Access and manage EAA for Gov from Control Center
In Akamai Control Center you can manage groups and properties for your Akamai accounts and monitor, configure, resolve, and plan your products.
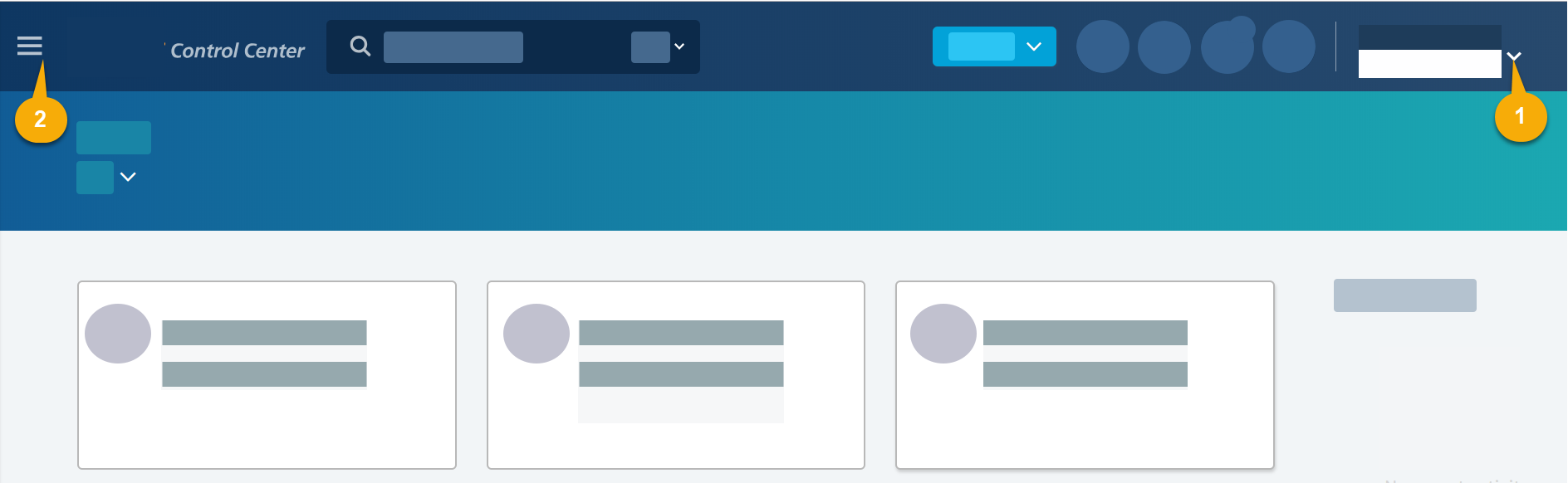
-
Account selector (1). Select the account or contract.
-
Services menu (2). Select ENTERPRISE SECURITY > Enterprise Center.
The contents and products under these menus may change based on the selected account or contract.
If you do not see the content or product in the menu, make sure the correct account or contract is selected. For further assistance contact your account representative or visit the Control Center help.
Access Enterprise Center from Akamai Control Center
-
Log in to Akamai Control Center at
<<PORTAL_URL>>. -
Go to ☰ > ENTERPRISE SECURITY > Enterprise Center.
Alternatively, you can go to ☰ > ENTERPRISE SECURITY > Enterprise Application Access . You will be redirected to Applications list page in EAA.
Control Center is not supported on Microsoft Edge browser.
Manage role-based access control
Enable role based access control for Enterprise Application Access for Gov (EAA for Gov) administrators in Identity and Access Management application in Akamai Control Center. When you have an account with Akamai, for each contract, admin and viewer roles are commonly used for controlling Enterprise Application Access for Gov (EAA for Gov). Other default roles like editor, publisher are not used in Enterprise Application Access for Gov. The admin role has read and write access to the EAA for Gov application. The viewer role has read access to the EAA for Gov application and cannot make configuration updates. Small organizations normally have one user with admin role, to configure the different components of Enterprise Application Access for Gov like connectors, applications, directories, identity providers, and applications, and other users as viewers. Large organizations might have multiple contracts to isolate staging environment and production environment, or for isolation between different geographical locations. They might want to have multiple administrators having different privileges for different contracts. Alternatively, even within one contract, an organization might want to have a unique administrator for each component.
With role-based access control, you get a higher level of control and can fine-tune administration management tasks. It can be seamlessly distributed across multiple administrators by the super administrator of the account with role-based access control in Akamai Control Center. You can also customize the control for different components in Enterprise Application Access for Gov to different administrators by choosing the proper permission settings in the Identity and Access Management application in Akamai Control Center.
These portal roles are preconfigured for Enterprise Application Access for Gov in the Identity and Access Management application in Akamai Control Center are:
| Preconfigured roles | Permission settings | Read or Write privileges |
|---|---|---|
| Admin | EAA - Admin | EAA for Gov administrator with read and write access to connectors, identity providers (IdP), directories, applications, and reports. |
| Viewer | EAA - ReadOnly | EAA for Gov administrator with read access to connectors, identity providers, directories, applications, and reports. |
The different portal roles that can be configured for Enterprise Application Access for Gov in the Identity and Access Management application in Akamai Control Center are:
| Configurable roles | Permission settings | Read or Write privileges |
|---|---|---|
| EAA for Gov applications administrator | EAA - App Admin | Control Center administrator with read and write access to EAA for Gov applications only, and read access to all EAA for Gov resources. |
| EAA for Gov connector administrator | EAA - Connector Admin | EAA for Gov administrator with read and write access to connectors only, and read access to all EAA for Gov resources. |
| EAA for Gov identity administrator | EAA - IDP Admin | EAA for Gov administrator with read and write access to EAA for Gov IdP and directories only, and read access to all EAA for Gov resources. |
| EAA for Gov reports administrator | EAA - Report Admin | EAA for Gov administrator with read and write access to EAA for Gov Reports only, and read access to all EAA for Gov resources. |
| EAA for Gov custom administrator | Any combination of the above settings | EAA for Gov administrator gets permissions based on which combinations are selected. For example, if you set both EAA - Connector Admin and EAA - IdP Admin permissions to one administrator, then your administrator have write access to connectors, identity providers, and directories, and read access to all EAA for Gov resources. |
In Akamai Control Center, with Identity and Access Management application, for each contract, you can create custom roles for EAA for Gov administration, and assign users belonging to the account to these roles.
Users with read only access might not be able configure or view some of the EAA for Gov Dashboard features.
Create a custom role on Akamai Control Center
The administrator for the account can create EAA for Gov app admin, EAA for Gov connector admin, EAA for Gov identity admin for controlling different Enterprise Application Access for Gov resources. It gives certain control for read and write privileges for different Enterprise Application Access for Gov components.
-
Go to ☰ > ACCOUNT ADMIN > Identity & access.
-
Select Roles.
-
Click Create role. In Create a new role configure the following:
-
In Enter Name type a name for the custom role.
-
In Enter Description type a description for the custom role.
-
In Summary enter a list of products.
-
-
Select All permissions. Based on the type of access required for the role, the administrator can select one or more of the permissions for controlling Enterprise Application Access for Gov:
| Admin role | Write and Read access resource type | Ready only access resource type |
|---|---|---|
| EAA - App Admin | ✓ EAA for Gov application | ✓ all |
| EAA - Connector Admin | ✓ EAA for Gov connector | ✓ all |
| EAA - IdP Admin | ✓ EAA for Gov identity provider (IdP) and directories | ✓ all |
| EAA - Report Admin | ✓ EAA for Gov Reports (IdP) | ✓ all |
Further customization is possible by selecting multiple choices, for example, you can have EAA - App Admin and EAA - Connector Admin set to one administrator, so that your admin has read and write access to application, connector, and read access to identity provider, directory, and EAA reports.
If you need to control other Akamai products, you can choose the permissions to access those products.
- Click Save.
Add a user to a portal role in Akamai Control Center
You can add any user belonging to the account, to do administration of the different resources like applications, connectors, identity providers (IdP) or directories.
-
Open the application.
-
In the Akamai Control Center, go to ☰ > ACCOUNT ADMIN > Identity & access.
-
In the classic Luna UI, on the Configure menu, go to Organization and click Manage Users & Groups.
-
-
Select Users and API Clients.
-
In Group select All Groups.
All the users associated with the account within all groups are shown. -
Select the user whose role needs to be modified.
-
Select Edit roles.
All of the contracts are in the Group name column. All of the roles of this user for each contract are in the Roles column. -
Select the contract for which you want to change the privileges for the user.
-
In Roles click Edit and enter the new role you created and update the role of the user.
-
Click Save. The user's role for the contract gets updated.
-
When the user logs into the Enterprise Center for the appropriate contract, based on the permissions set by the account administrator, they are allowed to access that resource.
Example:
There are three contracts for an account. The user user_a@gmail.com has an admin role for contract_1, unassigned roles for contract_2 and contract_3, initially.
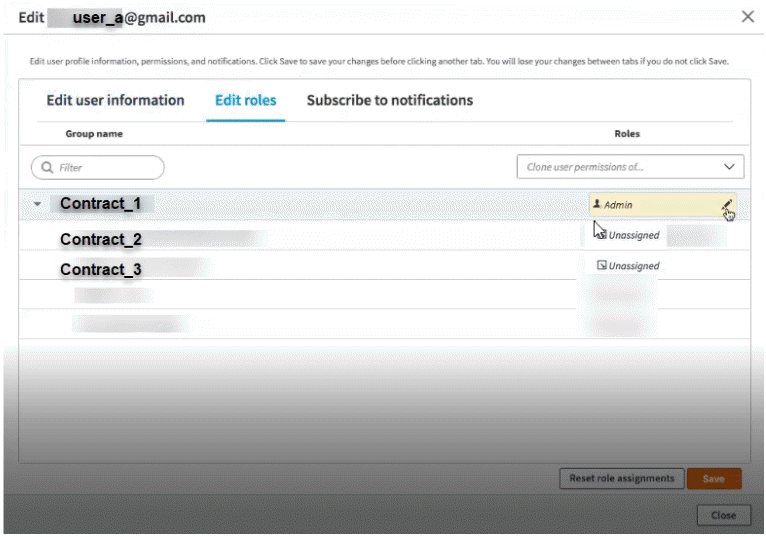
If you want to grant read and write access only to the EAA for Gov application resource for this user, update a custom role of EAA for Gov-App-Admin.
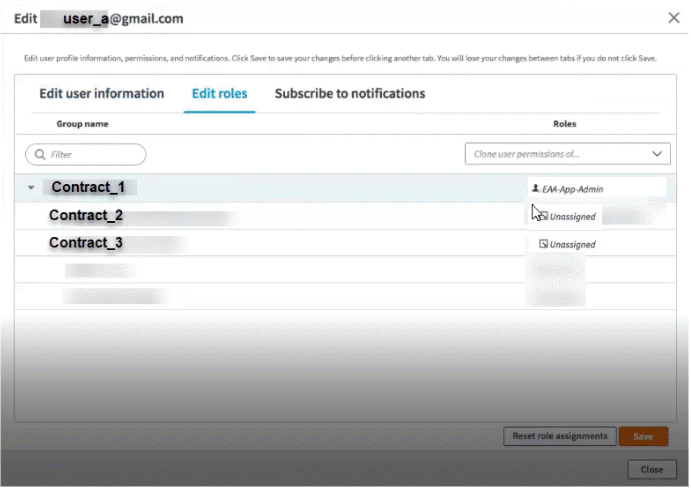
With the updated permissions, when the user logs in with valid credentials, they can make configuration updates in Applications. But when they try to access identity provider, directory, or connectors they get the error message: You are not authorized to perform this operation. Please contact your administrator.
Updated 7 months ago
