Mitigate threats against your web applications
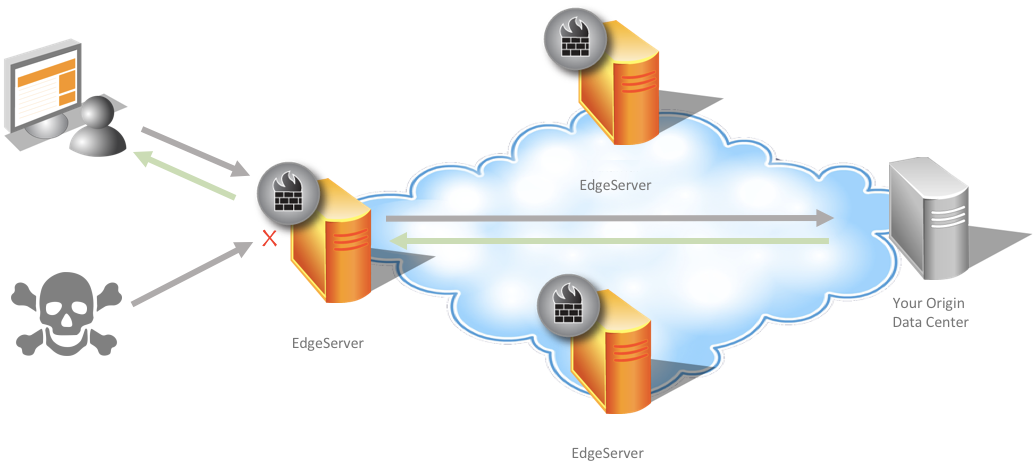
App & API Protector is a highly-scalable defense service that protects your website and APIs. It detects and mitigates application threats in HTTP and HTTPS traffic as they attempt to pass through Akamai’s edge platform to reach your origin data centers.
Choose your product
This solution comes in two flavors:
-
App & API Protector. Delivers robust protection that detects and mitigates application threats in HTTP and HTTPS traffic as they attempt to pass through Akamai's edge platform to reach your origin data centers. The platform specializes in accelerated web content delivery to expect significant speed improvements too. Setup and management is simple and protections update themselves. This is a great choice if you don't have a dedicated IT staff to manage protections.
-
App & API Protector with Advanced Security Management. If you have a dedicated security staff and need highly-scalable web app protection which gives you more precise control over what you protect and how, this is the solution for you. This premier WAF solution offers greater flexibility and the ability to fine-tune several settings. You can:
- use multiple security configurations to split protections between regions, websites, business units, or web property type
- scope different protection setups very precisely using match targets
- set actions and exceptions by individual rule
- stop malicious clients before they can attack using client reputation protections
- run your WAF in manual mode to schedule engine updates, or run in automatic to let the system upgrade itself regularly (recommended).
Configuration overview
Here's what goes into your web application security setup:
A Security Configuration is the basic building block you use to set protections. If you use:
-
App & API Protector you have a single security configuration that contains all your protections. To cover different hostnames with different kinds of protections, you use separate security policies.
-
App & API Protector with Advanced Security Management, you can have multiple security configurations. You might have separate security configurations for separate business units, domains, and development environments.
Security configurations are versioned and as you refine and test your updates, you have an audit trail of changes and can rollback to prior versions. One security configuration can cover many hostnames, but a single hostname is covered by only one active security configuration at a time.
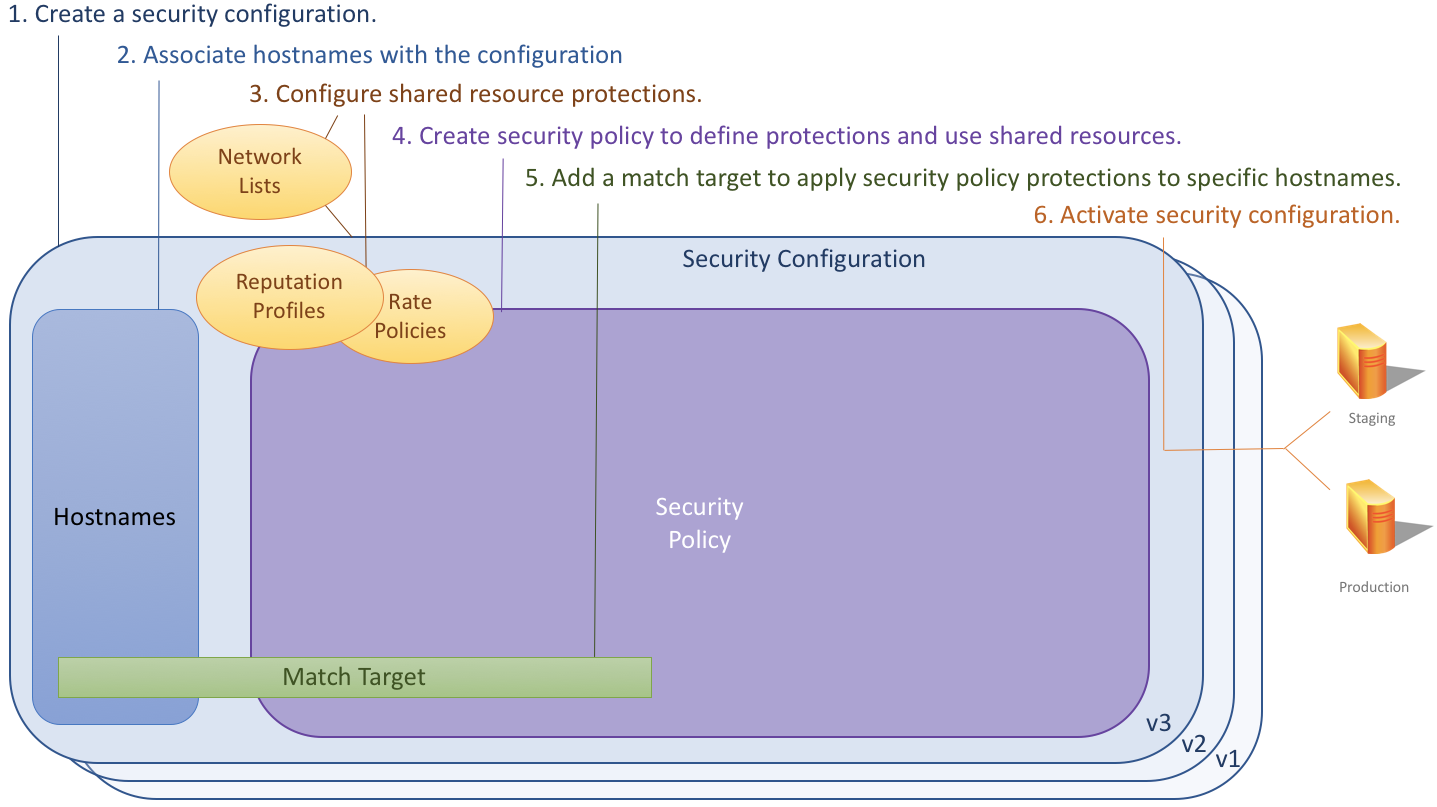
Shared Resources are elements you can use across multiple security policies or security configurations. The advantage of shared resources is that you update the definition in one place and all the instances where it’s used are updated automatically. Here are some examples of shared resources:
- Network Lists let you group IP addresses or geographic locations. For example, use the lists in security policies to allow or block traffic.
- Rate Policies let you set thresholds to flag request traffic that’s too fast to be from a human.
- Client Reputation Profiles let you filter out IP addresses likely to be web attackers, web scrapers, or other unwanted request clients.
A Security Policy lets you define the response action applied to different protection controls. Also, here's where you can apply or use shared resources you set up. You can use several security policies to cover different scenarios.
A Match Target defines which security policy applies to which API, hostname, and/or path (part of Advanced Security Management only). You can also focus a policy on a very precise set of requests, like those for a specific file type. You set the order in which protections evaluate match targets. For best results, order more specific match criteria last. Nothing is protected without a match target; you need at least one.
When a request meets the scope you set in hostname and match target criteria, App & API Protector applies a wide array of protections and evaluates a request in a set order.

Request Evaluation. A request that meets criteria you entered in your match target passes through the protection controls you set in your security policy. If evaluation detects an attack vector, it alerts you or denies further access right there, depending upon your action settings. Requests that don’t meet your match target criteria aren’t evaluated.
Your first security configuration in five minutes
*Before you begin: You must have a delivery configuration active on our platform, on at least the staging environment.*
- Visit https://control.akamai.com/ and log in.
- Go to > WEB & DATA CENTER SECURITY > Security Configuration.
- Click Create New Security Configuration.
- With Use recommended presets selected, click Create.
- App & API Protector walks you through the rest of setup.
- Activate the security configuration.
On the upper right of the security configuration page, click Activate. Select your Network (Staging to test, or Production to go live). Enter notes about what you changed in this version and click Activate.
Monitor and tune
Setup creates a new security configuration, with all protections on, with actions set to Alert, which means that you can now view requests in reports. For a few weeks monitor your traffic. You'll be able to view attack vs. regular requests. Based on what you see, you may want to tune protections, tweaking settings until you have them working the way you want. During this time, you can:
-
Create additional security policies. You may want different actions and settings for different hostnames and/or paths. For example, apply one set of protections to website pages and a different set to APIs.
-
Tweak protections. Protections let you set controls that apply to incoming requests. Click a link to learn how to configure, apply, and tune each protection (login required):
- Control requests by IP or geographic location. Say you've been getting bothersome requests from a few specific IP addresses. Or maybe you want to block all traffic from The Onion Router (TOR), which hackers use to hide their identity. IP/Geo controls let you block or allow traffic coming from a specific IP, subnet, or geographic area
- Protect against Denial-of-Service (DoS) attacks. Distributed Denial of Service (DDoS) attacks attempt to bring down web content by overwhelming a website's origin server with bogus requests, often from multiple locations and networks. This attack traffic can result in slow page loads and even complete blockage of legitimate site traffic.
- Limit high-rate clients. Identify clients that send requests at an excessive rate.
- Mitigate slow-posting clients. Slow POST attacks are Denial-of-Service attacks featuring extremely slow request rates. Attackers send a request in pieces, slowly, over time. You can designate a rate threshold (in bytes per second) that triggers either an alert or abort action for requests below that threshold.
- Use custom rules. Use custom rules to handle scenarios not covered by standard rules or to quickly patch new website vulnerabilities.
- Protect against web application attacks. Web application firewall protections perform rule-based evaluation of requests to either deny a request or trigger an alert. These rules focus on request behavior and traits. They defend against multiple known attack vectors and flag suspicious behavior, like protocol violations, HTTP policy violations, cross-site scripting attacks, injection attacks, and more.
- Enforce API request constraints. If you set API request body and resource constraints when you register your API, you can make your security policy enforce them.
- Control for client reputation. Stop malicious clients before they can attack, based on Akamai’s visibility into prior behavior of individual and shared IP addresses. (part of Advanced Security Management only)
- View and mitigate bots. Welcome the bots you want and mitigate those you don't. If you need to handle adversarial bots, or protect important transactional pages, like login or checkout, upgrade to Bot Manager Premier. See the intro in this guide.
-
When it's time to add a hostname, you can evaluate it first. Evaluation is a dedicated mode that lets you preview how the new hostname would fare under your current security setup. If a control triggers, even one you set to deny, the evaluation logs an alert. Track evaluation until you're certain that protections handle this new hostname appropriately. Then you can move the hostname to full protection with confidence.
Read on to learn about the following additional protection capabilities you can purchase with App & API Protector or individually:
- Combat adversarial bots. To stop attacks that target transactional pages (like login, gift card balance, or checkout) and to combat the most sophisticated bots, turn to Bot Manager Premier, which you can add on to any WAF solution or purchase alone.
- Prevent user account takeover. Stop credential stuffing and human web fraud with the smartest detection and mitigation.
- Detect suspicious or malicious script activity. Client-Side Protection & Compliance lets you detect attackers trying to steal data via first or third-party scripts that you use on your site.
For details on all you can do with App & API Protector, read the full online help (login required).
Updated over 1 year ago
