Deploy a hybrid solution for consistent web applications security in all environments
Akamai provides industry-leading web app and API protection capabilities on its edge network. App & API Protector Hybrid looks at extending this protection beyond the Akamai edge to ensure that threat prevention is closer to your applications.
With App & API Protector Hybrid, you gain advanced web application and API protection that goes far beyond traditional rules-based controls. Powered by machine learning, automation, and real-time threat intelligence from Akamai’s global network, it continuously defends against the OWASP Top 10 vulnerabilities across any environment, whether it’s your own datacenter or cloud, delivering consistent policies and centralized visibility from the Akamai Control Center dashboard.
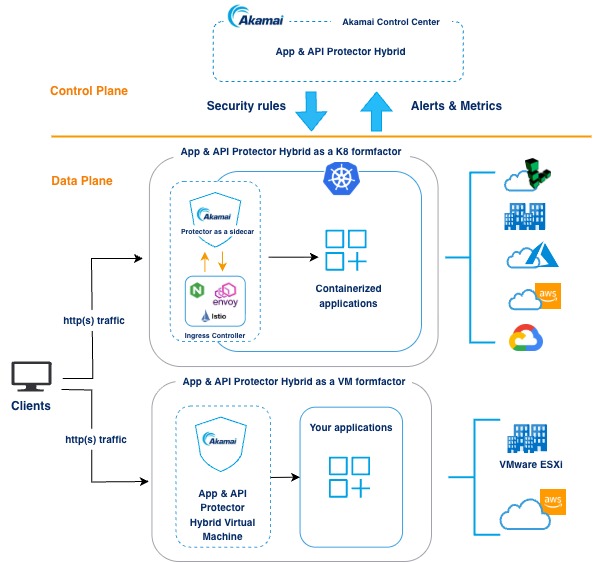
App & API Protector Hybrid enables its engine to run within your own cloud or on-premises infrastructure, while the dashboard lives in Akamai Control Center. Because the application engine operates on your premises, all inspection and data processing happens within your controlled environment and your clients’ data does not leave your infrastructure.
You can configure and control all Web Application Firewall rules, Custom Rules, and Rate Limiting Policies in the App & API Protector Hybrid dashboard which is the main control center for managing your security settings. You can access the dashboard in Akamai Control Center from anywhere at any time.
The protections you configure in the App & API Protector Hybrid dashboard live in Protector (the application engine) which applies all configured Web Application Firewall actions and rule customizations on the processed traffic.
Setup overview
Setup involves the following high-level steps:
Step 1. Create Connection and Security Configurations
There are two key configurations that you need to create in Akamai Control Center before deploying Protector on your infrastructure:
- Connection Configuration. You need it to establish communication between Protector (installed on your infrastructure) and the Akamai services.
- Security Configuration. It contains all websites you want to protect and details on how you want to protect them.
Step 2. Deploy Protector on your infrastructure.
After you’ve configured the Connection and Security Configurations, deploy Protector on your infrastructure. From now on, it will monitor, manage and secure traffic processing from sources you’ve defined. Depending on your deployment environment, Protector instances can run as sidecars in Kubernetes-based deployments (NGINX, Istio Ingress Gateway, Envoy Gateway), or as virtual machine instances created from a reverse proxy AMI or OVA image.
Monitor how protections work and adjust them
Setup includes creating a new Security Configuration, with all protections on and actions set to Alert, which means that you can now view requests in reports. For a few weeks monitor your traffic. You'll be able to view attack vs. regular requests. Based on what you see, you may want to adjust protections, tweaking settings until you have them working the way you want. Protections let you set controls that apply to incoming requests:
- Protect against web application attacks. Web Application Firewall protections perform rule-based evaluation of requests to either deny a request or trigger an alert. These rules focus on request behavior and traits. They defend against multiple known attack vectors and flag suspicious behavior, like protocol violations, HTTP policy violations, cross-site scripting attacks, injection attacks, and more.
- Use custom rules. Use custom rules to handle scenarios not covered by standard rules or to quickly patch new website vulnerabilities.
- Protect against excessive request rates and denial-of-service (DoS) attacks. Detect and control unusually high volumes of incoming requests that can indicate application abuse or denial-of-service attempts.
For comprehensive guidance on using App & API Protector, refer to the full online help (login required). If you’re interested in more details about the product, fill in the contact form.
Updated 2 months ago
