Prevent account abuse
How can you trust that a login request is coming from the account owner and not an imposter?
Use Account Protector to help detect and mitigate inauthentic user behavior that can lead to account takeover and other abuse. The solution recognizes authentic users, allowing seamless customer journeys for trusted users and blocking imposters who want to steal assets like: bank account funds, gift card balances, and rare game items. This solution works in real time, accelerating your ability to spot and stop account takeover without increasing friction for your legitimate users.
When you purchase Account Protector you also get the cutting-edge bot mitigation capabilities of Bot Manager Premier, which can help you fend off credential stuffing and other automated abusive behaviors.
User risk assessment
Account protector assesses user risk by detecting anomalies in user behavior based on the following:
-
An individual user profile, which is built over time. It contains previous devices, locations, network, activity time and other observed traits. Based on the profile, Account Protector can easily spot anomalies. The user may be connected to a username they use to identify themselves on your site, but also has a unique user identifier ( UUID) which is a random string of letters and numbers generated by Account Protector to uniquely identify a user.
-
If a user has no profile yet, Account Protector leverages population profiles derived from our vast global web delivery platform.
-
Other risk signals like source reputation, behavioral anomalies, and bot detections.
Request evaluation
You specify the endpoints that Account Protector should cover. When a user logs in, Account Protector evaluates the request and calculates a user risk score.
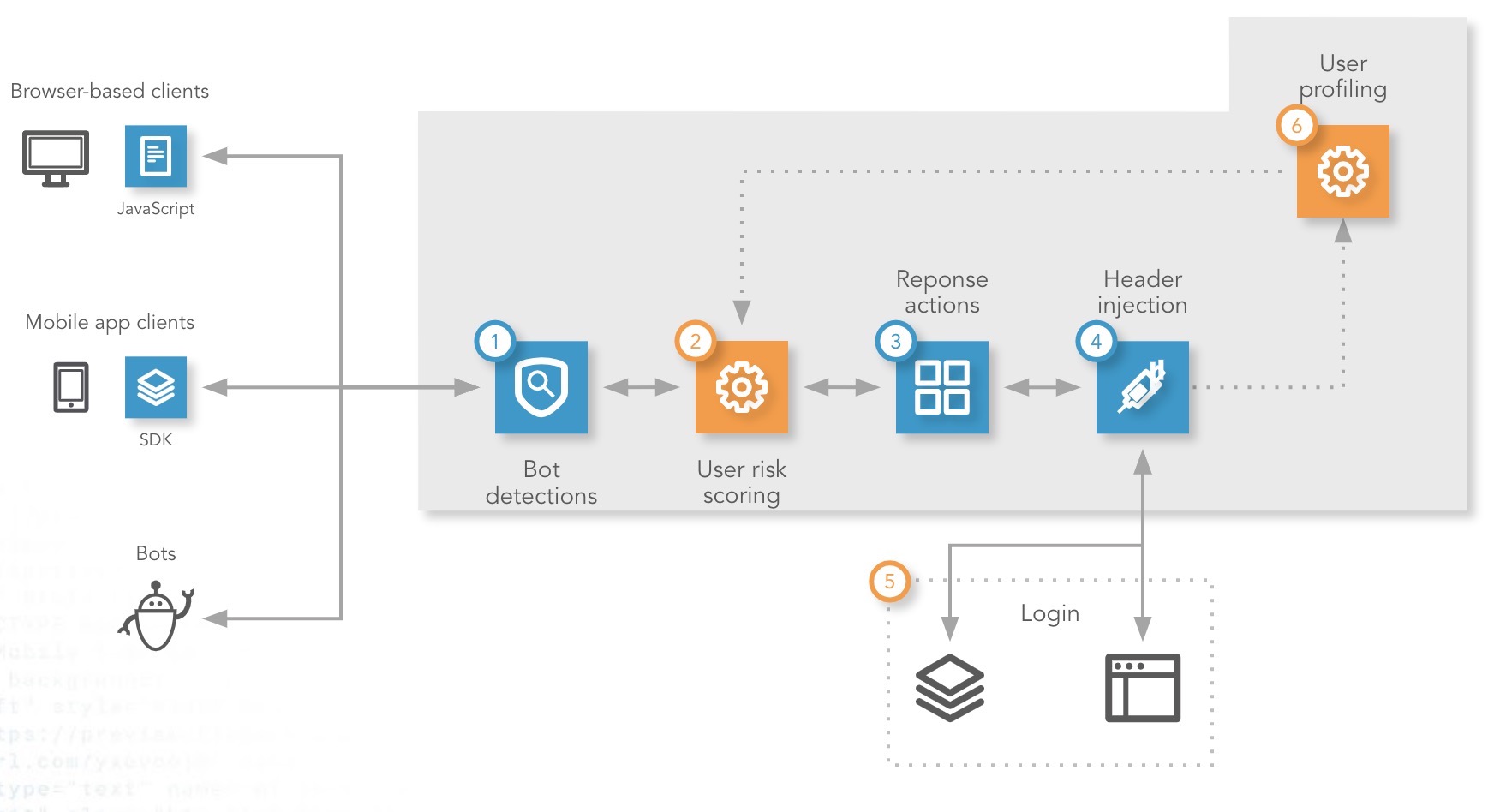
-
Bot Manager Premier evaluates the request and takes the action you specify when it detects an adversarial bot.
-
Account Protector evaluates the authenticity of the user and calculates a risk score for the request. Successful logins, behavioral data, and other factors feed advanced machine learning algorithms feed the user profile (see step 6).
-
Account Protector applies the action you set for the request's user risk score in your user risk response setup.
-
If you want, have Account Protector forward user risk information to your origin.
-
You can take additional action at the origin, including step-up authentication or additional fraud correlation.
-
Legitimate login requests are incorporated into the behavioral user profiling the product uses on future requests from the account owner. For example, if the user is a frequent-traveler, Account Protector learns this and factors varying locations into the user risk score for that specific user.
Setup
-
Define your login endpoints.
Tell Account Protector which login pages you want to protect and where to find them. -
Specify expected traffic.
When Account Protector knows what clients you don't expect, you can set an action for those requests. For client types you do expect to make requests, it lets you set a more nuanced response, based on user risk score.
For details, read the full Account Protector online help (login required).
Updated almost 2 years ago
