Detect threats in running containers
Falco is a cloud native security tool that provides runtime security. It leverages custom rules on Linux kernel events and other data sources through plugins, enriching event data with contextual metadata to deliver real-time alerts. Falco enables the detection of abnormal behavior, potential security threats, and compliance violations.
Prerequisites
- The Falco app needs to be activated.
- This lab should be performed by a user designed as a platform administrator.
Generate threats
For this lab we'll install the event-generator in a Team namespace. The event-generator is a tool designed to generate events for both syscalls and k8s audits. The tool can be used to check if Falco is working properly. It does so by performing a variety of suspects actions which trigger security events. The event-event generator implements a minimalistic framework which makes easy to implement new actions.
-
Sign in with a user that has the
platform-administratorrole. -
Select the Admin team in the Team view.
-
In the main menu, click the Shell link.
-
Add the Falco security charts repository:
helm repo add falcosecurity https://falcosecurity.github.io/charts helm repo update -
Install the chart in your team namespace:
helm install team-labs falcosecurity/event-generator -n team-labs -
Sign out.
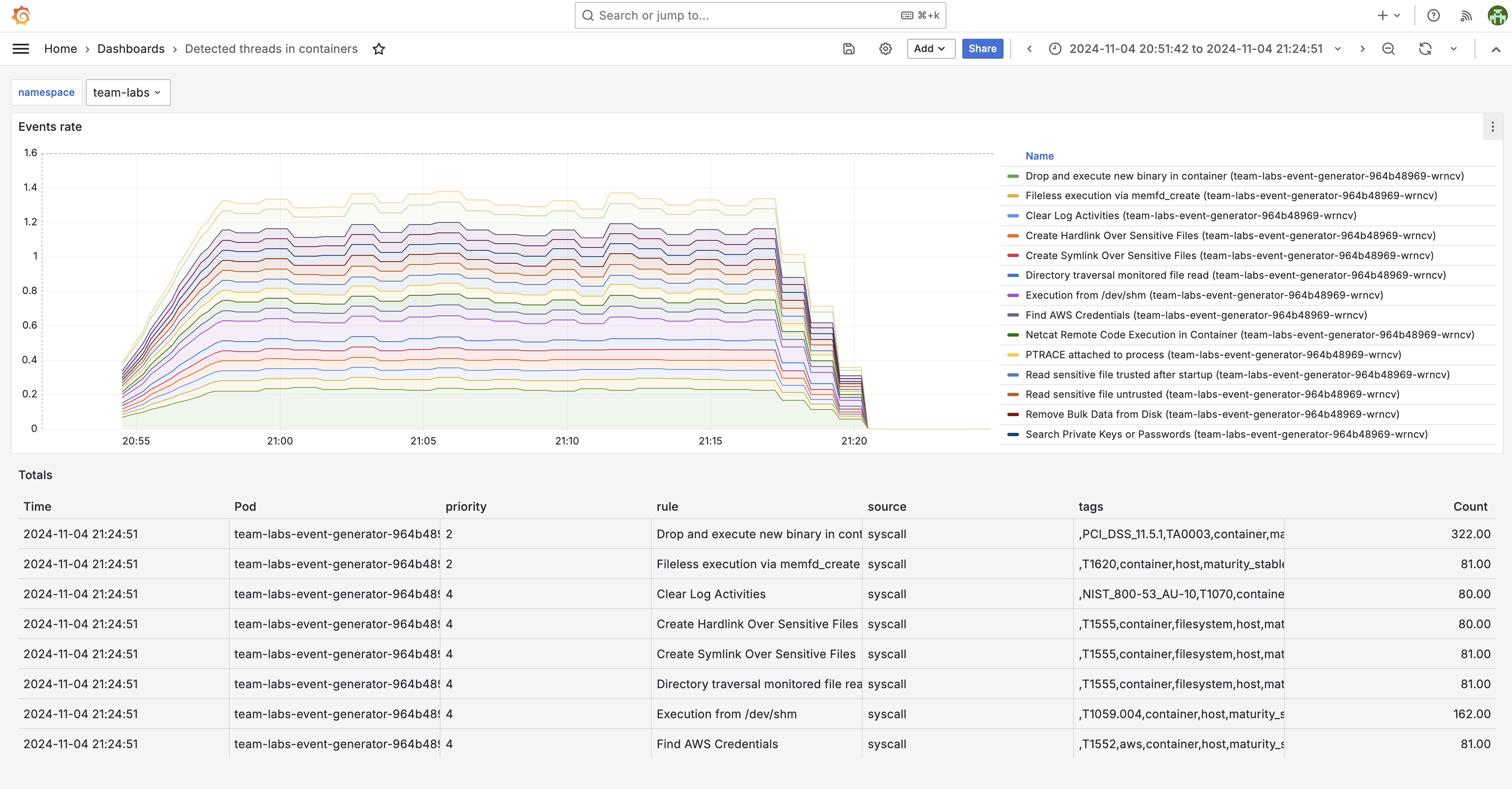
See the events in the detected threats in containers dashboard
-
Sign in as a Team member (using the
labs-user@labs.comuser). -
In the left menu, click on Apps and open Grafana.
-
Click on the Detected threats in containers dashboards.
-
See all the generated threat events:
Updated about 1 month ago
