requests to domains like www.example.com are still handled by Shield using the filtering mode you select.
Network Flow
Shield NS53 is positioned in front of your organization’s name servers to protect them from resource exhaustion attacks.
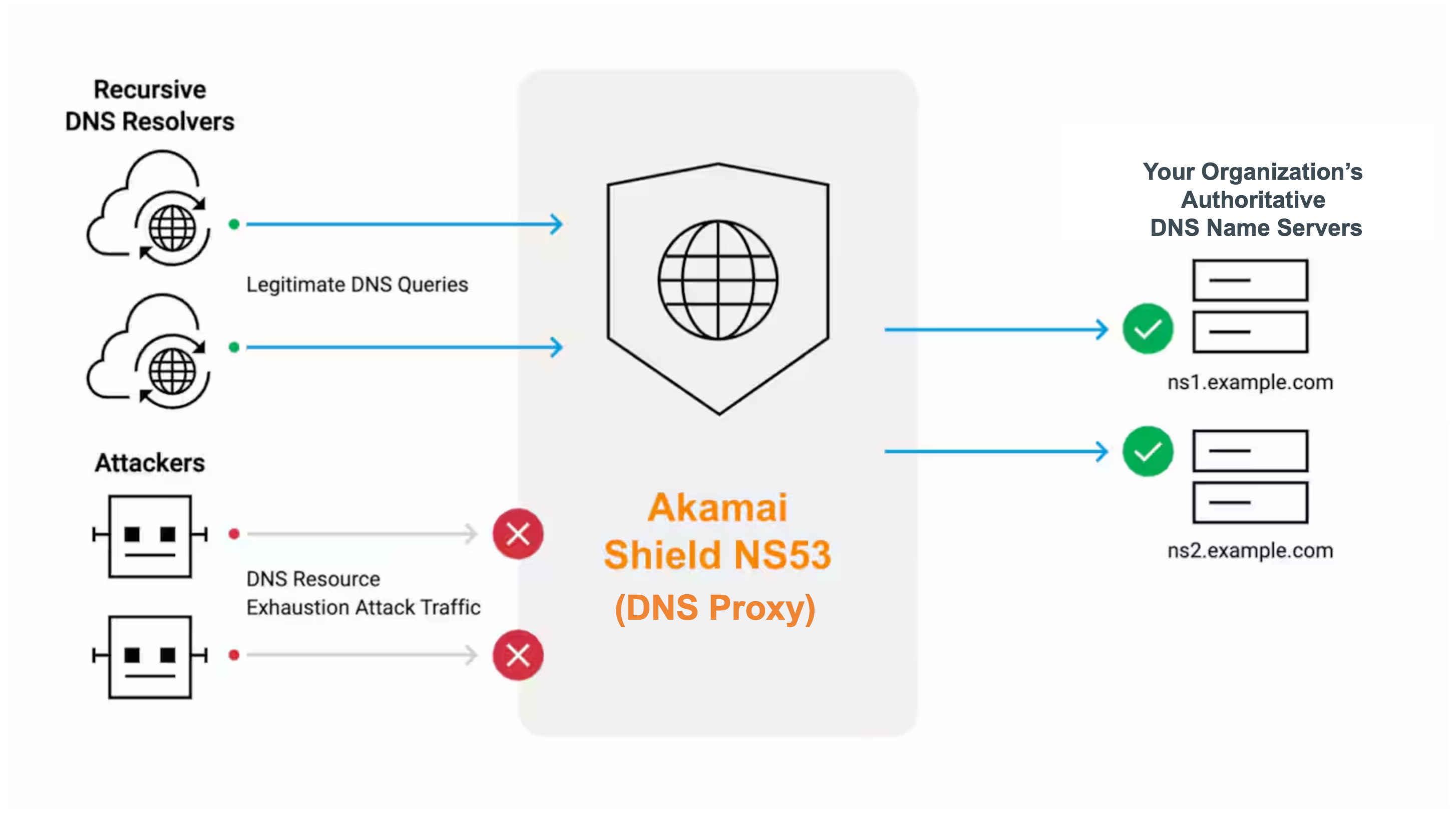
After you delegate traffic to Shield NS53, the following network flow applies:
- DNS queries are directed to Shield NS53.
- Shield NS53 uses DNS anycast to route DNS requests to the closest Shield NS53 Point of Presence (PoP) based on the user's location.
- Shield NS53 checks the incoming DNS request against your shield configuration. The filtering settings you apply to the shield configuration function as an allow list security policy.
- If the request is allowed based on this configuration, it forwards the request to the origin server. Shield NS53 caches the response from the origin server, honoring the original Time-to-Live (TTL) values.
- If the request is denied based on your shield configuration, Shield NS53 drops it with an NXDOMAIN/REFUSED response.
Allowed domains or FQDNs
As you configure manual or automatic filtering, consider this behavior for the domains or fully qualified domains (FQDN) you allow:
- If you use a wildcard for a domain or a zone file includes an NS delegation, all records for that domain, including its subdomains, are allowed. For example, if you specify
*example.com, Shield NS53 allows requests fromwww.example.comandwww2.example.com. - If you specify the full record without a wildcard or an NS delegation in the zone file, Shield NS53 only allows the record as it’s exactly defined. It does not allow additional subdomains, providing a more strict policy.
If you use automatic filtering or upload a zone file when setting domains for manual filtering, Shield NS53 checks for wildcards and NS delegations in your zone file. If they are used, shield allows the subdomains corresponding to those records.
Default response policy
Regardless of the filtering mode, Shield NS53 applies this behavior:
- If a DNS request arrives from a domain that is not in your zone namespace, the request is served with a REFUSED response.
- If a DNS request arrives from a domain that is part of your namespace but it is not specifically allowed as a FQDN, then the request is served with an NXDOMAIN response. For example, if you only allow the FQDN
www.example.comand the incoming request is fromattack.example.com, then this traffic is dropped with an NXDOMAIN response.
Shield statuses
As you create and modify your shield configuration, one of these statuses may appear:
- Active. Indicates the shield configuration is fully propagated, and it is ready to receive traffic.
- Pending. Indicates there is a configuration update that is not yet fully propagated. This update can take up to 30 minutes to propagate.
- New. Indicates the shield configuration was newly created and no service FQDNS or IP addresses are assigned to shield yet. After you create a shield, it can take up to 30 minutes before Akamai assigns service FQDNS or IP addresses to your configuration.
- Error. Indicates an internal error has occurred. Contact Akamai customer support.
Analytics
You can run and view reports on Shield NS53 traffic, events, and service availability. For more information, see Shield NS53 analytics.
Updated about 2 months ago
