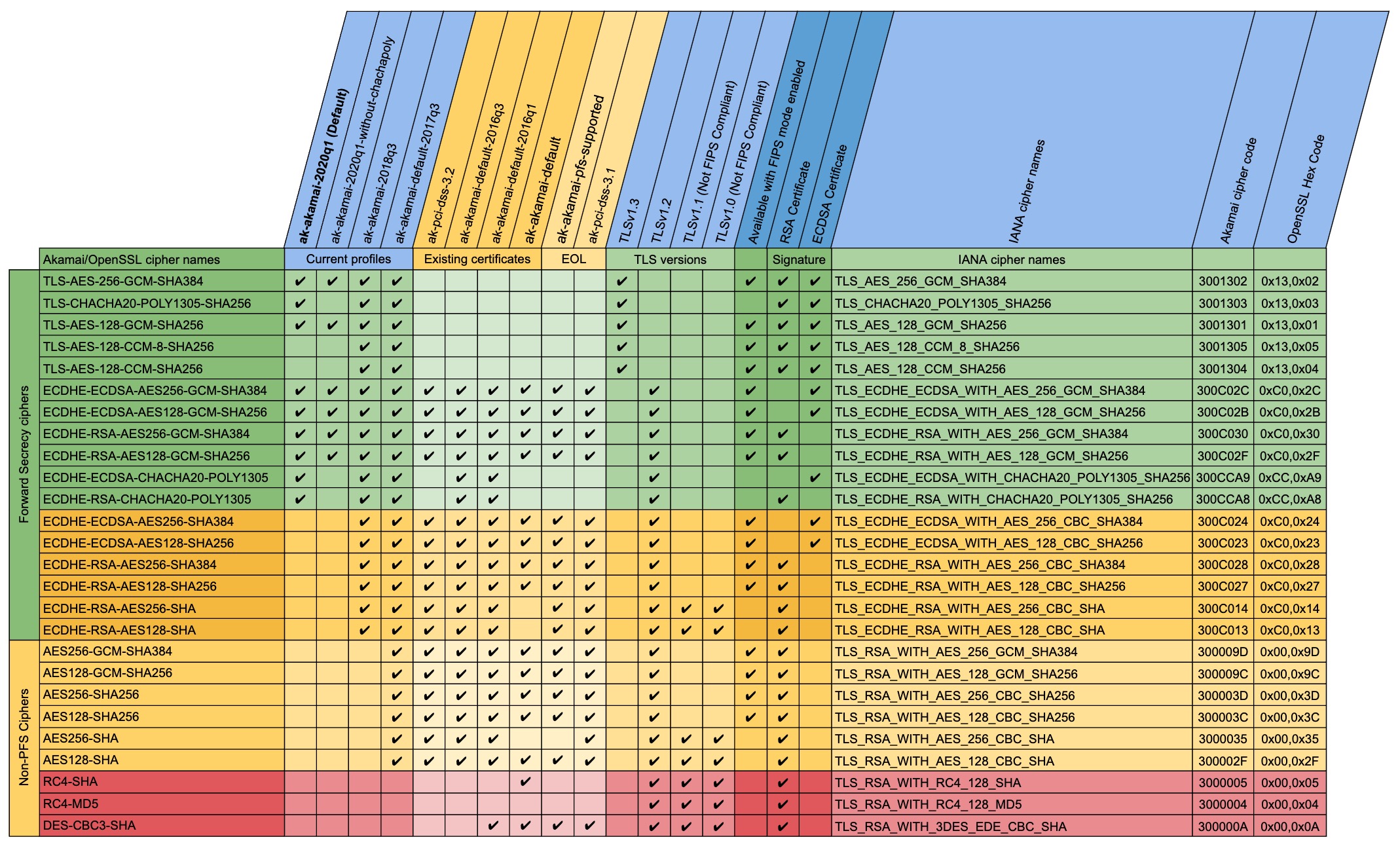
Akamai’s web properties can be configured with various SSL/TLS cipher suites. Through CPS, you can select a cipher profile which, in turn, selects a list of cipher suites which will be available for use during TLS handshake. Once enabled, Akamai does not update existing cipher profiles, except in the case of security incidents. Customers are encouraged to review their enrollment settings, and update to the latest cipher profile whenever possible.
This illustration shows enumeration of the currently supported cipher profiles:
All cipher suites in the “Active” cipher profiles are suitable for PCI and FedRAMP traffic (for certificates provisioned on Enhanced TLS). Cipher suites in each profile below are listed in the order they will be presented to connecting clients. If a client presents the ChaCha20-Poly1305 cipher, Akamai will move it to the top of the server-presented list, regardless of what is described below. This feature is to enable the best performance for those mobile devices which do not include AES acceleration hardware.
📘
For PFS (Forward Secrecy) support, HTTP/2 support, TLS 1.3 support, and PCI compliance, you can select the ak-akamai-2020q1 or ak-akamai-2018q3 cipher profile.
📘
For FedRAMP and FIPS compliance, select the ak-akamai-2020q1 cipher profile and enable FIPS mode on the certificate.
These cipher profiles are available to all users, for all certificates, and all enrollments.
| Profile | Cipher Suites |
|---|
ak-akamai-2020q1 (Default and recommended profile)
This profile supports TLSv1.2 and TLSv1.3 only, and is
the current default for new certificates as of Sep 16, 2020.
This profile is recommended for all certificates, and can
be selected to help obtain an “A” rating on the Qualys SSL
Labs server test.
| - TLS-AES-256-GCM-SHA384
- TLS-CHACHA20-POLY1305-SHA256
- TLS-AES-128-GCM-SHA256
- ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-CHACHA20-POLY1305
- ECDHE-RSA-CHACHA20-POLY1305
|
ak-akamai-2020q1-without-chachapoly
This profile supports TLSv1.2 and TLSv1.3 only, and excluding ChaChaPoly ciphers.
| - TLS-AES-256-GCM-SHA384
- TLS-AES-128-GCM-SHA256
- ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
|
ak-akamai-2018q3
This profile can be used with all TLS versions, including
TLS 1.3. It includes CBC ciphers which are no longer
recommended for use, but may be needed to support
older clients.
| - TLS-AES-256-GCM-SHA384
- TLS-CHACHA20-POLY1305-SHA256
- TLS-AES-128-GCM-SHA256
- TLS-AES-128-CCM-8-SHA256
- TLS-AES-128-CCM-SHA256
- ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-CHACHA20-POLY1305
- ECDHE-RSA-CHACHA20-POLY1305
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
|
ak-akamai-default-2017q3
This profile can be used with all TLS versions, including
TLS 1.3. This profile is intended to support legacy clients
which do not support Forward Secrecy, or still require
TLS 1.0 or TLS 1.1 support.
| - TLS-AES-256-GCM-SHA384
- TLS-CHACHA20-POLY1305-SHA256
- TLS-AES-128-GCM-SHA256
- TLS-AES-128-CCM-8-SHA256
- TLS-AES-128-CCM-SHA256
- ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-CHACHA20-POLY1305
- ECDHE-RSA-CHACHA20-POLY1305
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES256-SHA
- AES128-SHA
|
These cipher profiles are no longer selectable for use. Existing enrollments configured with these profiles may continue to use them.
| Profile | Cipher Suites |
|---|
| ak-pci-dss-3.2 | - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES256-SHA
- AES128-SHA
|
| ak-akamai-default-2016q3 | - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-CHACHA20-POLY1305
- ECDHE-RSA-CHACHA20-POLY1305
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES256-SHA
- AES128-SHA
|
ak-akamai-default-2016q1
Note: Secure properties that need to support connections
from Internet Explorer on Windows XP or Windows Server
2000 should use the ak-akamai-default-2016q1 profile to
enable the insecure DES-CBC3-SHA cipher suite.
| - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-CHACHA20-POLY1305
- ECDHE-RSA-CHACHA20-POLY1305
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES256-SHA
- AES128-SHA
- DES-CBC3-SHA
|
| ak-akamai-default | - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES128-SHA
- RC4-SHA
- DES-CBC3-SHA
|
These cipher profiles are no longer selectable for use. If you have existing enrollments configured with these profiles, you may continue to use them. When modifying an enrollment with these profiles, you’ll see an error displayed in the CPS interface prompting you to change the profile. Automated certificate renewals will continue.
| Profile | Cipher Suites |
|---|
| ak-akamai-pfs-supported | - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES128-SHA
- DES-CBC3-SHA
|
| ak-pci-dss-3.1 | - ECDHE-ECDSA-AES256-GCM-SHA384
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-ECDSA-AES256-SHA384
- ECDHE-ECDSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA384
- ECDHE-RSA-AES128-SHA256
- ECDHE-RSA-AES256-SHA
- ECDHE-RSA-AES128-SHA
- AES256-GCM-SHA384
- AES128-GCM-SHA256
- AES256-SHA256
- AES128-SHA256
- AES256-SHA
- AES128-SHA
- DES-CBC3-SHA
|